A Web Application Firewall (WAF) is a specialized firewall that protects web applications from cyber threats. It inspects, filters, and blocks malicious HTTP traffic, safeguarding web applications.
With cyber-attacks becoming increasingly complex and frequent, WAFs have become essential for protecting web applications. They can prevent various cyber attacks, such as SQL injection, Cross-Site Scripting (XSS), and Distributed denial-of-service (DDoS) attacks.
In this article, we will discuss the role of WAFs in securing web applications, their key features, and how to choose the right WAF for your organization.
What is a Web Application Firewall?
A Web Application Firewall (WAF) is a specialized security solution designed to protect web applications and APIs by filtering, monitoring, and blocking malicious web traffic and application-layer attacks. It operates at the application layer (Layer 7 in the OSI model) and focuses on HTTP/HTTPS traffic between web applications and the internet. The primary function of a WAF is to act as an intermediary between the client and the web server, scrutinizing incoming and outgoing traffic to identify and mitigate threats.
The core capabilities of a WAF include:
- SQL Injection Protection: SQL injection is a common attack vector where malicious SQL queries are inserted into input fields to manipulate the database. A WAF can detect and block such attempts.
- Cross-Site Scripting (XSS) Defense: XSS attacks involve injecting malicious scripts into web pages viewed by other users. WAFs can identify and filter out these scripts to prevent them from executing.
- CC Attack Interception: CC (Challenge Collapsar) attacks, also known as DDoS attacks, aim to overwhelm the server with excessive traffic. WAFs can detect and mitigate these attacks by filtering out malicious requests.
- Sensitive Data Protection: WAFs can prevent sensitive information from being leaked by monitoring and controlling data flows.
Differences between WAF and Firewall
Traditional firewalls operate at the network layer (Layer 3) and focus on filtering traffic based on IP addresses, ports, and protocols. In contrast, WAFs are specifically designed to protect web applications by analyzing application-layer traffic. Key differences include:
- Focus on Application Layer: WAFs concentrate on HTTP/HTTPS traffic and understand the nuances of web application protocols.
- Bidirectional Content Inspection: WAFs inspect both incoming and outgoing traffic, providing comprehensive protection.
- Semantic Analysis: WAFs use semantic analysis to understand the context and meaning of web traffic, enabling more accurate threat detection.
How does a WAF Work?
A Web Application Firewall (WAF) is a specialized security solution designed to protect web applications and APIs from a wide range of threats by analyzing and filtering HTTP/HTTPS traffic. Understanding how a WAF works involves exploring its core components, deployment modes, and the mechanisms it uses to detect and mitigate attacks. Below is a detailed explanation of how a WAF functions.
