In today's interconnected digital landscape, web protection has emerged as a paramount concern for organizations of all sizes. As cyber threats continue to evolve and become more sophisticated, the need for robust security measures has never been more critical. Enter the Open Web Application Security Project (OWASP), a beacon in the cybersecurity world that has been guiding both beginners and seasoned professionals through the murky waters of web application security for over two decades. Among OWASP’s most valuable contributions is the OWASP Top 10 list, a comprehensive guide that pinpoints the most critical security risks facing web applications today.

What is OWASP?
OWASP, founded in 2001, is a nonprofit foundation dedicated to improving the security of software through its community-led open-source software projects. With hundreds of chapters worldwide, tens of thousands of members, and leading educational and training conferences, OWASP has established itself as a cornerstone in the cybersecurity community.
The organization's mission is to make software security visible, so that individuals and organizations can make informed decisions about true software security risks. By providing impartial, practical, and freely available information on application security, OWASP empowers developers, security professionals, and organizations to create and maintain secure software applications.
OWASP's contributions to the field of cybersecurity are numerous and varied, including:
- Open-source security tools and libraries
- Comprehensive security documentation and best practices
- Local chapters for networking and knowledge sharing
- Global conferences and events
- Security standards and guidelines
What is the OWASP Top 10?
The OWASP Top 10 is a regularly updated report outlining the ten most critical web application security risks. This list serves as a powerful awareness document for web application security, identifying some of the most crucial risks facing organizations. The Top 10 project is based on a broad consensus among security experts worldwide, making it an authoritative source of information for organizations looking to secure their web applications.
The primary goals of the OWASP Top 10 are to:
- Educate developers, designers, architects, and organizations about the consequences of the most common web application security weaknesses
- Provide basic techniques to protect against these high-risk problem areas
- Provide guidance on where to go for further information on application security
By focusing on the most critical risks, the OWASP Top 10 helps organizations prioritize their security efforts, ensuring that resources are allocated to address the most pressing vulnerabilities first.
The Latest OWASP Top 10 (2021)
The most recent iteration of the OWASP Top 10 was released in 2021, reflecting the evolving landscape of web application security. Let's dive deep into each of these vulnerabilities, understanding what they are, why they're dangerous, and how to mitigate them. The OWASP Top 10 is typically updated every few years, with the next update expected in early 2025.
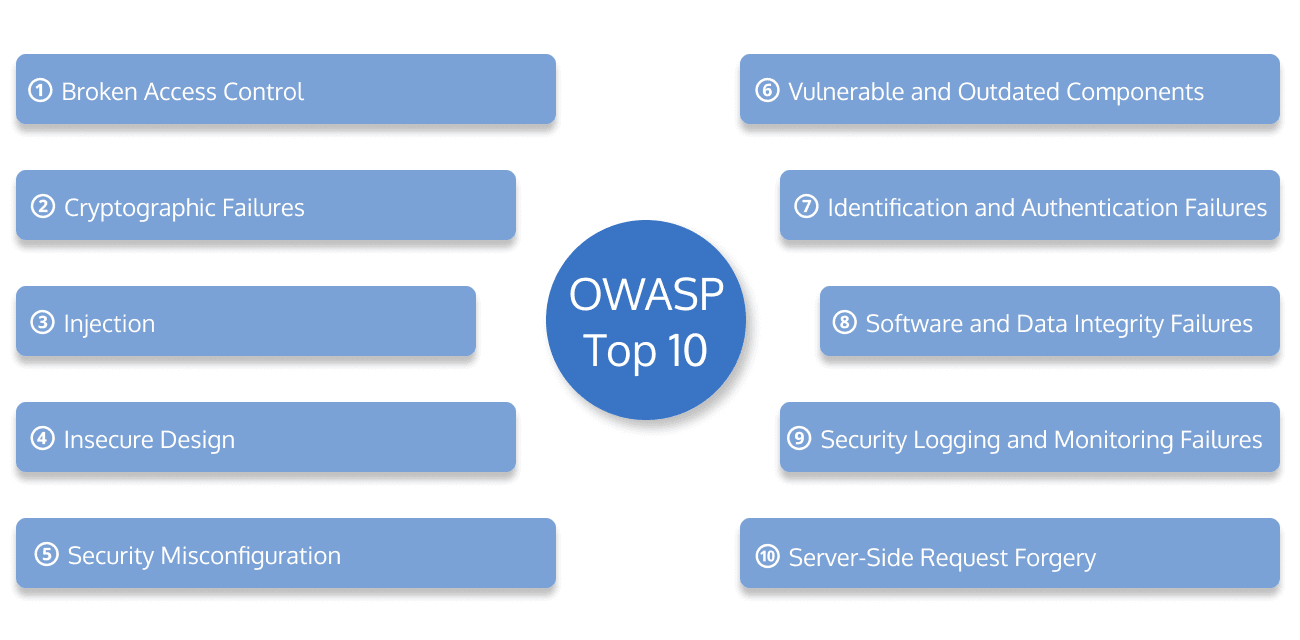
1. Broken Access Control
Climbing from the fifth position in 2017 to the top spot in 2021, Broken Access Control has become the most critical web application security risk. This vulnerability occurs when users can act beyond their intended permissions, potentially leading to unauthorized information disclosure, modification, or destruction of data.
