Enhancing Web Security: An In-Depth Analysis of OCSP Stapling
When users access your site via HTTPS, the server needs to respond with your site's TLS certificate. The user's browser checks the certificate's expiration date and will reject any expired certificates. In some cases, server owners must mark a certificate as invalid due to a private key leak. In such situations, certificate authorities must implement at least one method to revoke problematic certificates and notify browsers to reject these revoked certificates.
What is CRL?
CRL (Certificate Revocation List) is a structured data file in the PKI (Public Key Infrastructure) system that contains the serial numbers and revocation dates of certificates that have been revoked by the certificate authority. Before users access your site, their browsers will download and parse the CRL file, and then verify whether your certificate has been revoked through the CRL file. With the widespread use of HTTPS, published CRL files are becoming larger, which undoubtedly increases the network overhead for each connection. The limitations of CRL in terms of scalability are becoming increasingly apparent.
What is OCSP?
OCSP (Online Certificate Status Protocol) is an online query protocol used to verify the legitimacy of certificates. When users access your website via HTTPS, their browsers will verify the validity of the website server's certificate through an OCSP responder. (Browsers can now contact the responder to request the revocation status of a single certificate issued by the CA, without having to obtain and process the entire CRL.)
While OCSP might seem like an effective solution, the new protocol has proven to have practical issues.
- Performance: Browsers need to perform additional HTTP requests for each new HTTPS connection, increasing network overhead.
- Security: Most practical OCSP implementations are not reliable enough (due to network latency, configuration, or application errors), causing user browsers to fail OCSP checks. If the OCSP server is inaccessible or times out, the browser will consider the certificate valid and proceed with the HTTPS connection.
- Privacy: Since certificates are associated with keys and domain names, and browsers request revocation status before each new HTTPS connection, this means that browsers leak a significant portion of their users' browsing history to OCSP responders.
What is OCSP Stapling?
OCSP stapling is a technique that embeds an OCSP response directly into the TLS handshake process. Typically, when a client establishes an SSL/TLS connection with a server, if the client needs to verify the server's certificate status, it sends an OCSP request to the certificate authority (CA). This approach adds extra latency and may be susceptible to man-in-the-middle attacks.
With OCSP stapling, the server proactively provides its latest OCSP response during the TLS handshake process, thereby eliminating the need for additional communication between the client and the CA. This not only improves efficiency but also enhances security.
OCSP stapling requires servers to regularly obtain the latest OCSP responses from the CA and store them locally. When a client initiates a connection request, the server directly provides these responses to the client, thereby fulfilling the client's need for certificate status verification.
What is OCSP Must-Staple?
Since OCSP stapling is implemented on the server side, browsers cannot know if the server truly supports stapling, and OCSP stapling alone does not fully address the soft-fail security issue of OCSP.
As a result, attackers holding stolen certificate private keys can carry out a downgrade attack by presenting the certificate without OCSP stapling. The victim's browser cannot verify if the server genuinely supports stapling and cannot continue to query the OCSP responder as usual. The attacker can then simply block this OCSP query, effectively forcing the browser to accept the certificate as valid.
OCSP Must-Staple is a stricter security requirement that mandates all TLS-enabled servers to implement OCSP stapling technology. This means that when a client attempts to establish a connection with a server, the server must be able to provide the latest OCSP response, otherwise, the connection will not be established.
This requirement aims to ensure that all SSL/TLS connections have an efficient certificate status verification mechanism, thereby improving the overall network security. By enforcing OCSP stapling, the risk of security vulnerabilities and risks caused by inadequate certificate status verification can be reduced.
OCSP Must-Staple helps mitigate the aforementioned downgrade attacks, as well as reduces unnecessary traffic to the CA's OCSP response servers, thereby improving the overall performance of OCSP.
Enabling OCSP Stapling on Tencent EdgeOne
Scenario 1: Enabling OCSP Stapling for All Domain Names
To enable OCSP stapling for all domain names used to access a site, refer to the following information.
- Log in to the Tencent EdgeOne Console and click Site List in the left sidebar. In the site list, click the target site.
- On the site details page, choose Site Acceleration > HTTPS to go to the HTTPS page.
- On the OCSP stapling configuration card, toggle on the Site-wide setting switch.
Scenario 2: Enabling OCSP Stapling for Specified Domain Names
To enable OCSP stapling for specified domain names, refer to the following information.
- Log in to the Tencent EdgeOne Console and click Site List in the left sidebar. In the site list, click the target site.
- On the site details page, click Rule Engine.
- On the rule engine management page, click Create rule.
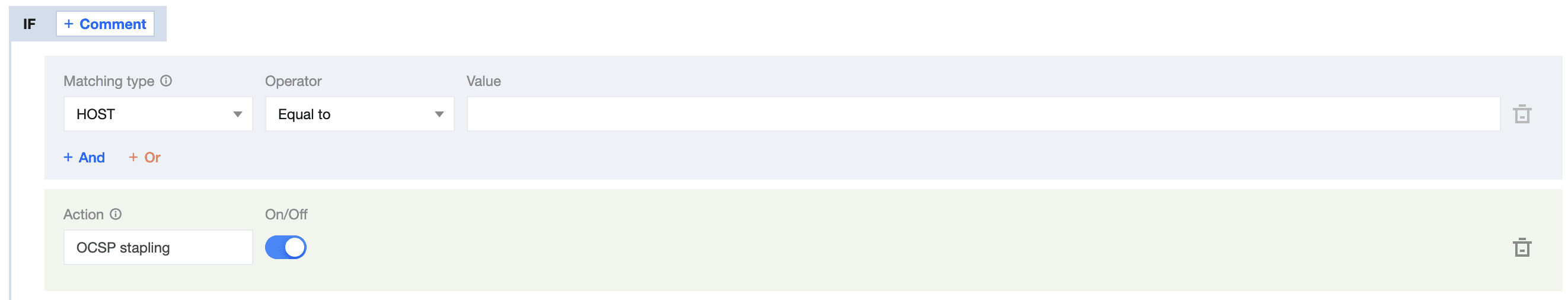
- On the page that appears, select HOST from Matching type and specify an operator and a value to match the requests of specified domain names.
- From the Operation drop-down list, select OCSP stapling.
- Click Save and publish.
The Execution Process of OCSP Stapling in Tencent EdgeOne
The following is the execution process of OCSP Stapling when enabled and disabled:
OCSP Stapling Disabled
- The client initiates a TLS handshake.
- EdgeOne responds to the TLS handshake (by returning the certificate).
- The client initiates an OCSP query.
- The CA returns the result.
OCSP Stapling Enabled
- The client initiates a TLS handshake.
- EdgeOne initiates an OCSP query.
- The CA returns the result, and EdgeOne caches the result.
- EdgeOne responds to the TLS handshake (by returning the certificate and OCSP information).
When OCSP stapling is enabled, EdgeOne performs OCSP queries and caches the results on servers. When a client initiates a TLS handshake with EdgeOne, EdgeOne responds with the OCSP information and certificate required for verification so that the client does not need to send a query request to the CA. This significantly improves the efficiency of the TLS handshake, reduces the time for verification, and improves the HTTPS request speed.
Conclusion
Tencent EdgeOne offers significant advantages in web security by integrating advanced security features directly into its edge computing platform. It provides robust protection against Distributed Denial of Service (DDoS) attacks, web application firewalls (WAF) to guard against common web vulnerabilities. Additionally, EdgeOne leverages Tencent's extensive threat intelligence and real-time monitoring capabilities to detect and respond to security threats swiftly.
We have now launched a free trial, welcome to Contact Us for more information.

