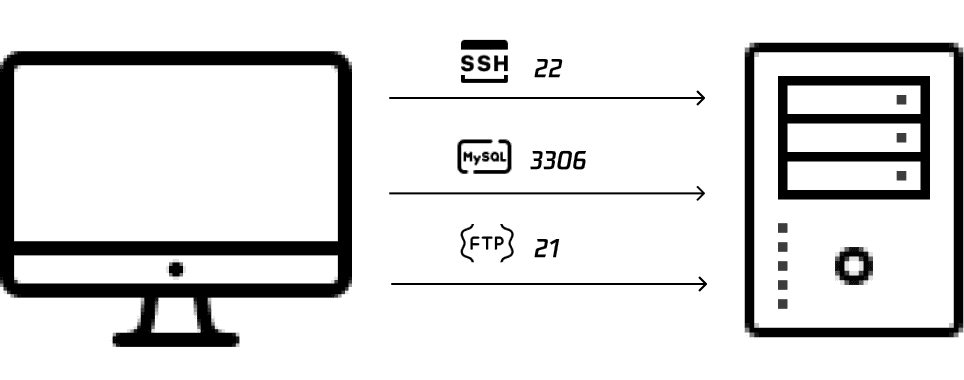
In the world of computer networking, ports play a crucial role in enabling communication between devices and applications. Think of ports as virtual doorways that allow data to flow in and out of a computer or network device. Just as a house has multiple doors for different purposes, a computer uses various ports to manage different types of network traffic. In our daily work, we often engage with various ports. For instance, we frequently use SSH on port 22, RDP on port 3389, and HTTP on port 80.
What are Ports in Networking?
A port is essentially a numerical identifier, ranging from 0 to 65535, that helps distinguish different services or applications running on a single device. When data travels across a network, it needs to know which "door" (port) to use to reach its intended destination. This system allows multiple services to operate simultaneously on a device without interfering with each other.
Key Points About Ports:
- Ports work alongside IP addresses to ensure data reaches the correct application on the right device.
- They enable multi-tasking by allowing various applications to communicate over the network at the same time.
- Ports are crucial for network security, as they can be monitored and controlled to protect against unauthorized access.
What are the Types of Ports?
Ports are categorized into three main types, each serving different purposes:
1. Well-Known Ports
- Range: 0 to 1023
- Description: These ports are reserved for widely used protocols and services. They are assigned by the Internet Assigned Numbers Authority (IANA) and are commonly recognized across the internet.
- Examples:
- HTTP: Port 80 (used for web traffic)
- HTTPS: Port 443 (used for secure web traffic)
- FTP: Port 21 (used for file transfer)
- SSH: Port 22 (used for secure shell access)
- SMTP: Port 25 (used for sending emails)
2. Registered Ports
- Range: 1024 to 49151
- Description: These ports are not as universally recognized as well-known ports but are registered for specific applications and services. They can be used by user applications and are also assigned by IANA.
- Examples:
- MySQL: Port 3306 (used for MySQL database connections)
- PostgreSQL: Port 5432 (used for PostgreSQL database connections)
- RDP: Port 3389 (used for Remote Desktop Protocol)
3. Dynamic or Private Ports
- Range: 49152 to 65535
- Description: These ports are not assigned to any specific service and are often used for temporary or dynamic connections. They are typically assigned by the operating system when an application requests a port.
- Examples: These ports are often used for client-side applications, such as web browsers or email clients, when they connect to servers. For instance, when a web browser connects to a web server, it may use a dynamic port in this range for the outgoing connection.
How Ports Work?
When you browse the internet or use a network application, ports are working behind the scenes to ensure smooth communication. Here's a simple example:
- You type a website address into your browser.
- Your browser sends a request to the web server's IP address on port 80 (for HTTP) or 443 (for HTTPS).
- The web server, which is listening on these ports, receives the request.
- The server processes the request and sends back the webpage through the same port.
- Your browser receives the data and displays the website.
This process allows multiple users to access the same web server simultaneously, with each request directed to the appropriate service based on the port number.
