Network Protocols and TCP/IP
A computer network is a system that connects two or more computing devices for transmitting and sharing information. Computing devices include everything from a mobile phone to a server. These devices are connected using physical wires such as fiber optics, but they can also be wireless. However, in order to enable communication between these different devices, a protocol is needed to establish communication standards. Thus, computer network protocols network protocols were developed: They specify the rules for communication and data exchange between different network devices and define specific aspects such as data format, transmission order, error handling, and more. Computer network protocols enable computer equipment produced by different manufacturers to communicate with each other, achieving global interoperability. With the development of network technology, network protocols are also constantly evolving and updating to meet the needs for higher speed, greater security, and more reliable communication.
Computer network protocols are usually divided according to the hierarchical structure of the network architecture. Common network architectures include the OSI (Open Systems Interconnection) reference model and the TCP/IP (Transmission Control Protocol/Internet Protocol) model.
TCP/IP is a data link protocol used on the internet to let computers and other devices send and receive data. TCP/IP stands for Transmission Control Protocol/Internet Protocol and makes it possible for devices connected to the internet to communicate with one another across networks.
What is TCP/IP and How it Works?
The TCP/IP protocol suite orchestrates the transmission of data between devices, ensuring that the information conveyed remains precise and unaltered upon arrival.
To guarantee the integrity of each communication as it traverses the network, the TCP/IP model dissects data into discrete packets, which are subsequently reassembled into the original message at the destination. This approach of parceling out data into smaller units enhances accuracy compared to the alternative of transmitting the entire data set in one go.
Once a message has been segmented into packets, these units may follow diverse paths to their destination, particularly if congestion occurs on a particular route. This is akin to dispatching several birthday cards to the same residence via postal service. Although the cards start their trip from your abode deposit each into a separate mailbox, and they could travel through various routes before reaching the intended recipient's domicile.
Layers of the TCP/IP Model
The TCP/IP framework comprises four distinct layers: the Network Access layer, the Internet layer, the Transport layer, and the Application layer. Each layer has specific functions and interacts with the upper and lower layers to ensure the smooth exchange of data between systems.
- Network Access Layer: This layer is also known as the link layer or data link layer, responsible for establishing, maintaining, and terminating communication links between adjacent nodes. It encapsulates data into frames and transmits them through physical media such as Ethernet, Wi-Fi, etc.
- Internet Layer: This layer is entrusted with transmitting data packets across distinct networks. Its cornerstone protocol is the Internet Protocol (IP), which boasts two primary iterations: IPv4 and IPv6. The Internet layer further incorporates routing protocols, which are instrumental in identifying the most efficient route for data packets from the source to the destination.
- Transport Layer: The fundamental responsibility of this layer is to initiate, sustain, and conclude end-to-end connections between the origin and the destination. It furnishes two key transport protocols: the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). TCP delivers dependable, connection-oriented transmission services, while UDP provides non-guaranteed, connectionless transmission services.
- Application Layer: Positioned at the summit of the model, this layer directly delivers services to users. It encompasses protocols employed by a myriad of applications, including HTTP (for web browsing), FTP (for file transfer), SMTP (for email transmission), and more. Application layer protocols interface with the transport layer utilizing sockets.
How does the TCP/IP Model Work?
Whenever you transmit any data over the internet, such as a message, a photograph, or a file, the TCP/IP model segments that information into packets using a four-layered process. Initially, the data traverses these layers in a specific sequence, and subsequently, it travels in the opposite direction during the reassembly phase on the recipient's end.
