In today's digital landscape, cybersecurity has become a critical concern for businesses, organizations, and individuals. As more and more activities move online, the need to protect sensitive information, maintain operational integrity, and ensure compliance with security standards has never been more pressing. Two key components of a robust cybersecurity strategy are Web Application Firewalls (WAF) and traditional firewalls. While both are designed to enhance security, they serve different purposes and operate in distinct ways. This article explores the key differences between WAF and firewalls, highlighting their unique functionalities, deployment scenarios, and how they can complement each other in a comprehensive cybersecurity framework.
What are Firewalls?
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Its primary function is to create a barrier between internal networks and external threats, such as unauthorized access and malicious traffic. Firewalls are essential for protecting private networks, ensuring that only legitimate traffic is allowed to pass through while blocking potentially harmful or unwanted data.
Types of Firewalls
Firewalls come in various types, each with its strengths and limitations:
- Packet-Filtering Firewalls: These are the most basic type of firewalls. They operate at the network layer (Layer 3) of the OSI model and filter traffic based on IP addresses, ports, and protocols. They are simple and fast but cannot inspect the content of packets.
- Stateful Inspection Firewalls: These firewalls track the state of network connections and can make decisions based on the context of the traffic. They are more advanced than packet-filtering firewalls and can provide better security by analyzing the full context of traffic flows.
- Proxy Firewalls: Also known as application-level gateways, proxy firewalls act as intermediaries between internal and external networks. They filter traffic at the application layer (Layer 7) and can provide detailed traffic inspection and control. However, they can introduce latency and may not be suitable for high-speed networks.
- Next-generation firewalls: NGFWs are advanced firewalls that combine traditional firewall capabilities with modern security features such as intrusion prevention systems (IPS), application awareness, and threat intelligence. They are designed to provide comprehensive protection against a wide range of threats.
Strengths and Limitations
Firewalls are highly effective at blocking unwanted traffic and preventing unauthorized access to private networks. They can be configured to allow or deny traffic based on specific rules, providing a strong first line of defense against network-level attacks. However, firewalls have limitations when it comes to inspecting application-layer traffic. They may not be able to detect sophisticated attacks that exploit vulnerabilities in web applications, such as SQL injection or cross-site scripting (XSS).
What are Web Application Firewalls (WAF)?
A Web Application Firewall (WAF) is a specialized security solution designed to protect web applications from application-layer attacks. Unlike traditional firewalls, which focus on network traffic, WAFs are specifically tailored to monitor and filter HTTP/HTTPS traffic between web applications and clients. They provide an additional layer of security by inspecting and analyzing web traffic to identify and block malicious requests.
Key Features
WAFs offer several key features that make them essential for protecting web applications:
- Protection Against OWASP Top Ten Threats: WAFs are designed to mitigate common web application vulnerabilities listed in the OWASP Top Ten, such as SQL injection, XSS, cross-site request forgery (CSRF), and others.
- Monitoring and Logging: WAFs provide detailed monitoring and logging capabilities, allowing administrators to track and analyze traffic patterns, detect anomalies, and respond to potential threats in real-time.
- Custom Rules and Policies: WAFs can be configured with custom rules and policies to address specific security needs. This allows organizations to fine-tune their security posture and adapt to evolving threats.
Strengths and Limitations
WAFs are highly effective at mitigating application-layer attacks that traditional firewalls may miss. They provide granular control over web traffic and can detect and block sophisticated threats that target web applications. However, WAFs are limited in their ability to address broader network-level threats. They are designed to protect web applications and may not provide comprehensive protection for other aspects of the network.
