What is Web Security: A Comprehensive Guide to Threats, Defenses, and Best Practices

In the digital age, web security has become a critical concern for individuals, businesses, and governments worldwide. As our lives increasingly move online, the protection of sensitive information and digital assets has never been more important. Web security encompasses a range of practices, technologies, and protocols designed to safeguard websites, web applications, and user data from cyber threats. This article explores the multifaceted world of web security, highlighting its importance, common threats, essential measures, and future trends.
What is Web Security?
Web security refers to the protective measures and protocols implemented to safeguard websites, web applications, web services, and users from security threats, attacks, and vulnerabilities. It encompasses a broad range of technologies, practices, and policies designed to protect the web ecosystem from unauthorized access, data breaches, and other malicious activities. Web security involves securing both the client-side (browser) and server-side components, as well as the data transmission channels between them.
Why Web Security Is Important
Web security has become critically important for several reasons:
- Expanding Digital Footprint: As organizations and individuals conduct more activities online, the potential impact of security breaches increases exponentially.
- Sophisticated Threats: Cyber attacks are becoming increasingly sophisticated, with attackers developing new techniques to exploit vulnerabilities.
- Data Value: The monetary and strategic value of data continues to rise, creating stronger incentives for attackers.
- Regulatory Requirements: Laws like GDPR, CCPA, and industry-specific regulations mandate specific security measures to protect user data.
- Interconnected Systems: Modern web applications rarely operate in isolation, creating complex security dependencies between services.
- Reputation Management: Security breaches can severely damage organizational reputation and consumer trust, often with long-lasting consequences.
How Web Security Impacts Individuals and Businesses
Impact on Individuals
- Personal Data Protection: Web security safeguards sensitive personal information from identity theft and fraud.
- Financial Security: Protects financial data and prevents unauthorized transactions.
- Privacy Preservation: Ensures personal communications and activities remain private.
- Digital Trust: Enables individuals to use online services with confidence.
- Device Security: Prevents malware infections that could compromise personal devices.
Impact on Businesses
- Financial Implications: Security breaches cost businesses an average of $4.35 million per incident (as of 2022), including direct costs, fines, and remediation expenses.
- Operational Continuity: Web security ensures business operations remain uninterrupted by cyber attacks.
- Customer Trust: Strong security practices build customer confidence and loyalty.
- Competitive Advantage: Security can differentiate businesses in industries where data protection is valued.
- Legal Compliance: Proper security measures help businesses meet regulatory requirements and avoid penalties.
- Intellectual Property Protection: Safeguards valuable business assets, including proprietary algorithms, designs, and business strategies.
Web security is not merely a technical consideration but a fundamental business requirement and a critical component of responsible digital citizenship. As our reliance on web technologies continues to grow, the importance of robust web security measures will only increase.
Web Architecture and Security Risks
Client-Server Vulnerabilities
The client-server model, which forms the backbone of modern web applications, presents a series of security challenges that developers and security professionals must understand and address.
1. Client-side
On the client side, one of the most significant risks is cross-site scripting (XSS). Attackers can inject malicious JavaScript code into web pages, which then executes in other users' browsers. This can lead to session hijacking, where the attacker gains unauthorized access to user accounts, or the defacement of websites, damaging the reputation and credibility of the affected organization. Additionally, malicious scripts can redirect users to phishing sites, tricking them into revealing sensitive information.
2. Server-side
Server-side vulnerabilities are equally concerning. Misconfigured servers, such as outdated versions of Apache or Nginx, become prime targets for distributed denial-of-service (DDoS) attacks. These attacks can overwhelm server resources, causing service disruptions and potential data loss. Furthermore, improperly secured databases can lead to data breaches, exposing sensitive information like user credentials and personal data.
3. API Security
Communication between clients and servers also poses risks. Unencrypted HTTP traffic is susceptible to eavesdropping, allowing attackers to intercept sensitive information transmitted between parties. Insecure APIs, which often handle critical backend logic, can expose vulnerabilities that attackers exploit to manipulate application behavior or access restricted data.
