Understanding Virtual IP: What It Is and How It Works
In the age of rapid digital development today, the continuous progress of network technologies has bestowed great convenience on our lives and work. Virtual IP, an important network technology, is playing an ever more crucial role.
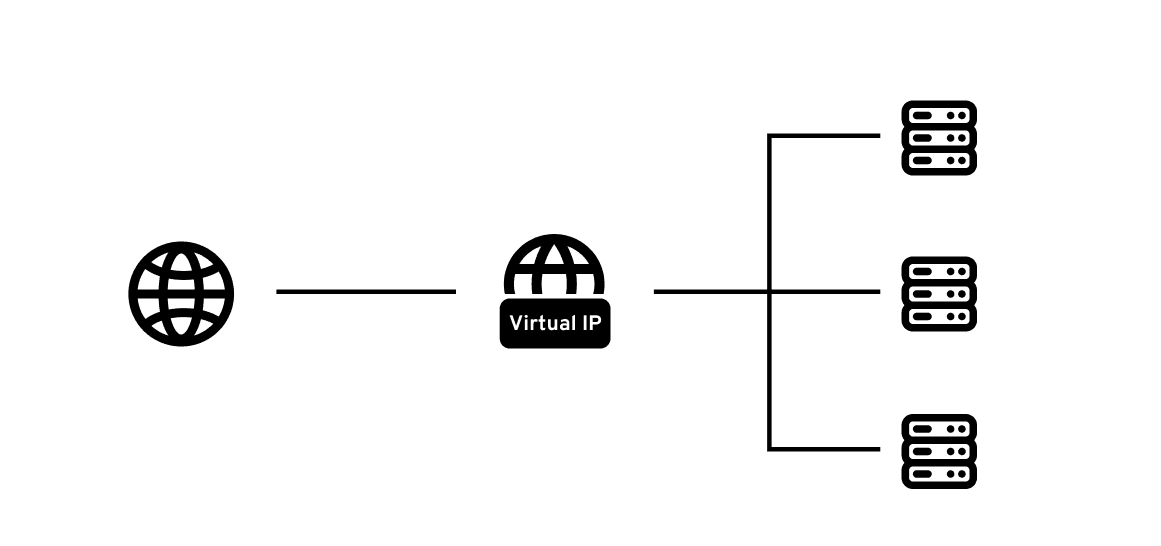
What is Virtual IP?
Virtual IP, also known as the virtual IP address, is an IP address that is not assigned to the network card of a real elastic cloud server. Nevertheless, it can perform network communications just as a real IP address does and has the same network access capabilities as a private IP. In simple terms, it is akin to a "virtual house number", enabling devices in the network to locate specific services or resources without relying on the actual physical IP address.
How Virtual IP Works?
The working mechanism of Virtual IP involves creating an abstraction layer between the physical network infrastructure and the services running on it. When a Virtual IP is configured, it acts as a single point of contact for clients to access services, while the actual network traffic is directed to one or more physical servers behind the scenes.
In a typical setup, the Virtual IP address floats between multiple physical servers, with only one server actively handling the VIP at any given time. If the active server fails, the VIP automatically moves to another available server, ensuring continuous service availability. This process is often managed by clustering software or load balancers that monitor the health of all servers and handle the transition of the Virtual IP when necessary.
For load balancing purposes, a Virtual IP can distribute incoming requests across multiple physical servers based on various algorithms such as round-robin, least connections, or weighted distribution. This helps optimize resource utilization and improve overall system performance.
The implementation of Virtual IP relies on protocols like ARP (Address Resolution Protocol) for IPv4 or NDP (Neighbor Discovery Protocol) for IPv6. When a Virtual IP moves between servers, the new active server broadcasts an ARP announcement to update the network's ARP tables, ensuring that network traffic is correctly routed to the current active server.
Virtual IPs are particularly valuable in modern cloud computing and containerized environments, where services need to be highly available and scalable. They provide a stable endpoint for clients while allowing underlying infrastructure to change dynamically without affecting the service availability.