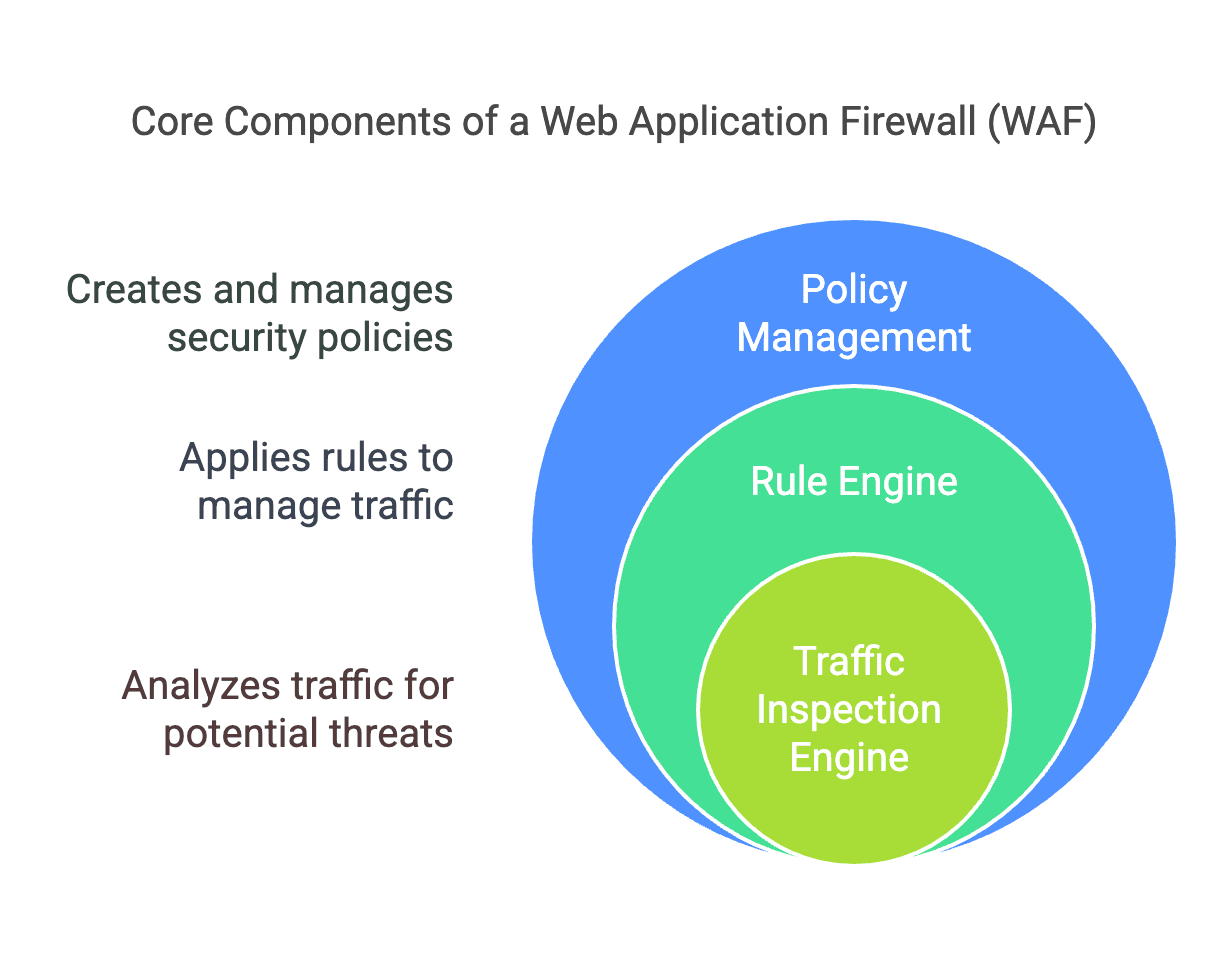
Core Components of a WAF
1. Traffic Inspection Engine
The traffic inspection engine is the heart of a WAF. It is responsible for analyzing incoming and outgoing HTTP/HTTPS traffic to identify potential threats. The engine uses several techniques to inspect traffic:
- Signature-Based Detection: The WAF compares incoming traffic against a database of known attack signatures. For example, it can detect SQL injection attacks by looking for patterns such as SQL keywords in URL parameters or form fields.
- Behavioral Analysis: This involves monitoring the behavior of users and traffic patterns to identify anomalies. For instance, if a user is making an unusually high number of requests in a short period, it might indicate a brute-force attack.
- Semantic Analysis: The WAF understands the context and meaning of web traffic. For example, it can differentiate between a legitimate request for a web page and a malicious request that attempts to exploit a vulnerability.
- Machine Learning: Advanced WAFs use machine learning algorithms to learn from historical data and adapt to new threats. This allows the WAF to detect zero-day attacks and other sophisticated threats that traditional signature-based methods might miss.
2. Rule Engine
The rule engine is a set of predefined rules that the WAF uses to determine how to handle specific types of traffic. These rules can be configured by security administrators to suit the specific needs of an organization. Some common rules include:
- Allow/Deny Rules: These rules specify which types of traffic should be allowed or blocked. For example, a rule might block all traffic from a specific IP address that has been identified as malicious.
- Rate Limiting: This rule limits the number of requests a user can make within a certain time frame. It helps prevent DDoS attacks and brute-force attacks.
- Data Masking: This rule ensures that sensitive data, such as credit card numbers or personal information, is masked or removed from responses to prevent data leakage.
3. Policy Management
Policy management involves creating and managing the security policies that the WAF uses to protect web applications. Policies can be customized based on the specific requirements of each application and can include:
- Application-Specific Policies: Different web applications may have different security requirements. For example, an e-commerce site might need stricter rules for payment processing than a blog.
- User-Based Policies: Policies can also be tailored based on user roles and permissions. For instance, administrative users might have different access rules compared to regular users.
- Dynamic Policies: Some WAFs can dynamically adjust policies based on real-time threat intelligence and user behavior.