Attack Vectors
Understanding common attack vectors is crucial for developing effective security strategies.
1. Weak authentication
Weak authentication mechanisms, such as the use of default credentials or simple passwords, make systems vulnerable to brute-force attacks. Attackers systematically try different combinations until they gain unauthorized access, highlighting the need for strong, multi-factor authentication methods.
2. Insecure APIs
Insecurely designed APIs present another significant risk. Poorly implemented endpoints can enable data scraping, where attackers extract large amounts of sensitive information. Additionally, APIs with inadequate validation may allow injection attacks, compromising both data integrity and security.
3. Third-party dependencies
Modern web applications often rely on third-party libraries and components, which can introduce vulnerabilities. Notable examples include the Log4j vulnerability, where a widely used logging library flaw created backdoors for potential attacks. Developers must carefully manage and update these dependencies to mitigate such risks.
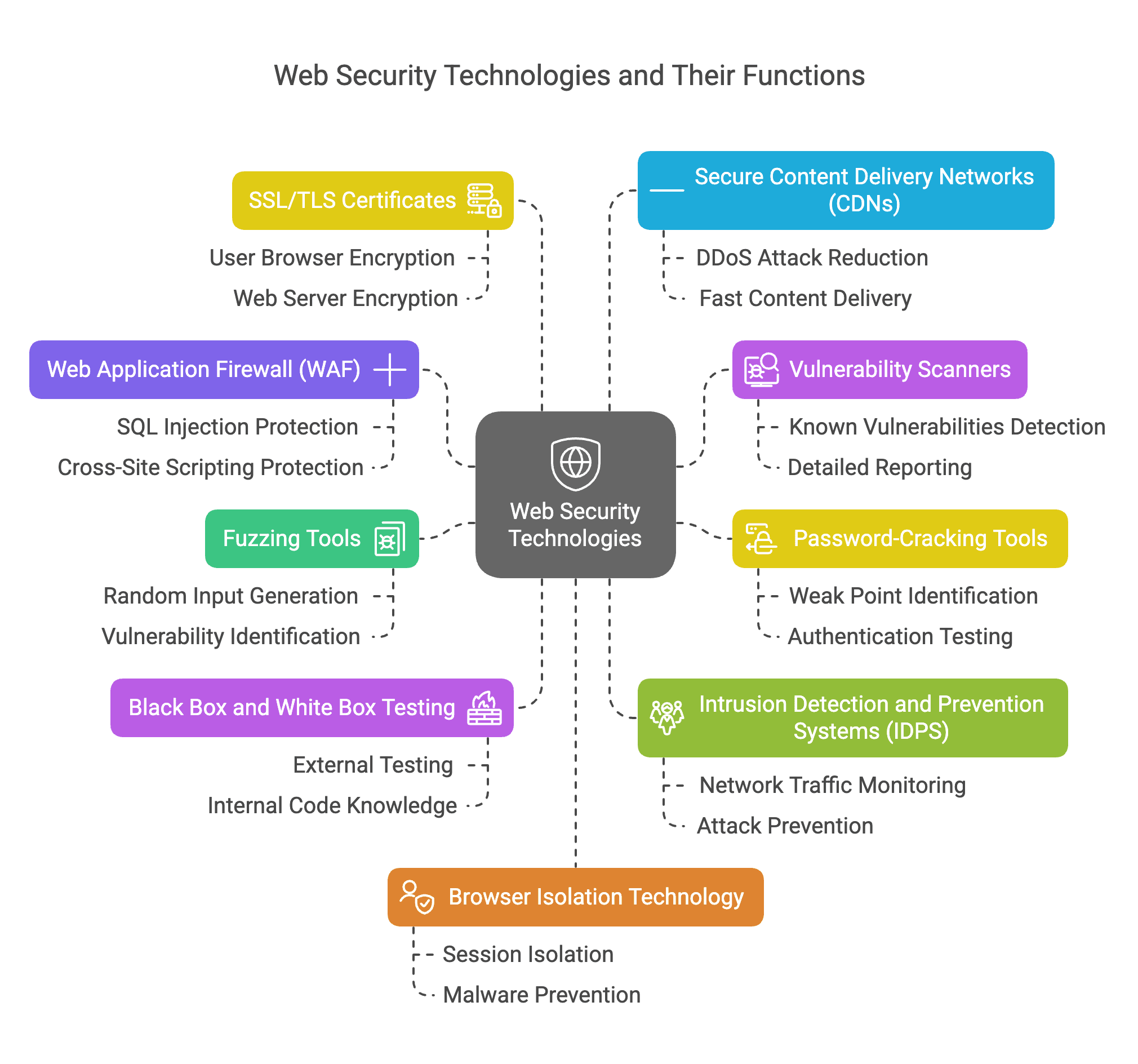
Web Security Technologies
A variety of tools and technologies are available to enhance web security. Some of the most commonly used include:
- Web Application Firewall (WAF): A WAF acts as a barrier between web applications and potential attackers, filtering out malicious traffic and protecting against common web vulnerabilities such as SQL injection and cross-site scripting (XSS).
