The digital era has transformed web applications into the backbone of modern business operations, social interactions, and information dissemination. However, this reliance on web technologies has also made them prime targets for cybercriminals. In 2025, the threat landscape has evolved significantly, with attackers leveraging sophisticated techniques to exploit vulnerabilities in web applications. The CIA triad—Confidentiality, Integrity, and Availability—remains a cornerstone of web security, guiding the development of robust defense mechanisms to protect sensitive data, ensure accurate information, and maintain service availability.
As web applications continue to grow in complexity, the need for comprehensive protection strategies has never been more critical. This article delves into advanced web protection techniques, exploring common attack vectors, core defense mechanisms, and future trends in web security. By understanding these elements, organizations can better safeguard their digital assets and maintain trust in an increasingly interconnected world.
What is Web Protection?
Web protection refers to the measures, tools, and technologies designed to safeguard users, data, and systems from various online threats while navigating the internet. It aims to protect against cyber threats such as malware, phishing scams, data breaches, and other malicious activities that could compromise the integrity and confidentiality of web-based information.
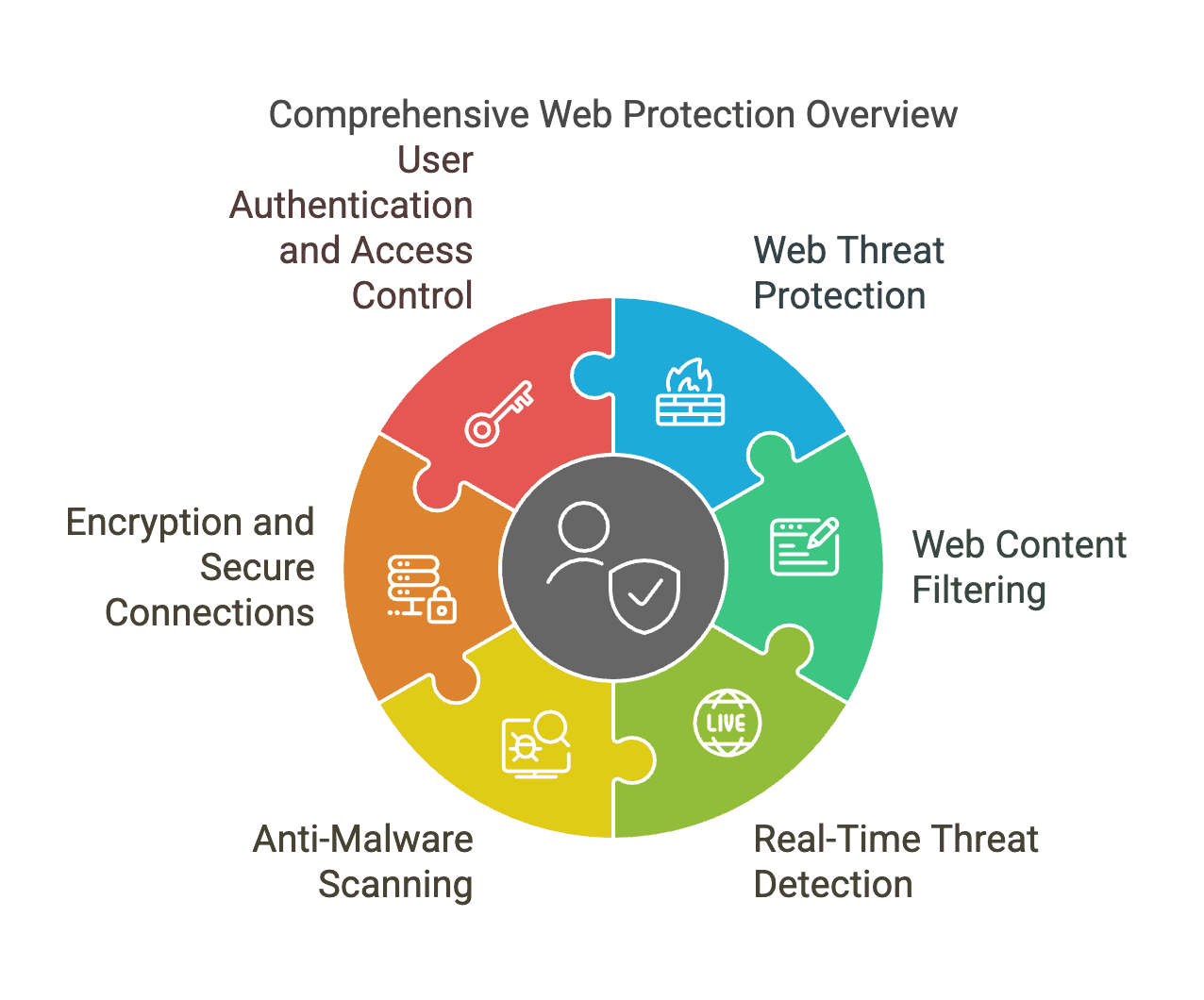
Key Components of Web Protection
- Web Threat Protection: This involves detecting and blocking malicious websites, downloads, and URLs to prevent users from accessing harmful content.