Deployment Modes
1. Transparent Proxy Mode
In transparent proxy mode, the WAF acts as an intermediary between the client and the web server. It inspects traffic without modifying the IP addresses of the requests. This mode is useful for organizations that want to deploy a WAF without making significant changes to their existing network infrastructure.
2. Reverse Proxy Mode
In reverse proxy mode, the WAF terminates incoming connections and forwards requests to the web server. This mode provides more control over traffic and can offer additional security features, such as SSL/TLS termination and content caching. It is commonly used in environments where high performance and security are critical.
3. Routing Mode
In routing mode, the WAF is configured as a network device that routes traffic between different network segments. This mode is useful for complex network architectures where traffic needs to be routed through multiple devices.
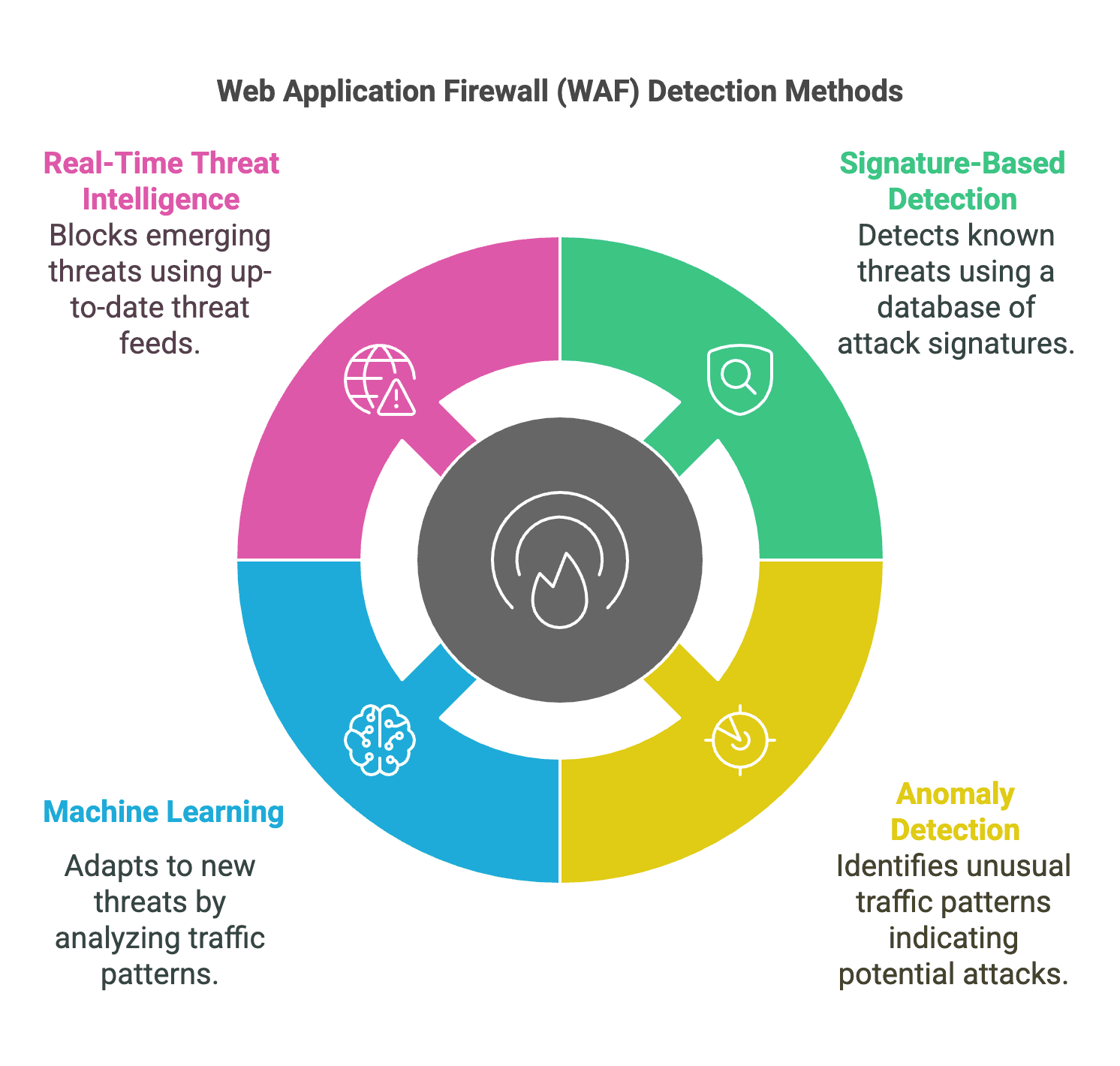
WAF Detection and Mitigation Mechanisms
1. Signature-Based Detection
Signature-based detection is the most common method used by WAFs. It involves comparing incoming traffic against a database of known attack signatures. These signatures are typically updated regularly to include new threats. For example, a WAF might detect a SQL injection attack by looking for patterns such as SELECT * FROM in URL parameters.