- Vulnerability Scanners: Automated tools that scan web applications for known vulnerabilities and provide detailed reports on potential security issues.
- Password-Cracking Tools: While attackers often use these tools, they can also be used by security professionals to test the strength of passwords and identify weak points in authentication systems.
- Fuzzing Tools: These tools generate random input to test web applications for unexpected behavior and identify potential vulnerabilities.
- Black Box and White Box Testing Tools: Black box testing involves testing a web application without knowledge of its internal workings, while white box testing involves testing with full knowledge of the application's code. Both approaches help identify different types of vulnerabilities.
- Intrusion Detection and Prevention Systems (IDPS): These systems monitor network traffic for signs of suspicious activity and can take action to block or prevent potential attacks.
- SSL/TLS Certificates: Secure Sockets Layer (SSL) and Transport Layer Security (TLS) certificates are used to encrypt data transmitted between a user's browser and a web server, ensuring secure communication.
- Secure Content Delivery Networks (CDNs): CDNs can provide additional security benefits by distributing content across multiple servers, reducing the risk of DDoS attacks, and ensuring faster and more secure content delivery.
- Browser Isolation Technology: This technology isolates web browsing sessions from the user's device, preventing malware from infecting the local system.
Common Web Security Threats
The web landscape has numerous security threats that can compromise systems and data. Some of the most prevalent threats include:
1. SQL Injection: How It Works and Potential Damage
SQL injection occurs when an attacker inserts malicious SQL code into a website's database query, typically through unsanitized input fields. This can allow attackers to:
- Access sensitive data from databases
- Modify database content
- Delete entire databases
- Execute administrative operations on the database
- In some cases, issue commands to the operating system
The infamous "Bobby Tables" scenario (named after a popular web comic) illustrates how a simple malicious input like Robert'); DROP TABLE Students;-- could delete an entire database table if proper input sanitization isn't in place.
2. Cross-Site Scripting (XSS): Risks and Examples
XSS attacks involve injecting malicious scripts into websites viewed by other users. When these scripts execute in victims' browsers, they can:
- Steal session cookies and hijack user sessions
- Capture keystrokes, including passwords
- Redirect users to malicious websites
- Modify webpage content to collect sensitive information
For example, an attacker might post a comment on a blog that contains hidden JavaScript code. When other users view the comment, the script executes in their browsers, potentially stealing their authentication cookies.
