In the ever-evolving cybersecurity landscape, firewalls have emerged as a cornerstone of network protection. From their humble beginnings as simple packet filters to their current iteration as sophisticated next-generation firewalls (NGFWs), firewalls have continuously adapted to meet the growing complexity of modern threats. This article aims to provide a comprehensive overview of the various types of firewalls, their historical evolution, real-world applications, and future trends. By the end of this guide, readers will have a holistic understanding of how firewalls shape modern cybersecurity and why they remain indispensable in protecting digital assets.
What is a Firewall?
A firewall is a network security device or software that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between internal networks (trusted environments) and external networks (untrusted environments, such as the Internet) to prevent unauthorized access and protect against malicious activities. Firewalls are essential components of modern cybersecurity infrastructure, providing a critical layer of defense against a wide range of cyber threats.
Key Functions of a Firewall
- Traffic Filtering: Firewalls examine network traffic and filter it based on specific criteria, such as IP addresses, port numbers, protocols, and application data. They can allow or block traffic based on predefined rules to ensure that only legitimate and safe data passes through.
- Access Control: Firewalls enforce access control policies to restrict unauthorized access to internal networks and resources. They can differentiate between trusted and untrusted sources of traffic and apply appropriate security measures to each.
- Threat Detection and Prevention: Modern firewalls, such as Next-Generation Firewalls (NGFWs), integrate advanced threat detection capabilities, including intrusion prevention systems (IPS) and deep packet inspection (DPI). These features help identify and block sophisticated threats like malware, phishing attacks, and application-layer attacks.
- Logging and Monitoring: Firewalls generate logs and provide monitoring capabilities to track network traffic and detect suspicious activities. Security teams can use these logs to investigate incidents, identify potential threats, and improve security policies.
- Network Segmentation: Firewalls can segment networks into smaller, isolated zones (microsegmentation) to limit the spread of threats within the network. This approach ensures that even if one part of the network is compromised, the rest of the network remains protected.
