In today's rapidly evolving digital landscape, cybersecurity has become a cornerstone of organizational resilience. businesses increasingly rely on web applications and interconnected networks, the need for robust security solutions has never been more critical. Two prominent technologies that have emerged to address these challenges are Web Application Firewalls (WAFs) and Next-Generation Firewalls (NGFWs). Both play vital roles in protecting digital assets, but their functions and deployment scenarios differ significantly. This article aims to provide a comprehensive technical comparison between WAFs and NGFWs, highlighting their unique capabilities, deployment scenarios, and how they can be strategically combined to fortify modern digital infrastructures.
Understanding Web Application Firewalls (WAFs)
A Web Application Firewall (WAF) is a specialized security solution designed to protect web applications from a wide range of application-layer attacks. Unlike traditional firewalls that focus on network traffic, WAFs specifically target the vulnerabilities and threats that arise from web-based interactions. They operate primarily at Layer 7 of the OSI model, where web applications reside, and provide granular protection against sophisticated attacks that exploit application logic and data.
Key Features and Capabilities
- Protection Against Application-Layer Attacks: WAFs are particularly effective against common web application vulnerabilities outlined in the OWASP Top 10, such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF). These attacks target the application's logic, data, and user interactions, making them difficult to detect without specialized tools.
- DDoS Mitigation and Traffic Filtering: WAFs can identify and block malicious traffic that may overwhelm a web application, such as Distributed Denial of Service (DDoS) attacks. By analyzing traffic patterns and filtering out suspicious requests, WAFs ensure that legitimate users can access the application without disruption.
- Compliance Assistance: Many organizations are required to comply with industry standards and regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR). WAFs play a crucial role in meeting these compliance requirements by providing detailed logs, audit trails, and security controls that demonstrate adherence to regulatory guidelines.
