In today's digital age, where websites and web applications form the backbone of online interactions and transactions, web security has become a crucial concern for individuals, businesses, and organizations alike. Web security encompasses a wide range of strategies, technologies, and protocols designed to safeguard sensitive data, maintain the integrity of online systems, and ensure a secure user experience. Understanding the importance of web security is essential for anyone involved in web development, IT management, or simply using the internet for daily activities.
What is Web Security?
Web security refers to the measures and practices used to protect websites, web applications, and their users from various threats and vulnerabilities. It encompasses a wide range of strategies and technologies designed to safeguard data, maintain privacy, and ensure the reliability and integrity of web-based systems.
How Web Security Works
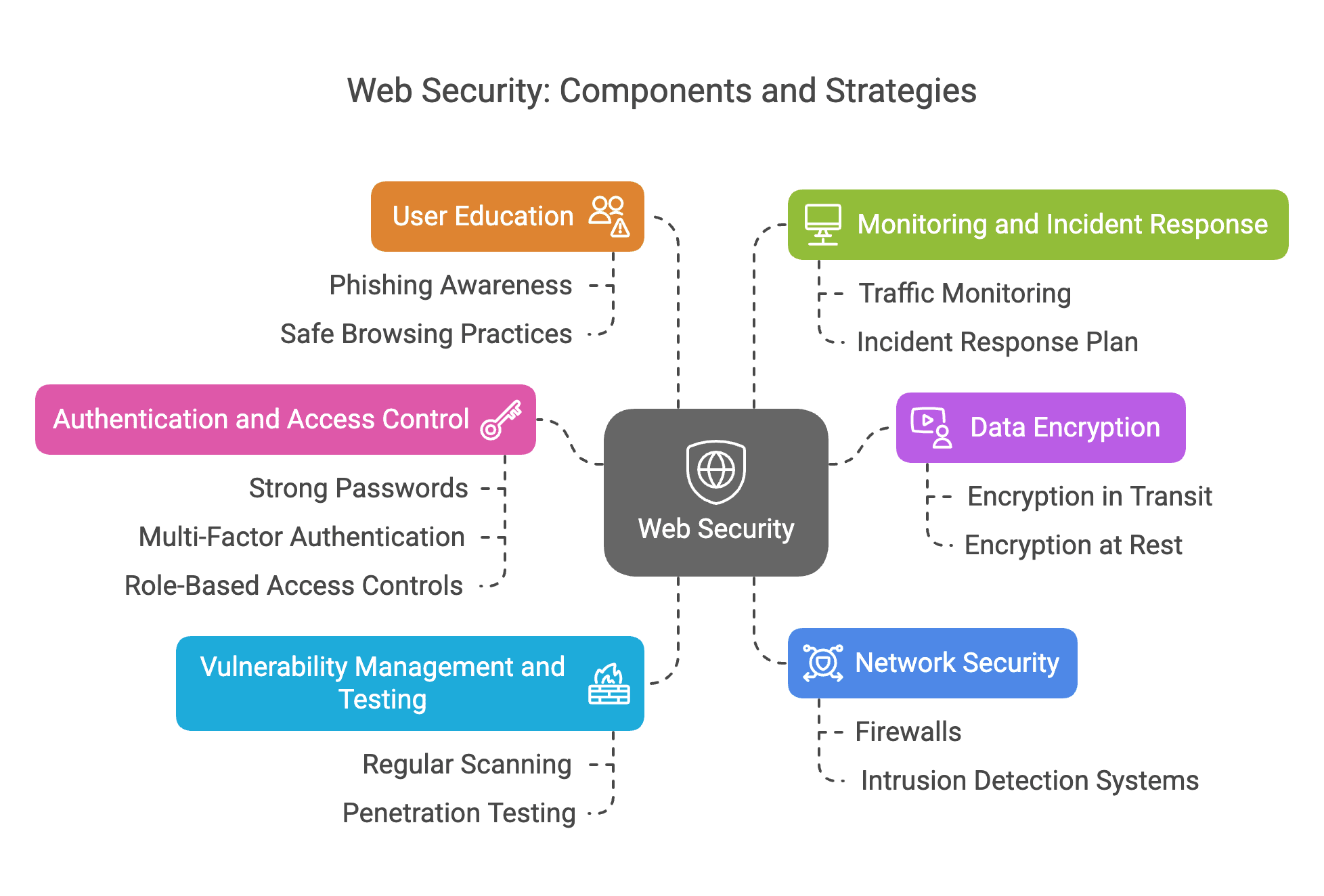
Web security employs a multi-layered approach to protect against various threats. Key components of web security include:
- Authentication and Access Control: Ensuring that only authorized users can access specific parts of a website or application. This is typically achieved through strong passwords, multi-factor authentication, and role-based access controls.
