HTTPS (Hyper Text Transfer Protocol Secure) is a network transmission protocol used for secure and encrypted data transmission between clients and servers. It is the secure version of the HTTP protocol, which uses SSL/TLS protocol on the basis of HTTP to encrypt and authenticate data, ensuring the privacy and integrity of the data during transmission.
How Does HTTPS Work?
1. HTTPS Communication Process
The communication process of HTTPS is as follows:
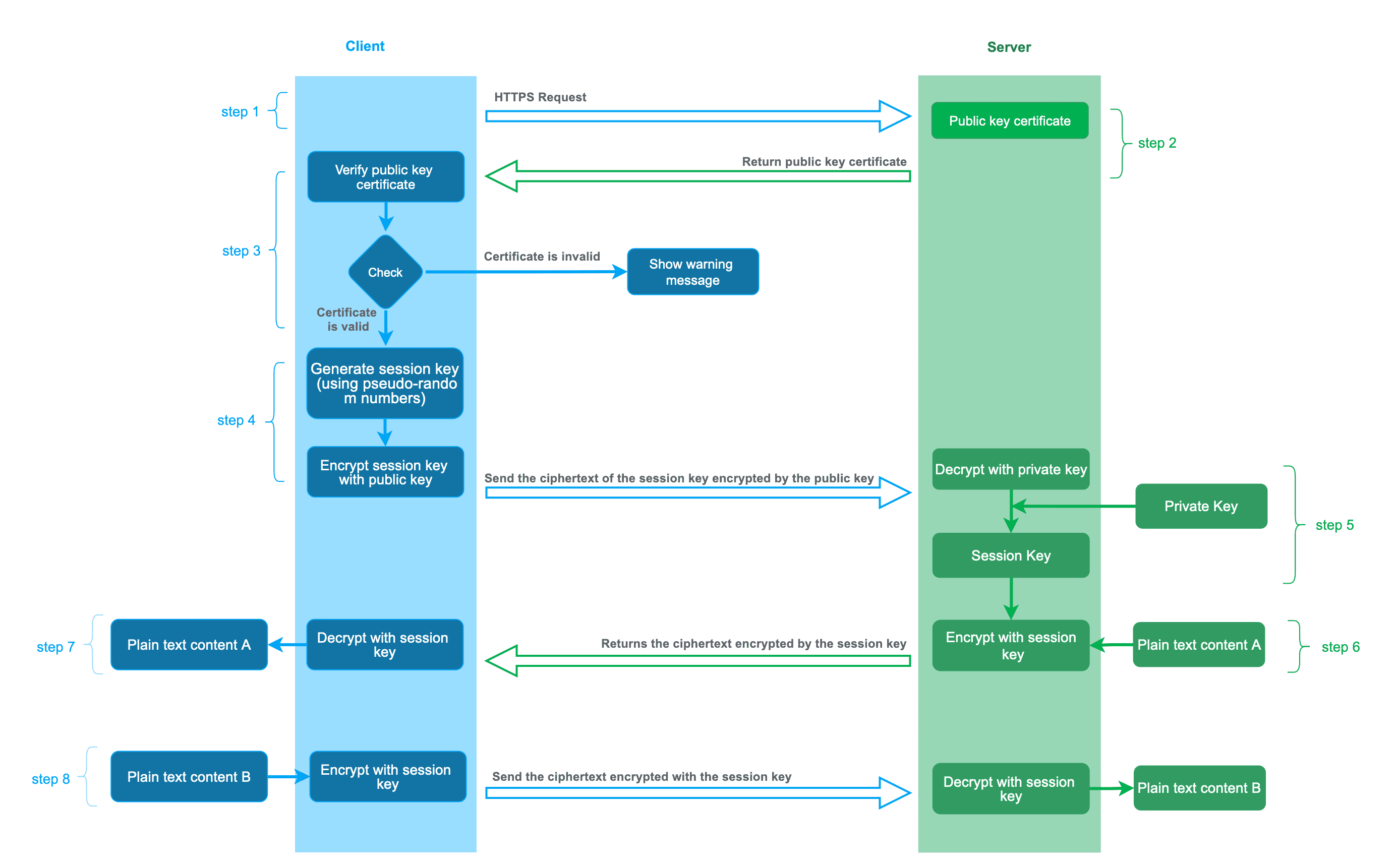
- Client initiates an HTTPS request.
- Server returns a pre-configured public key certificate to the client.
- Client verifies the public key certificate, including checking the certificate's validity period, whether its purpose matches the requested site, whether it is in the CRL revocation list, and whether the higher-level certificate is valid. This is a recursive process, continuing until the root certificate is verified (either the operating system's built-in root certificate or the client's built-in root certificate). If the verification passes, the process continues; otherwise, a warning message is displayed.
- Client uses a pseudorandom number generator to generate the symmetric key used for encryption, then encrypts this symmetric key with the certificate's public key and sends it to the server.
- Server uses its private key to decrypt the message, obtaining the symmetric key. In this way, both the client and the server hold the same symmetric key.
- Server uses the symmetric key to encrypt the "plaintext content A" and sends it to the client.
- Client uses the symmetric key to decrypt the encrypted response, obtaining the "plaintext content A".