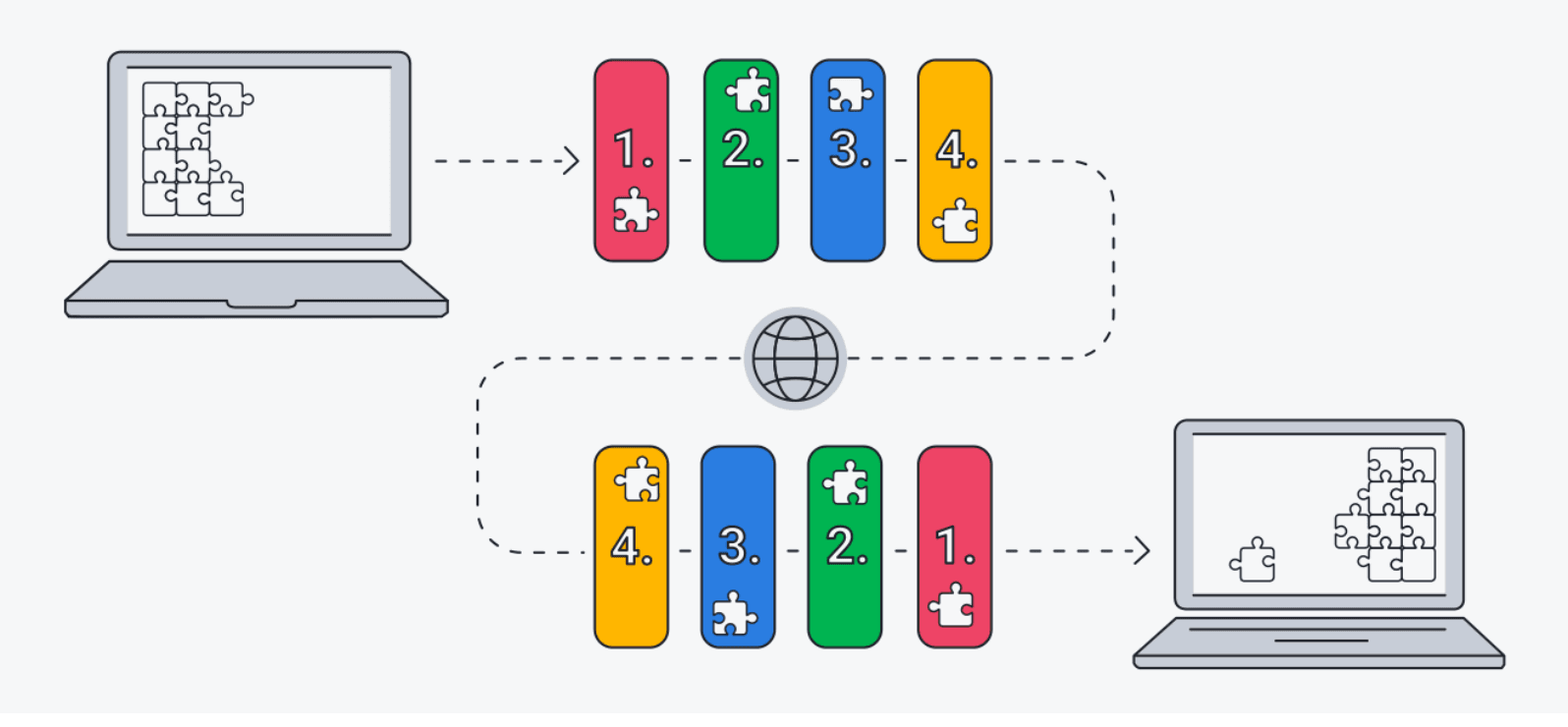
The TCP/IP model is effective due to the standardization of the entire process. In the absence of standardization, communication would become chaotic and impede the overall speed—fast internet service depends on efficiency. As the worldwide standard, the TCP/IP model represents one of the most efficient methods for transmitting data across the internet.
TCP vs IP
TCP and IP are both essential protocols in the Internet Protocol Suite (IPS), but they serve different purposes.
IP is a packet-switched protocol responsible for routing data packets between devices on a network. It provides the basic communication mechanism for internet communication, assigning unique IP addresses to devices and ensuring that packets are delivered to the correct destination.