3. Phishing Attacks: Techniques and Prevention
Phishing combines technical deception with social engineering to trick users into revealing sensitive information:
- Spoofed emails: Messages appearing to come from legitimate organizations
- Fake websites: Convincing replicas of trusted websites designed to steal credentials
- Spear phishing: Highly targeted attacks using personal information to increase credibility
- Clone phishing: Duplicating legitimate communications but replacing links or attachments with malicious ones
4. Malware and Ransomware: Distribution Methods and Consequences
Web-based malware distribution remains one of the most common attack vectors:
- Drive-by downloads: Malware that installs without user consent when visiting infected websites
- Malicious advertisements: Legitimate advertising networks compromised to deliver malware
- Trojanized downloads: Legitimate-seeming software that contains hidden malicious code
- Ransomware: Malware that encrypts user data and demands payment for decryption keys
These threats constantly evolve, requiring continuous vigilance and adaptive security strategies.
Essential Web Security Measures
To combat these threats, a comprehensive set of security measures is essential:
1. HTTPS: Role in Data Encryption and Secure Transmission
HTTPS (HTTP Secure) provides encrypted communications between clients and servers:
- Uses SSL/TLS protocols to establish encrypted connections
- Authenticates website identity through digital certificates
- Prevents eavesdropping, data tampering, and forgery
- Protects user privacy and sensitive information during transmission
Modern browsers now flag non-HTTPS websites as "Not Secure," making HTTPS implementation essential for maintaining user trust.
2. Input Validation: Preventing Malicious Data Entry
Proper input validation is a fundamental security practice:
- Client-side validation: Provides immediate feedback but can be bypassed
- Server-side validation: Essential for security, cannot be circumvented by attackers
- Whitelisting: Accepting only known good input patterns
- Parameterized queries: Separating code from data to prevent injection attacks
3. Data Security Management: Protecting Sensitive Information
Protecting data throughout its lifecycle is a critical component of web security:
- Data classification: Categorizing information based on sensitivity and value to apply appropriate protection levels
- Data encryption at rest: Securing stored data using encryption algorithms to prevent unauthorized access even if storage systems are compromised
- Database security: Implementing proper access controls, authentication, and encryption for database systems
- Data minimization: Collecting and retaining only necessary data to reduce attack surface
- Data masking and tokenization: Protecting sensitive information by replacing it with non-sensitive equivalents
- Data loss prevention (DLP): Implementing systems to detect and prevent unauthorized data exfiltration
- Privacy compliance: Ensuring data-handling practices comply with relevant regulations like GDPR, CCPA, and industry-specific requirements
- Data lifecycle management: Establishing policies for secure data creation, storage, usage, archiving, and deletion
- Backup and recovery: Regular data backups with encryption and secure storage to enable recovery from ransomware and other destructive attacks
4. Secure Coding Practices: Developer's Role in Building Secure Websites
Developers play a crucial role in web security:
- Following the principle of least privilege
- Implementing proper error handling that doesn't reveal sensitive information
- Avoiding hardcoded credentials in source code
- Using prepared statements for database queries
- Validating and sanitizing all user inputs
- Keeping dependencies and libraries updated
5. Regular Updates and Patches: Importance of Staying Current
Many security breaches exploit known vulnerabilities that have already been patched:
- Implementing automatic updates when possible
- Establishing patch management procedures
- Testing patches before deployment in critical systems
- Monitoring vulnerability disclosures related to used technologies
These measures form the foundation of a robust web security posture.
Best Practices for Web Security
Beyond essential measures, adopting best practices can further enhance web security:
1. Code Reviews and Security Testing: Ensuring Code Integrity
Systematic examination of application code helps identify security vulnerabilities:
- Manual code reviews: Experienced developers examining code for security flaws
- Automated static analysis: Tools that scan code for known vulnerability patterns
- Dynamic testing: Testing running applications to find runtime vulnerabilities
- Penetration testing: Simulated attacks to identify exploitable vulnerabilities
2. Access Control and Authentication Mechanisms: Limiting Unauthorized Access
Properly implemented authentication and authorization are critical:
- Multi-factor authentication: Requiring multiple verification methods
- Strong password policies: Encouraging complex, unique passwords
- Session management: Secure handling of user sessions to prevent hijacking
- Role-based access control: Limiting user permissions based on requirements
3. Security Policies and Incident Response Plans: Proactive and Reactive Strategies
Organizations need both prevention and response strategies:
- Documented security policies that define requirements and procedures
- Incident response plans that outline steps to take when breaches occur
- Regular security training for all employees
- Tabletop exercises to practice breach response scenarios
4. User Education and Awareness Programs: Empowering Users to Stay Safe
Users represent both a vulnerability and a defense:
- Training on recognizing phishing attempts
- Password management best practices
- Safe browsing habits and awareness of common threats
- Procedures for reporting suspected security incidents
These practices promote a culture of security awareness and preparedness.