- Web Content Filtering: It allows organizations or individuals to control and restrict access to specific websites or content categories deemed inappropriate or potentially harmful.
- Real-Time Threat Detection: Advanced web protection solutions use real-time monitoring to identify and respond to potential security risks as they occur.
- Anti-Malware Scanning: This component scans websites, downloads, and files for known malware signatures or suspicious behavior to prevent infections.
- Encryption and Secure Connections: Web protection often includes encryption technologies like SSL/TLS to ensure that data transmitted over the web remains secure.
- User Authentication and Access Control: Implementing multi-factor authentication and other access control mechanisms helps verify user identities and restrict access to sensitive data.
Importance of Web Protection
- Keep Users Safe: Web protection helps prevent users from falling victim to online scams, phishing attempts, and cyberbullying, especially at home.
- Protect Sensitive Data: In the workplace, it safeguards against unauthorized access and data breaches, ensuring the confidentiality and integrity of valuable information.
- Improve Work Efficiency: By proactively identifying and blocking threats, web protection minimizes disruptions to business operations and enhances productivity.
Practical Solutions
- Regular Software Updates: Keeping software and security tools up to date is crucial for protecting against newly discovered vulnerabilities.
- Cybersecurity Training: Educating users about web threats and promoting cautious online behavior is fundamental in mitigating risks.
- Integrated Threat Intelligence: Modern web protection systems use threat intelligence to monitor and respond to globally recognized vulnerabilities and attack vectors.
In summary, web protection is essential for ensuring a safe and secure online experience, both for individuals and organizations.
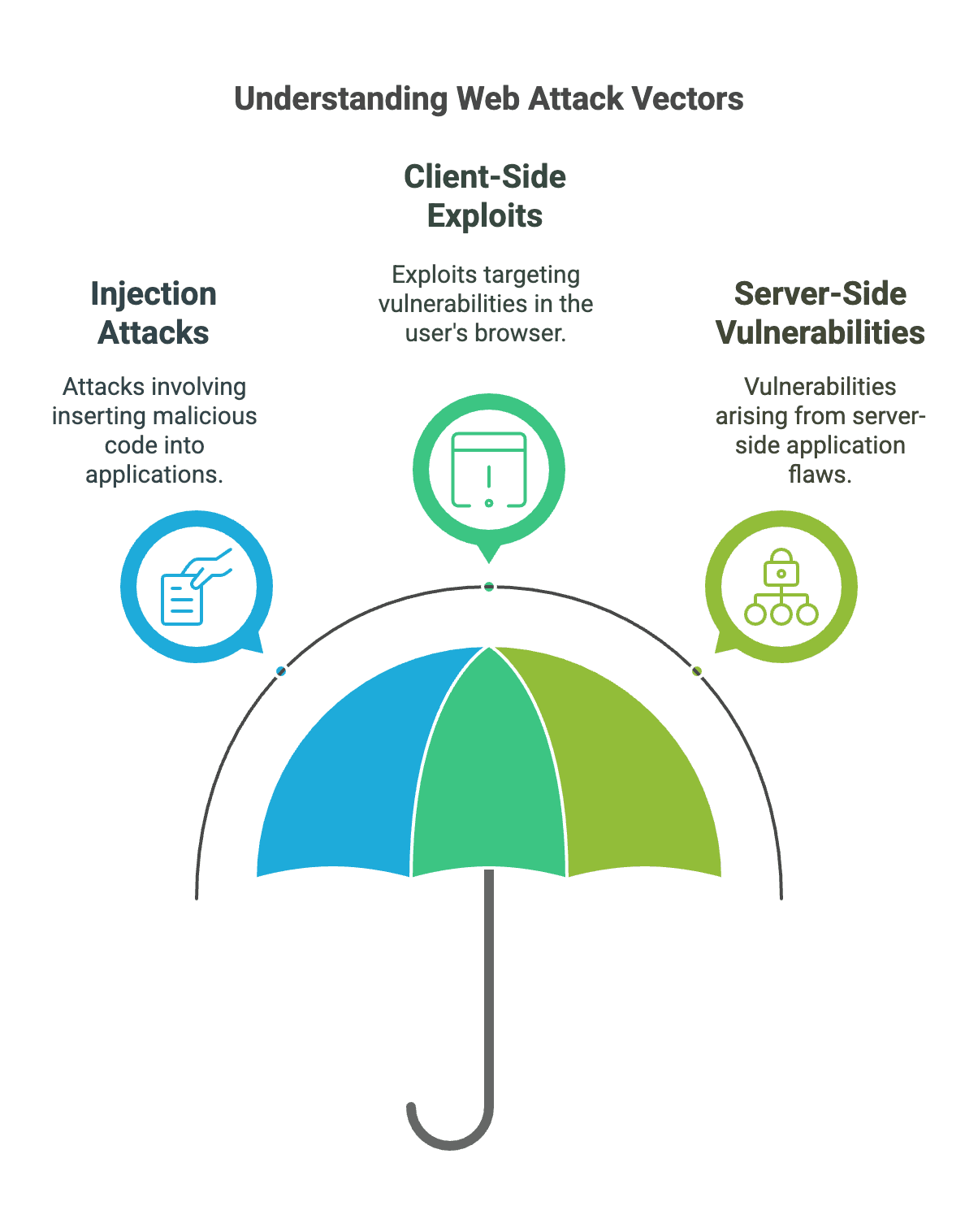
Common Web Attack Vectors
1. Injection Attacks
Injection attacks remain one of the most prevalent and dangerous threats to web applications. These attacks involve inserting malicious code into an application through user input fields, which are then executed by the application's backend systems.