What are the Types of Virtual IP?
1. Static Virtual IP
Once set, its IP address remains fixed and will retain that specific IP value for an extended period. Typically, network administrators manually configure it in accordance with network planning and requirements.
It is ideal for services or devices with high demands for IP address stability. For instance, for important servers within an enterprise, like mail servers and database servers, employing a static virtual IP ensures that other devices can establish continuous and accurate connections with them, facilitating internal network management and stable access by external customers.
2. Dynamic Virtual IP
The IP address is not fixed and will be dynamically allocated and adjusted according to certain rules or conditions. Dynamic allocation can be automatically accomplished by network devices such as routers and DHCP servers.
It is more frequently used in some temporary network application scenarios. For example, during large network conferences or events, dynamic virtual IPs are temporarily allocated to the devices of participants to meet their network access requirements during the event. After the event concludes, these IPs can be retrieved and reallocated. Additionally, in some small network environments that are cost-sensitive and have low requirements for IP address stability, dynamic virtual IPs will also be utilized to enable network access for devices.
3. Shared Virtual IP
Multiple physical devices or users jointly utilize the same virtual IP address. Generally, network devices such as routers and load balancers are employed to allocate and manage traffic to ensure that different devices or users can communicate normally without interfering with each other when using the shared virtual IP.
It is more common when network service providers (ISP) offer network access services for multiple users. For example, in the scenario of broadband access in a residential area, multiple residents may access the Internet through the same shared virtual IP. Network devices in the background rationally allocate and manage the network traffic of different residents to achieve efficient network services. Similarly, when some small enterprises or office places adopt the shared network access method, they may also use shared virtual IPs.
4. Floating Virtual IP
It is capable of "floating" among multiple physical devices and being dynamically bound to one of these devices in accordance with the operating status of the devices (such as availability, load conditions, and so on). Generally, its functions are achieved in combination with high availability and load balancing mechanisms.
It is extensively utilized in server cluster environments. For instance, in a Web application server cluster consisting of multiple servers, the floating virtual IP will be dynamically bound to the server with a lighter load and normal operation based on the load conditions and normal operation status of each server. When a certain server malfunctions or has an excessive load, the floating virtual IP can promptly "float" to other appropriate servers to ensure the continuity and high efficiency of the service.
Advantages of Virtual IP
- High Availability: When a physical device, say a server, malfunctions, the virtual IP can swiftly switch to other properly functioning devices. For instance, in a server cluster, if one server goes offline, with the aid of the virtual IP mechanism, client access requests to the server cluster can be instantly redirected to the remaining available servers, ensuring uninterrupted service.
- Load Balancing: The virtual IP can collaborate with load balancing technology to evenly distribute the network requests of a large number of clients among multiple physical devices such as servers. For example, in a large-scale Web application scenario, by setting a virtual IP through a load balancer, user access requests can be rationally distributed to different servers according to algorithms like round-robin and weighted round-robin. This prevents a single server from experiencing performance degradation or even crashing due to excessive load, effectively enhancing the performance and response speed of the overall system.
- Flexibility: When changes occur in the network environment, such as adding, removing, or migrating physical devices, adjusting the configuration of the virtual IP is relatively straightforward. There is no need for extensive changes to the client's network settings. Only the mapping relationship between the virtual IP and the physical devices needs to be replanned at the network level. For instance, when an enterprise upgrades its servers, by utilizing the virtual IP, services can be easily migrated to new devices without affecting normal access to related businesses.
- Simplifying Network Management: For complex network architectures, the virtual IP can abstract multiple physical devices into a logical entity for management. Network administrators can indirectly control the operating status of multiple associated physical devices by managing the virtual IP. For example, in a data center, by clustering numerous servers and assigning a virtual IP to them, the administrator can uniformly manage the entire cluster through this virtual IP, including monitoring traffic and performance. This significantly simplifies the management process and workload.
