Application Security: Protecting Software in an Interconnected World

Twenty years ago, most security breaches targeted network infrastructure. Today, attackers have shifted their focus dramatically—94% of security incidents now involve application layer attacks. Look at any recent headline-making breach, from Change Healthcare to Snowflake, and you'll find vulnerable code at the center of the story.
The stakes keep rising. Organizations now run on software, with the average enterprise using over 900 different applications. Critical infrastructure, financial systems, healthcare services, and transportation networks all depend on code that was often written under tight deadlines with features prioritized over security. Meanwhile, attackers have grown remarkably sophisticated, using automated tools to scan for vulnerabilities across thousands of targets simultaneously.
Despite these threats, many development teams still treat security as a compliance checkbox rather than a core requirement. This disconnect creates a perfect storm: rapidly developed applications with expanding attack surfaces facing increasingly determined adversaries. Breaking this cycle requires a fundamental shift from treating security as an afterthought to making it an integral part of how software gets built.
What is Application Security?
Application security—or AppSec—protects software applications from threats by identifying and fixing security vulnerabilities throughout the development process. Unlike network security, which defends infrastructure, application security tackles flaws in the code itself—from design-level architecture problems to implementation bugs that attackers can exploit.
Effective application security spans the entire software lifecycle:
- Pre-development: Security architects conduct threat modeling sessions that identify potential attack vectors before coding begins. These sessions ask critical questions: "Where would attackers target this system?" and "What would they gain by compromising it?"
- Development: Developers follow secure coding guidelines that prevent common vulnerabilities like injection flaws. Security-focused code reviews catch issues that automated tools might miss.
- Testing: Security testing tools scan code for weaknesses, while QA creates test cases specifically designed to verify security controls work as expected.
- Deployment: Security teams verify secure configurations and validate that production environments don't introduce new risks to hardened code.
- Post-deployment: Runtime protection and monitoring detect attacks against live applications, while vulnerability management processes address new threats as they emerge.
Modern application security has evolved beyond the old "security as a gate" model. Instead of blocking releases with last-minute security reviews, effective AppSec programs provide developers with tools, training, and feedback throughout the development process—making security a built-in feature rather than a hurdle to overcome.
What is the Role of Application Security?
Application security serves a unique function that bridges the traditional divide between development teams focused on building features and security teams concerned with defending systems. This gap often leads to friction—developers feel security slows them down, while security professionals worry about vulnerabilities being pushed to production.
In practice, application security translates abstract security requirements into concrete implementation guidance. When regulations mandate "secure authentication," application security defines exactly what that means: password complexity rules, multi-factor authentication requirements, session timeout limits, and so on. This translation makes security actionable for development teams.
The function also serves as an early warning system for emerging threats. When new vulnerability classes emerge—like the Log4Shell vulnerability that sent security teams scrambling in late 2021—application security professionals assess the organization's exposure, prioritize remediation efforts, and develop compensating controls.
