Computer networking and communication serve as the lifeblood of modern digital interactions, enabling a multitude of computing devices - ranging from personal computers to servers and other network devices - to connect, interact, and exchange data, resources, and services. At the heart of this intricate web of connections lies the primary objective of fostering seamless communication, facilitating collaboration, and promoting the free flow of information among users, devices, and applications. Underpinning these complex systems are network protocols, the unseen yet pivotal mechanisms that ensure the smooth operation of the Internet and other network systems, forming the bedrock of our interconnected digital world.
What are Network Protocols?
Computer networking and communication refer to the technology and methods used to connect multiple computer devices so they can exchange data and resources. Network protocols are conventions used in computer networks to specify communication rules and data transmission formats. Computer networking and communication have the following requirements for network protocols:
- Interoperability: Different manufacturers and devices need to communicate with each other, requiring unified protocol standards.
- Reliability: Protocols need to ensure reliable data transmission, including error detection and correction mechanisms.
- Efficiency: Protocols need to be designed efficiently to reduce latency and increase throughput when transmitting data in the network.
- Security: Data transmitted over the network needs to ensure confidentiality, integrity, and availability, requiring secure protocol mechanisms for data protection.
- Scalability: As networks scale and demands grow, protocols need to have good scalability to adapt to evolving network environments.
- Simplicity: Protocols need to be designed to be simple and understandable to reduce implementation and maintenance complexity.
These requirements guide the design and evolution of network protocols to adapt to the ever-changing network environments and application needs.
What is the OSI Model and How it Works?
Understanding how network protocols operate is crucial to grasping how interconnected devices communicate over a network. The most prevalent model is the Open Systems Interconnection (OSI), which demonstrates how computer systems communicate over networks. This seven-layer model visualizes the communication process between two network devices across the seven layers.
Network Protocols divide the communication process into discrete tasks across each layer of the OSI model. To facilitate network communication, each layer runs one or more protocols. For instance, the Internet Protocol (IP) routes data by managing information like source and destination addresses of data packets to achieve network-to-network communication. Therefore, it is referred to as a network layer protocol.
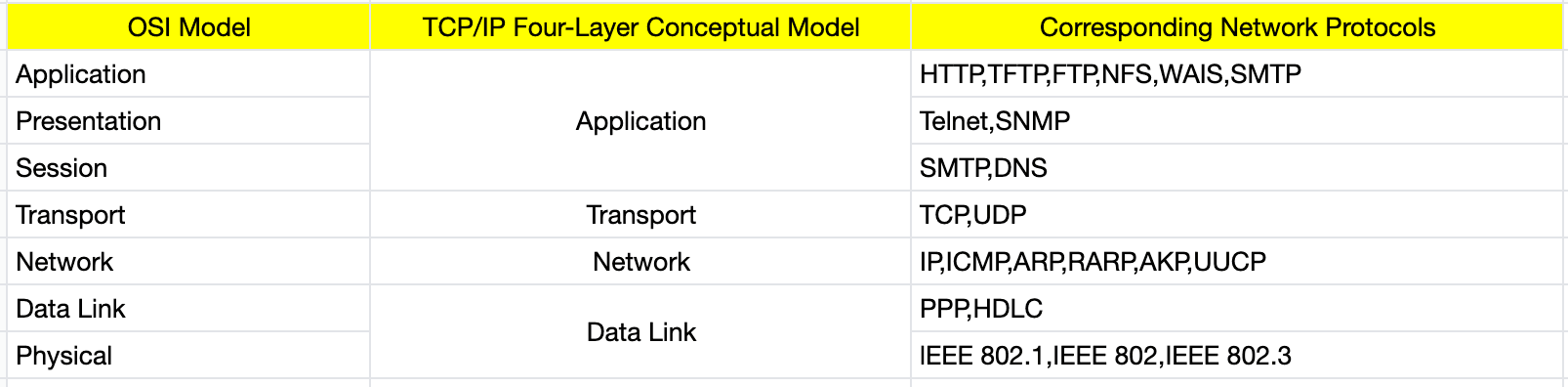
- Physical Layer: Responsible for defining the transmission medium and data format to ensure reliable transmission of the bitstream.
- Data Link Layer: Responsible for the transmission and reception of data frames, error detection, and correction, as well as the identification and addressing of physical addresses.
- Network Layer: Responsible for packet routing, addressing, and forwarding, ensuring that data can be transmitted from source to destination.
- Transport Layer: Provides end-to-end reliable data transmission services, responsible for data segmentation and reassembly, flow control, congestion control, etc.
- Session Layer: Manages and coordinates communication sessions, establishes, maintains, and terminates session connections.
- Presentation Layer: Responsible for data format conversion, encryption, and compression to ensure data exchange between different systems can proceed correctly.
- Application Layer: Provides users with various application services and interfaces, including email, file transfer, web browsing, etc.
Each protocol in the OSI model plays a crucial role in enabling communication between different systems over a network. They work in concert to facilitate the transmission, routing, and delivery of data from one application on one computer to another application on another computer.
Three main types of Network Protocols
Different protocols offer various functions to ensure efficient, fast, and secure network communication. Various types of Network Protocols can be classified into the following three categories to help organizations operate seamlessly in different business scenarios:
Network communication protocols
These protocols establish the rules and formats for transmitting data between networks. Communication protocols manage various aspects of analog and digital communication, such as syntax, authentication, semantics, and error detection. Some important network communication protocols include:
- Hypertext Transfer Protocol (HTTP): Commonly known as the internet protocol, it enables communication between servers and browsers. The default port is 80.