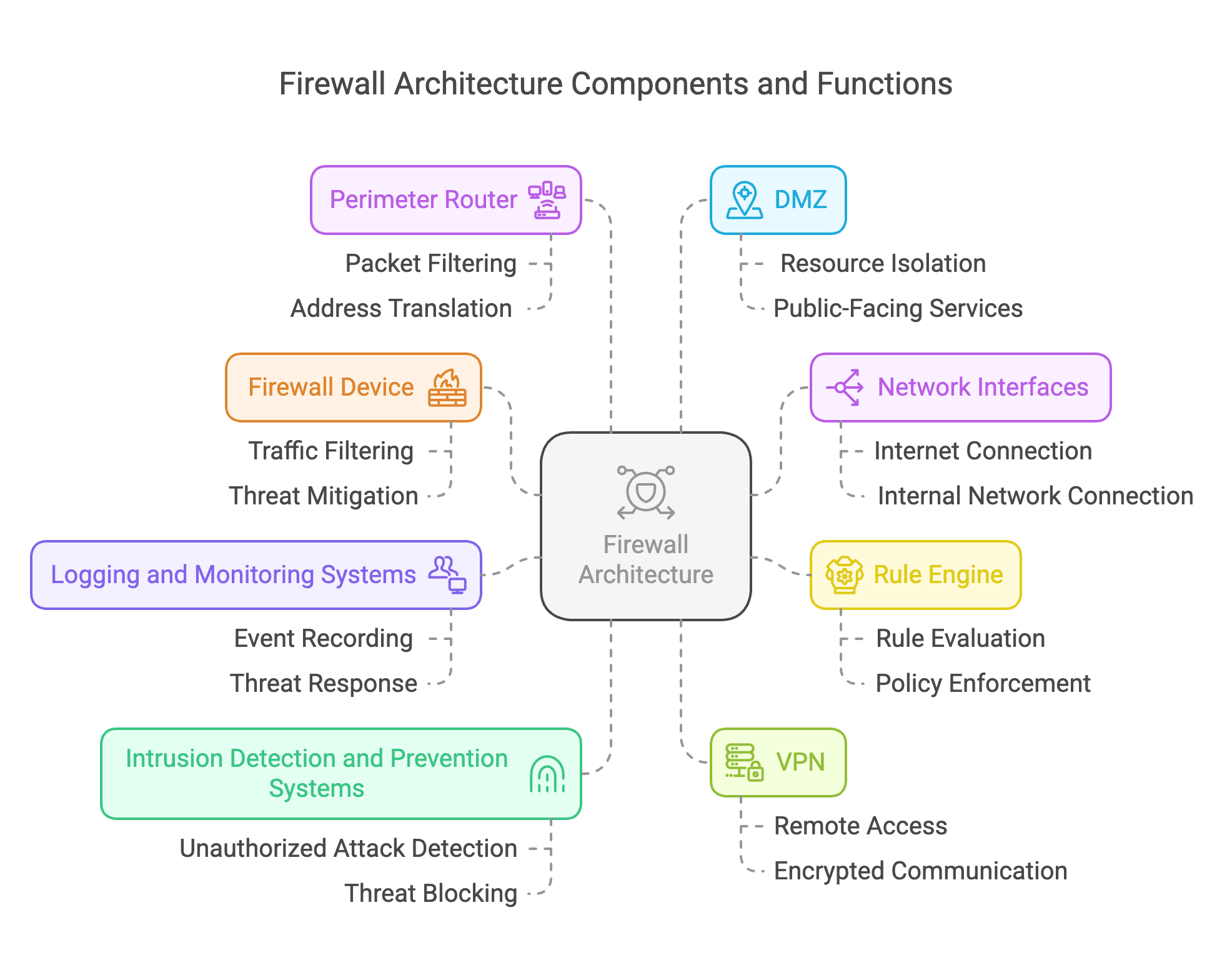
Key Components of Firewall Architecture
The key components of a firewall architecture work together to ensure network security by controlling and monitoring traffic flow. Here are the main components:
1. Firewall Device
The firewall device is the core component that acts as a barrier between internal networks and external threats. It filters and inspects network traffic based on predefined security rules. Modern firewalls often include advanced features such as intrusion prevention systems (IPS) and deep packet inspection (DPI) to detect and mitigate sophisticated threats.
2. Network Interfaces
Network interfaces are the gateways that connect the firewall to different network segments, such as the Internet, internal networks, and demilitarized zones (DMZs). They ensure that traffic is directed to the appropriate destinations and facilitate the transmission of packets.
3. Rule Engine
The rule engine defines the behavior of the firewall. It consists of a set of rules that specify which traffic should be allowed or denied based on criteria such as source IP addresses, destination ports, and protocol types. These rules are evaluated sequentially to enforce security policies.
4. Logging and Monitoring Systems
Logging and monitoring systems provide visibility into the firewall’s activities. They record and analyze events such as connection attempts, rule matches, and security breaches. This enables administrators to identify and respond to potential threats effectively.
5. Intrusion Detection and Prevention Systems (IDS/IPS)
IDS and IPS are advanced components that enhance firewall capabilities. IDS detects unauthorized attacks and suspicious activities, while IPS takes proactive measures to block or mitigate these threats.
6. Virtual Private Network (VPN)
VPN components provide secure connections between networks or devices. They ensure encrypted communication, allowing remote access to the internal network while maintaining security.
7. Perimeter Router
The perimeter router connects the internal network to the external network (e.g., the internet). It performs packet filtering and address translation, providing an additional layer of security.
8. Demilitarized Zone (DMZ)
In some firewall architectures, a DMZ is established as a buffer zone between the internal network and the external network. It isolates critical internal resources from potential threats while allowing controlled access to public-facing services.