- Zero-Day Exploit Protection: WAFs often come equipped with advanced threat detection mechanisms that can identify and block zero-day exploits—attacks that target vulnerabilities before they are publicly known or patched. This proactive defense mechanism is essential for protecting web applications from emerging threats.
Deployment Scenarios and Typical Use Cases
WAFs are typically deployed in front of web servers, either as a hardware appliance, a software solution or as a cloud-based service. They are ideal for organizations that rely heavily on web applications, such as e-commerce platforms, financial institutions, and SaaS providers. By placing a WAF between the web application and the internet, organizations can create a secure perimeter that filters out malicious traffic before it reaches the application.
Exploring Next-Generation Firewalls (NGFWs)
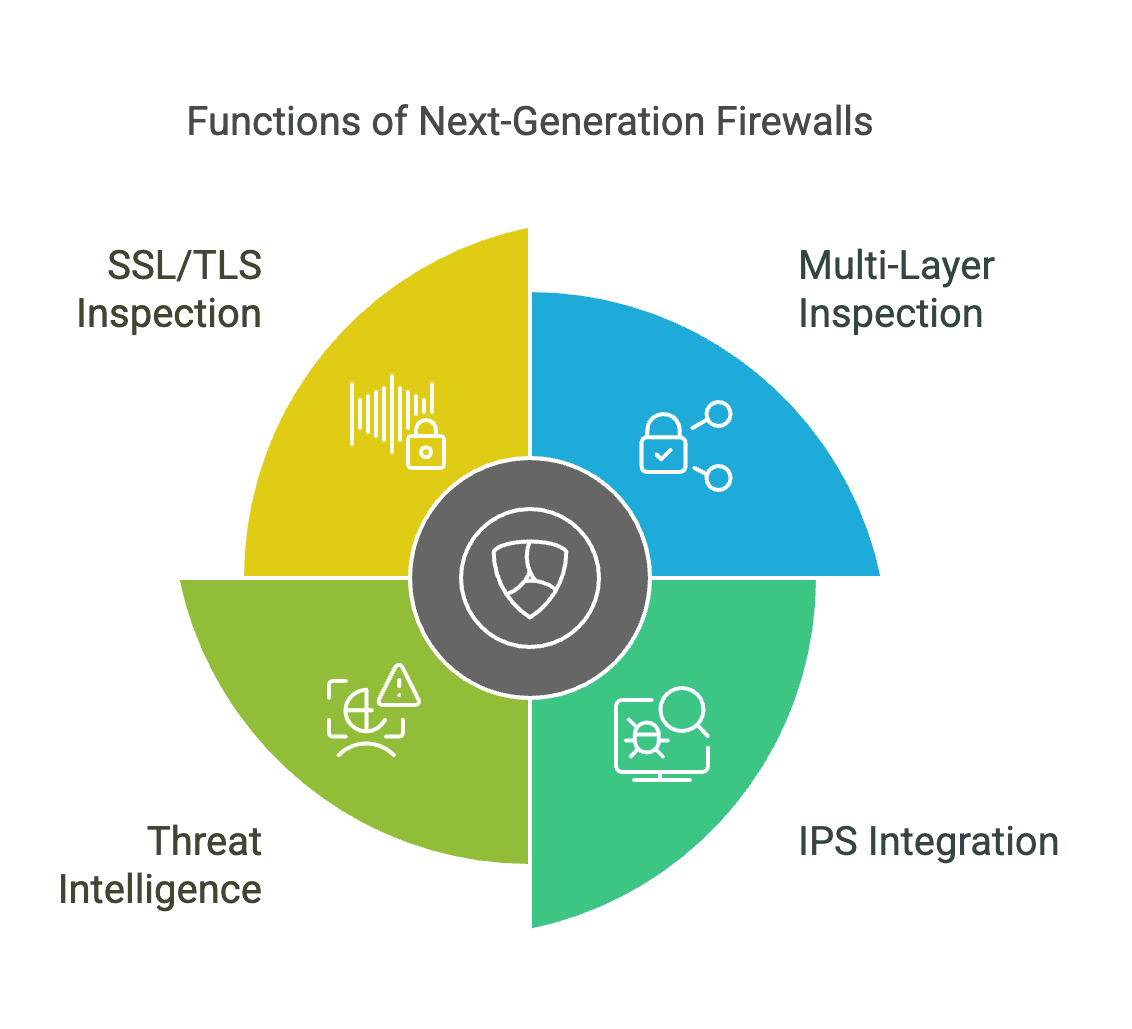
Next-Generation Firewalls (NGFWs) represent a significant evolution in firewall technology, moving beyond traditional packet filtering to provide comprehensive security across multiple layers of the network. NGFWs integrate advanced features such as Intrusion Prevention Systems (IPS), application awareness, and threat intelligence to offer robust protection against a wide range of threats.
Core Functionalities and Advanced Features
- Multi-Layer Inspection: NGFWs operate across multiple layers of the OSI model, including Layers 3 (Network), 4 (Transport), and 7 (Application). This multi-layer inspection allows them to detect and block threats that traditional firewalls might miss, such as malware embedded in encrypted traffic or sophisticated attacks that exploit application vulnerabilities.
- Intrusion Prevention System (IPS) Integration: NGFWs often include an integrated IPS, which provides real-time detection and prevention of known and emerging threats. By analyzing network traffic for suspicious patterns and behaviors, IPS can identify and block attacks before they can cause damage.
- Threat Intelligence and Real-Time Updates: NGFWs leverage threat intelligence feeds to stay updated on the latest threats and vulnerabilities. This allows them to automatically adjust their policies security and block known malicious IP addresses, domains, and attack vectors.
- SSL/TLS Inspection and Termination: Many modern attacks exploit encrypted traffic to evade detection. NGFWs can decrypt SSL/TLS traffic, inspect it for threats, and then re-encrypt it, ensuring that even encrypted communications are secure.