Most importantly, mature application security programs fundamentally change how organizations build software. Through developer education, security champions programs, and integrated tooling, they create a culture where security becomes everyone's responsibility rather than being outsourced to a specialized team. The most successful organizations don't treat security as a separate concern but as an integral quality attribute—just like performance, reliability, and usability.
Types of Application Security
As applications have diversified across platforms and deployment models, application security has specialized to address unique threats in different environments:
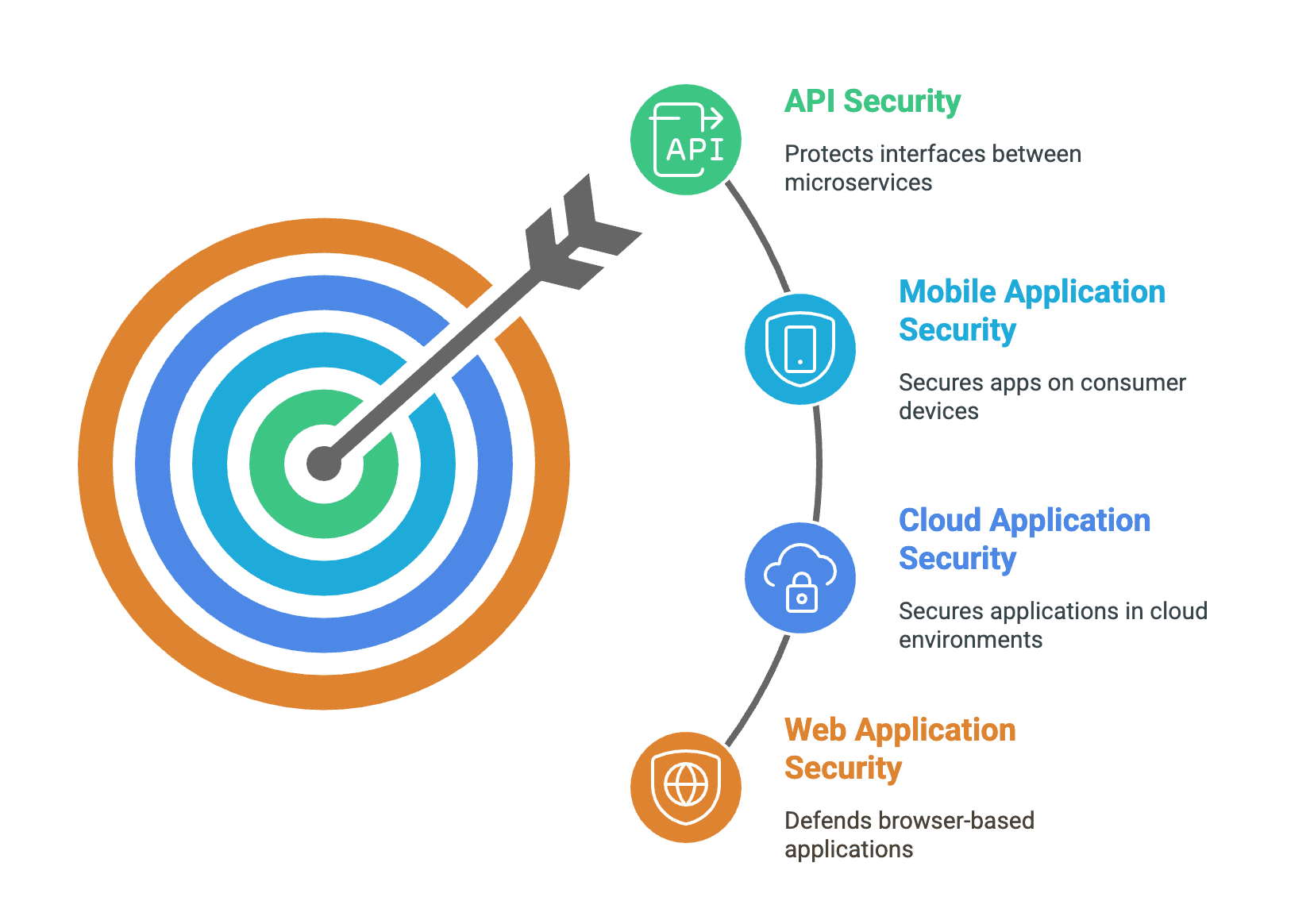
Web Application Security
Web application security defends browser-based applications against a barrage of attacks targeting their exposed interfaces. These applications present an attractive target because they're publicly accessible and often the gateway to valuable data. Just one unvalidated input field can lead to SQL injection attacks that extract entire databases, while a single cross-site scripting vulnerability can compromise user accounts.
The OWASP Top Ten—a list of the most critical web application security risks—serves as an essential baseline for protection, though it barely scratches the surface of potential vulnerabilities. Modern defenses combine secure development practices with runtime protections: validating all inputs, implementing proper authentication workflows, managing sessions securely, and encrypting sensitive data both in transit and at rest.
Cloud Application Security
The distributed nature of cloud environments has completely transformed how applications must be secured. Cloud application security addresses the complex challenge of protecting applications across environments where traditional security perimeters don't exist and infrastructure changes constantly.
Under the shared responsibility model, security duties are divided between cloud providers and their customers—often with dangerous gaps when responsibilities aren't clearly defined. While providers secure the underlying infrastructure, customers must still implement proper access controls, secure their configurations, protect their data, and monitor for unusual activity.
Cloud-native applications bring additional complexity through their use of microservices, containers, and serverless functions—each component requiring specific security controls. Misconfigurations have become the leading cause of cloud security incidents, with simple mistakes like public S3 buckets or excessive IAM permissions leading to massive data exposures.
Mobile Application Security
Mobile application security tackles the unique challenges of securing apps that run on consumer devices beyond organizational control. These applications face threats from multiple directions: malicious apps that might access their data, network-based attacks against their communications, and even physical device compromise.
Security for mobile apps must account for how they handle sensitive data on devices that could be lost, stolen, or compromised. Techniques like certificate pinning prevent man-in-the-middle attacks against API communications, while secure local storage mechanisms protect data at rest through encryption. Code obfuscation deters reverse engineering attempts, making it harder for attackers to understand how applications work or locate security weaknesses.
The fragmented mobile ecosystem creates additional challenges, with iOS and Android presenting different security models and constraints that security professionals must navigate. Each platform requires specific security approaches—from app permissions to secure storage mechanisms.
API Security
As applications have been decomposed into microservices, APIs have become the connective tissue holding these components together—and a prime target for attackers. API security focuses on protecting these crucial interfaces from exploitation through robust authentication, careful authorization, input validation, and rate limiting to prevent abuse.