2. Anomaly Detection
Anomaly detection involves monitoring traffic patterns and identifying deviations from normal behavior. For example, if a user is making an unusually high number of requests in a short period, it might indicate a brute-force attack. Anomaly detection can also identify unusual traffic patterns that might indicate a DDoS attack.
3. Machine Learning
Advanced WAFs use machine learning algorithms to analyze traffic and detect threats. Machine learning models can learn from historical data and adapt to new threats. For example, a machine learning model might identify a new type of attack by analyzing the behavior of traffic and identifying patterns that are similar to known threats.
4. Real-Time Threat Intelligence
Some WAFs integrate with real-time threat intelligence feeds to stay up-to-date with the latest threats. This allows the WAF to detect and block emerging threats before they can cause damage. For example, a WAF might receive an alert about a new zero-day exploit and update its rules to block traffic that matches the exploit's signature.
Mitigation Actions
1. Blocking Traffic
When a WAF detects a threat, it can block the offending traffic to prevent it from reaching the web server. Blocking can be done at various levels, such as blocking specific IP addresses, blocking specific requests, or blocking all traffic from a particular source.
2. Rate Limiting
Rate limiting is a technique used to limit the number of requests a user can make within a certain time frame. This helps prevent DDoS attacks and brute-force attacks by limiting the rate at which an attacker can send requests.
3. Alerting and Logging
When a threat is detected, the WAF can generate alerts and log the incident for further investigation. Alerts can be sent to security administrators via email, SMS, or other notification methods. Logging provides a record of all detected threats, which can be useful for forensic analysis and improving security policies.
A Web Application Firewall (WAF) works by inspecting HTTP/HTTPS traffic, detecting threats using a combination of signature-based detection, anomaly detection, and machine learning, and mitigating threats through blocking, rate limiting, and alerting. By deploying a WAF, organizations can significantly enhance the security of their web applications and protect against a wide range of threats.
What are the Types of WAFs?
Web Application Firewalls (WAFs) can be categorized into several types based on their deployment models and functionalities. Each type has its own advantages and disadvantages, and the choice of WAF often depends on the specific needs and infrastructure of an organization. Here are the main types of WAFs:
1. Network-Based WAFs
Network-based WAFs are deployed at the perimeter of a network and are designed to protect all web applications on the network. They operate by inspecting incoming traffic to the network and blocking any traffic that does not meet the configured security rules. These WAFs are typically deployed on hardware devices or as a software solution that runs on a dedicated server.
Pros:
- Can protect all web applications on a network.
- Can be used to protect against a wide range of threats, including network-based threats.
- Can be configured to block traffic based on a variety of criteria, such as IP addresses and port numbers.
Cons:
- Requires a dedicated hardware or software solution.
- May require a significant investment in hardware and maintenance.
- May not provide as granular a level of control as host-based WAFs.
2. Host-Based WAFs
Host-based WAFs are deployed on individual web servers and are designed to protect the web application running on that server. They operate by inspecting incoming traffic to the web application and blocking any traffic that does not meet the configured security rules. Host-based WAFs are typically deployed as software solutions that run on the web server.
Pros:
- Provides a granular level of control over the web application being protected.
- Can be deployed on any type of web server.
- Does not require a dedicated hardware solution.
Cons:
- Only protects the web application running on the server where it is deployed.
- May require additional resources to manage and maintain.
3. Cloud-Based WAFs
Cloud-based WAFs are hosted and managed by a third-party provider. They operate by inspecting incoming traffic to a web application and blocking any traffic that does not meet the configured security rules. Cloud-based WAFs are typically deployed as a service, with the WAF provider managing the hardware and software infrastructure required to run the WAF.
Pros:
- No need to purchase or maintain hardware or software infrastructure.
- Easy to scale up or down as needed.
- Can be used to protect web applications hosted on any type of server.