SQL Injection
SQL Injection (SQLi) is a classic example of an injection attack. Attackers exploit vulnerabilities in web applications by tampering with SQL queries through user inputs, such as login forms or search boxes. For instance, an attacker might append a malicious SQL statement to a query, allowing them to bypass authentication, extract sensitive data, or modify the database.
Mitigation Strategies:
- Prepared Statements: The primary defense against SQLi is the use of prepared statements. These statements pre-compile SQL queries and bind parameters, ensuring that user input is treated as data rather than executable code. For example, in a Java application using JDBC, prepared statements can be implemented as follows:
String query = "SELECT * FROM users WHERE username = ? AND password = ?";
PreparedStatement stmt = connection.prepareStatement(query);
stmt.setString(1, username);
stmt.setString(2, password);
ResultSet results = stmt.executeQuery();- Stored Procedures: Another effective approach is to use stored procedures, which encapsulate SQL logic within the database. This reduces the risk of SQLi by isolating user input from SQL execution.
- Input Validation: Implementing strict input validation ensures that only expected data types and formats are accepted. For example, rejecting non-numeric input for a numeric field can prevent SQLi attempts.
Command Injection
Command Injection targets operating system-level vulnerabilities by injecting malicious commands into web applications. Attackers exploit input fields that are used to execute system commands, such as file uploads or shell commands.
Mitigation Strategies:
- Input Sanitization: Sanitizing user input is crucial for preventing command injection. This involves removing or escaping special characters that could be interpreted as commands. For example, in PHP, the
escapeshellcmd()function can be used to sanitize user input:
$userInput = escapeshellcmd($_POST['input']);
system($userInput);- Least Privilege Principle: Restricting the privileges of the web application's operating system account can limit the impact of a successful command injection attack. For instance, running the web server with minimal permissions can prevent attackers from executing critical system commands.