- Data Encryption: Encrypting data both in transit and at rest to prevent unauthorized access. This ensures that even if data is intercepted, it remains unreadable without the encryption key.
- Vulnerability Management and Testing: Regularly scanning for vulnerabilities in web applications and conducting penetration testing to identify and fix security weaknesses before they can be exploited by attackers.
- Network Security: Implementing firewalls, intrusion detection systems, and other network security measures to protect the underlying infrastructure of websites and applications.
- User Education: Training users to recognize and avoid common security threats such as phishing emails, suspicious links, and unsafe downloads. Educated users are less likely to inadvertently compromise security.
- Monitoring and Incident Response: Continuously monitoring web traffic and system activity to detect and respond to security incidents in real time. This includes having an incident response plan in place to quickly address and mitigate any security breaches.
Why is Web Security Important?
- Protects sensitive data: Web security safeguards personal and organizational data such as passwords, credit card details, and confidential business information. Without it, attackers could steal this data, leading to identity theft, financial loss, and reputational damage.
- Maintains user trust: When users know a website is secure, they are more likely to engage with it. Trust is crucial for e-commerce sites where users share payment details. A breach can drive users away permanently.
- Prevents malware spread: A secure website prevents the injection and spread of malware. This protects both the website's visitors and the website itself from being used as a vector for infecting other systems.
- Complies with regulations: Many industries have strict data protection regulations like GDPR or HIPAA. Web security ensures compliance, avoiding hefty fines and legal issues for businesses handling sensitive information.
- Reduces downtime: Security breaches often cause websites to crash or be taken offline. Robust web security minimizes the risk of such incidents, ensuring continuous availability and a smooth user experience.
- Enhances brand reputation: A secure website reflects a responsible and trustworthy brand. It shows that the organization values user safety and is committed to protecting their interests, which can enhance the overall brand image.
Web security encompasses the protective measures and protocols implemented to safeguard websites, web applications, and web services against security threats and vulnerabilities. In an era where organizations conduct critical business operations online and store sensitive customer data on web servers, robust security measures are no longer optional but essential.
Common Web Security Threats
The digital landscape is fraught with numerous threats that can compromise the security of websites and applications. Some of the most common web security threats include:
1. Injection Attacks
Injection vulnerabilities remain among the most prevalent and dangerous web security threats. SQL injections occur when attackers insert malicious SQL code into database queries, potentially gaining unauthorized access to sensitive information. Cross-Site Scripting (XSS) involves injecting malicious scripts into web pages viewed by others, allowing attackers to hijack user sessions or redirect users to malicious sites. Cross-Site Request Forgery (CSRF) tricks authenticated users into performing unwanted actions on websites where they're logged in.
2. Authentication Vulnerabilities
Authentication systems often represent a weak link in web security. Common issues include weak password policies, absence of multi-factor authentication, and insecure credential storage. Brute force attacks, credential stuffing, and session hijacking are frequently used to exploit these vulnerabilities, giving attackers unauthorized access to user accounts.
3. Sensitive Data Exposure
Inadequate protection of sensitive data remains a critical issue. Many applications fail to properly encrypt data at rest or in transit, exposing personal information, financial details, or authentication credentials to potential interception or theft. This exposure can lead to severe consequences, including identity theft, financial fraud, and regulatory penalties.
4. Security Misconfigurations
Security misconfigurations represent low-hanging fruit for attackers. These include default installations, incomplete configurations, open cloud storage, error messages containing sensitive information, and unnecessary services running on the server. Proper configuration management is essential but often overlooked.
5. Broken Access Control
Access control failures can allow attackers to access unauthorized functionality or data. These vulnerabilities include bypassing access control checks, elevating privileges, or manipulating access control tokens. Without proper restrictions, users might access sensitive files, modify permissions, or view other users' data.