Cons:
- Requires a subscription to a third-party service.
- May not provide as much control over the WAF configuration as on-premises solutions.
- May not provide the same level of protection as an on-premises WAF, depending on the provider and the specific service being used.
4. Blocklist vs. Allowlist WAFs
WAFs can also be distinguished by their security models:
- Blocklist WAFs follow a negative security model, blocking certain endpoints or types of traffic while allowing all others.
- Allowlist WAFs follow a positive security model, blocking all traffic by default and allowing only traffic that is explicitly approved.
Allowlist WAFs are generally considered more secure because they minimize the risk of malicious traffic evading defenses due to improperly configured firewall rules. However, they may not be practical in situations where all valid traffic types or endpoints cannot be anticipated. Many modern WAFs operate using a hybrid security model that combines both blocklist and allowlist approaches.
In summary, the type of WAF an organization chooses will depend on its specific security needs, infrastructure, and operational capabilities. Network-based, host-based, and cloud-based WAFs each offer unique benefits and trade-offs, while blocklist and allowlist models provide different approaches to security. Understanding these differences can help organizations make informed decisions to protect their web applications effectively.
Use Cases of WAFs
Web Application Firewalls (WAFs) are versatile security tools with a wide range of use cases across various industries and deployment scenarios. Here are some of the most common use cases for WAFs:
1. Preventing Data Leaks
Web applications often handle sensitive data such as personal information, financial details, and business secrets. Attackers may exploit vulnerabilities like SQL injection or cross-site scripting (XSS) to steal this data. WAFs can detect and block such malicious requests, thereby protecting sensitive information from being leaked.
2. Mitigating Application Layer Attacks
WAFs are designed to protect against a variety of application layer attacks, including:
- SQL Injection: Protecting databases from unauthorized access.
- Cross-Site Scripting (XSS): Preventing malicious scripts from being injected into web pages.
- Cross-Site Request Forgery (CSRF): Blocking unauthorized requests made by attackers.
- Command Injection: Preventing attackers from executing system commands through web forms.
3. Defending Against DDoS Attacks
Distributed Denial of Service (DDoS) attacks aim to overwhelm web servers with excessive traffic. WAFs can detect and mitigate these attacks by filtering out malicious requests and rate-limiting traffic. Some WAFs offer advanced DDoS protection features such as Layer 7 flood protection.
4. API Security
Modern web applications heavily rely on APIs, which can be vulnerable to attacks. WAFs can be configured to protect APIs by validating requests, enforcing rate limits, and detecting anomalies.
5. Customizable Security Policies
WAFs allow organizations to define custom security policies tailored to their specific needs. For example, rules can be set to block traffic from specific IP addresses, limit the number of requests from a single user, or enforce specific authentication mechanisms.
6. Protecting Against Bot Traffic
WAFs can detect and block malicious bot traffic, preventing automated attacks such as brute-force login attempts, content scraping, and spam submissions.
7. Web Page Tampering Prevention
WAFs can monitor and protect web pages from unauthorized modifications, ensuring the integrity of the content displayed to users.
Choosing the Right WAF for Your Organization
A Web Application Firewall (WAF) is a powerful tool that can protect your online applications from a variety of cyber attacks. When selecting a WAF, organizations should consider several key factors:
- Performance Throughput: The WAF should be able to handle the expected traffic load without introducing significant latency.
- False Positive Rate: A low false positive rate is crucial to avoid blocking legitimate traffic.
- Rule Update Frequency: Regular updates to the WAF's rule set are essential to stay ahead of emerging threats.
- Compatibility with Existing Security Infrastructure: The WAF should integrate seamlessly with other security solutions, such as intrusion detection systems (IDS) and security information and event management (SIEM) systems.
However, choosing the right WAF is not always straightforward. Here are other key factors you should consider when selecting a WAF:
- Deployment Options: WAFs can be deployed in the cloud, on-premises, or in a hybrid manner. Cloud-based WAFs offer seamless scalability and global coverage, while on-premises WAFs provide greater customization and control. Hybrid deployments combine the advantages of both. You should choose the deployment option that best suits your business needs and security strategy.
- Ease of Integration with Existing Infrastructure: The ideal WAF should integrate easily with your existing security infrastructure, including Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM) systems, and more. This can enhance security performance and simplify security management processes.