TCP, on the other hand, is a connection-oriented protocol that provides reliable, end-to-end communication services on top of IP. It establishes a virtual circuit between two devices and ensures that data packets are delivered in the correct order, without errors, and with acknowledgments of receipt.
In summary, IP is responsible for the delivery of packets, while TCP is responsible for the reliable delivery of data. Together, they form the foundation of internet communication.
TCP/IP Model vs OSI Model
What is the OSI Model?
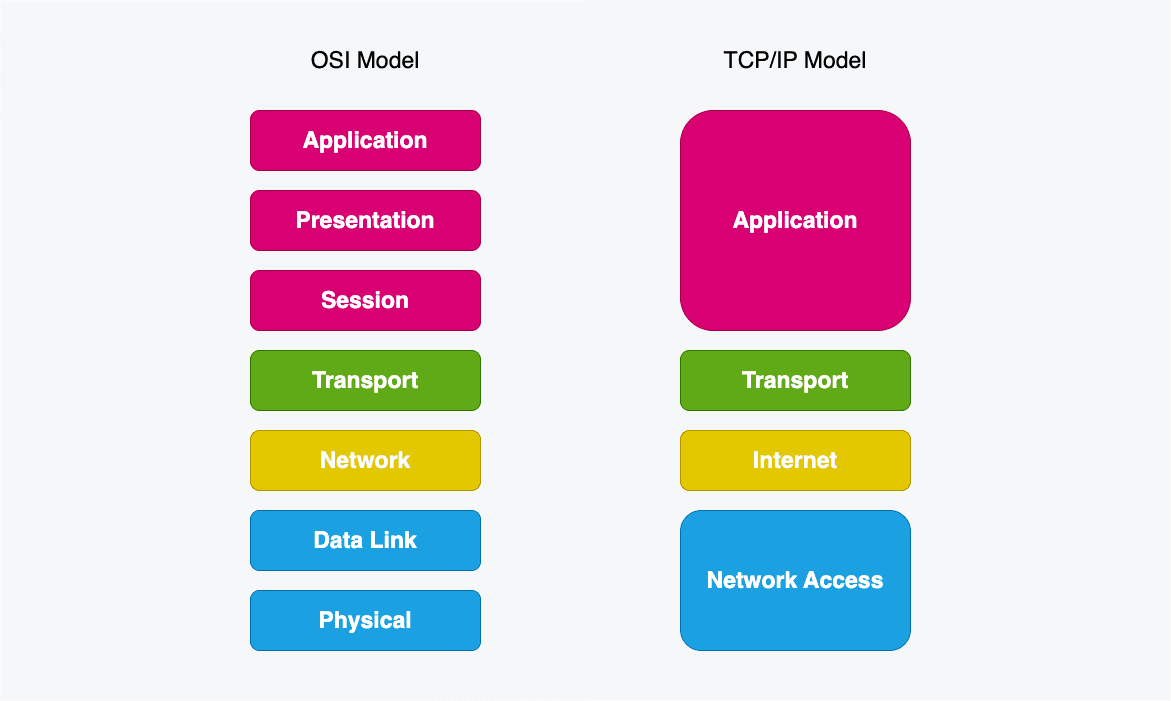
The OSI model is another way of transmitting data over the internet. The biggest difference between the OSI and TCP/IP models is the OSI model has seven layers instead of five. Although both the TCP/IP and OSI models transport data, the ways they send it are slightly different, which is sometimes why TCP/IP is used instead of OSI. The OSI model has the following layers:
- Physical Layer: It is the lowest layer of the OSI model that is responsible for the physical data connection between the devices.
- Data Link: It ensures error-free node-to-node delivery of the message.
- Network Layer: The data gets its address in this layer. It also received routing instructions from moving from source to destination in the network.
- Transport Layer: It is responsible for reliable message delivery across different points on the network on its way to its destination.
- Session Layer: This layer helps with establishing, managing, and terminating sessions.