Cloud-based Web Security
Cloud-based web security refers to the set of technologies, policies, and practices designed to protect web-based applications and data hosted in the cloud. It aims to safeguard against various threats, such as unauthorized access, data breaches, and cyber-attacks.
Shared Responsibility Model
Cloud-based web security operates under a shared responsibility model. The cloud service provider (CSP) is responsible for securing the underlying infrastructure, while the customer is responsible for securing the data, applications, and access controls within the cloud environment. The extent of shared responsibilities varies depending on the cloud service model (IaaS, PaaS, SaaS):
- IaaS: The customer is responsible for securing the operating system, applications, and user access, while the CSP secures the physical infrastructure.
- PaaS: The CSP secures the operating system and virtual network controls, while the customer secures the data and applications.
- SaaS: The CSP secures the entire stack, including applications and middleware, while the customer focuses on securing data and user access.
Benefits of Cloud-Based Web Security
These solutions offer several advantages, including:
- Scalability and Cost-Effectiveness: Cloud-based security services can easily scale to meet the needs of growing businesses without requiring significant upfront investment in hardware and infrastructure.
- Continuous Updates: Cloud providers can quickly deploy updates and patches to protect against the latest threats, ensuring that security measures are always up-to-date.
- Global Threat Intelligence: Cloud-based security solutions often leverage global threat intelligence to detect and respond to emerging threats in real time.
- Improved Performance: By offloading security processing to the cloud, businesses can improve the performance of their web applications and reduce the burden on their local infrastructure.
- Compliance Support: Cloud-based security services can help businesses meet regulatory compliance requirements by providing detailed logs and reports of security activities.
Emerging Trends and Future Outlook
The field of web security is continually evolving, driven by technological advancements and changing threat landscapes.
1. AI and Machine Learning in Threat Detection
Artificial intelligence is transforming both attacks and defenses:
- Machine learning systems that identify unusual patterns suggesting attacks
- Behavioral analysis to detect account compromises
- Automated response systems that can counter attacks in real-time
- Unfortunately, attackers are also using AI to develop more sophisticated threats
2. Zero-Trust Architecture: A New Approach to Security
The zero-trust model represents a paradigm shift in security thinking:
- Eliminating implicit trust within networks
- Requiring verification for every access attempt
- Implementing least-privilege access controls
- Continuous monitoring and validation
3. Impact of Regulations on Web Security Practices
Legal frameworks increasingly influence security implementation:
- GDPR in Europe enforcing data protection requirements
- CCPA and other state laws in the US
- Industry-specific regulations like HIPAA for healthcare
- International standards like ISO 27001 guiding security practices
4. Predictions for the Evolving Web Security Landscape
The security field continues to evolve rapidly:
- Increased adoption of passwordless authentication
- Growing focus on API security as applications become more interconnected
- Rising importance of supply chain security
- Greater integration of security into development processes (DevSecOps)
Looking ahead, the future of web security will demand continuous innovation, collaboration, and adaptability to protect our increasingly digital world.
Protecting Your Web Security with EdgeOne
EdgeOne Web Protection is a cloud-native security solution that integrates enterprise-grade web application protection with global edge computing infrastructure and integrates AI algorithms to enhance web security and performance. Designed for modern cyber threats, it provides multi-layered defense through:
- AI-powered Threat Detection: EdgeOne employs an AI engine that leverages Tencent's extensive threat information database, which contains over 100 million records. This AI engine serves as a smarter threat recognition kernel, capable of accurately identifying and blocking web threats such as SQL injection, XSS attacks, and local file inclusion.