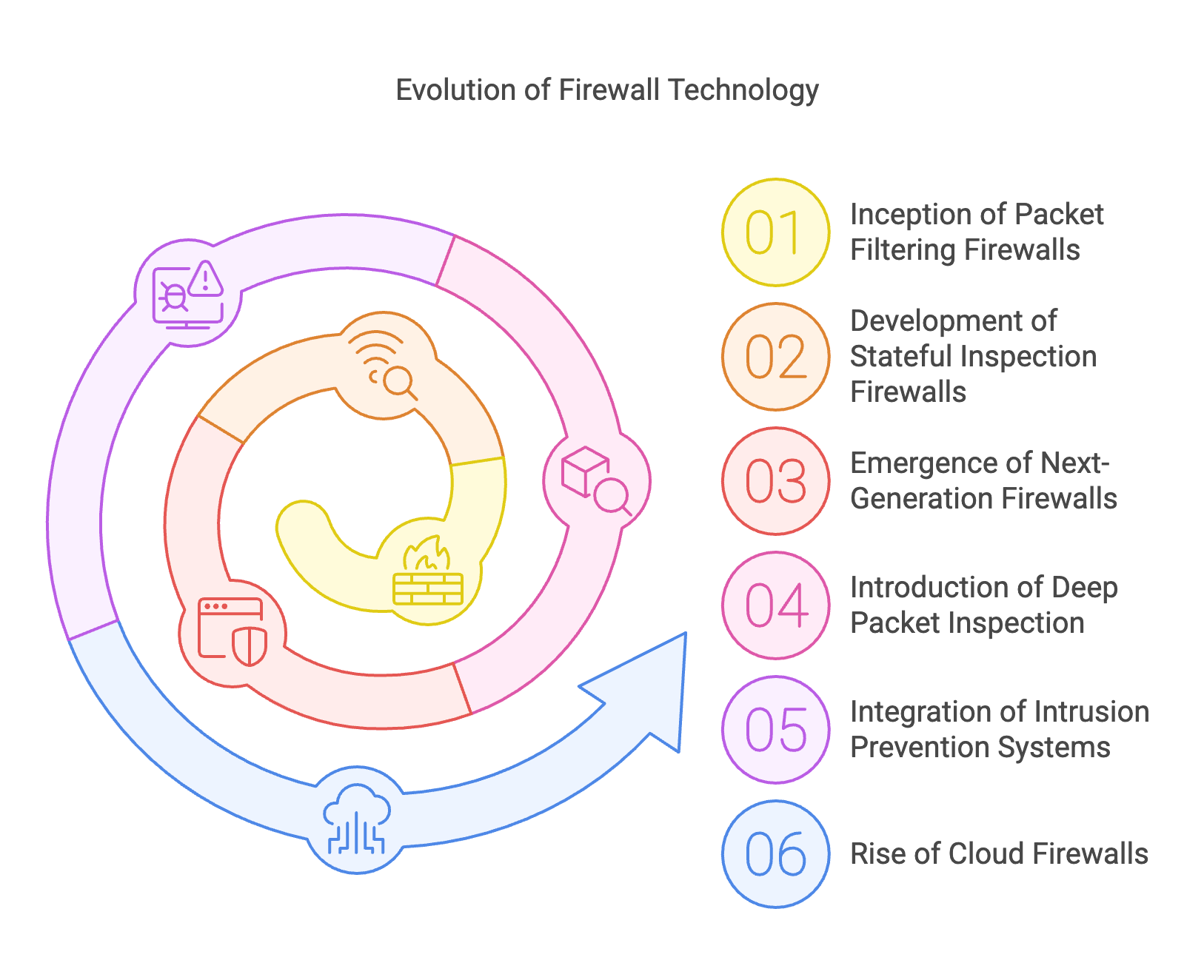
Historical Evolution of Firewalls
Early Firewalls: Packet Filtering and Stateful Inspection
Firewalls have come a long way since their inception in the late 1980s. The first generation of firewalls relied on packet filtering, a method that examines individual data packets based on predefined rules. These rules typically included source and destination IP addresses, port numbers, and protocols. Packet filtering firewalls were simple and efficient but could not understand the context of network traffic, making them vulnerable to more sophisticated attacks.
The next significant advancement was stateful inspection firewalls, which appeared in the early 1990s. Unlike their predecessors, stateful firewalls could track the state of active connections, allowing them to make more informed decisions about incoming and outgoing traffic. By analyzing the context of each packet, stateful inspection firewalls provided a more robust defense against unauthorized access and malicious activities. This technology laid the foundation for modern firewall capabilities.
