Email is crucial for modern communication, playing a vital role in personal, professional, and academic correspondence. Its significance lies in its versatility, speed, and efficiency, enabling users to instantly send and receive messages globally. Email simplifies the exchange of information, facilitates document sharing, and coordinates tasks and projects, making it indispensable for businesses and individuals. However, with the rise in its usage, email has also become a popular target for cybercriminals. Therefore, ensuring email security is crucial to protect sensitive information from potential threats.
What is Email Security?
Email security refers to the measures and techniques implemented to protect email accounts and communication from unauthorized access, loss, or compromise. This includes safeguarding sensitive information transmitted via email from various threats such as phishing attacks, malware, spam, and identity theft. Effective email security strategies involve the use of encryption, secure email gateways, anti-spam filters, and phishing detection mechanisms to ensure the confidentiality, integrity, and availability of email communications. By prioritizing email security, organizations and individuals can significantly reduce the risk of data breaches and ensure the privacy of their communications.
How does Email Work?
When you send an email to your friends or contacts, it is almost immediately delivered to the recipients within the blink of an eye. However there is a set of processes that happens in the background from when you send the email, and till the email is delivered to the recipient's Inbox. Email is an electronic communication method for transmitting and exchanging messages over computer networks.
Here is a brief overview of how email works:
- Sending an Email.
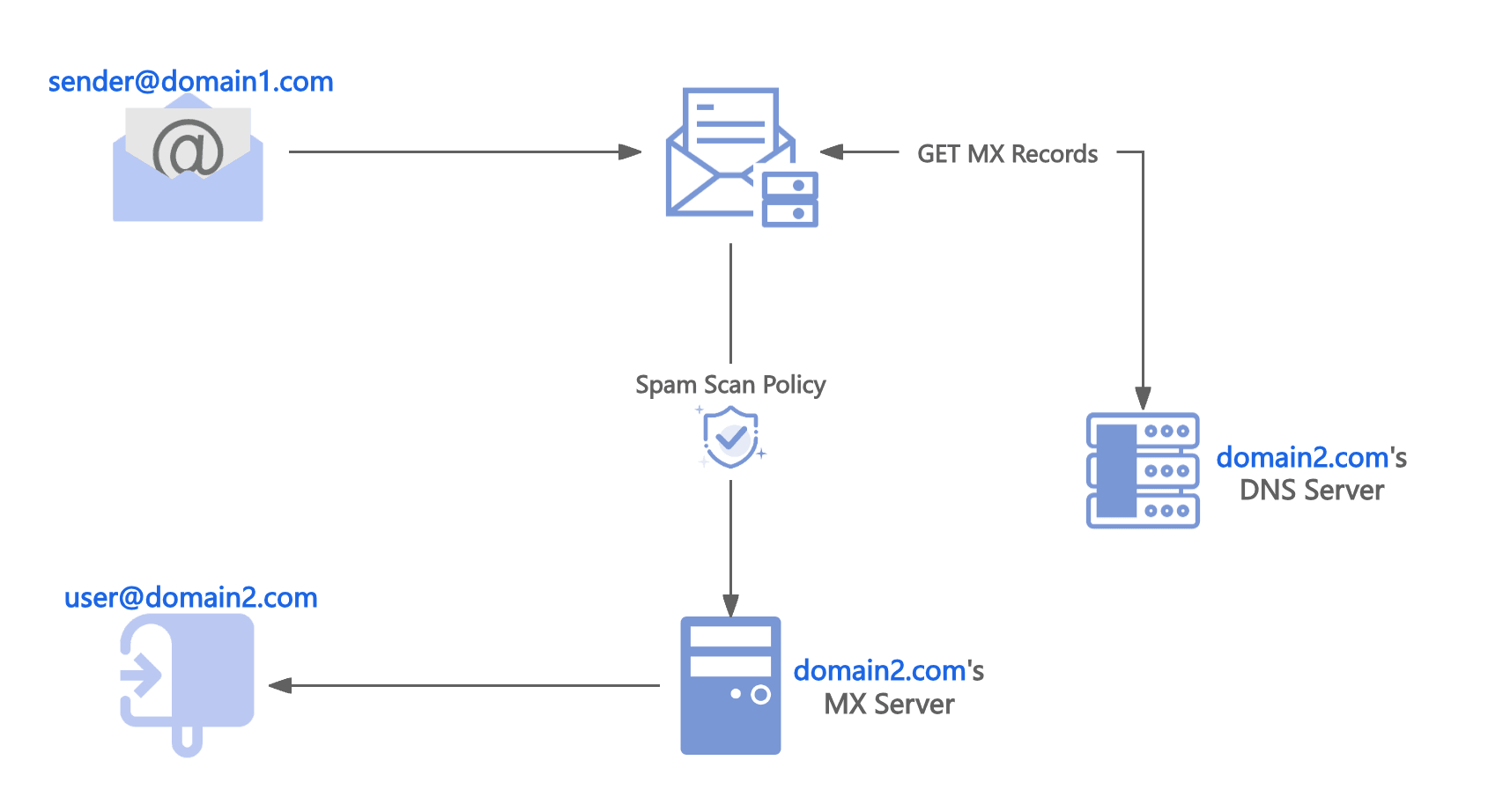
- Email Server Processing: Upon receiving the email, the sender's mail server performs several processes. First, the server verifies the sender's identity and permissions to ensure they have the authority to send the email. Then, the server checks the format and size of the email and applies spam filtering to prevent the transmission of junk mail. If everything is in order, the mail server stores the email in the sender's mailbox, awaiting further delivery.
- Finding the Recipient's Email Server: The sender's mail server needs to locate the recipient's mail server to deliver the email to the correct destination. To accomplish this, the sender's mail server queries the recipient's domain name system (DNS) records to find the mail server associated with the recipient's email address.
