In the realm of cybersecurity, understanding the tactics and techniques employed by attackers is crucial for developing effective defense strategies. One of the most insidious methods used by cybercriminals is lateral movement. This term refers to the techniques that attackers use to move through a network after gaining initial access, allowing them to expand their reach and escalate privileges. In this blog, we will delve into the principles of lateral movement, explore specific techniques used in both Windows and Linux environments, and discuss preventive measures that organizations can implement to safeguard their networks.
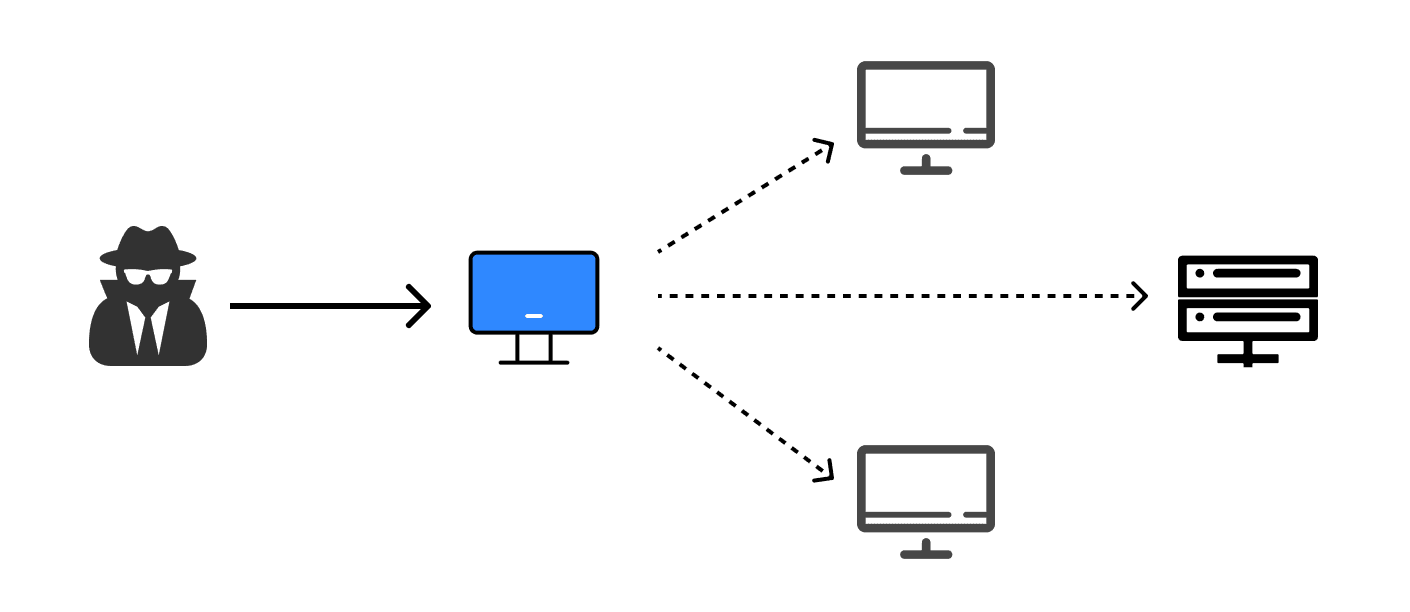
The Principle of Lateral Movement
Lateral movement typically begins quietly after an attacker successfully breaches the perimeter defenses of a network system and gains initial access to a host. The core operating principle revolves around exploring and exploiting the trust relationships, security vulnerabilities, and misconfigurations among the hosts within the target network. This gradual expansion of privileges and continuous spread of the attack scope can lead to significant data breaches and system compromises.
To fully grasp the concept of lateral movement, it is essential to understand the broader attack lifecycle. This lifecycle generally consists of several stages:
- Reconnaissance: Attackers gather information about the target network, identifying potential vulnerabilities and entry points.
- Initial Access: This stage involves breaching the network perimeter, often through phishing, exploiting vulnerabilities, or using stolen credentials.