Advancements Leading to Next-Generation Firewalls (NGFW)
As cyber threats became more complex, traditional firewalls struggled to keep pace. The advent of next-generation firewalls (NGFWs) marked a significant leap forward. NGFWs integrate multiple advanced security features, including deep packet inspection, intrusion prevention systems (IPS), and application awareness. These capabilities enable NGFWs to identify and block sophisticated threats, such as advanced malware and application-layer attacks, which traditional firewalls could not detect.
One of the key innovations in NGFWs is their ability to perform deep packet inspection (DPI). Unlike basic packet filtering, DPI examines the contents of each packet, allowing the firewall to identify and block malicious activities hidden within seemingly benign traffic. Additionally, NGFWs integrate IPS to detect and prevent intrusions in real-time, providing a more proactive defense against cyber threats.
The Role of Firewalls in the Age of Cloud Computing
The rise of cloud computing has transformed the way organizations deploy and manage their IT infrastructure. Traditional firewalls, designed for on-premises networks, often fall short in protecting cloud environments. This challenge led to the development of cloud firewalls and firewall-as-a-service (FWaaS) solutions. These cloud-native firewalls leverage the scalability and flexibility of cloud computing to provide comprehensive security for cloud-based applications and data.
Types of Firewalls: A Detailed Overview
1. Traditional Firewalls: Foundational Architectures
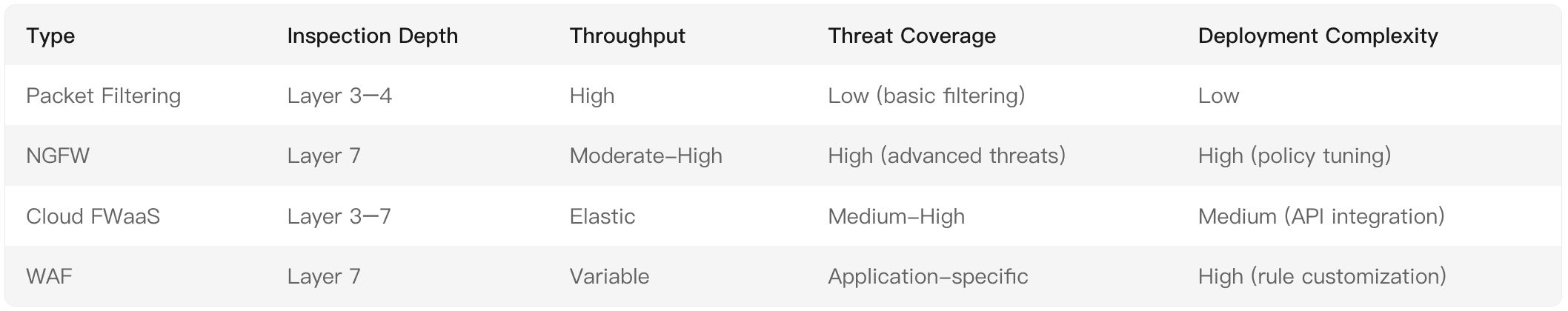
1.1 Packet Filtering Firewalls
- Operational Layer: Network Layer (Layer 3) and Transport Layer (Layer 4) of the OSI model.
- Mechanism: Stateless inspection of packet headers (source/destination IP, port, protocol) against predefined ACLs (Access Control Lists).
- Use Case: Basic perimeter defense in legacy networks.
- Limitations:
- No session awareness (vulnerable to IP spoofing and ACK scan attacks).
- Inability to inspect payloads or detect application-layer threats.
1.2 Stateful Inspection Firewalls
- Core Innovation: Maintains a state table tracking active connections' lifecycle (SYN, SYN-ACK, FIN).
- Capabilities:
- Context-aware filtering (e.g., allowing response packets only to established sessions).
- Mitigates TCP flood attacks via session timeout configurations.
- Enterprise Example: Cisco ASA (Adaptive Security Appliance) in legacy deployments.
1.3 Proxy Firewalls (Application-Level Gateways)
- Architecture: Acts as an intermediary, terminating client connections and initiating new outbound sessions.
- Security Value:
- Full application-layer protocol validation (e.g., HTTP RFC compliance).
- Content filtering (blocking malicious MIME types) and user authentication.