- Customization Capabilities: Different organizations may face different threats and therefore require different protection strategies. A robust WAF should offer high customization capabilities, allowing you to create and modify security rules according to your needs. This ensures that your WAF can effectively defend against specific application threats.
- Cost and Maintenance Requirements: When choosing a WAF, you need to consider the total cost of ownership, including purchase cost, implementation cost, maintenance cost, and training cost. Additionally, you should consider the maintenance requirements of the WAF. The ideal WAF should be easy to manage and maintain and offer strong support and service.
Common Web Application Firewall (WAF) vendors include Tencent Edgeone Web Protection, Cloudflare WAF, Akamai WAF, Imperva WAF, and more.
Future Development of WAF
Capability Enhancements
Next-generation WAFs are evolving to address emerging threats and provide more comprehensive protection:
- API Security: With the increasing use of APIs in modern applications, protecting them from attacks is crucial. Next-gen WAFs offer specialized features for API security, including rate limiting, authentication, and access control.
- Business Anti-Fraud: These WAFs can detect and prevent fraudulent activities, such as account takeovers and payment fraud, by analyzing user behavior and transaction patterns.
- Multi-Layer Protocol Analysis: Next-gen WAFs can analyze traffic across multiple layers, providing a more holistic view of potential threats.
- Web Page Tampering Prevention: They can detect and prevent unauthorized modifications to web pages, ensuring the integrity of the content.
- Bot Traffic Identification: Next-gen WAFs can distinguish between legitimate and malicious bot traffic, mitigating the risk of automated attacks.
- Content Risk Control: By integrating with content delivery networks (CDNs), these WAFs can provide real-time risk assessment and mitigation for content delivery.
Bypass Techniques
Despite the robustness of WAFs, attackers continue to develop new techniques to bypass their defenses:
- Chunked Encoding Splitting: Attackers can split malicious payloads across multiple chunks to evade detection.
- SQL Syntax Ambiguity Exploitation: By using ambiguous SQL syntax, attackers can bypass simple signature-based detection.
- Cloud WAF Real IP Detection: Attackers may attempt to detect the real IP address of the server behind a cloud-based WAF to bypass its protection.
Next-Gen WAF Trends
The future of WAF technology is focused on enhancing its capabilities to stay ahead of evolving threats:
- Intelligent Threat Hunting: Next-gen WAFs will use advanced analytics and machine learning to proactively hunt for threats and identify new attack vectors.
- Full Traffic Auditing: Comprehensive logging and auditing of web traffic will enable organizations to detect anomalies and respond to incidents more effectively.
- Adaptive Policies: WAFs will adapt their policies in real time based on the threat landscape and user behavior.
- WAAP Ecosystem Integration: The integration of Web Application and API Protection (WAAP) solutions will provide a more holistic approach to security, combining WAF capabilities with specialized API protection.
Market Projections
The market for next-generation WAFs is expected to grow significantly in the coming years. By 2025, it is projected that over 50% of the WAF market will be dominated by next-gen solutions. This growth is driven by the increasing sophistication of web attacks and the need for more advanced protection mechanisms. Cloud-based deployments are also expected to continue to rise, as organizations seek scalable and cost-effective security solutions.
Conclusion
Web Application Firewalls are essential tools in the modern security landscape, providing critical protection against a wide range of web-based threats. As technology continues to evolve, so too must WAFs, adapting to new challenges and offering more advanced capabilities to ensure the security of web applications and APIs.
Tencent EdgeOne provides a robust Web Application Firewall (WAF) as part of its security solutions. Here are some key features of the WAF:
- Protection Against Diverse Threats: The WAF protects against a wide range of web application threats, including SQL injection, Cross-Site Scripting (XSS), and other common web exploits.
- DDoS Mitigation: Along with the WAF, Tencent EdgeOne also provides DDoS mitigation services. This helps to protect your applications from Distributed Denial of Service attacks, which can cause significant disruption.
- Global Coverage: Based on Tencent's global edge nodes, the WAF provides global coverage. This means your applications are protected no matter where your users are located.
- Integration with Other Services: The WAF seamlessly integrates with other services provided by Tencent EdgeOne, such as CDN acceleration and DNS services. This provides a comprehensive solution for improving your applications' performance and security.
- Suitable for Various Industries: Tencent EdgeOne's WAF safeguards diverse industries such as e-commerce, retail, finance service, content and news, and gaming, improving their user experience.
Sign Up to begin your journey with us!