Use Cases and Deployment Options
NGFWs are versatile solutions that can be deployed in various environments, including physical data centers, cloud infrastructures, and hybrid setups. They are particularly useful for organizations that require comprehensive network-wide security, such as enterprises with multiple locations, remote workers, and complex IT environments. NGFWs can be deployed as hardware appliances, virtual machines, or cloud-based services, making them suitable for organizations of all sizes.
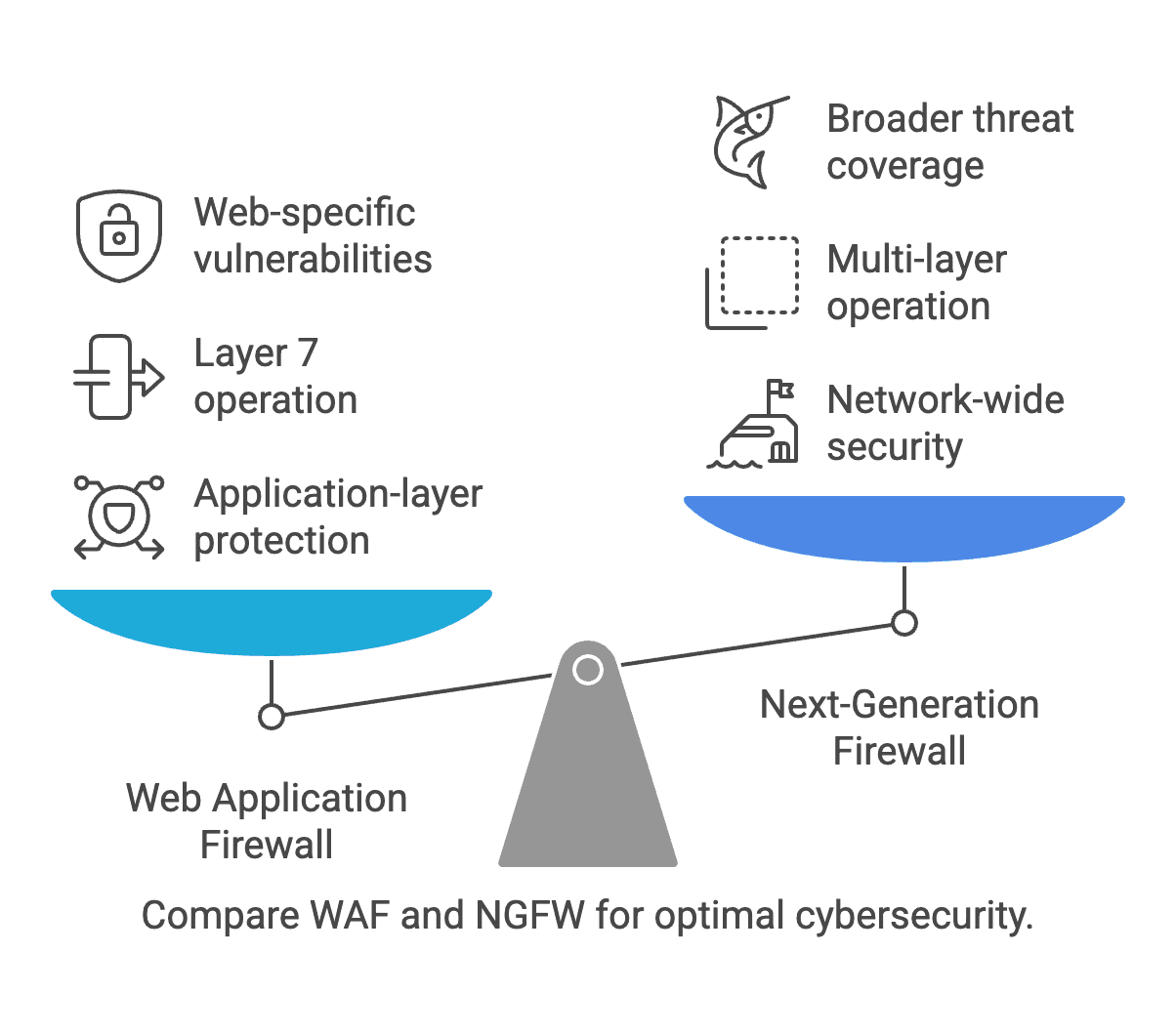
Technical Comparison: WAF vs NGFW
While both WAFs and NGFWs are essential components of modern cybersecurity, they serve different purposes and operate at different layers of the network. Understanding their key differences is crucial for selecting the right solution for specific security needs.