- Performance Trade-off: High latency due to deep inspection; rarely used for high-throughput networks.
2. Next-Generation Firewalls (NGFW): The Modern Standard
2.1 Definition & Core Features
NGFWs integrate traditional firewall capabilities with advanced functionalities:
- Deep Packet Inspection (DPI): Full stack analysis (Layers 2–7) to detect protocol anomalies.
- Application Identification: Signature-based and behavioral analysis (e.g., distinguishing Facebook chat from standard HTTP).
- Threat Intelligence Integration: Automated IOC (Indicators of Compromise) updates from platforms like MITRE ATT&CK.
- SSL/TLS Decryption: In-line decryption for encrypted traffic inspection (requires certificate management).
2.2 Use Cases
- Zero-Day Protection: Sandboxing integration to detonate suspicious files.
- Policy Granularity: Rules based on user identity (AD/LDAP integration), not just IP addresses.
- Vendor Example: Palo Alto Networks' PAN-OS with App-ID and User-ID features.
3. Specialized Firewall Types for Modern Architecture
3.1 Web Application Firewalls (WAF)
- Focus: Layer 7 protection for HTTP/HTTPS applications.
- Detection Methods:
- Positive security model (allowlisting known good request patterns).
- Negative security model (blocking OWASP Top 10 threats like SQLi, XSS).
- Deployment: Reverse proxy mode (cloud-based: AWS WAF, Azure WAF) or network-based hardware.
3.2 Cloud Firewalls (FWaaS)
- Architecture: Scalable, API-driven security for distributed cloud environments (AWS Security Groups, Azure NSG).
- Key Features:
- Microsegmentation for east-west traffic control.
- Integration with CSPM (Cloud Security Posture Management) tools.
3.3 Internal Segmentation Firewalls
- Purpose: Restrict lateral movement post-breach (Zero Trust alignment).
- Implementation: Software-defined perimeters (e.g., Illumio) or VLAN-aware NGFWs.
4. Emerging Firewall Technologies
4.1 AI-Powered Firewalls
- ML Applications:
- Anomaly detection via unsupervised learning (e.g., Darktrace's Enterprise Immune System).
- Predictive threat scoring based on historical data.
4.2 Container & Kubernetes Firewalls
- Runtime Protection: Enforce network policies via CNI plugins (e.g., Cilium, Calico).
- Compliance: CIS benchmarks for orchestrated environments.
4.3 IoT-Specific Firewalls
- Protocol Support: MQTT, CoAP, and Zigbee inspection.
- Lightweight Agents: Deployed on edge gateways for resource-constrained devices.