The widespread adoption of REST and GraphQL APIs has created new attack surfaces that traditional security tools often miss. Organizations frequently discover "shadow APIs"—undocumented endpoints that were created for internal use but inadvertently exposed to the internet. These forgotten interfaces often lack proper security controls and provide attackers with backdoor access to critical systems.
Application Security Tools
The application security toolbox has grown significantly as development practices have evolved. Modern AppSec programs leverage several complementary technologies:
Static Application Security Testing (SAST)
SAST tools analyze application source code, bytecode, or binaries to identify security flaws without executing the program. Think of them as sophisticated code reviewers that never get tired or distracted. These tools excel at finding vulnerabilities like buffer overflows, SQL injection flaws, and hardcoded credentials.
By integrating SAST into development environments, teams catch vulnerabilities during coding rather than after completion. This shift-left approach dramatically reduces remediation costs—fixing issues during development costs a fraction of addressing them after release.
Advanced SAST tools understand code context and dataflow, reducing false positives that plague earlier generations. They can trace how user input moves through an application, identifying points where it might be used unsafely in database queries, operating system commands, or output rendering.
Dynamic Application Security Testing (DAST)
DAST tools approach applications from an attacker's perspective, testing running applications by sending malicious inputs and analyzing responses. By interacting with applications as they actually operate, DAST finds vulnerabilities that static analysis might miss—particularly issues related to runtime behavior, server configurations, and authentication workflows.
The black-box nature of DAST means it works without access to source code, making it valuable for testing third-party applications and services. However, DAST typically identifies symptoms rather than root causes, finding the manifestation of vulnerabilities without pinpointing the exact line of code responsible.
Software Composition Analysis (SCA)
Modern applications are assembled more than written, with up to 85% of typical codebases consisting of open-source components. SCA tools identify these third-party components and detect known vulnerabilities within them, essentially providing an "ingredients list" with security warnings.
Beyond identifying vulnerabilities, advanced SCA tools analyze license compliance, component age, and maintenance status. A component with security issues that's actively maintained may represent less risk than a "secure" component that hasn't been updated in years.
With supply chain attacks increasing dramatically, SCA has become essential for managing third-party risk. The compromise of a single widely-used component can affect thousands of downstream applications, as demonstrated by major incidents like the event-stream attack.
Runtime Application Self-Protection (RASP)
RASP tools integrate directly into applications, monitoring behavior and blocking attacks in real-time. Unlike perimeter defenses that lack application context, RASP understands application logic and can distinguish between normal and malicious operations.
This technology acts as a last line of defense, protecting applications even when they contain unpatched vulnerabilities. When a vulnerability can't be immediately fixed—perhaps due to complexity or business constraints—RASP provides compensating controls that prevent exploitation while development teams work on permanent solutions.
Real-World Examples of Application Security
Abstract security concepts become concrete through real-world examples:
Banking Application Protection
A major retail bank discovered through penetration testing that their mobile banking application stored authentication tokens insecurely. An attacker with physical access to a device could potentially extract these tokens and gain unauthorized account access. Rather than accepting this risk, they implemented a comprehensive security overhaul.
The bank deployed application shielding technology that prevented debugging and tampering, securely encrypted sensitive data using the device's hardware security modules, and implemented certificate pinning to prevent API communications from being intercepted. They also added behavioral biometrics that could detect unusual patterns in how users interacted with the app.
When a sophisticated attack campaign later targeted multiple banks in their region, these measures prevented exploitation while several competitors suffered breaches. The security investment delivered clear ROI through avoided breach costs, preserved customer trust, and prevention of regulatory penalties.
E-commerce Platform Security
An online electronics retailer experienced the nightmare scenario: hackers injected credit card skimming code into their checkout flow through an SQL injection vulnerability. Before the breach was detected, thousands of customer credit card numbers were stolen.
The incident triggered a complete security transformation. The company implemented security champions in each development team, conducted secure coding workshops for all developers, and integrated automated security testing into their CI/CD pipeline. They migrated to a tokenized payment system that reduced PCI scope and implemented a bug bounty program that rewarded security researchers for responsibly reporting vulnerabilities.
These measures proved effective when the security scanning system detected and blocked an attempted follow-up attack six months later. The investment not only prevented another breach but became a competitive advantage as the company highlighted their security practices in marketing materials.
Healthcare Software Protection
After several ransomware incidents hit the healthcare sector, a medical records software vendor recognized their application could be a vector for attacks against hospitals. They implemented application security by design, starting with comprehensive threat modeling for each module.