Key Differences Between WAF and Firewall
Layer of Operation
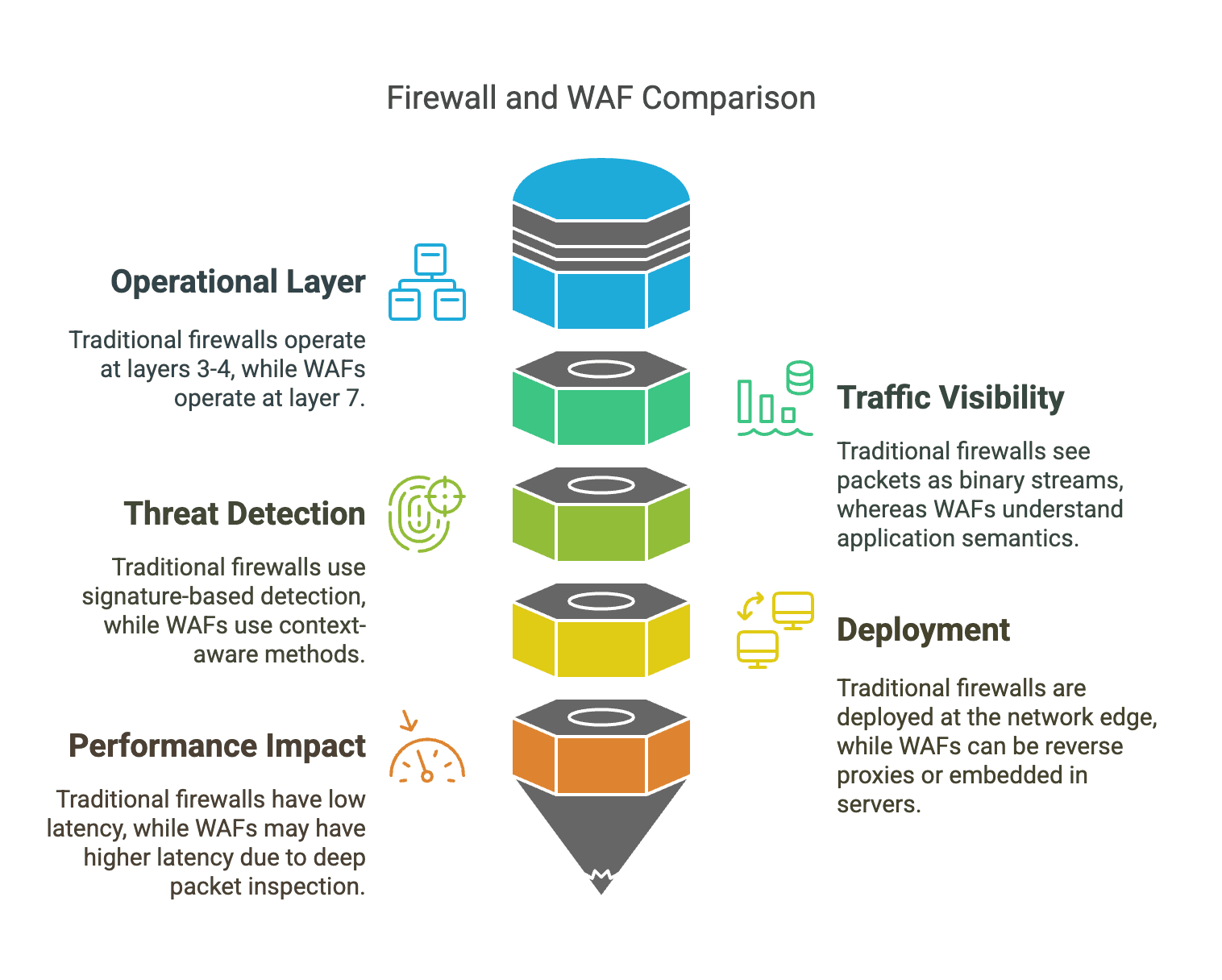
One of the most fundamental differences between WAFs and firewalls is the layer of the OSI model at which they operate. Firewalls typically operate at OSI Layers 3 and 4, which correspond to the network and transport layers. They focus on monitoring and controlling network traffic based on IP addresses, ports, and protocols. In contrast, WAFs operate at OSI Layer 7, the application layer. They are specifically designed to inspect and filter HTTP/HTTPS traffic, providing detailed analysis and protection for web applications.
Traffic Targeted
Firewalls protect private networks from unauthorized access and malicious traffic. They monitor and control network traffic, ensuring that only legitimate traffic is allowed to pass through. WAFs, on the other hand, focus specifically on web applications and HTTP/HTTPS traffic. They protect web applications from application-layer attacks, such as SQL injection, XSS, and CSRF.
Deployment and Architecture
Firewalls are typically deployed at the network edge, where they act as a barrier between internal networks and external threats. They are strategically placed to monitor and control traffic entering and leaving the network. WAFs, however, are deployed closer to web applications and servers. They are often placed in front of web servers to provide real-time monitoring and filtering of web traffic.
Types of Attacks Mitigated
Firewalls are effective at protecting against network-level attacks, such as unauthorized access, port scanning, and denial-of-service (DoS) attacks. They can block malicious traffic based on predefined rules and policies. WAFs, on the other hand, are designed to protect against application-layer attacks. They can detect and block sophisticated threats that target web applications, such as SQL injection, XSS, CSRF, and other OWASP Top Ten vulnerabilities.
Firewall vs WAF: Use Cases
Firewall Use Cases
Firewalls are essential for protecting individual users and networks. They are commonly used in the following scenarios:
- Network Perimeter Protection: Firewalls are essential for protecting the perimeter of a network. They act as a barrier between internal networks and external threats, such as the Internet. By filtering traffic based on IP addresses, ports, and protocols, they prevent unauthorized access and block malicious traffic.
- Segmentation of Internal Networks: Firewalls can be used to segment internal networks into different security zones. This helps in controlling the flow of traffic between different parts of the network and limiting the spread of potential threats.