- Delivering the Email: The email client (web/ mobile/ desktop) connects to the Outgoing SMTP server based on the email account you used. The email client handovers the email in MIME format to the Outgoing SMTP server. The Outgoing SMTP validates the sender's details and processes the message for sending. It also verifies the attachment size and verifies whether the email complies with the outgoing email policy set for the particular account. Once the entire validation is completed, it places it in the Outgoing queue. The SMTP server looks up the DNS records of the domain and retrieves the MX records information of the recipient servers (A Records in case no MX record is found). Then the SMTP Server connects with the Recipient email server MTA and sends the email through the SMTP protocol.
- Receiving the Email.
What are the Types of Email Attacks?
Here are some common types of email attacks:
- Phishing Emails: Phishing emails are deceptive emails that impersonate legitimate entities such as banks, social media platforms, or e-commerce websites. Attackers attempt to trick victims into clicking malicious links, providing personal information, or downloading malicious attachments to obtain sensitive information.
- Ransomware Emails: Ransomware emails contain malware, such as ransomware, which encrypts the victim's files and demands a ransom payment to decrypt them. Victims are typically infected when they open an attachment or click on a link in the email.
- Malicious Attachments: Malicious attachments are email attachments that contain malware such as viruses, trojans, or spyware. Once the victim opens the attachment, the malware executes on their computer, potentially leading to data breaches, system crashes, or remote control by the attacker.
- Spam Emails: Spam emails are unsolicited or irrelevant bulk emails. They may contain advertisements, fraudulent information, scam links, or malware. Spam emails not only waste the recipient's time and resources but may also contain deceptive content.
- Social Engineering Attacks: Social engineering attacks manipulate and deceive individuals to gain information or access. Attackers may send emails impersonating legitimate entities to trick victims into providing sensitive information, passwords, or performing malicious actions.
- Botnet Attacks: Attackers can spread botnets through email, forming networks of infected computers used for sending spam emails, launching distributed denial-of-service (DDoS) attacks, or engaging in other malicious activities.
