In today's increasingly digital world, web applications and API interfaces have become critical components of modern enterprise operations. However, the growing prevalence of cyber threats has made securing these applications and interfaces a significant challenge. Web Application and API Protection (WAAP) has emerged as a comprehensive security solution.
What is WAAP?
Web Application and API Protection (WAAP) is a security approach that focuses on safeguarding web applications and APIs (Application Programming Interfaces) from various threats and cyberattacks. As web applications and APIs have become critical components of modern online services, ensuring their security has become a priority for organizations.
WAAP typically involves a combination of security solutions, best practices, and technologies to protect web applications and APIs from threats such as:
- Injection attacks (e.g., SQL injection, cross-site scripting)
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks
- Unauthorized access and data breaches
- Session hijacking and man-in-the-middle attacks
- API abuse and misuse
With the increasing number of cyber-attacks targeting web applications and API interfaces, WAAP has become an essential tool for enterprises to protect their business operations and data security. WAAP helps enterprises identify and mitigate various cyber threats, ensuring the stable operation of their web applications and API interfaces.
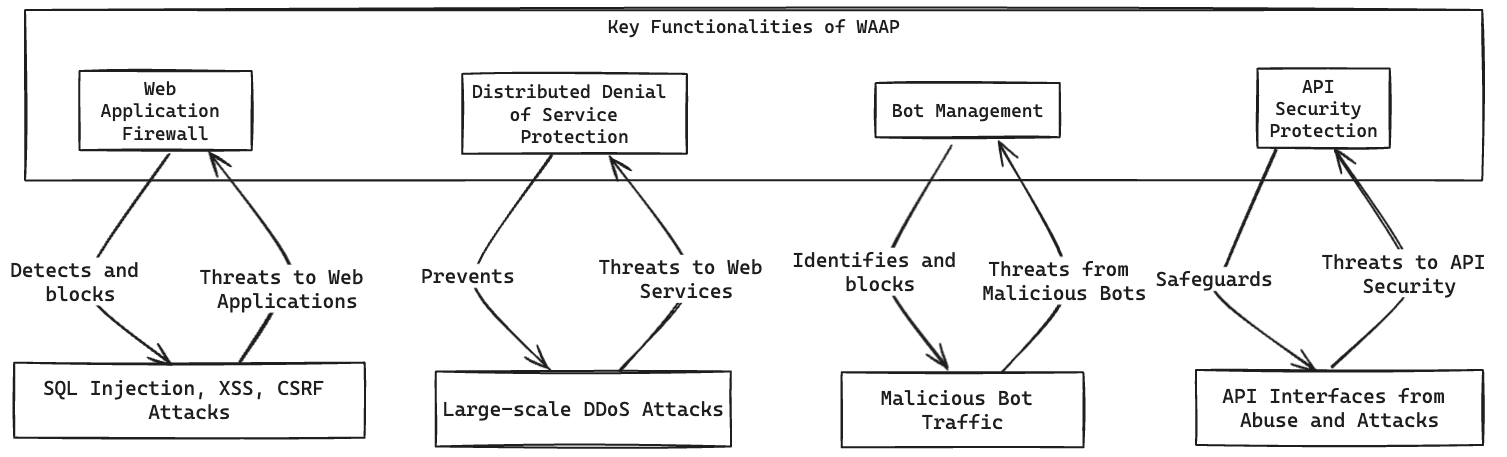
What are the Key Functionalities of WAAP?
WAAP offers several key functionalities to protect web applications and API interfaces from various cyber threats. These functionalities include:
- Web Application Firewalls (WAF): The WAF, the core component of WAAP, is responsible for detecting and blocking attacks targeting web applications, such as SQL injection, XSS, and CSRF. It analyzes HTTP/HTTPS traffic to identify and block malicious requests, safeguarding web applications.
- Distributed Denial of Service (DDoS) Protection: DDoS protection, a crucial component of WAAP, is designed to prevent large-scale DDoS attacks. Through globally distributed scrubbing centers and intelligent traffic scheduling technology, DDoS protection can effectively mitigate malicious traffic, ensuring the stable operation of web applications and API interfaces.
- Bot Management: Bot management functions to identify and block malicious bot traffic, preventing data scraping, account hijacking, and other automated attacks. Through behavioral analysis and fingerprint recognition, bot management can distinguish between legitimate users and malicious bots, ensuring service security.
- API Security Protection: API security protection aims to safeguard API interfaces from abuse and attacks. Through mechanisms such as authentication, access control, rate limiting, and traffic control, API security protection ensures that only legitimate users can access API interfaces, preventing data breaches and other security threats.
WAAP vs WAF
WAAP (Web Application and API Protection) and WAF (Web Application Firewall) are both security solutions aimed at protecting web applications from various cyber threats. While they share some similarities, there are key differences between the two.
WAAP (Web Application and API Protection)
- WAAP is a more comprehensive security solution that focuses on protecting both web applications and APIs (Application Programming Interfaces) from a wide range of threats.
- WAAP typically includes a WAF as a component, along with other security features such as API security, DDoS protection, bot mitigation, and threat intelligence.
- It is designed to address the increasing complexity of modern web applications and APIs, which often involve multiple components, microservices, and third-party integrations.
- WAAP provides a holistic approach to web application and API security, offering protection against a wider range of threats, including DDoS attacks, SQL injection, cross-site scripting (XSS), and more.
- WAAP solutions may also include advanced features such as machine learning and artificial intelligence to detect and block sophisticated attacks that traditional WAFs might miss.