1. Purpose and Scope
- WAF: Focused on protecting web applications from application-layer attacks. It provides granular security controls tailored to the unique vulnerabilities and threats that web applications face.
- NGFW: Designed to provide comprehensive network-wide security. NGFWs protect against a wide range of threats, including malware, advanced persistent threats (APTs), unauthorized access, and insider threats.
2. Layer of Operation
- WAF: Exclusively operates at Layer 7 (application layer) of the OSI model. It inspects HTTP/S traffic and provides detailed protection for web application interactions.
- NGFW: Operates across multiple layers (Layers 3, 4, and 7). This multi-layer inspection allows NGFWs to detect and block threats that span different layers of the network.
3. Threat Coverage
- WAF: Specializes in protecting against web-specific vulnerabilities, such as those listed in the OWASP Top 10. It is particularly effective against SQL injection, XSS, CSRF, and other application-layer attacks.
- NGFW: Provides broader threat coverage, including malware detection, APT prevention, unauthorized access attempts, and insider threats. NGFWs leverage threat intelligence and real-time updates to stay ahead of emerging threats.
4. Traffic Type
- WAF: Primarily handles HTTP/S traffic, focusing on web application interactions. It is designed to filter and inspect web requests and responses to protect the application's logic and data.
- NGFW: Inspects all types of network traffic, including TCP/IP, UDP, and other protocols. This comprehensive traffic inspection allows NGFWs to detect and block threats across the entire network.
5. Integration and Scalability
- WAF: Often integrated with other web infrastructure components, such as load balancers and Content Delivery Networks (CDNs). This integration enhances performance and provides a holistic view of web application traffic.
- NGFW: Designed to integrate with a wide range security of solutions, including VPNs, endpoint protection, and cloud security services. NGFWs can scale to meet the needs of large enterprises and complex IT environments.
When to Use WAF vs NGFW
Choosing between a WAF and an NGFW depends on the specific security needs of an organization. Understanding their respective use cases can help make an informed decision.
WAF Use Cases
- E-commerce Platforms: E-commerce websites are prime targets for application-layer attacks due to their customer-facing nature and the sensitive data they handle. A WAF can protect against SQL injection, XSS, and other attacks that target user data and application logic.
- Customer-Facing Web Applications: Organizations that rely on web applications for customer interactions, such as banking, healthcare, and government services, benefit from the granular protection provided by WAFs. These applications often handle sensitive information and require compliance with industry regulations.
- SaaS Platforms: Software-as-a-Service providers need to ensure the security of their applications while maintaining high availability. WAFs can protect against DDoS attacks and application-layer threats, ensuring a secure and reliable service for their customers.
NGFW Use Cases
- Internal Network Protection: Enterprises with complex internal networks, including multiple locations and remote workers, require comprehensive security solutions. NGFWs provide multi-layer protection against a wide range of threats, ensuring the security of the entire network.
- Cloud Environments: Cloud-based infrastructures often face unique security challenges, including shared resources and multi-tenancy. NGFWs can be deployed in cloud environments to provide real-time threat detection and prevention, ensuring the security of cloud-based applications and data.
- Remote Work Setups: With the increasing prevalence of remote work, organizations need to secure their networks against threats that exploit remote access protocols and VPN connections. NGFWs can provide robust protection for remote work setups, ensuring that sensitive data remains secure.