- Execution: Once inside, attackers execute malicious code to establish a foothold within the network.
- Persistence: Attackers create backdoors or other means to maintain access to the compromised system.
- Lateral Movement: This is where the attacker begins to explore the network, moving from one system to another to expand their control.
- Data Exfiltration: Finally, attackers may steal sensitive data or deploy ransomware to extort the organization.
By understanding this lifecycle, organizations can better prepare for and defend against lateral movement attacks.
Lateral Movement in Windows Environments
In a Windows environment, the principle of lateral movement is primarily based on the network architecture, trust relationships, and security mechanisms of the Windows operating system. Here are some specific examples of lateral movement techniques used in Windows environments:
Attacks Based on Windows Domain Environment
1. Kerberos Ticket Passing Attack: In Windows domain environments, Kerberos is the primary authentication protocol. When a user logs into the domain, they receive a Ticket Granting Ticket (TGT) from the Domain Controller (DC). If an attacker obtains a user's TGT on a compromised host, they can use tools like Mimikatz to perform a ticket passing attack. This allows the attacker to request service tickets from other servers within the domain, accessing resources as if they were legitimate users.
2. Exploiting Domain Trust Relationships: Trust relationships between Windows domains facilitate user access to resources across multiple domains. An attacker controlling a host within one domain can exploit this trust to access resources in other trusted domains. For example, if an attacker compromises a host in a main domain, they can use the credentials obtained to access hosts in a subdomain, achieving lateral movement.
3. Exploiting Windows Network Share Vulnerabilities:
- SMB Protocol Vulnerability Exploitation: The Server Message Block (SMB) protocol is used for file sharing and other network services. Vulnerabilities in SMB can be exploited for lateral movement. For instance, the EternalBlue vulnerability (CVE-2017-0144) allows attackers to execute arbitrary code on a target host, enabling them to scan and attack other Windows hosts with open SMB services.
- Misuse of Shared Folder Permissions: Improperly configured shared folder permissions can be exploited by attackers. If a shared folder is set with "Everyone" having full control, an attacker can access sensitive files or place malicious software in the folder, infecting other users who access it.
Exploiting Vulnerabilities in Windows Remote Management Tools
1. Remote Desktop Protocol (RDP) Vulnerability Exploitation: RDP is used for remotely connecting to Windows desktops. Vulnerabilities in RDP can be exploited to infiltrate target hosts. Attackers may use brute-force attacks to crack RDP login passwords or exploit code execution flaws to gain remote sessions.
2. Windows Management Instrumentation (WMI) Vulnerability Exploitation: WMI is a management tool used for system monitoring. Attackers can exploit vulnerabilities in WMI to perform remote operations, such as querying or controlling services on other Windows hosts within the same network.
Lateral Movement in Linux Environments
In the Linux environment, lateral movement involves attackers using various techniques to expand their attack scope after gaining certain privileges on a Linux host. Below are some common examples:
Lateral Movement Based on SSH
1. SSH Brute Force: Attackers may use tools like Hydra to perform brute-force attacks on SSH logins, trying numerous combinations of usernames and passwords. Once they gain access, they can move laterally within the network.
2. SSH Private Key Theft: If attackers obtain SSH private key files from a user on a compromised Linux host, they can use the corresponding public key to log into other servers that allow authentication with that key.
Lateral Movement Using Exploits
1. System Vulnerability Exploitation: Attackers can exploit unpatched vulnerabilities in Linux systems to expand laterally. For example, the Dirty COW vulnerability (CVE-2016-5195) allows attackers to escalate privileges and move higher in the network.
2. Web Application Vulnerability Exploitation: If a web application running on a Linux server has vulnerabilities, attackers can exploit these to gain control of the server and search for sensitive information to access other servers in the network.
Lateral Movement Leveraging Internal Network Services
1. Samba Service Vulnerability Exploitation: If a Linux system has a misconfigured or vulnerable Samba service, attackers can exploit these issues to gain system privileges or access shared resources.