- Compliance and Policy Enforcement: Firewalls help organizations meet compliance requirements by enforcing security policies. They can log and monitor traffic, ensuring that only authorized activities are allowed.
- Basic Protection Against Network-Level Threats: Firewalls provide a first line of defense against common network-level attacks, such as port scanning and denial-of-service (DoS) attacks.
WAF Use Cases
WAFs are specifically designed to protect web applications and are used in the following scenarios:
- Protection Against Application-Layer Attacks: WAFs specialize in protecting web applications from application-layer attacks, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). These attacks target vulnerabilities in web applications and can lead to data breaches.
- Enhanced Security for Web-Centric Environments: WAFs are particularly useful in environments where web applications are a critical part of the business infrastructure. They provide detailed inspection and filtering of HTTP/HTTPS traffic, ensuring that web applications are protected from sophisticated threats.
- Meeting Compliance Requirements: WAFs can help organizations meet compliance requirements related to web application security. For example, they can be used to meet the requirements of PCI DSS for protecting web applications.
- Real-Time Monitoring and Threat Detection: WAFs provide real-time monitoring and logging capabilities, allowing administrators to detect and respond to threats quickly. They can analyze traffic patterns and identify anomalies that may indicate an ongoing attack.
How to Choose the Right Security Tool
When to Use a Firewall
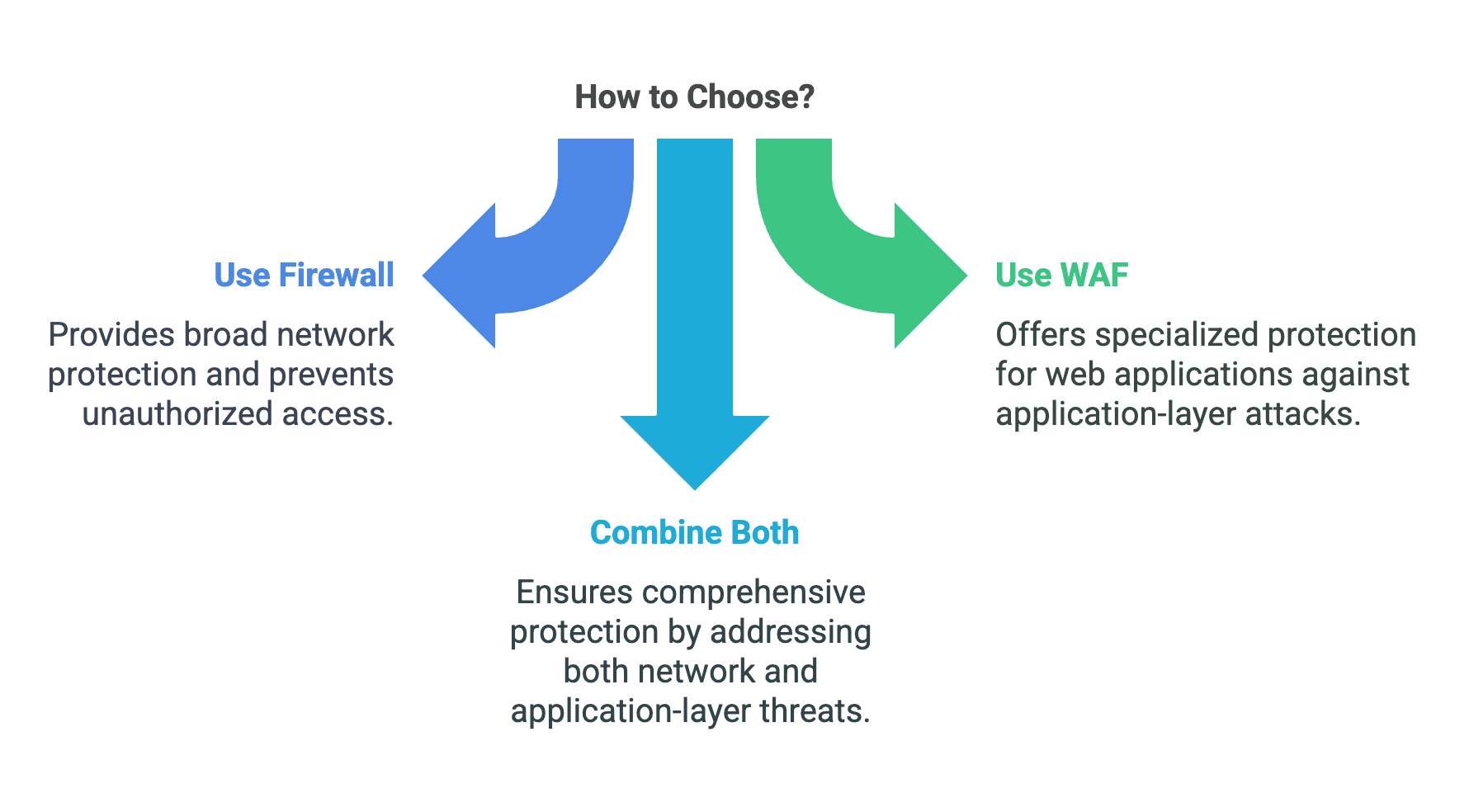
Firewalls are essential for broad network protection and preventing unauthorized access. They are ideal for organizations that need to protect private networks from external threats and ensure that only legitimate traffic is allowed to pass through. Firewalls provide a strong first line of defense against network-level attacks and are a fundamental component of any cybersecurity strategy.