Complementary Deployment
While WAFs and NGFWs serve different purposes, they can be deployed together to provide layered security. A WAF can protect web applications from application-layer threats, while an NGFW can provide comprehensive network-wide protection against a broader range of threats. This layered approach ensures that both web applications and the underlying network infrastructure are secure.
Practical Considerations and Best Practices
Selecting the right firewall solution requires careful consideration of organizational needs, existing security infrastructure, and future scalability. Here are some practical considerations and best practices for deploying WAFs and NGFWs:
- Assess Your Security Needs: Conduct a thorough risk assessment to identify the specific threats your organization faces. This will help determine whether a WAF, NGFW or a combination of both is necessary.
- Integrate with Existing Security Frameworks: Ensure that the chosen firewall solution integrates seamlessly with your existing security infrastructure. This includes compatibility with other security tools, centralized management consoles, and threat intelligence feeds.
- Implement Layered Security: Given the unique strengths of WAFs and NGFWs, consider deploying them in a layered security architecture. This approach ensures that multiple layers of defense are in place to protect against a wide range of threats. For example, an NGFW can provide broad network security, while a WAF offers specialized protection for web applications.
- Regularly Update and Patch: Both WAFs and NGFWs rely on up-to-date threat intelligence and software patches to remain effective. Regularly update the firewall firmware, threat signatures, and security policies to ensure they can detect and mitigate the latest threats.
- Monitor and Analyze Logs: Effective security requires continuous monitoring and analysis of firewall logs. Use Security Information and Event Management (SIEM) systems to aggregate and analyze logs from both WAFs and NGFWs. This will help identify potential security incidents, track threat trends, and optimize firewall rules for better performance and protection.
- Customize Security Policies: Avoid a one-size-fits-all approach to firewall rules. Customize security policies based on the specific needs of your applications and network. For example, a WAF protecting an e-commerce platform might have different rules compared to one protecting a government website. Similarly, an NGFW in a cloud environment may require different configurations than one in a traditional data center.
- Conduct Regular Penetration Testing: Regularly test your firewall defenses through penetration testing and vulnerability assessments. This helps identify weaknesses in your security posture and ensures that your WAF and NGFW are effectively blocking potential threats. Penetration testing should be conducted both internally and externally to cover all possible attack vectors.
- Educate and Train Staff: Cybersecurity is not just about technology; it also involves people. Ensure that your IT staff is well-trained in managing and configuring firewalls. Additionally, educate end-users about security best practices to reduce the risk of social engineering attacks and other human-related vulnerabilities.
- Plan for Scalability: As your organization grows, so will your security needs. Choose firewall solutions that can scale to accommodate increased traffic, additional applications, and expanding network infrastructure. This includes both hardware scalability and the ability to integrate with emerging technologies like cloud services and IoT devices.
- Leverage Automation and AI: Modern firewalls often come with advanced features like machine learning and AI-driven threat detection. Leverage these capabilities to automate routine security tasks, such as threat identification, anomaly detection, and policy enforcement. Automation can significantly enhance the effectiveness of your firewall while reducing the burden on your security team.
Conclusion
In the dynamic world of cybersecurity, both Web Application Firewalls (WAFs) and Next-Generation Firewalls (NGFWs) are essential tools for protecting digital assets. WAFs specialize in defending web applications against application-layer threats, while NGFWs offer comprehensive network-wide security against a broader range of threats. Deploying them together in a layered security strategy can significantly enhance an organization's security posture. Integrating these solutions with existing security frameworks and following best practices for management ensures robust defense against modern cyber threats. As technology advances, staying informed about the latest firewall developments is crucial for maintaining a secure digital environment.
EdgeOne is a prime example of a unified platform that combines WAF, DDoS protection, Bot management, and CDN acceleration capabilities. This integrated solution provides organizations with a comprehensive security framework that covers multiple aspects of their IT infrastructure. By combining these tools into a single platform, EdgeOne offers a more cohesive and effective approach to cybersecurity.