- Client initiates another HTTPS request, encrypts the request's "plaintext content B" using the symmetric key, and then the server decrypts the ciphertext using the symmetric key, obtaining the "plaintext content B".
2. Connections Between SSL, TLS, and HTTPS
- SSL (Secure Sockets Layer) is an encryption protocol used to implement secure communication in networks. The purpose of the SSL protocol is to provide an encryption and authentication layer between the application layer (e.g., HTTP) and the transport layer (e.g., TCP).
- TLS (Transport Layer Security) is the successor version of the SSL protocol, offering higher security and performance. In fact, TLS 1.0 is essentially SSL 3.1, and their differences mainly lie in improvements to encryption algorithms and protocol details.
- The relationship between HTTPS and TLS/SSL is that HTTPS achieves secure communication by using SSL or TLS protocols to encrypt and authenticate the HTTP protocol. When communicating between clients and servers, HTTPS uses SSL or TLS protocols to encrypt data, ensuring the security of the transmission process. Nowadays, due to TLS being an updated and more secure version of SSL, the TLS protocol is more commonly used in practice.
HTTP vs HTTPS
The main difference between HTTP and HTTPS lies in the security of data transmission:
- Security: HTTP is not secure, while HTTPS is secure. Data transmitted by HTTP is not encrypted, so it can be intercepted and obtained by anyone who intercepts network transmission. HTTPS encrypts data through the SSL/TLS protocol, protects the integrity and privacy of the data, making it not easy to be stolen and tampered with during transmission.
- Port: HTTP uses port 80 by default, while HTTPS uses port 443 by default.
- URL: In the address bar of most browsers, HTTPS websites will display a small lock icon, indicating that the connection is secure. HTTP websites do not have this.
- Certificate: HTTPS needs to use certificates issued by a certification authority (CA). If the certificate is not trusted by the browser, users will see a warning, telling them that the connection may not be secure.
- Performance: Because HTTPS needs to encrypt data, it may be slightly slower than HTTP in processing speed. However, with the advancement of technology, this gap is becoming smaller and smaller.
- SEO Optimization: Search engines like Google favor HTTPS websites in rankings because they are more secure.
What are the Differences between HTTP/2, HTTP/3, and HTTPS?
HTTP/2 and HTTP/3 are different versions of the HTTP protocol, while HTTPS is a secure communication protocol for encrypting data.
- HTTP/2: Introduces features like multiplexing and header compression to enhance performance and efficiency by reusing connections and handling parallel requests.
- HTTP/3: Based on the UDP protocol, it uses the QUIC protocol to transmit data, aiming to facilitate faster connection establishment and improve performance during network interruptions. HTTP/3 operates on QUIC at the transport layer instead of TCP, enabling faster connection establishment and improved performance.
- HTTPS: It is the secure version of the HTTP protocol, ensuring secure data transmission between clients and servers by encrypting and authenticating data using the TLS/SSL protocol.
In summary, HTTPS is the secure version of the HTTP protocol, while HTTP/2 and HTTP/3 are different versions of the HTTP protocol, both of which can operate under HTTPS.
Is HTTPS 100% Secure?
Although HTTPS is more secure than HTTP, it cannot guarantee 100% security. HTTPS indeed improves the security of data transmission, preventing data from being intercepted or tampered with by third parties, but there are still some potential security risks and limitations:
- Certificate issues: If the server's SSL/TLS certificate is not issued by a trusted Certificate Authority (CA), or if the certificate has expired or been tampered with, the HTTPS connection may be vulnerable to attacks.
- Man-in-the-middle attacks: Although HTTPS can prevent most man-in-the-middle attacks, in certain situations, such as when an attacker controls the communication link between the user and the server or forges a valid certificate, the attacker may still be able to intercept and tamper with data.
- Server and client security vulnerabilities: HTTPS provides secure data transmission through encryption but cannot prevent application-level vulnerabilities such as SQL injection, cross-site scripting (XSS), and other web-based attacks.
- Encryption algorithm and protocol vulnerabilities: Although the TLS protocol is constantly being updated to fix known vulnerabilities and improve security, new vulnerabilities and security issues may continue to emerge. Therefore, it is essential to use the latest encryption algorithms and protocols.
- User behavior: Users may mistakenly trust the wrong websites, such as phishing sites, even if they use HTTPS. Users need to be cautious in verifying the authenticity of websites to avoid leaking personal information.
Tencent EdgeOne: Supporting HTTPS and Key Advantages
Tencent EdgeOne provides excellent support for HTTPS and offers several advantages when you use this secure protocol:
- Flexible Encryption Support: EdgeOne provides comprehensive encryption capabilities, supporting both international standard certificates with RSA/ECC algorithms and Chinese SM standard certificates with SM2 algorithm to ensure secure data transmission.
- Free and Paid Certificates: EdgeOne provides both free and paid certificate options. If you're a SME site owner or run a personal blog, you might consider configuring a free certificate for your domain. This way, you can support HTTPS access without any notable initial costs.
- HTTP to HTTPS Conversion: EdgeOne can enforces secure connections by automatically redirecting HTTP requests to HTTPS through 301/302 redirects, enhancing website security and protecting user privacy.
In summary, implementing HTTPS not only enhances your website's SEO efficiency, but more importantly, it provides a secure platform for your visitors, thereby cultivating trust with your target audience.