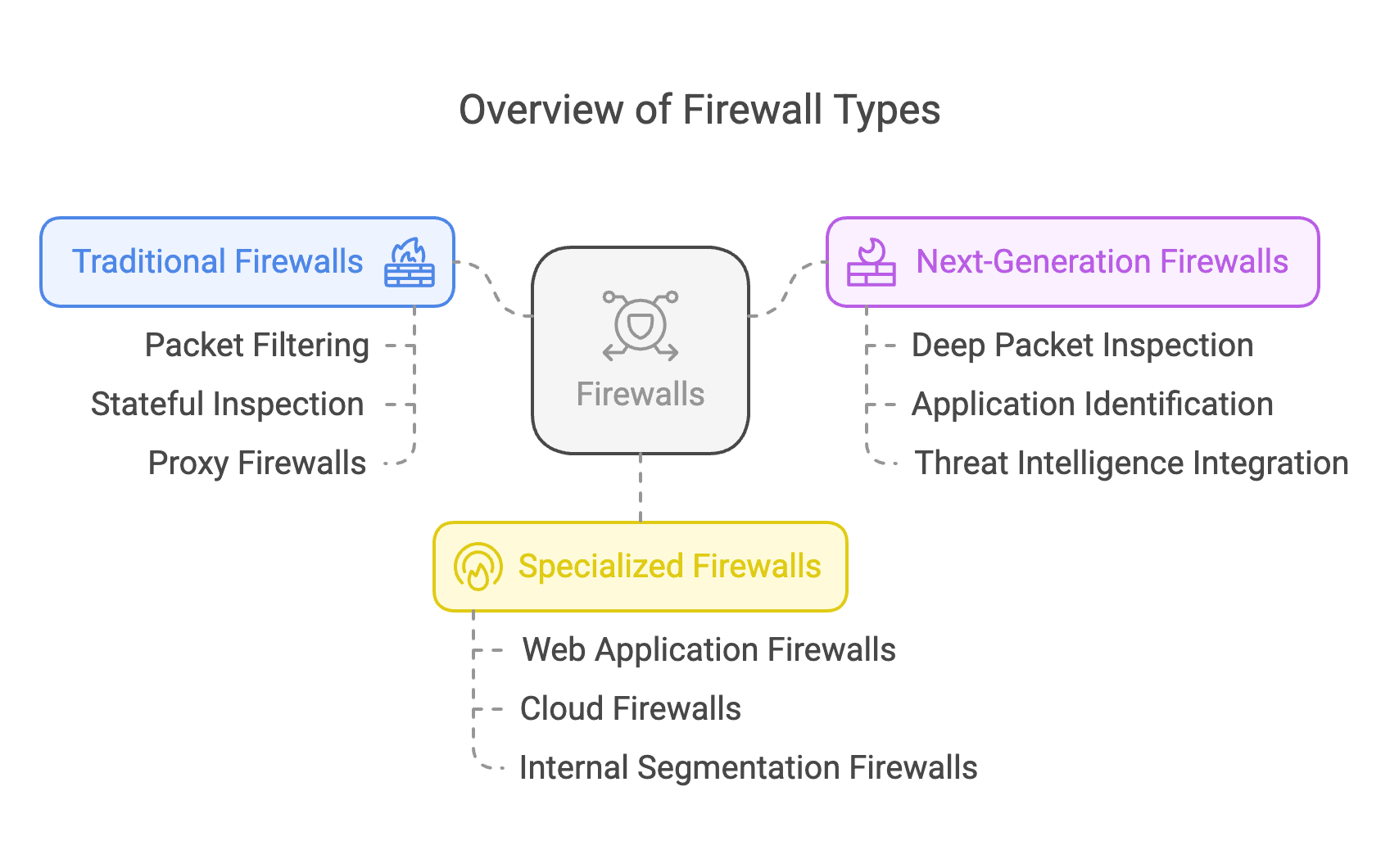
Modern firewalls have evolved from static packet filters to dynamic, context-aware systems integrated with threat intelligence and cloud ecosystems. Enterprises must adopt a layered defense strategy, combining NGFWs for perimeter/internal security, WAFs for application protection, and AI-driven solutions for adaptive threat response. As networks grow more heterogeneous, firewall architectures will increasingly emphasize automation, API-driven orchestration, and cross-platform visibility.
Industry-Specific Firewall Requirements
Financial Services
The financial industry is highly regulated and faces significant threats from cybercriminals targeting sensitive financial data. Firewalls in this sector must comply with regulations such as the Payment Card Industry Data Security Standard (PCI-DSS) and the Gramm-Leach-Bliley Act (GLBA). Financial institutions require robust next-generation firewalls (NGFWs) with advanced threat detection and prevention capabilities to protect against sophisticated attacks. Additionally, they often deploy Web Application Firewalls (WAFs) to secure online banking platforms and other web-based applications.
Healthcare
Healthcare organizations must comply with the Health Insurance Portability and Accountability Act (HIPAA) to protect patient data. Firewalls in the healthcare sector need to provide comprehensive protection for both on-premises and cloud-based environments, ensuring that sensitive patient information remains secure. Web Application Firewalls (WAFs) are particularly important for protecting electronic health records (EHR) systems and other web-based applications. Additionally, healthcare organizations often use container firewalls to secure containerized medical applications and data.
Government and Public Sector
Government agencies face unique challenges in protecting national security and sensitive government data. Firewalls in this sector must comply with stringent regulations such as the Federal Information Security Modernization Act (FISMA). Government agencies often deploy advanced next-generation firewalls (NGFWs) with deep packet inspection and intrusion prevention capabilities. They also use internal firewalls to segment their networks and prevent the spread of threats within the organization. Additionally, government agencies leverage cloud firewalls and firewall-as-a-service (FWaaS) solutions to secure their growing cloud-based infrastructure.