WAF (Web Application Firewall)
- WAF is a specific type of security solution that focuses on protecting web applications from common threats such as SQL injection, cross-site scripting (XSS), and other OWASP Top Ten vulnerabilities.
- WAF operates by monitoring and filtering incoming HTTP/HTTPS traffic, applying a set of predefined rules to block or allow specific requests.
- WAFs can be deployed as a standalone solution or as part of a broader security infrastructure, such as an intrusion prevention system (IPS) or a next-generation firewall (NGFW).
- While WAFs offer protection against many common web application threats, they may not be as effective in addressing the unique security challenges posed by APIs or complex, distributed applications.
- WAFs typically rely on signature-based detection and predefined rules, which may not be sufficient to detect and block more advanced or targeted attacks.
In summary, while both WAAP and WAF aim to protect web applications from cyber threats, WAAP provides a more comprehensive and holistic approach to security, covering both web applications and APIs. WAF is a component of WAAP and focuses on protecting web applications from common threats. Organizations should consider their specific needs and the complexity of their web applications and APIs when deciding between WAAP and WAF solutions.
Case Studies and Applications of WAAP
Case studies and applications of WAAP (Web Application and API Protection) demonstrate how organizations can benefit from implementing this comprehensive security solution to protect their web applications and APIs from various cyber threats. Here are a few examples:
- E-commerce Company: An e-commerce company faced severe DDoS attacks, causing its website to go down frequently. After deploying WAAP, the company successfully mitigated the attacks, ensuring the stable operation of its website and improving customer satisfaction.
- Social Media Platform: A social media platform suffered from a bot-driven spam campaign, leading to a significant drop in user engagement. WAAP's bot management functionality helped the platform identify and block malicious bot traffic, restoring user engagement and improving platform security.
- Financial Institution: A financial institution experienced multiple data breaches due to unauthorized API access. By implementing WAAP's API security protection, the institution strengthened its API defenses, preventing further data breaches and safeguarding sensitive customer information.
- Online Gaming Platform: An online gaming platform was being targeted by cybercriminals using DDoS attacks to disrupt services and exploit vulnerabilities in the platform's web application and APIs. By deploying a WAAP solution, the gaming platform was able to mitigate DDoS attacks and protect its web applications and APIs from threats such as SQL injection and cross-site scripting (XSS). The WAAP solution also provided bot mitigation, preventing cheaters from using automated scripts to gain an unfair advantage in the games.
These case studies highlight the importance of implementing comprehensive security solutions like WAAP to protect web applications and APIs from various cyber threats. By leveraging WAAP, organizations can ensure the security and availability of their online services, maintain customer trust, and comply with industry regulations.
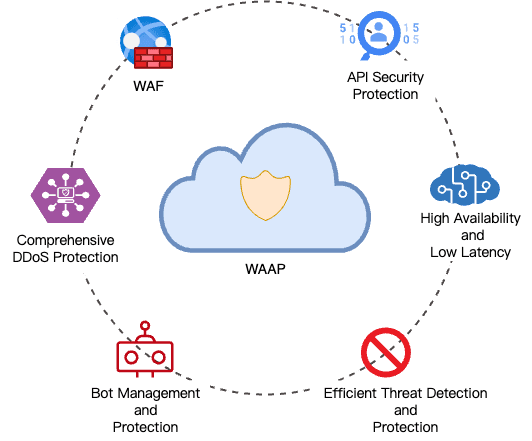
Benefits of Tencent EdgeOne
Web Application and API Protection (WAAP) serves as a comprehensive security solution, effectively countering various cyber threats and protecting web applications and API interfaces. The WAAP functionalities within Tencent EdgeOne products combine multiple advanced technical advantages, providing comprehensive web application and API protection. Through efficient threat detection and protection, comprehensive DDoS protection, bot management and protection, API security protection, high availability and low latency, and compliance and security certification, EdgeOne effectively safeguards enterprises' core business and data security. As technology continues to advance, EdgeOne will play an increasingly important role in future cybersecurity protection.
Tencent EdgeOne offers the following advantages:
- Efficient Threat Detection and Protection: EdgeOne utilizes advanced threat detection technologies to identify and block various complex web attacks in real-time. Its threat detection mechanisms include signature-based detection, behavioral analysis, and machine learning, ensuring the ability to counter evolving attack methods.
- Comprehensive DDoS Protection: EdgeOne not only provides WAF functionalities but also integrates robust DDoS protection capabilities. Through globally distributed scrubbing centers and intelligent traffic scheduling technology, EdgeOne can effectively mitigate large-scale DDoS attacks, ensuring the stable operation of web applications and API interfaces.
- Bot Management and Protection: EdgeOne features advanced bot management functionalities, capable of identifying and blocking malicious bot traffic, preventing data scraping, account hijacking, and other automated attacks.
- API Security Protection: EdgeOne offers comprehensive API security protection, preventing API abuse, data breaches, and other security threats. Through authentication, access control, rate limiting, and traffic control mechanisms, EdgeOne ensures that only legitimate users can access API interfaces.
- High Availability and Low Latency: EdgeOne provides high availability and low latency security protection services through globally distributed edge nodes and intelligent routing technology. Users can enjoy fast and stable access experiences regardless of their location.
- Compliance and Security Certification: EdgeOne complies with various international and industry security standards, helping enterprises meet compliance requirements and reduce compliance risks. By providing detailed logs and reports, EdgeOne assists enterprises in conducting security audits and compliance checks.
You are welcome to Contact Us for more information.