2. Client-Side Exploits
Client-side vulnerabilities exploit weaknesses in the user's browser or client-side code, often bypassing traditional security measures.
XSS (Cross-S Scriptiteing)
XSS attacks involve injecting malicious scripts into web pages viewed by other users. XSS can be categorized into three types: DOM-based, Reflected, and Stored.
- DOM-based XSS: This type of XSS occurs when the client-side script writes attacker-controlled data to the DOM. For example, an attacker might manipulate the
window.locationobject to inject malicious scripts. - Reflected XSS: Reflected XSS occurs when an attacker injects a script into the current page immediately after user interaction. For instance, an attacker might craft a malicious URL with a script, which is reflected in the page's response.
- Stored XSS: Stored XSS involves storing malicious scripts in a database or file, which are then executed when other users view the page. This type of XSS is particularly dangerous, as it can persist over time.
Mitigation Strategies:
- Content Security Policy (CSP): CSP is a powerful defense mechanism against XSS. It defines which sources of content are allowed to be executed on a webpage. For example, setting a CSP header like
Content-Security-Policy: script-src 'self';can prevent the execution of scripts from external sources. - Sanitization Libraries: Modern sanitization libraries, as such OWASP's AntiSamy or DOMPurify, can help filter out malicious scripts from user input. These libraries ensure that only safe HTML tags and attributes are allowed.
- Escaping Output: Always escape user input before rendering it on the page. For example, in JavaScript, you can use
htmlspecialchars()to escape special characters:
const userInput = htmlspecialchars(userInput);
document.getElementById('output').innerHTML = userInput;CSRF (Cross-Site Request Forgery)
CSRF attacks trick a user's browser into executing unwanted actions on a web application to which they are authenticated. For example, an attacker might embed a malicious link in an email that, when clicked, acts on the user's behalf.
Mitigation Strategies:
- Token-Based Validation: Implementing anti-CSRF tokens is a common defense. These tokens are unique values generated for each user session and included in forms or requests. The server validates the token before processing the request. For example, in a Django application, CSRF tokens can be included in forms as follows:
<form method="post">
{% csrf_token %}
<!-- Form fields -->
</form>- SameSite Cookie Attribute: The SameSite attribute for cookies ensures that cookies are only sent with requests originating from the same site. Setting
SameSite=LaxorSameSite=Strictcan prevent CSRF attacks by restricting cookie transmission across different sites.
3. Server-Side Vulnerabilities
Server-side vulnerabilities often stem from improper handling of file operations, data serialization, and authentication mechanisms.
File Inclusion (LFI/RFI)
File Inclusion vulnerabilities occur when an application includes files based on user input without proper validation. Local File Inclusion (LFI) allows attackers to access local files, while Remote File Inclusion (RFI) enables the inclusion of remote files, leading potentially to code execution.
Mitigation Strategies:
- Path Traversal Prevention: Implementing allowlists for file paths can prevent unauthorized file access. For example, restricting file inclusion to a predefined directory ensures that only authorized files are accessible.
- Input Validation: Strictly validating user input to ensure it conforms to expected patterns can prevent malicious file paths from being processed. For instance, rejecting input containing directory traversal sequences (
../) can mitigate LFI risks.
Insecure Deserialization
Insecure Deserialization occurs when an application deserializes untrusted data, potentially allowing attackers to execute arbitrary code. This vulnerability is particularly prevalent in REST APIs, where data is frequently serialized and deserialized.
Mitigation Strategies:
- Schema Validation: Validating the structure and content of serialized data against a predefined schema can prevent the deserialization of malicious data. For example, using JSON Schema validation ensures that only expected data formats are accepted.
- Restricting Deserialization: Limiting the types of objects that can be deserialized can reduce the attack surface. For instance, in Java, using libraries like Jackson with strict deserialization settings can prevent the instantiation of unauthorized classes.
Core Defense Mechanisms for Web Protection
Web Application Firewalls (WAF)
A Web Application Firewall (WAF) is a critical component of web security, designed to filter and monitor HTTP traffic between a web application and the internet. WAFs can detect and block common attack vectors, such as SQLi and XSS, by analyzing incoming requests and applying predefined rules.