Examples of broken access control include:
- Modifying a URL parameter to access another user's account
- Bypassing access checks by modifying the web browser's state
- Elevating privileges to those of an administrator
To mitigate this risk, developers should implement robust access control mechanisms, including:
- Enforcing principle of least privilege
- Implementing proper session management
- Conducting thorough testing of access control mechanisms
2. Cryptographic Failures
Previously known as "Sensitive Data Exposure," this category emphasizes failures related to cryptography that often lead to sensitive data exposure. This risk underscores the importance of properly implementing encryption and other cryptographic practices to protect sensitive information.
Common cryptographic failures include:
- Using weak cryptographic algorithms
- Improper implementation of strong algorithms
- Inadequate key management
To address this risk:
- Use strong, up-to-date cryptographic algorithms
- Implement proper key management practices
- Encrypt all sensitive data in transit and at rest
3. Injection
Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker's hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
Injection attacks can lead to:
- Data theft, modification, or destruction
- Loss of data integrity
- Denial of service
- Complete system takeover
Prevention measures include:
- Using parameterized queries
- Input validation and sanitization
- Adopting Object Relational Mapping (ORM) tools
4. Insecure Design
A new addition to the OWASP Top 10, Insecure Design focuses on risks related to design and architectural flaws. This category emphasizes the need to shift left in the software development lifecycle, incorporating security by design principles from the outset.
Insecure design can manifest as:
- Missing or ineffective control design
- Business logic flaws
- Inadequate threat modeling
To improve design security:
- Implement secure development lifecycle practices
- Use threat modeling in the design phase
- Conduct regular security architecture reviews
5. Security Misconfiguration
Security misconfiguration remains a prevalent issue, often resulting from insecure default configurations, incomplete or ad hoc configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information.
Common misconfigurations include:
- Unnecessary features enabled or installed
- Default accounts with unchanged passwords
- Overly informative error messages
Mitigation strategies:
- Implement a repeatable hardening process
- Review and update configurations regularly
- Maintain a minimal platform without unnecessary features
6. Vulnerable and Outdated Components
Components such as libraries, frameworks, and other software modules often run with full privileges. If a vulnerable component is exploited, it can facilitate serious data loss or server takeover.
Risks associated with vulnerable components:
- Known vulnerabilities in widely used components
- Lack of support for older versions
- Difficulty in tracking component versions
To address this risk:
- Maintain an inventory of all components
- Monitor sources like CVE and NVD for vulnerabilities
- Implement a patch management process
7. Identification and Authentication Failures
Previously known as "Broken Authentication," this category includes weaknesses in session management, credential management, and other aspects of establishing and maintaining user identity.