The Importance of Ports in Networking
Ports are essential for several reasons:
- Multi-Tasking: Ports allow multiple applications to run on a single device simultaneously. For instance, a computer can host a web server, an email server, and a file transfer service all at once, each using different ports.
- Security: Firewalls and security systems often use port numbers to control access to services. By blocking or allowing traffic on specific ports, network administrators can enhance security and protect against unauthorized access.
- Protocol Differentiation: Different protocols use different ports, which helps in distinguishing between various types of traffic. For example, web traffic (HTTP) is routed through port 80, while email traffic (SMTP) is routed through port 25.
Why Use a Firewall to Block Certain Ports?
Firewalls are essential security tools used to protect networks and systems from unauthorized access and potential threats. One of the key functions of a firewall is to block certain ports, which is crucial for several reasons:
- Security Risks: Certain ports are commonly associated with well-known services that are often targeted by attackers. For example, ports like 21 (FTP), 23 (Telnet), and 80 (HTTP) can be exploited if not properly secured. By blocking these ports, firewalls help mitigate the risk of unauthorized access and attacks such as brute force, denial of service (DoS), or exploitation of vulnerabilities in the services running on those ports.
- Preventing Malware and Intrusions: Many types of malware and malicious activities use specific ports to communicate with command and control (C&C) servers or to spread within a network. By blocking these ports, firewalls can help prevent malware from establishing connections that could lead to data breaches or further infections.
- Controlling Network Traffic: Firewalls can manage and control the flow of network traffic by blocking ports that are not necessary for business operations. This helps to reduce congestion and improve overall network performance. By limiting the number of open ports, organizations can also simplify their network management and monitoring efforts.
- Compliance and Regulatory Requirements: Many industries have specific regulations and compliance standards that require organizations to implement security measures, including the management of network ports. Blocking certain ports can help organizations meet these requirements and protect sensitive data.
- Minimizing Attack Surface: The more open ports a network has, the larger its attack surface becomes. By blocking unnecessary ports, firewalls help minimize the potential entry points for attackers, thereby enhancing the overall security posture of the network.
- Preventing Unauthorized Services: Some organizations may want to restrict the use of certain services that run on specific ports, such as peer-to-peer file sharing or remote desktop access. By blocking these ports, firewalls can prevent unauthorized applications from running on the network.
- Policy Enforcement: Organizations often have specific security policies in place that dictate which services and applications are allowed. Firewalls enforce these policies by blocking ports associated with unauthorized or non-compliant services.
Overall, using a firewall to block certain ports is a fundamental practice in network security that helps maintain the integrity, confidentiality, and availability of systems and data.
How to Check Open Ports?
Knowing which ports are open on a service is essential for network management and security. Here are some popular methods to check open ports:
- Using Native Command Line Tools: Most operating systems come with built-in command line tools, such as 'netstat', which is available on both Windows and Unix-like systems. These tools can list currently open ports and their associated services.
- Dedicated Network Security Software: For more comprehensive solutions, there are dedicated network security applications and firewalls. These offer in-depth scanning and monitoring capabilities to continuously track open ports and evaluate their security status.
- Online Checker Tools: You can use online open ports checker to check the open ports of a website.
Conclusion
Ports are the unsung heroes of computer networking, enabling seamless communication between devices and applications. By directing traffic to the right destinations, ports make it possible for us to enjoy a wide range of online services simultaneously. Understanding ports is not just important for IT professionals; it's valuable knowledge for anyone who uses the internet and wants to grasp how our connected world functions.
To further enhance your network's security, consider using EdgeOne DDos Protection, which allow you to configure port filtering to effectively prevent potential network attacks. This not only safeguards your network from threats but also ensures the smooth operation of your applications and services. We have now launched a Free Trial, welcome to Sign Up and Contact Us for more information.
FAQs
Q1: What is the range of port numbers?
A1: Port numbers range from 0 to 65535, with well-known ports typically below 1024.
Q2: What is port forwarding?
A2: Port forwarding is a technique that allows external devices to access services on a private network by mapping specific ports.
Q3: Why are some ports considered "well-known"?
A3: Well-known ports (0-1023) are reserved for common services and protocols, such as HTTP (80), HTTPS (443) and SSH (22).