Rule-Based Filtering vs. ML-Driven Anomaly Detection
- Rule-Based Filtering: Traditional WAFs rely on predefined rules to identify and block malicious traffic. These rules are based on known attack patterns and signatures. For example, a rule might block requests containing SQL keywords like
SELECTorDROP. - Machine Learning-Driven Anomaly Detection: Modern WAFs leverage machine learning algorithms to detect anomalies in traffic patterns. By analyzing normal behavior, these WAFs can identify deviations that may indicate an attack. For instance, an unusual spike in requests from a single IP address might trigger an alert.
The OWASP Top 10 is a widely recognized list of the most critical web application security risks. A well-configured WAF can effectively block these attacks in real-time. For example, a WAF can detect and block SQLi attempts by analyzing query patterns and rejecting suspicious input. Similarly, it can prevent XSS attacks by filtering out malicious scripts from incoming requests.
Secure Coding Practices
Secure coding practices are fundamental to preventing web application vulnerabilities. By integrating security into the development lifecycle, organizations can reduce the risk of exploitation.
Parameterized Queries for SQLi Prevention
As discussed earlier, parameterized queries are a cornerstone of SQLi prevention. By separating SQL logic from user input, developers can ensure that user data is treated as data rather than executable code. This approach not only prevents SQLi but also improves the overall security of database interactions.
Output Encoding Frameworks
Output encoding frameworks help prevent XSS attacks by converting special characters into harmless HTML entities. For example, the OWASP Java Encoder can be used to encode output in Java applications:
String encodedOutput = org.owasp.encoder.Encode.forHtml(userInput);Infrastructure Hardening
Hardening the underlying infrastructure is essential for maintaining web application security. This includes adopting modern encryption protocols and implementing access control mechanisms.
HTTPS/TLS 1.3 Adoption and HSTS Enforcement
HTTPS encrypts data transmitted between the client and server, preventing eavesdropping and tampering. Adopting the latest TLS 1.3 protocol ensures stronger encryption and improved performance. Additionally, enforcing HTTP Strict Transport Security (HSTS) ensures that browsers only interact with the server over HTTPS, reducing the risk of downgrade attacks.
Role-Based Access Control (RBAC) and Least-Privilege Principles
Implementing Role-Based Access Control (RBAC) restricts access to sensitive data and functionality based on user roles. The least-privilege principle ensures that users and applications have only the minimum permissions necessary to perform their tasks. For example, a web application might restrict database access to specific roles, reducing the risk of unauthorized data manipulation.