Their approach included strict input validation for all data entry points, granular access controls based on clinical roles, automatically encrypting sensitive patient data, and rigorous validation of all third-party components. The development team created custom security test cases that simulated known attack patterns against healthcare systems.
When a major ransomware campaign later targeted their customer base, hospitals using their software maintained operational continuity while others experienced critical disruptions. The application's security architecture prevented the malware from encrypting patient data, allowing healthcare providers to continue treating patients while they remediated their infrastructure.
The Critical Importance of Application Security
The business case for application security has never been stronger:
Data breach costs have reached record levels, averaging $4.88 million per incident according to IBM's 2024 Cost of a Data Breach Report. This figure doesn't capture the full impact on businesses—stock prices typically drop 5-7% following disclosure of major breaches, and customer churn increases dramatically in consumer-facing industries.
Regulatory requirements for application security continue to expand. The EU's GDPR explicitly requires "security by design and default" with potential fines of up to 4% of global revenue for non-compliance. Industry-specific regulations like PCI DSS for payment processing and HIPAA for healthcare mandate specific application security controls.
Most importantly, software now powers critical infrastructure and essential services. Application vulnerabilities can impact physical systems, public safety, and national security. The Colonial Pipeline ransomware incident demonstrated how software security issues can create real-world consequences like fuel shortages across entire regions.
For organizations building custom software or deploying third-party applications, why application security is important goes beyond compliance requirements to fundamental business resilience.
Implementing Application Security
Creating an effective application security program requires a systematic approach:
- Start with assessment: Before implementing security controls, understand your current state. Inventory applications, conduct risk assessments, and identify security gaps. This baseline helps prioritize efforts where they'll have the greatest impact.
- Secure the development process: Implement security gates at critical points in your development workflow. These include security requirements during planning, threat modeling during design, code reviews during implementation, and security testing before release.
- Provide developer enablement: Developers can't fix what they don't understand. Provide secure coding training tailored to your technology stack, create language-specific guidelines, and build reusable security components that make the secure way the easy way.
- Choose appropriate tools: Select security testing tools that integrate with your development pipeline and technology stack. The right tools minimize friction while providing actionable feedback that developers can use to fix issues quickly.
- Build verification and validation: Implement processes to verify security controls work as intended. This includes positive security testing (verifying features work) and negative testing (confirming attacks are blocked).
- Monitor and respond: Deploy runtime monitoring to detect attacks against production applications. Establish incident response procedures specifically for application security events.
- Create feedback loops: Use metrics and findings to continuously improve your application security program. Track vulnerability trends, remediation times, and security debt to guide future improvements.
Organizations starting this journey should follow a structured methodology outlined in the application security checklist to ensure systematic implementation of controls across all applications.
Conclusion
Application security has evolved from a niche technical concern to a business imperative. As organizations continue their digital transformation journeys, the security of their applications directly impacts business outcomes, customer trust, and regulatory compliance.
The most effective application security programs don't treat security as a separate activity but integrate it throughout the software development lifecycle. By making security part of the development process rather than an afterthought, organizations can deliver secure applications that enable innovation while protecting critical assets.
While perfect security remains elusive, a mature application security program significantly reduces risk by eliminating common vulnerabilities, detecting sophisticated attacks, and containing damage when breaches occur. In today's threat landscape, this capability isn't just a technical consideration—it's a business necessity.
For organizations looking to enhance their application security posture without building everything from scratch, EdgeOne provides comprehensive protection for web and cloud applications through its integrated security platform. EdgeOne combines advanced web protection, DDoS protection, API security, and bot management in a single solution that deploys in minutes rather than months. Experience how EdgeOne's security features can strengthen your application defenses while simplifying management—start your free trial today and see the difference layered security makes for your business-critical applications.
FAQs
Q1: What's the difference between application security and network security?
A1: Application security focuses on vulnerabilities within software code and design, while network security protects the infrastructure applications run on; both are necessary as network protections cannot stop attacks exploiting flaws in the application itself.
Q2: When should application security testing be performed?
A2: Security testing should occur throughout the development lifecycle, not just before release—integrating automated security testing into CI/CD pipelines finds vulnerabilities earlier when they're less expensive to fix.
Q3: Which application security testing method is most effective?
A3: No single method catches all vulnerabilities—the most effective approach combines static analysis (SAST), dynamic testing (DAST), software composition analysis (SCA), and manual penetration testing for comprehensive coverage.
Q4: How can organizations prioritize application security vulnerabilities?
A4: Prioritize vulnerabilities based on exploitability, potential business impact, and exposure to untrusted users—focus first on externally accessible applications handling sensitive data with vulnerabilities that have known exploit methods.
Q5: What role do developers play in application security?
A5: Developers are the first line of defense in application security—they need security training, secure coding guidelines, appropriate tools, and a supportive culture that values security alongside functionality and performance.