- Transmission Control Protocol (TCP):
- TCP is a protocol that converts data into packets for transmission between servers and clients. Organizations use TCP to transmit files, text, images, and emails, among other content, because it can ensure that data packets are delivered accurately in the correct order.
- It is worth noting that TCP establishes a connection between the source device and the target device before attempting to transmit data.
- Internet Protocol (IP): Facilitates routing of data packets between networks. IP contains addressing and control information for data packet delivery across networks. It works in conjunction with TCP. While it ensures the delivery of packets to the correct address, TCP orders them correctly.
- User Datagram Protocol (UDP):
- UDP is a communication protocol designed to send data packets from one device to another on the network.
- Many organizations use UDP as an alternative to TCP because it offers higher transmission speeds. Although the increase in speed comes at the expense of accuracy, UDP can better support video/audio streaming services, online gaming, or Voice over Internet Protocol (VoIP) calls, which can handle a certain degree of data loss.
- Another major difference between the two is that UDP does not attempt to establish a connection before sending data packets to the destination. At the same time, it does not guarantee the delivery of data to other devices.
- File Transfer Protocol (FTP):
- Allows server file sharing by establishing two TCP connections, one for data transfer and the other for control.
- The data transfer connection transmits actual files, while the control connection transmits control information like passwords to ensure data retrieval in case of data loss.
- The default ports are 20 and 21.
Network Security Protocols
These protocols ensure secure data transmission over network connections. Network security protocols define mechanisms to protect data from unauthorized access. They leverage encryption and cryptography for protection. The following are some commonly used network security protocols:
- Secure File Transfer Protocol (SFTP):
- Facilitates secure file transfers over networks using public key encryption and client-server verification.
- It encrypts and authenticates through the SSH (Secure Shell) protocol, ensuring the confidentiality and integrity of file transfer.
- Hypertext Transfer Protocol Secure (HTTPS): This secure version of HTTP ensures data security between browsers and servers through encryption, overcoming the limitations of HTTP. The default port is 443.
- Secure Socket Layer (SSL):
- Primarily aids in secure internet connections and uses encryption to protect sensitive data. The SSL protocol secures both server-client and server-server communications.
- An SSL certificate is a digital certificate that adheres to the SSL protocol, containing the owner's public key and related identity information, issued by a trusted digital certificate authority (CA).
- SSL certificates use the SSL protocol for communication, featuring server authentication and data transmission encryption capabilities. They ensure the security of communication between services within a device and between devices and external parties, preventing the tampering of communication data during transmission and posing security risks, thereby enhancing system security.
- Digital certificates can be considered a kind of security passport or ID card on the internet, providing proof of identity on the network.
Network Management Protocols
Network administrators require standard policies and procedures to manage and monitor networks to maintain smooth communication. Network management protocols ensure fast troubleshooting and optimal performance. Key network management protocols include:
- Simple Network Management Protocol (SNMP):
- Assists administrators in managing network devices by monitoring endpoint information to track network performance and proactively diagnose network issues.
- The default port is 161.
- Network monitoring platforms typically use SNMP to monitor the performance and status of devices throughout the network in real-time. This protocol is used in conjunction with an SNMP manager or software client to send SNMP GET requests to SNMP-enabled devices.
- Each SNMP-enabled device has a local SNMP agent that collects performance data from the device and forwards this information to the SNMP manager, allowing administrators to obtain a top-down view of performance and status.
- Internet Control Message Protocol (ICMP):
- ICMP aids in diagnosing network connectivity problems. Network devices use ICMP to send error messages, highlight congestion and timeouts, and transmit other operational information to assist in network troubleshooting.
- Troubleshooting tools like Ping send ICMP requests to devices and measure the round-trip time or the time it takes for the device to respond to the request. The amount of delay in the response can then be used to gauge the quality of the connection. Other tools, such as traceroute, use ICMP to troubleshoot and measure the efficiency of network routing, telling users how long it takes for a message to travel from one device to another.
- cybercriminals sometimes use this protocol as part of an ICMP flood attack, attempting to overwhelm servers with illegal ICMP requests to deny computing resources to end-users.
Tencent EdgeOne
Tencent EdgeOne provides acceleration and security solutions based on Tencent's edge computing nodes to protect e-commerce and retail, financial services, content information, games, and other industries to improve user experience. Including:
- Domain Sevice: Helps translate a website's domain name into its corresponding IP address, enabling users to access the website.
- Site Acceleration: EdgeOne offers intelligent acceleration services for both dynamic and static content, effectively enhancing website loading speeds and user experience.
- Security Protection: A key feature of EdgeOne, offers robust policy configuration and security event alert options for applications that integrate with the platform. By validating traffic and requests at the edge, it effectively safeguards against external threats and security risks, ensuring the integrity of your business operations and the confidentiality of sensitive data.
- L4 Proxy: A TCP/UDP-level secure acceleration service suitable for scenarios requiring efficient transmission and security protection simultaneously.
- Edge Functions: An event-driven service that enables developers to quickly implement business logic without concerning themselves with underlying operations and management.