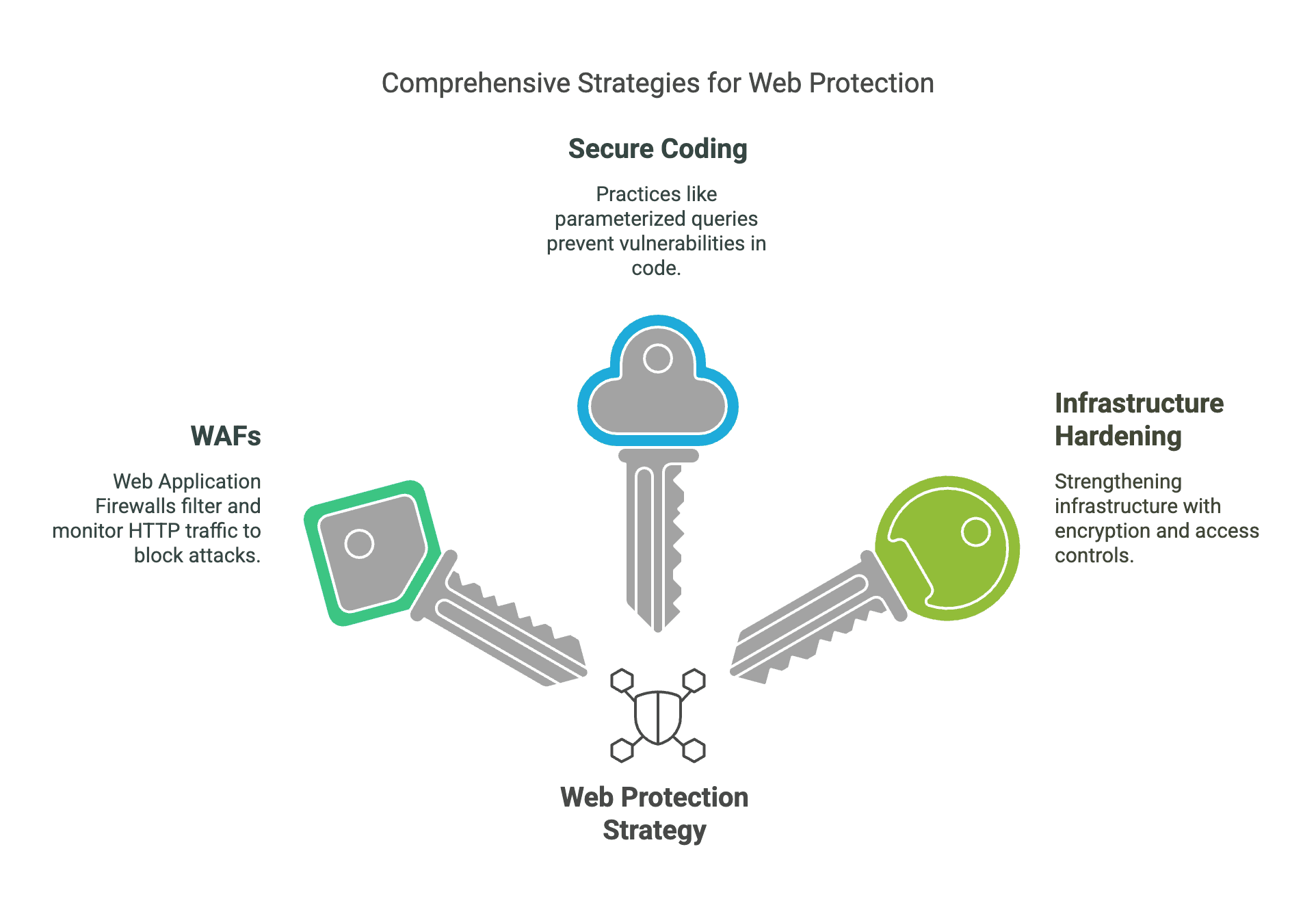
Advanced Web Protection Strategies
Proactive Threat Mitigation
Proactive threat mitigation involves identifying and addressing vulnerabilities before they can be exploited. This requires integrating advanced security tools and practices into the development and deployment lifecycle.
Runtime Application Self-Protection (RASP) Integration
RASP solutions provide real-time protection by embedding security controls within the application runtime environment. These controls can detect and block attacks as they occur, providing an additional layer of defense. For example, RASP can monitor API calls and block suspicious activity, such as attempts to exploit insecure deserialization vulnerabilities.
Automated Vulnerability Scanning with SAST/DAST Tools
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) tools are essential for identifying vulnerabilities during the development and testing phases. SAST tools analyze the source code for security flaws, while DAST tools test the running application for vulnerabilities. Integrating these tools into the CI/CD pipeline ensures that vulnerabilities are identified and remediated early in the development lifecycle.
Compliance and Monitoring
Compliance with data protection regulations and continuous monitoring are crucial for maintaining web application security. This involves implementing robust data encryption, audit trails, and attack pattern analysis.
GDPR/CCPA Alignment in Data Encryption and Audit Trails
The General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) require organizations to protect user data and maintain transparency in data processing. Implementing strong encryption for sensitive data and maintaining detailed audit trails can help organizations comply with these regulations. For example, using AES-256 encryption for data at rest and TLS for data in transit ensures that user data is protected from unauthorized access.
SIEM Systems for Attack Pattern Analysis
Security Information and Event Management (SIEM) systems collect and analyze security logs from various sources to detect and respond to attacks. By correlating events and identifying patterns, SIEM systems can provide real-time alerts and facilitate rapid response to security incidents. For example, a SIEM system might detect a series of failed login attempts and trigger an alert for potential brute-force attacks.
Future Trends of Web Protection
The future of web protection will be shaped by advancements in artificial intelligence, quantum-resistant cryptography, and decentralized identity systems. These emerging trends offer new opportunities for enhancing web security.