- Saving IP Resources: In some situations, multiple physical devices can share a virtual IP to achieve efficient reuse of IP resources. For example, in small enterprises or home networks, multiple devices can share a virtual IP through a router to access the Internet, avoiding the need to assign a public IP to each device separately and thus saving precious IP resources. Especially in the context of the growing scarcity of public IP addresses, this advantage is even more prominent.
Application Scenarios
1. Cloud Computing Field
- Allocation and Management of Virtual Machine Resources: In the cloud computing environment, a large number of virtual machines require network communication to provide services. Virtual IPs are employed to assign independent logical IP addresses to each virtual machine, facilitating operations such as resource allocation, load balancing, and virtual machine migration within the cloud platform. For example, when a virtual machine needs to be migrated from one physical host to another, its virtual IP can stay unchanged, ensuring that the connections of other connected virtual machines or external clients are not disrupted.
- High Availability of Cloud Services: Cloud service providers leverage virtual IPs to achieve high availability of services. For instance, in a cloud storage service, multiple storage servers form a cluster and share a virtual IP. When one of the servers malfunctions, through the failover mechanism of the virtual IP, client requests can be automatically redirected to other normal servers, ensuring that users can continuously access the cloud storage service and thereby enhancing the user experience and service reliability.
2. Data Center
- Server Cluster: Data centers typically construct server clusters to boost computing power and reliability. Virtual IPs are employed for the unified management and load balancing of these clusters. For example, in a Web server cluster, multiple servers collaborate to receive client requests via virtual IPs and then distribute the requests to each server according to load balancing algorithms. This not only enhances the performance of the system but also guarantees the continuity of services when individual servers malfunction.
- Data Backup and Disaster Recovery: Virtual IPs also play a crucial role in data backup and disaster recovery planning in data centers. For instance, a virtual IP is established between the primary data center and the backup data center. When a disaster (such as a fire, earthquake, and so on) occurs in the primary data center and leads to service interruption, the network switching device redirects the virtual IP to the backup data center, enabling clients to rapidly regain access to data and services and realizing the disaster recovery function of the data center.
3. Enterprise Network
- High Availability of Internal Systems: The crucial business systems within an enterprise, like mail servers and ERP systems, typically require ensuring high availability. By configuring virtual IPs for these systems and integrating with the failover mechanism, when the physical server hosting the system malfunctions, the virtual IP can be switched to the standby server, guaranteeing that enterprise employees can continuously and smoothly utilize these important internal systems.
- Remote Access: As the demand for remote work among enterprise employees increases, virtual IPs are employed to achieve safe and convenient remote access. For instance, an enterprise can utilize the combination of a virtual private network (VPN) and virtual IP to allow employees to connect to the enterprise's internal network via the Internet when they are away from the office, access internal resources. At the same time, virtual IPs can be used to manage the access rights of different employees to ensure the security of the enterprise network.
4. Internet Service Providers
- Broadband Access Services: When offering broadband access services to a large number of users, ISPs frequently employ the approach of utilizing shared virtual IPs. The devices of multiple users share a single virtual IP to access the Internet via network devices like routers. This not only satisfies the Internet access requirements of users but also saves IP resources to a certain degree and enhances the utilization ratio of resources.
- Network Address Translation (NAT): Virtual IPs are also applied in NAT technology. ISPs convert the private IP addresses of multiple users into one or more shared virtual IP addresses to enable the connection between users' devices and the Internet. At the same time, it hides the real IP addresses of users, playing a certain role in protecting privacy and security.
5. Internet Application Services
- Large Websites and Applications: In the case of large websites (such as e-commerce platforms and social platforms), as well as applications, virtual IPs are integrated with load balancers to enhance the performance and reliability of services. By allocating client requests to multiple servers and utilizing virtual IPs to ensure service continuity, it can be guaranteed that the user's access experience will not be greatly impacted even when servers fail or during periods of high network traffic.