When to Use a WAF
WAFs are ideal for organizations that rely heavily on web applications and need to protect against application-layer attacks. They are particularly useful in environments where web applications are exposed to the internet and are at risk of being targeted by sophisticated threats. WAFs provide specialized protection for web applications and can detect and block attacks that traditional firewalls may miss.
Combining WAF and Firewall
While firewalls and WAFs serve different purposes, they can be highly effective when used together. Combining these two security tools creates a layered security approach that provides comprehensive protection against a wide range of threats. Firewalls can protect the network from external threats, while WAFs can provide specialized protection for web applications. This layered approach ensures that both network-level and application-layer threats are addressed, providing a robust defense against potential attacks.
Future Trends and Convergence in Firewalls and WAFs
As cybersecurity continues to evolve, the traditional roles of firewalls and Web Application Firewalls (WAFs) are undergoing significant changes. The future of these security tools is marked by the integration of advanced technologies, cloud-native solutions, and unified platforms that offer comprehensive protection against a wide range of threats.
1. AI/ML Integration
The incorporation of Artificial Intelligence (AI) and Machine Learning (ML) is transforming both firewalls and WAFs, enabling them to detect and respond to threats more effectively.
- Firewalls: AI and ML are being used to enhance predictive analytics, allowing firewalls to identify and respond to anomalous traffic patterns in real-time. These advanced capabilities enable firewalls to detect and block sophisticated threats, including those that may have previously gone unnoticed. For example, AI-driven firewalls can analyze traffic patterns to identify potential DDoS attacks or unauthorized access attempts, providing a more proactive approach to network security.
- WAFs: WAFs are leveraging AI and ML to develop behavioral models that can detect zero-day API abuses and other emerging threats. By analyzing the behavior of web traffic, WAFs can identify unusual patterns that may indicate an attack, even if the specific threat has not been previously identified. This proactive approach helps organizations stay ahead of attackers who are constantly evolving their tactics.
2. Cloud-Native Evolution
The shift towards cloud-native solutions is driving the evolution of both firewalls and WAFs, making them more scalable and flexible.
- Firewall-as-a-Service (FWaaS): FWaaS solutions are becoming increasingly popular, offering organizations the ability to deploy and manage firewalls in the cloud. Providers like Zscaler and Perimeter 81 offer FWaaS solutions that provide comprehensive network security without the need for on-premises hardware. These cloud-based firewalls can scale dynamically to meet changing network demands, ensuring that organizations always have the protection they need.
- Serverless WAFs: The rise of serverless computing has led to the development of serverless WAFs. Solutions like AWS Lambda@Edge provide WAF protections that are integrated into serverless environments. This allows organizations to protect their web applications and APIs without the need for traditional WAF deployments. Serverless WAFs offer the benefits of scalability and flexibility, making them ideal for modern web-centric environments.
3. Unified Platforms
The future of cybersecurity is moving towards unified platforms that integrate multiple security tools into a single, cohesive solution. This trend is driven by the need for comprehensive protection against a wide range of threats.
EdgeOne is a prime example of a unified platform that combines WAF, DDoS protection, Bot management, and CDN acceleration capabilities. This integrated solution provides organizations with a comprehensive security framework that covers multiple aspects of their IT infrastructure. By combining these tools into a single platform, EdgeOne offers a more cohesive and effective approach to cybersecurity.
Through its unified platform architecture, EdgeOne’s Web Protection service achieves integrated security capabilities, lightweight operations and management, and maximized defense effectiveness. It is particularly suitable for medium and large enterprises and global business scenarios that need to balance security and performance. Users no longer need to trade-off between multiple standalone products to obtain comprehensive, integrated protection across the entire business chain. Sign up to begin your journey with us!
Conclusion
In conclusion, understanding the differences between WAFs and traditional firewalls is essential for a comprehensive cybersecurity strategy. Firewalls protect networks from unauthorized access and malicious traffic, while WAFs specialize in safeguarding web applications against application-layer attacks. Combining both creates a layered security approach that offers robust protection against diverse threats. The choice depends on the specific needs of the organization. Carefully evaluating these needs and selecting the right tools ensures effective protection in today's complex digital environment.