Common failures include:
- Permitting weak passwords
- Poorly implemented multi-factor authentication
- Session fixation attacks
Best practices for robust authentication:
- Implement multi-factor authentication
- Limit or delay failed login attempts
- Use secure session management techniques
8. Software and Data Integrity Failures
This new category focuses on making assumptions related to software updates, critical data, and CI/CD pipelines without verifying integrity. It includes insecure deserialization, which can lead to remote code execution attacks.
Integrity failures can result in:
- Unauthorized code execution
- Data tampering
- Supply chain attacks
Mitigation strategies:
- Use digital signatures to verify software integrity
- Ensure libraries and dependencies are from trusted sources
- Implement integrity checks for critical data
9. Security Logging and Monitoring Failures
Insufficient logging and ineffective integration with incident response can allow attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data.
Consequences of inadequate logging and monitoring:
- Delayed breach detection
- Inability to conduct proper forensic analysis
- Increased impact of successful attacks
To improve logging and monitoring:
- Implement centralized log management
- Ensure logs capture sufficient detail without including sensitive data
- Regularly review and analyze logs for suspicious activity
10. Server-Side Request Forgery (SSRF)
SSRF flaws occur when a web application is fetching a remote resource without validating the user-supplied URL. This can allow attackers to coerce the application to send a crafted request to an unexpected destination, even when protected by a firewall, VPN, or another type of network access control list (ACL).
SSRF can lead to:
- Data exfiltration
- Internal system compromise
- Lateral movement within internal networks
To prevent SSRF:
- Sanitize and validate all client-supplied input data
- Enforce the URL schema, port, and destination with a positive allow list
- Disable HTTP redirections
Purpose and Importance of OWASP Top 10
The OWASP Top 10 serves as a crucial resource for organizations, developers, and security professionals. It helps prioritize security efforts by focusing on the most critical risks facing web applications. By addressing these top risks, organizations can significantly improve their overall security posture and protect against a wide range of potential attacks.
The OWASP Top 10 is not just a list of vulnerabilities but a comprehensive guide that includes:
- Detailed descriptions of each risk
- Example attack scenarios
- Guidance on how to prevent these vulnerabilities
- References to OWASP and other resources for further learning
Conclusion
The OWASP Top 10 is an invaluable resource for anyone involved in the web application lifecycle, from development to deployment and maintenance. By staying informed about the most critical security risks and adopting the recommended preventative measures, we can fortify our digital infrastructures against potential attacks. As cybersecurity threats continue to evolve, the OWASP Top 10 will remain an essential guide in our collective effort to create a safer online world.
FAQs
Q1: How often is the OWASP Top 10 updated?
A1: The OWASP Top 10 is updated approximately every three years, with the latest version released in 2021.
Q2: How can I use the OWASP Top 10 for my organization?
A2: Organizations can use the OWASP Top 10 as a starting point for conducting security risk assessments, prioritizing the mitigation of identified vulnerabilities, and integrating secure coding practices into the software development lifecycle.
Q3: Is the OWASP Top 10 only applicable to web applications?
A3: While primarily focused on web applications, the principles and practices recommended in the OWASP Top 10 can be applied to other types of software and technologies to improve overall security posture.
Q4: Where can I find more information on mitigating these risks?
A4: The OWASP Top 10 report provides detailed descriptions of each risk, including examples, incidence rates, and guidance on prevention. Additionally, OWASP offers a wealth of resources on its website, including cheat sheets, tools, and further documentation to help mitigate these vulnerabilities.
About Us
Tencent EdgeOne provides a robust Web Protection service, effectively blocking a variety of threats. With an extensive attack feature library covering key security issues identified in the OWASP Top 10, it mitigates risks from web attacks, exploitation of vulnerabilities, trojans, backdoors, and other security issues. We have now launched a Free Trial, welcome to Sign Up or Contact Us for more information.