2. NFS Service Vulnerability Exploitation: Attackers may exploit vulnerabilities in NFS configurations to mount remote NFS shared directories and access sensitive information, facilitating lateral movement.
Lateral Movement Through Malware or Scripts
1. Implanting Trojans or Backdoors: After infiltrating a Linux host, attackers may implant trojans or backdoors that establish connections with external servers, allowing them to search for other vulnerable hosts within the network.
2. Using Scripts for Automated Scanning and Attacking: Attackers may write scripts to scan other hosts in the same network segment, looking for vulnerabilities or weak passwords to exploit.
Means of Lateral Movement
Lateral movement can occur through various means, including:
- Exploitation of Vulnerabilities: Attackers actively seek security vulnerabilities in operating systems, applications, and network devices. By crafting specialized malware or scripts, they can exploit these vulnerabilities to gain access to target hosts.
- Credential Theft: Acquiring legitimate user credentials is critical for lateral movement. Attackers may use keyloggers, network sniffers, or memory reading tools to obtain passwords, allowing them to move around the network as legitimate users.
- Abuse of Network Shares and Connections: Negligently configured network shared folders can become channels for lateral movement. Attackers can upload malicious programs to shared folders, infecting other users who access them.
- Malware Propagation: Trojans, worms, and other types of malware can facilitate lateral movement. Once a host is infected, the malware may actively search for other targets within the network, replicating itself and spreading the infection.
Preventive Measures for Lateral Movement
To mitigate the risks associated with lateral movement, organizations should implement a series of preventive measures:
- Vulnerability Management: Establishing a comprehensive vulnerability scanning mechanism is essential. Organizations should deploy professional vulnerability scanning tools to perform regular scans of all hosts, servers, and network devices. Once vulnerabilities are discovered, immediate remediation processes should be initiated, including rigorous testing of patches to ensure compatibility with existing systems.
- Access Control: Adhering to the principle of least privilege is crucial for permission management. Users should be granted only the minimum necessary permissions based on their job roles. Implementing multi-factor authentication for privileged accounts can enhance security, and detailed logging of account operations can help detect abnormal behaviors.
- Credential Protection: Establishing a strong password policy is fundamental for protecting credentials. Passwords should be complex and changed regularly. Multi-factor authentication should be promoted as a standard for network logins, and high-strength encryption algorithms should be used for storing credentials.
- Network Segmentation and Access Restrictions: Dividing the network into different security zones can help contain lateral movement. Deploying firewalls and setting up Access Control Lists (ACLs) can restrict access between these zones. Additionally, implementing Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) can monitor and analyze network traffic in real-time.
- Comprehensive Security Services: Organizations should consider utilizing security services that provide protection against DDoS attacks and other threats. Services like EdgeOne can offer tailored DDoS protection strategies based on specific business needs.
Conclusion
In cybersecurity, lateral movement represents a complex and covert form of attack that poses a severe threat to both corporate and personal network assets. By exploiting network trust relationships and vulnerabilities, attackers can expand their reach and escalate privileges, leading to significant data breaches. Understanding the principles and techniques of lateral movement is essential for developing effective defense strategies. Organizations must remain vigilant, continuously monitor cybersecurity trends, and adapt their protective measures to safeguard their networks in an ever-evolving threat landscape. By implementing comprehensive, multi-layered security strategies, organizations can better protect themselves against the risks associated with lateral movement and ensure the secure operation of their network information systems.
EdgeOne is a cutting-edge platform designed to enhance network security and optimize performance for businesses of all sizes. Its primary function is to provide a comprehensive suite of security features that protect against a wide range of cyber threats, including malware, phishing, and DDoS attacks.
Additionally, EdgeOne offers seamless integration with existing security infrastructure, enabling organizations to bolster their defenses without overhauling their current systems. Its user-friendly interface and advanced analytics provide security teams with actionable insights, allowing for informed decision-making and rapid incident response.
Join us today and discover how EdgeOne can help safeguard your organization against evolving cyber threats while optimizing your network performance. Don’t miss this opportunity to elevate your security posture — sign up now!