- Presentation Layer: It is responsible for encrypting and decrypting the data and converting it into a form that is accessible by the application layer.
- Application Layer: In this layer, an application (for example, an internet browser) receives the data and a user can then interact with it.
Similarities between the TCP/IP Model and OSI Model
- Both the models are based on a layered architecture.
- Protocols are defined in a layer-wise way.
Both models convert the raw data into packets and help them reach their destination node. - Each model has different layers with a specific function. This helps in identifying issues if any failure occurs.
- The Physical and Data Link layers of the OSI model correspond to the Network Access layer of the TCP/IP model.
- The Application, Presentation, and Sessions layers of the OSI model correspond to the Application layer of the TCP/IP model.
- Both models have the network layer and the transport layer.
Differences between the TCP/IP Model and OSI Model
The most notable distinction between the two models lies in the fact that the OSI model divides various functions into separate layers, whereas the TCP/IP model groups them into single layers. This is particularly evident in the application and network access layers of the TCP/IP model, which encompass several layers outlined in the OSI model.
This difference can pose challenges when it comes to troubleshooting issues or optimizing performance while using the TCP/IP model. In contrast, the OSI model allows for a more targeted approach to problem-solving. For instance, one can concentrate exclusively on the application layer, presentation layer, or session layer to identify why data is not being transmitted as expected.
Is TCP/IP Secure?
TCP/IP is an open, connection-oriented communication protocol tailored for data exchange on the Internet.
The original TCP/IP protocol does not provide end-to-end encryption or authentication. This means that, without using additional security mechanisms, data transmitted through TCP/IP is unencrypted and easily intercepted and viewed by intermediaries.
To enhance the security of TCP/IP, several security protocols have been developed, such as SSL/TLS (Secure Sockets Layer/Transport Layer Security). These protocols provide encryption, authentication, and integrity protection on top of TCP/IP. For example, when we access an HTTPS website in our browser, the communication between our browser and the website is encrypted through SSL/TLS.
The L4 Proxy on Tencent EdgeOne
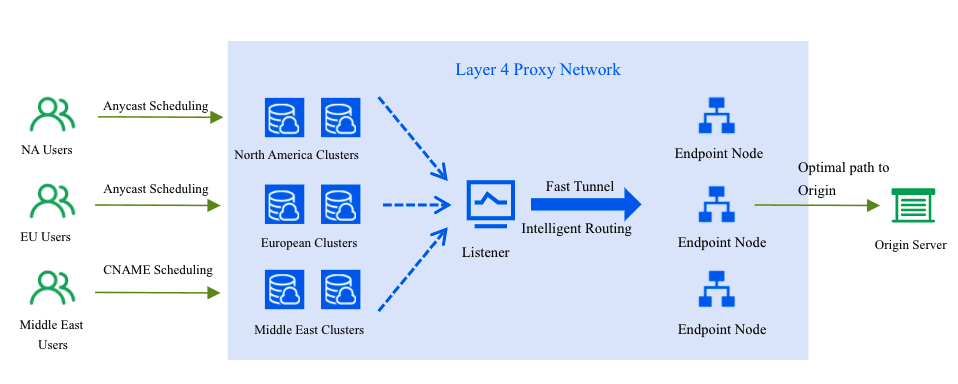
The Tencent EdgeOne L4 Proxy serves as a robust acceleration service founded upon the TCP/UDP protocols. Utilizing a globally dispersed network of layer-4 proxy nodes, coupled with an innovative DDos module and sophisticated routing techniques, Tencent EdgeOne facilitates seamless, proximate access for end-users. It meticulously purifies edge traffic and oversees port monitoring and forwarding, ensuring the provision of high-availability and low-latency DDoS mitigation and acceleration solutions tailored for layer-4 applications.
Feel free to contact us to learn more about Tencent EdgeOne and its features. You can also click here to get started free and experience its benefits firsthand.