Sign up to start a free trial with us!
FAQs about WAF and NGFW
Q1: What is the primary difference between a WAF and an NGFW?
A1: The primary difference lies in their focus and scope. A Web Application Firewall (WAF) specializes in protecting web applications from application-layer threats such as SQL injection and XSS attacks, operating mainly at Layer 7 of the OSI model. In contrast, a Next-Generation Firewall (NGFW) provides comprehensive network-wide security across multiple layers (Layers 3, 4, and 7), protecting against a broader range of threats including malware, unauthorized access, and APTs.
Q2: When should I use a WAF instead of an NGFW?
A2: Use a WAF when you need to protect specific web applications from application-layer attacks. WAFs are ideal for e-commerce platforms, customer-facing web applications, and SaaS solutions where granular protection of web interactions is crucial. An NGFW, on the other hand, is best suited for comprehensive network security, especially in environments with multiple locations, remote workers, or complex IT infrastructures.
Q3: Can I use a WAF and an NGFW together?
A3: Yes, deploying both a WAF and an NGFW is highly recommended. This layered security approach leverages the strengths of both solutions to provide comprehensive protection. The WAF can protect web applications from specific threats, while the NGFW secures the entire network against a broader range of attacks. This combination creates a robust defense against modern cyber threats.
Q4: How do WAFs and NGFWs handle encrypted traffic?
A4: WAFs primarily focus on HTTP/S traffic and can decrypt SSL/TLS traffic to inspect web applications for interaction threats. NGFWs, however, are designed to handle all types of network traffic, including encrypted traffic. They can decrypt SSL/TLS traffic, inspect it for threats, and then re-encrypt it, ensuring that even encrypted communications are secure.
Q5: What are the key features of a WAF?
A5: Key features of a WAF include protection against application-layer attacks (e.g., SQL injection, XSS, CSRF), DDoS mitigation, compliance assistance (e.g., PCI DSS, GDPR), and zero-day exploit protection. WAFs also provide detailed logging and audit trails for security monitoring and incident response.
Q6: What are the key features of an NGFW?
A6: NGFWs offer multi-layer inspection (Layers 3-4 and 7), integrated Intrusion Prevention Systems (IPS), threat intelligence and real-time updates, SSL/TLS inspection, and comprehensive threat coverage against malware, APTs, and unauthorized access. They also support scalable deployment options for various environments, including physical, virtual, and cloud-based setups.
Q7: How do I choose the right firewall solution for my organization?
A7: The choice depends on your specific security needs. Conduct a risk assessment to identify the threats your organization faces. If your primary concern is web application security, a WAF may be sufficient. For broader network protection, consider an NGFW. In many cases, deploying both solutions together provides the most comprehensive security.
Q8: Are WAFs and NGFWs difficult to deploy and manage?
A8: Both WAFs and NGFWs can be complex to deploy and manage, especially in large or complex IT environments. However, modern solutions often come with user-friendly interfaces, automated features, and integration capabilities that simplify deployment and management. Training your IT staff and leveraging vendor support can also help ensure smooth implementation and ongoing maintenance.
Q9: How do WAFs and NGFWs fit into a larger cybersecurity strategy?
A9: WAFs and NGFWs are integral components of a comprehensive cybersecurity strategy. They work alongside other security tools such as SIEM systems, endpoint protection, and threat intelligence platforms to provide layered defense. By integrating these firewalls with existing security frameworks, organizations can achieve a holistic approach to protecting their digital assets.
Q10: What are the future trends in WAF and NGFW technology?
A10: Future trends in WAF and NGFW technology include increased automation and AI-driven threat detection, enhanced integration with cloud services and IoT devices, and improved scalability for hybrid environments. Staying informed about these advancements will help organizations maintain robust security as technology evolves.