AI-Driven Attack Prediction and Quantum-Resistant Cryptography
Artificial Intelligence (AI) has the potential to revolutionize web security by predicting and preventing attacks before they occur. Machine learning algorithms can analyze vast amounts of data to identify emerging threats and adapt defenses accordingly. Additionally, the development of quantum-resistant cryptography is crucial as quantum computing becomes more prevalent. Quantum-resistant algorithms, such as lattice-based cryptography, can ensure that encryption remains secure even in the face of quantum computing advancements.
Decentralized Identity Systems
Decentralized identity systems, such as blockchain-based authentication, offer a new approach to managing digital identities. By leveraging blockchain technology, these systems can provide secure, tamper-proof identity verification. For example, a blockchain-based identity system can ensure that user credentials are stored securely and verified without relying on a central authority.
EdgeOne Web Protection: Next-Gen Security at the Edge
EdgeOne Web Protection is a cloud-native security solution that integrates enterprise-grade web application protection with global edge computing infrastructure and integrates AI algorithms to enhance web security and performance. Designed for modern cyber threats, it provides multi-layered defense through:
- AI-Powered Threat Detection: EdgeOne employs an AI engine that leverages Tencent's extensive threat information database, which contains over 100 million records. This AI engine serves as a smarter threat recognition kernel, capable of accurately identifying and blocking web threats such as SQL injection, XSS attacks, and local file inclusion.
- Bot Behavior Analysis: The platform integrates AI technology to analyze and model user request behaviors comprehensively. This feature intelligently identifies abnormal traffic and differentiates between legitimate and malicious bots. It supports custom session protection policies to further enhance security.
- Rate-Limiting and CC Attack Protection: EdgeOne's AI-driven rate-limiting technology uses adaptive algorithms to detect and mitigate CC attacks. It analyzes traffic patterns in real-time and applies custom rules to filter out malicious requests, ensuring stable service performance.
- Edge AI Computing: EdgeOne is designed to support edge AI computing, allowing lightweight AI models to be deployed at the edge nodes. This capability enables real-time decision-making and reduces latency by processing data closer to the user. It is particularly useful for applications requiring rapid response, such as traffic monitoring and smart manufacturing.
- Smart Web Protection: By combining AI algorithms with Tencent's vast web attack sample library, EdgeOne matches request characteristics to identify and block malicious activities. This AI-driven approach ensures that web applications are protected in real-time against evolving threats.
EdgeOne Web Protection is designed to empower enterprises with robust, next-generation security at the edge, ensuring that digital assets remain protected against even the most sophisticated threats. Now we have launched a free trial for a quick start, Sign In to join us!
Conclusion
In 2025, the hyperconnected nature of web ecosystems demands a balanced approach to security that prioritizes both usability and protection. By adopting comprehensive web protection strategies, organizations can mitigate evolving cyber threats and maintain trust in their digital services. The integration of DevSecOps pipelines is essential for embedding security into the development lifecycle, ensuring that web applications are secure from inception to deployment.
As the threat landscape continues to evolve, staying ahead requires a proactive and adaptive approach to web security. By leveraging advanced defense mechanisms, embracing emerging trends, and fostering a culture of security awareness, organizations can build resilient web applications that withstand the challenges of the modern digital age.
FAQs about Web Protection
1. What is web protection?
Web protection refers to the measures and technologies used to safeguard websites, web applications, and online services from various threats, such as hacking, malware, data breaches, and unauthorized access. It includes security tools, practices, and strategies to ensure the confidentiality, integrity, and availability of web-based assets.
2. Why is web protection important?
Web protection is crucial because websites and web applications often store sensitive information, such as personal data, financial details, and business secrets. Without proper protection, this information can be compromised, leading to financial losses, reputational damage, and legal issues. Additionally, web protection helps maintain the trust of users and customers, ensuring a secure and reliable online experience.
3. What are the common web threats that need protection?
Some common web threats include:
- Malware and viruses: Malicious software that can infect websites and steal data.
- SQL injection: An attack that exploits vulnerabilities in a website's database to inject malicious SQL code.
- Cross-site scripting (XSS): An attack that allows attackers to inject malicious scripts into web pages viewed by other users.