6. Advanced Persistent Threats
Advanced Persistent Threats (APTs) involve sophisticated attackers who gain access to systems and remain undetected for extended periods. These threat actors often use multiple attack vectors and advanced techniques to maintain persistent access while extracting sensitive data or compromising system functionality.
Best Practices for Web Security
Implementing effective web security requires a combination of technical measures and best practices. Some key best practices include:
1. Essential Security Measures
HTTPS Implementation and SSL/TLS
HTTPS has become the standard for secure web communication. By implementing SSL/TLS certificates, websites encrypt data transmitted between servers and clients, preventing eavesdropping and man-in-the-middle attacks. Modern implementations should use TLS 1.2 or 1.3, with older protocols disabled to prevent downgrade attacks.
Secure Authentication Mechanisms
Strong authentication systems represent the first line of defense against unauthorized access. Best practices include implementing multi-factor authentication, enforcing strong password policies, using secure password hashing algorithms (like bcrypt or Argon2), and implementing account lockout mechanisms to prevent brute force attacks.
Input Validation and Sanitization
All user inputs should be treated as potentially malicious. Comprehensive input validation includes checking data types, length, format, and range. Server-side validation is essential, while client-side validation improves user experience. Proper sanitization removes potentially dangerous characters or scripts before processing or storing data.
Session Management
Secure session management prevents attackers from hijacking user sessions. Best practices include generating strong session identifiers, implementing appropriate timeouts, securely storing session data, and invalidating sessions after logout. Regenerating session IDs after authentication helps mitigate session fixation attacks.
Security Headers and Cookies
HTTP security headers provide an additional layer of protection against various attacks. Content-Security-Policy prevents XSS attacks by specifying trusted content sources. X-Frame-Options prevents clickjacking. Strict-Transport-Security enforces HTTPS. Cookies should be configured with secure attributes like HttpOnly and SameSite to prevent client-side access and CSRF attacks.
2. Security in Web Development
Secure Coding Practices
Security must be integrated throughout the development lifecycle, not added as an afterthought. Developers should follow secure coding guidelines, conduct regular code reviews focused on security, and participate in security training. Common principles include least privilege, defense in depth, failing securely, and minimizing the attack surface.
OWASP Top 10 Awareness
The OWASP Top 10 represents the most critical web application security risks. Development teams should be familiar with these risks and implement specific controls to address each one. Regular updates to the OWASP list reflect the evolving threat landscape and should inform ongoing security efforts.
Security Frameworks and Libraries
Leveraging established security frameworks and libraries can significantly enhance application security. These tools provide pre-built components for authentication, authorization, input validation, and other security functions. However, teams must ensure these dependencies are regularly updated to address newly discovered vulnerabilities.
Dependency Management and Updates
Many security breaches exploit known vulnerabilities in third-party components. Organizations must maintain an inventory of all dependencies, regularly check for security updates, and implement a patch management process. Automated tools can scan dependencies for known vulnerabilities and alert teams when updates are needed.
3. Testing and Validation
Vulnerability Scanning Techniques
Regular vulnerability scanning identifies security weaknesses before attackers can exploit them. Automated scanners can detect common vulnerabilities like misconfigurations, outdated software, and known security issues. Both authenticated and unauthenticated scans should be performed to provide comprehensive coverage.
Penetration Testing Methodologies
Penetration testing involves simulating real-world attacks to identify vulnerabilities that automated scanners might miss. These controlled attacks evaluate the effectiveness of security controls and uncover complex vulnerabilities that require human expertise to detect. Regular penetration testing should be conducted by skilled professionals, especially after significant changes.
Code Reviews for Security
Security-focused code reviews help identify vulnerabilities during development. Reviewers should look for issues like hardcoded credentials, insecure cryptographic implementations, and logic flaws that could lead to security breaches. Automated static analysis tools can complement manual reviews by flagging potential issues.
Automated Security Testing Tools
Integrating security testing into CI/CD pipelines enables early detection of vulnerabilities. Dynamic Application Security Testing (DAST) tools analyze running applications, while Static Application Security Testing (SAST) tools analyze source code. Interactive Application Security Testing (IAST) combines both approaches for more comprehensive coverage.