E-commerce and Retail
E-commerce and retail companies face frequent attacks targeting their web applications and online platforms. These organizations require robust Web Application Firewalls (WAFs) to protect against application-layer threats such as SQL injection and cross-site scripting. They also deploy next-generation firewalls (NGFWs) to provide comprehensive protection for their network infrastructure. Additionally, e-commerce companies often use cloud firewalls to secure their cloud-based applications and data, ensuring that customer information remains protected.
Manufacturing and IoT
The manufacturing industry increasingly relies on Internet of Things (IoT) devices to optimize production processes. These devices introduce new security challenges, as they often lack robust security features. Firewalls in the manufacturing sector must provide comprehensive protection for both traditional IT infrastructure and IoT devices. They often deploy next-generation firewalls (NGFWs) with advanced threat detection capabilities and use distributed firewalls to segment their networks and contain potential threats. Additionally, manufacturing companies leverage container firewalls to secure containerized IoT applications and data.
Choosing the Right Firewall for Your Organization
Selecting the right firewall for your organization requires a thorough understanding of your network architecture, assets, and security needs. Here are some key considerations to help guide your decision:
Assessing Network Architecture and Assets
Begin by evaluating your organization's network architecture and identifying the assets that require protection. Consider the types of devices and applications in use, as well as the data they handle. Determine whether your network is primarily on-premises, cloud-based, or hybrid, as this will influence your firewall requirements.
Evaluating Security Needs and Budget Constraints
Assess your organization's security needs based on the types of threats you face and the regulatory requirements you must comply with. Consider the level of protection required for your network and applications, as well as the budget available for firewall deployment and management. Balancing security needs with budget constraints is crucial to ensure that you select a firewall solution that meets your organization's requirements without breaking the bank.
Integration with Existing Infrastructure
Evaluate how well the firewall solution integrates with your existing IT infrastructure. Ensure that the firewall can work seamlessly with your current network devices, security systems, and management tools. Compatibility and ease of integration are essential for minimizing deployment time and reducing the risk of security gaps.
Compliance and Regulatory Considerations
Consider the regulatory requirements that apply to your industry, such as GDPR, HIPAA, or PCI-DSS. Ensure that the firewall solution you select complies with these regulations and provides the necessary features to meet your compliance obligations. Compliance is critical for avoiding fines and maintaining customer trust.
Future Trends in Firewall Technology
Artificial Intelligence and Machine Learning in Firewalls
The future of firewalls lies in the integration of artificial intelligence (AI) and machine learning (ML) technologies. AI-powered firewalls can analyze vast amounts of data to detect and respond to threats in real time. They can also learn from past incidents to improve their detection capabilities over time. This proactive approach to threat detection and prevention will become increasingly important as cyber threats continue to evolve.
Zero Trust Architecture and Firewalls
Zero Trust architecture is gaining traction as a security model that assumes no user or device should be trusted by default. Firewalls will play a crucial role in implementing Zero Trust principles by continuously verifying the identity and security posture of users and devices. This approach ensures that only authorized and secure connections are established, reducing the risk of unauthorized access and lateral movement within the network.
The Impact of 5G and IoT on Firewall Deployment
The widespread adoption of 5G and the Internet of Things (IoT) will introduce new challenges for firewall deployment. 5G networks offer faster speeds and lower latency, but they also increase the attack surface for cyber threats. Firewalls will need to adapt to secure the growing number of IoT devices and ensure that sensitive data remains protected in a 5G-enabled world. This will require advanced capabilities such as micro-segmentation and distributed firewall architectures to effectively manage and secure IoT traffic.
Predictive Analytics and Threat Intelligence Integration
Future firewalls will increasingly rely on predictive analytics and threat intelligence to stay ahead of emerging threats. By integrating real-time threat intelligence feeds, firewalls can proactively block known malicious activities and adapt to new threats as they emerge. Predictive analytics will also enable firewalls to anticipate potential attacks based on historical data and behavioral patterns, providing a more proactive defense against cyber threats.