- Phishing: Fraudulent attempts to obtain sensitive information by masquerading as a trustworthy entity.
- DDoS attacks: Distributed Denial of Service attacks that overwhelm a website with traffic, causing it to crash.
- Data breaches: Unauthorized access to sensitive data stored on web servers.
4. How can I protect my website from attacks?
To protect your website, you can take several steps:
- Use HTTPS: Encrypt data transmitted between your website and users to prevent eavesdropping and tampering.
- Implement firewalls: Web Application Firewalls (WAFs) can detect and block malicious traffic.
- Regularly update software: Keep your web server, content management system (CMS), and plugins up to date to patch vulnerabilities.
- Use strong authentication: Require strong passwords and consider multi-factor authentication (MFA) for accessing your website's backend.
- Perform regular security audits: Conduct vulnerability scans and penetration testing to identify and fix weaknesses.
- Backup data: Regularly back up your website's data to recover quickly in case of an attack or data loss.
5. What is a Web Application Firewall (WAF), and how does it work?
A Web Application Firewall (WAF) is a security tool that filters, monitors and blocks malicious traffic to and from a web application. It acts as a barrier between the internet and your web server, analyzing HTTP traffic and applying predefined security rules to identify and mitigate threats such as SQL injection, XSS, and DDoS attacks. WAFs can be deployed on-premises or as a cloud service and are essential for protecting web applications from common vulnerabilities.
6. How can I protect my website from DDoS attacks?
To protect your website from DDoS attacks:
- Use a Content Delivery Network (CDN): CDNs can distribute traffic across multiple servers, making it harder for attackers to overwhelm your website.
- Implement rate limiting: Restrict the number of requests a user can make within a certain timeframe to prevent abuse.
- Deploy a DDoS protection service: Many cloud providers and security companies offer DDoS mitigation services that can detect and absorb large-scale attacks.
- Configure your firewall: Set up rules to block suspicious traffic patterns and IP addresses associated with DDoS attacks.
7. What role does user education play in web protection?
User education is vital in web protection because many security breaches result from human error or lack of awareness. Educating users about safe online practices, such as recognizing phishing emails, using strong passwords, and avoiding suspicious links, can significantly reduce the risk of security incidents. Training employees and customers on security best practices is an essential part of a comprehensive web protection strategy.
8. How can I ensure the security of third-party plugins and integrations?
Third-party plugins and integrations can introduce vulnerabilities to your website. To ensure their security:
- Choose reputable providers: Only use plugins and integrations from well-known and trusted sources.
- Keep them updated: Regularly update third-party components to patch known vulnerabilities.
- Review permissions: Ensure that plugins and integrations have only the necessary permissions and access to your website's data.
- Monitor for changes: Keep an eye on the security reputation of third-party providers and remove any components that become compromised or unsupported.
9. What are some best practices for securing e-commerce websites?
E-commerce websites handle sensitive financial information, so security is paramount. Some best practices include:
- PCI compliance: Ensure your website meets Payment Card Industry Data Security Standards (PCI DSS) to protect cardholder data.
- Tokenization and encryption: Use tokenization to replace sensitive data with non-sensitive equivalents and encrypt data both in transit and at rest.
- Secure checkout processes: Implement secure payment gateways and use HTTPS throughout the checkout process.
- Regular security audits: Conduct frequent vulnerability scans and penetration tests to identify and fix security issues.
- Monitor for fraud: Use fraud detection tools to identify and prevent suspicious transactions.
10. How can I recover from a web security breach?
If your website experiences a security breach, take the following steps:
- Isolate the affected systems: Disconnect compromised servers or systems from the network to prevent further damage.
- Investigate the breach: Determine the scope of the breach, identify the vulnerabilities exploited, and understand how data was compromised.
- Notify affected parties: Inform users, customers, and relevant authorities about the breach and guide what actions they should take.
- Patch vulnerabilities: Fix the security weaknesses that led to the breach and apply updates to prevent future attacks.
- Restore from backups: Use recent backups to restore your website and data to a secure state.
- Review and improve security: Conduct a thorough review of your security measures and implement additional protections to enhance your web protection strategy.