4. Organizational Security Strategies
Security Policies and Procedures
Clear security policies establish expectations and requirements for protecting web assets. These policies should cover areas like access control, password management, incident response, and acceptable use. Regular reviews ensure policies remain relevant as technology and threats evolve.
Employee Training and Awareness
Human error remains a significant factor in security breaches. Regular security awareness training helps employees recognize phishing attempts, understand secure development practices, and follow organizational security policies. Simulated phishing exercises can reinforce training by providing practical experience.
Incident Response Planning
Despite best efforts, security incidents will occur. A well-defined incident response plan enables organizations to detect, contain, and recover from breaches quickly. The plan should define roles and responsibilities, communication procedures, and steps for identifying, evaluating, and remediating security incidents.
Compliance Requirements
Organizations must navigate complex regulatory requirements like GDPR, CCPA, PCI DSS, and HIPAA. These regulations establish baseline security requirements and impose penalties for non-compliance. A comprehensive compliance program helps organizations meet these requirements while improving overall security posture.
Emerging Trends in Web Security
AI and Machine Learning Applications
Artificial intelligence and machine learning are increasingly applied to both attack and defense strategies. Security tools leverage these technologies to detect anomalous behavior, predict potential threats, and automate responses to attacks. However, attackers also use AI to develop more sophisticated phishing campaigns and identify vulnerabilities.
DevSecOps Integration
DevSecOps integrates security throughout the development lifecycle rather than treating it as a separate phase. This approach emphasizes collaboration between development, operations, and security teams. Automated security testing, infrastructure as code security checks, and secure CI/CD pipelines are key components of successful DevSecOps implementation.
Zero Trust Architecture
The Zero Trust model assumes no user or system should be inherently trusted, even those inside the network perimeter. This approach requires verification for all access requests, applies least-privilege principles, and monitors all activities. For web applications, this means continuous authentication, detailed access controls, and comprehensive logging.
Cloud Security Considerations
As organizations migrate to cloud environments, security approaches must adapt. Cloud security requires shared responsibility between providers and customers. Organizations must understand which security aspects they're responsible for and implement appropriate controls for data protection, access management, and compliance in cloud environments.
How EdgeOne Protects Your Web Security
1. Comprehensive Edge Protection
EdgeOne delivers integrated security at the network edge, combining CDN performance with enterprise-grade protection. This unified approach eliminates security gaps while reducing management complexity and securing web applications, APIs, and critical assets before threats reach your infrastructure.
2. Multi-layered Defense System
EdgeOne's security architecture provides defense-in-depth through multiple coordinated protection layers:
- Web Application Firewall (WAF): Blocks OWASP Top 10 threats including injection attacks, XSS, and authentication vulnerabilities using continuously updated rule sets
- DDoS Protection: Automatically mitigates volumetric attacks with scalable filtering capacity that absorbs even the largest attack traffic
- Bot Management: Distinguishes between legitimate users, good bots, and malicious automation using behavioral analysis and machine learning
- API Security: Protects API endpoints with specialized validation, rate limiting, and schema enforcement
3. Real-time Threat Intelligence
EdgeOne leverages global threat data across its network to provide proactive protection. When an attack targets any customer, defensive measures are immediately propagated across the entire platform, creating collective immunity against emerging threats.
4. Zero-Trust Implementation
The platform enforces rigorous authentication and authorization at every access point, implementing zero-trust principles through:
- Identity-based access controls
- Contextual authentication
- Continuous session validation
- Granular permission enforcement
5. Business Benefits
Organizations implementing EdgeOne gain significant advantages:
- Reduced security management overhead
- Improved performance through integrated CDN
- Enhanced visibility with unified security analytics
- Simplified compliance with regulatory requirements
- Protection that scales automatically with traffic demands
EdgeOne transforms security from a resource-intensive challenge into a business enabler, providing comprehensive protection without sacrificing performance or user experience. By moving security to the edge, threats are neutralized before reaching your origin infrastructure, dramatically reducing risk exposure while optimizing resource utilization.
Conclusion
Web security is a continuous battle against evolving threats. By combining technical defenses (HTTPS, secure coding), proactive policies (penetration testing), and user education, organizations can build resilient systems. As cybercriminals grow sophisticated, adopting AI-driven tools and zero-trust frameworks will define the next era of web security.