- Spyware Emails: Spyware emails distribute malware through email to monitor victims' activities, steal sensitive information, or gain remote control over infected computers.
What is Business Email Compromise (BEC)?
Business email leakage refers to the unauthorized disclosure or exposure of the content, attachments, or contact information of business organizations or companies' emails. This leakage can occur due to internal negligence, malicious actions, cyber attacks, or other security vulnerabilities.
Business email leakage can have serious implications for an organization, including but not limited to:
- Confidential information disclosure: Business emails may contain sensitive information such as business plans, customer data, financial information, contract details, etc. The leakage of such information can lead to business competition risks, legal liabilities, and reputational damage.
- Intellectual property leakage: Business emails may contain information related to intellectual property, such as patents, trademarks, trade secrets, etc. The leakage of such information can result in intellectual property infringement or theft.
- Financial fraud: Leaked business emails can be exploited by hackers or fraudsters for financial fraud activities, such as phishing attacks using forged emails, fake invoice scams, etc.
- Brand reputation damage: Business email leakage can harm an organization's brand reputation. The leaked information can be misused or made public, undermining the organization's credibility and customer trust.
Best Practices for Email Security
Below are some best practices to help users protect email security:
- Use Strong Passwords and Two-Factor Authentication (2FA): A strong, unique password is the first line of defense. Additionally, enabling 2FA adds an extra layer of security by requiring a second form of identification.
- Be Wary of Suspicious Emails: Always be cautious of emails from unknown senders, unexpected attachments, or links. These could be phishing attempts or contain malware.
- Encrypt Sensitive Emails: Encryption converts your email content into a format that can only be read with a decryption key. This prevents unauthorized access to your emails during transmission.
- Regularly Update and Patch Your Systems: Keeping your email software and devices updated ensures you have the latest security patches, reducing vulnerabilities.
- Use a Secure Email Gateway: A secure email gateway prevents the transmission of emails that break company policy or will deliver malware.
How can DNS Records Help Prevent Email Attacks?
The Domain Name System (DNS) stores public records about a domain, including that domain's IP address. The DNS is essential for enabling users to connect to websites and send emails without memorizing long alphanumeric IP addresses.
DNS records can help prevent email attacks in several ways:
- SPF (Sender Policy Framework) Records: SPF records are a type of DNS record that defines which servers are allowed to send emails on behalf of your domain. This can prevent spammers from forging your domain to send emails. The receiving server can check if the sender's IP address is listed in the SPF record, and if not, the email may be marked as spam or rejected.
- DKIM (DomainKeys Identified Mail) Records: DKIM is an email authentication method that allows the recipient to check if the email has been tampered with. The sending server signs the email with a private key, and the recipient can verify the signature with the public key in DNS. If the signature verification fails, the email may be treated as spam or rejected.
- DMARC (Domain-based Message Authentication, Reporting & Conformance) Records: DMARC is a DNS-based email authentication system that uses SPF and DKIM for verification and defines how to handle emails when verification fails. This can prevent phishing and fraudulent emails.
Conclusion
Ensuring email security is crucial in today's digital age, where email has become a primary mode of communication for personal, professional, and commercial activities. The importance of securing emails is due to their vulnerability as a vector for cyber threats such as phishing scams, malware distribution, and data breaches. These attacks not only compromise sensitive information but can also lead to significant financial losses and damage to an organization’s reputation. Implementing strong email security measures ensures the integrity and confidentiality of communications, safeguards personal and corporate data, and maintains trust between parties.
Tencent EdgeOne offers robust security features designed to protect your digital assets and ensure the integrity of your online operations. With advanced threat detection and mitigation capabilities, EdgeOne provides comprehensive protection against DDoS attacks, web application attacks, and other cyber threats. We have now launched a Free Trial, welcome to Contact Us for more information.