Conclusion
Firewalls have come a long way since their inception, evolving from simple packet filters to sophisticated next-generation firewalls capable of detecting and blocking advanced threats. As technology continues to advance, firewalls will remain a cornerstone of network security, adapting to meet the challenges of modern cyber threats. By understanding the various types of firewalls, their historical evolution, and future trends, organizations can make informed decisions about selecting the right firewall solution to protect their digital assets.
EdgeOne offers comprehensive security advantages by integrating advanced security features with edge computing capabilities. It provides robust Web Protection, Bot Management, and DDoS protection, effectively mitigating large-scale traffic attacks to ensure service availability. The built-in Web Application Firewall (WAF) defends against common web threats like SQL injection, XSS, and CSRF, safeguarding web applications from malicious requests. Additionally, EdgeOne's intelligent traffic scheduling and edge caching mechanisms optimize content delivery while reducing latency, ensuring a seamless user experience. By combining security and acceleration in a single platform, EdgeOne simplifies management and enhances overall network resilience.
Sign Up to begin your journey with us!
FAQs about Firewalls
1. What is a firewall?
A firewall is a security system that monitors and controls incoming and outgoing network traffic based on predefined security rules. It acts as a barrier between internal networks (trusted environments) and external networks (such as the internet) to prevent unauthorized access while allowing legitimate traffic to pass through.
2. Why do I need a firewall?
A firewall is essential for protecting your network from unauthorized access, malware, hacking attempts, and other cyber threats. It also helps ensure compliance with regulatory standards (e.g., GDPR, HIPAA) and improves network performance by filtering out unwanted traffic.
3. How does a firewall work?
A firewall works by filtering network traffic according to a set of security rules. These rules define which traffic is allowed to pass through and which traffic should be blocked. Firewalls can operate at different layers of the network, such as the network layer (packet filtering) or the application layer (deep packet inspection).
4. What are the different types of firewalls?
There are several types of firewalls, including:
- Network Firewalls: Protect entire networks by filtering traffic at the perimeter.
- Host-Based Firewalls: Installed on individual devices to provide an additional layer of security.
- Next-Generation Firewalls (NGFW): Offer advanced features like deep packet inspection, application control, and integrated intrusion prevention.
- Unified Threat Management (UTM) Firewalls: Combine multiple security functions (firewall, antivirus, IPS) into a single device.
- Firewall as a Service (FWaaS): Cloud-based firewalls that provide centralized management and scalability.
5. What is the difference between a hardware firewall and a software firewall?
- Hardware Firewall: A physical device dedicated to network security, often used in larger organizations for high performance and scalability.
- Software Firewall: Installed on individual devices (computers, servers) to provide additional security. Suitable for small businesses and home networks.
6. Can a firewall protect against all types of cyber threats?
No, a firewall cannot protect against all types of cyber threats. While it is effective at blocking unauthorized access and filtering traffic, it may not protect against advanced threats like phishing, zero-day exploits, or insider attacks. A comprehensive security strategy that includes antivirus software, intrusion detection systems, and employee training is essential.
7. What is a stateful firewall?
A stateful firewall monitors the state of active network connections and uses this information to make more informed decisions about which traffic to allow or block. Unlike stateless firewalls, stateful firewalls can detect and block malicious activities that span multiple packets or sessions.
8. What is a next-generation firewall (NGFW)?
An NGFW is an advanced type of firewall that goes beyond traditional packet filtering. It includes features like deep packet inspection, application awareness, intrusion prevention systems (IPS), and unified threat management (UTM). NGFWs are designed to address modern security threats more effectively.
9. How do I choose the right firewall for my organization?
Choosing the right firewall involves assessing your organization's size, security needs, budget, and future scalability. Considering the type of firewall (hardware, software, cloud-based), key features (threat detection, application control, VPN support), vendor reputation, and support. Testing and evaluating different options before deployment is also crucial.
10. Can I use multiple firewalls together?
Yes, you can use multiple firewalls together to provide layered security. For example, you might use a network firewall at the perimeter and host-based firewalls on individual devices. Ensure that the firewalls are properly configured and do not interfere with each other.