- Bot Behavior Analysis: The platform integrates AI technology to analyze and model user request behaviors comprehensively. This feature intelligently identifies abnormal traffic and differentiates between legitimate and malicious bots. It supports custom session protection policies to further enhance security.
- Rate-limiting and CC Attack Protection: EdgeOne's AI-driven rate-limiting technology uses adaptive algorithms to detect and mitigate CC attacks. It analyzes traffic patterns in real time and applies custom rules to filter out malicious requests, ensuring stable service performance.
- Edge AI Computing: EdgeOne is designed to support edge AI computing, allowing lightweight AI models to be deployed at the edge nodes. This capability enables real-time decision-making and reduces latency by processing data closer to the user. It is particularly useful for applications requiring rapid response, such as traffic monitoring and smart manufacturing.
- Smart Web Protection: By combining AI algorithms with Tencent's vast web attack sample library, EdgeOne matches request characteristics to identify and block malicious activities. This AI-driven approach ensures that web applications are protected in real time against evolving threats.
EdgeOne Web Protection is designed to empower enterprises with robust, next-generation security at the edge, ensuring that digital assets remain protected against even the most sophisticated threats. Now we have launched a free trial for a quick start. Sign up to join us!
Conclusion
Web security is a critical component of modern digital infrastructure. With the increasing sophistication of cyber threats, individuals and organizations need to understand the importance of web security and take proactive measures to protect their websites and applications. By implementing a comprehensive web security strategy that includes both technical tools and best practices, businesses can reduce the risk of security breaches and ensure a safe and secure online environment for their users.
FAQs about Web Security
1. What is web security?
Web security refers to the measures and practices used to protect websites, web applications, and their users from cyber threats. It involves safeguarding sensitive data, maintaining system integrity, and ensuring a secure user experience.
2. Why is web security important?
Web security is crucial because it helps protect against data breaches, financial losses, and reputational damage. It also ensures that users can trust your website or application, which is essential for maintaining customer loyalty and business success.
3. What are the most common web security threats?
Common web security threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), session hijacking, and DDoS attacks. These threats can compromise user data, steal sensitive information, or disrupt website operations.
4. How can I protect my website from attacks?
To protect your website, you should implement a multi-layered security approach. This includes using strong authentication methods, encrypting data, regularly updating software, conducting vulnerability scans, and employing security tools like Web Application Firewalls (WAFs) and Intrusion Detection Systems (IDSs).
5. What is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) is a security tool that filters and monitors HTTP traffic between a web application and the internet. It helps protect against common web vulnerabilities, such as SQL injection and XSS, by blocking malicious traffic.
6. How does SSL/TLS help with web security?
SSL/TLS certificates encrypt data transmitted between a user's browser and a web server. This ensures that sensitive information, such as login credentials and financial data, remains confidential and secure from eavesdropping and tampering.
7. What is the difference between black box and white box testing?
Black box testing involves testing a web application without knowledge of its internal workings, focusing on external inputs and outputs. White box testing, on the other hand, involves testing with full knowledge of the application's code, allowing for a more in-depth analysis of potential vulnerabilities.
8. What is phishing, and how can I protect against it?
Phishing is a type of cyber attack where attackers trick users into providing sensitive information through fake websites or emails. To protect against phishing, users should be educated to recognize suspicious links and emails, and organizations should implement multi-factor authentication to add an extra layer of security.
9. What are some best practices for web security?
Some best practices for web security include conducting regular security audits, keeping software up-to-date, using strong passwords and multi-factor authentication, training users to recognize threats, and implementing a comprehensive security strategy that includes both technical and administrative controls.
10. How can I stay informed about the latest web security threats and trends?
Staying informed about web security threats and trends is essential. You can follow security blogs, subscribe to newsletters from cybersecurity companies, join online forums and communities, and attend webinars and conferences. Additionally, keeping up-to-date with security certifications and training can help you stay ahead of emerging threats.

