Mastering Web Security with EdgeOne: A Comprehensive Guide to HTTPS Configuration
What is HTTPS?
The HTTPS protocol (Hyper Text Transfer Protocol over Secure Socket Layer) is an extension of HTTP used for secure communication in computer networks and is widely used on the Internet, according to the definition from Wikipedia.
In HTTPS, the original HTTP protocol is encrypted by TLS (Transport Layer Security) or its predecessor SSL (Secure Socket Layer). Therefore, HTTPS is often referred to as HTTP over TLS or HTTP over SSL. From this definition, it can be seen that HTTPS is not an independent communication protocol, but an extension of HTTP, used to ensure communication security. To understand HTTPS, it is first necessary to understand the HTTP protocol and the TLS protocol.
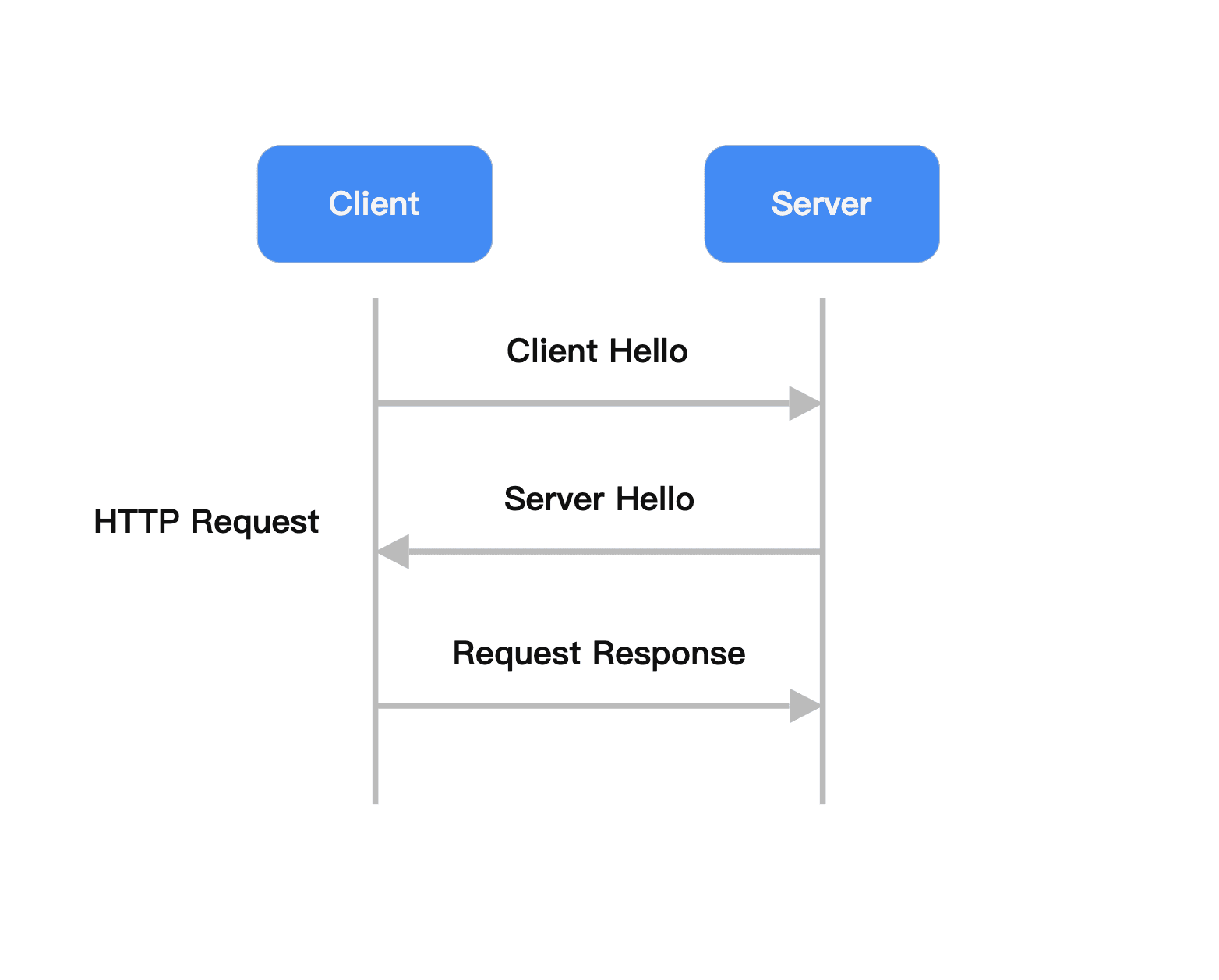
The HTTP protocol (HyperText Transfer Protocol) is an application layer communication protocol between the client browser or other programs and the Web server. The process of HTTP access is as follows:
The SSL/TLS protocol, TLS (Transport Layer Security), and its predecessor SSL (Secure Sockets Layer) are security protocols designed to provide security and data integrity for Internet communication.
Netscape launched the HTTPS protocol with SSL encryption when it released the first web browser in 1994, marking the origin of SSL. The IETF standardized SSL and published the TLS 1.0 standard document (RFC 2246) in 1999.