- Content Delivery Network (CDN): CDN providers utilize virtual IPs to manage and distribute content more efficiently. For instance, different nodes within a CDN may share a virtual IP. When a user requests content, the virtual IP assists in directing the request to the nearest and most suitable node for quicker content delivery.
Security Considerations for Virtual IP
While virtual IPs bring numerous conveniences, there are also several key security aspects that require attention:
1. Potential Security Risks
- IP Address Spoofing: Attackers might forge virtual IP addresses to masquerade as legitimate network nodes and send malicious data packets. For instance, in network communications, malicious actors could use the same virtual IP as a target server cluster to send misleading information to other servers or clients, potentially leading to problems such as data leakage and service disruption.
- Traffic Hijacking: Since virtual IPs often involve scenarios like sharing among multiple physical devices or dynamic allocation, there is a risk of criminals hijacking the traffic bound for the virtual IP during network transmission. They may tamper with the data content, insert malicious advertisements, or direct users to malicious websites, thereby harming the interests of users and network security.
- Configuration Vulnerabilities: If the configuration of virtual IPs is improper, such as having unreasonable permission settings and incomplete access control policies, it may be exploited by hackers. For example, if the virtual IP configuration of a server cluster allows unauthorized external access, hackers may seize the opportunity to break in and obtain sensitive data on the server.
2. Security Protection Measures
- Firewall Setup: Deploy firewalls and configure the rules rationally to strictly filter the traffic directed at virtual IPs. Filtering rules based on conditions such as source IP addresses, destination IP addresses, and port numbers can be established to block suspicious external traffic from entering and prevent attacks like IP address spoofing. For instance, only permit IP addresses within a specific range to communicate with the virtual IP and reject data packets from unknown or suspect sources.
- Access Control: Establish a refined access control mechanism to clearly specify which devices, users, or network areas are allowed to access the virtual IP and the corresponding permission levels. Through means such as authentication and authorization, ensure that only legitimate entities can interact with the virtual IP. For example, in an enterprise network, when employees access the virtual IP of the internal system, they need to go through username and password verification as well as permission review to prevent unauthorized access.
- Encryption Technology: Utilize encryption technologies in network communications involving virtual IPs, such as SSL/TLS encryption protocols. In this way, even if the data is hijacked during transmission, it is difficult for criminals to obtain valid information within. For example, in the scenario of remote working via virtual IP, encrypt the communication between employees and the enterprise's internal network to ensure the confidentiality and integrity of the data.
- Monitoring and Auditing: Continuously monitor the usage of virtual IPs, including aspects such as traffic volume, access sources, and data flow directions. At the same time, conduct regular audits to check for any abnormal access behaviors or configuration changes. If any abnormalities are detected, take prompt measures to handle them, such as blocking suspicious connections and adjusting configurations, to maintain the security of the virtual IP.
Conclusion
As technologies like cloud computing, big data, and the Internet of Things continue to evolve, the application prospects of Virtual IP will become even more expansive. In the future, Virtual IP is likely to be integrated with more emerging technologies such as Software Defined Networking (SDN) and Network Function Virtualization (NFV), offering more opportunities for the optimization and innovation of network architectures. Meanwhile, with the widespread adoption of 5G networks, Virtual IP will also assume a more crucial role in the mobile network environment, providing users with more stable and efficient network services.
In conclusion, as an important network technology, Virtual IP plays an unrivaled role in enhancing network availability, flexibility, and performance. Whether in enterprise networks, cloud computing environments, or mobile networks, Virtual IP holds extensive application prospects. With the continuous advancement of technology, Virtual IP will continue to serve as an important intelligent link in the future network world.
About Us
EdgeOne provides comprehensive cloud security services by integrating multiple advanced security technologies to create a robust protective barrier for users. Its core features include DDoS attack defense, a Web Application Firewall (WAF), and an intelligent bot management system. These security components work together to form a complete protection network, effectively defending against various cyber threats, ensuring the secure operation of web applications and servers, and maintaining the integrity and availability of data. We have now launched a Free Trial, welcome to Sign Up or Contact Us for more information.