Subsequently, TLS 1.1 (RFC 4346, 2006), TLS 1.2 (RFC 5246, 2008), and TLS 1.3 (RFC 8446, 2018) were released. This protocol is widely used in applications such as browsers, email, instant messaging, VoIP, and network faxes. It has now become the industry standard for confidential communication on the Internet.
The handshake process of TLS is as follows:
As shown in the above description, the TLS protocol uses asymmetric encryption algorithms for identity authentication of the communicating parties, and then exchanges symmetric keys as session keys.
The session key is used to encrypt the data exchanged between the two parties, ensuring the confidentiality and reliability of communication between the two applications, and preventing eavesdropping by attackers on the communication between the client and server applications. Below are some key concepts involved in the HTTPS protocol:
Symmetric-key algorithm
Symmetric encryption Symmetric key algorithms are a class of encryption algorithms in cryptography. These algorithms use the same key for encryption and decryption, or two keys that can be easily derived from each other. In fact, this set of keys becomes a shared secret among two or more members to maintain exclusive communication.
- Advantages: The algorithm is public, requires less computation, has fast encryption speed, and has high encryption efficiency, making it suitable for encrypting larger amounts of data.
- Disadvantages: Both parties in the transaction need to use the same key, which means the key must be transmitted. The key cannot be guaranteed to not be intercepted during transmission, so the security of symmetric encryption cannot be ensured. When each pair of users uses symmetric encryption algorithms, they need to use unique keys unknown to others, which can cause a rapid increase in the number of keys held by both sender and receiver, making key management a burden for both parties. Symmetric encryption algorithms are difficult to use in distributed network systems, mainly due to key management difficulties and higher usage costs.
Asymmetric cryptography
Asymmetric encryption Asymmetric cryptography is an algorithm in cryptography that requires two keys: a public key and a private key. The public key is used for encryption, while the private key is used for decryption. The ciphertext obtained by encrypting the plaintext with the public key can only be decrypted using the corresponding private key, and the original plaintext can be obtained. The original public key used for encryption cannot be used for decryption.
Asymmetric encryption is so called because it uses two different keys for encryption and decryption, unlike symmetric encryption, which uses the same key for both. The public key can be made public and can be freely released; the private key must not be made public and must be strictly kept secret by the user. It should never be provided to anyone through any means, nor disclosed to the trusted party with whom communication is desired. The advantages and disadvantages are as follows:
- Advantages: The algorithm is public, encryption and decryption use different keys, the private key does not need to be transmitted through the network, and the security is very high.
- Disadvantages: The computation is relatively large, and the encryption and decryption speeds are much slower compared to symmetric encryption. Although encryption transmission can effectively prevent the content from being tampered with by a third party, it does not solve the issue of identity authentication.
Certificate Authority
Certificate Authority A Certificate Authority (CA) is an authoritative organization responsible for issuing and managing digital certificates and serves as a trusted third party in electronic commerce transactions, bearing the responsibility of verifying the legitimacy of public keys in the public key infrastructure.
The CA center issues a digital certificate for each user who uses a public key. The purpose of the digital certificate is to prove that the user listed in the certificate legally owns the public key listed in the certificate. The digital signature of the CA organization prevents attackers from forging and tampering with certificates. It is responsible for generating, distributing, and managing the digital certificates required by all entities participating in online transactions, making it the core link in secure electronic transactions.
What's the Difference between HTTPS and HTTP?
The biggest difference between HTTPS and HTTP is the addition of an SSL (Secure Sockets Layer) or TLS (Transport Layer Security) layer. With this security layer, the communication security between the two communicating parties on the Internet is ensured. Please refer to this article for more details
Preparation before Configuring HTTPS on EdgeOne
Before configuring HTTPS, you need to apply for a certificate for the corresponding domain from a Certificate Authority (CA). Users can purchase certificates or apply for free single-domain certificates through the Tencent Cloud SSL Certificate Console.
When applying for a certificate, the Certificate Authority (CA) needs to verify whether the applicant is the owner of the domain. Common verification methods include DNS verification and file verification.
After applying for the certificate, you need to follow the instructions to configure the corresponding DNS resolution or place the files required by the CA on the user's source server for CA verification. Once the verification is passed, you can obtain the corresponding certificate and private key.
How to Configure HTTPS in the EdgeOne Console?
You can configure HTTPS on the Tencent EdgeOne console's certificate management page. It supports deploying certificates for individual domains or in batches. Users can upload the certificates they want to configure, or first host the certificates on Tencent Cloud and then deploy them to the EdgeOne console.
How to Configure Forced HTTPS?
After configuring the HTTPS certificate for the domain, you can globally configure forced HTTPS for all domains under your site in the Site Acceleration section of Tencent EdgeOne. However, it is recommended to use the powerful and rich Rule Engines to configure different rules for different domains under the current site. Through the rule engine, you can configure forced HTTPS and specify its redirection method. There are many more features of the rule engine waiting for you to explore.
You can also learn more about the usage and features of the Tencent EdgeOne Rule Engine by reading this article. If you are interested in experiencing these benefits firsthand, feel free to contact us to learn more about Tencent EdgeOne and its features. You can also click here to get started free and experience its benefits firsthand.

