HTTP vs HTTPS: The Crucial Role of SSL Certificates in Web Security

Introduction to HTTP and HTTPS
What is HTTP?
HTTP (Hypertext Transfer Protocol) is a protocol used to transfer hypertext from web servers to local browsers. It is a communication protocol based on TCP/IP used to transfer data such as HTML files, image files, query results, etc.
How HTTP Works
HTTP works on a client-server architecture. The browser acts as an HTTP client and sends all requests to the HTTP server or web server. Web servers include Apache servers, IIS servers (Internet Information Services), etc.
After receiving the request, the web server sends the response information to the client.
The default port number for HTTP is 80, but it can also be changed to 8080 or other ports.
Three Notes on HTTP:
- HTTP is a stateless protocol: This means that each connection only handles one request. After the server processes the client's request and receives the client's response, it disconnects. This approach can save transmission time.
- HTTP is media-independent: This means that any type of data can be sent via HTTP as long as the client and server know how to handle the data content. The client and server specify the appropriate MIME-type content type.
- HTTP is stateless: This means that the protocol has no memory for transaction processing. The lack of state means that if subsequent processing requires previous information, it must be retransmitted, which may increase the amount of data transmitted in each connection. On the other hand, the response from the server is faster when it does not require previous information.
What is HTTPS?
HTTPS is a secure HTTP channel, which is the secure version of HTTP. HTTPS adds an SSL layer to HTTP. The security foundation of HTTPS is SSL, so the detailed content of encryption requires SSL.
The main functions of the HTTPS protocol can be divided into two types: one is to establish an information security channel to ensure the security of data transmission, and the other is to confirm the authenticity of the website.
How HTTPS Works
HTTPS can encrypt information to prevent sensitive information from being obtained by third parties, so many services with high-security levels, such as bank websites or email, use the HTTPS protocol.
When the client communicates with the web server using HTTPS, the following steps occur:
- The client uses an HTTPS URL to access the web server and requests to establish an SSL connection with the web server.
- After receiving the client's request, the web server sends a copy of its certificate information (which contains the public key) to the client.
- The client's browser and the web server begin to negotiate the security level of the SSL connection, that is, the level of information encryption.
- Based on the agreed security level, the client's browser establishes a session key encrypts it using the web server's public key, and then sends it to the web server.
- The web server decrypts the session key using its private key.
- The web server uses the session key to encrypt the communication between the client and the web server.
Differences Between HTTP and HTTPS
The data transmitted by the HTTP protocol is unencrypted, which means it is in plaintext. Therefore, using the HTTP protocol to transmit private information is very insecure. To ensure the encrypted transmission of this private data, Netscape designed the SSL (Secure Sockets Layer) protocol to encrypt the data transmitted by the HTTP protocol, thus giving birth to HTTPS. In simple terms, the HTTPS protocol is a network protocol constructed from SSL + HTTP, which can perform encrypted transmission and identity authentication and is more secure than the HTTP protocol.
The main differences are as follows:
- The HTTPS protocol requires applying for a certificate from a CA, and generally, there are fewer free certificates, so there is a certain cost involved.
- HTTP is the Hypertext Transfer Protocol, where information is transmitted in plaintext, while HTTPS is a secure SSL encryption transmission protocol.
- HTTP and HTTPS use completely different connection methods and different ports; the former uses port 80, while the latter uses port 443.
- HTTP connections are simple and stateless; the HTTPS protocol is a network protocol constructed from SSL + HTTP that can perform encrypted transmission and identity authentication, making it more secure than the HTTP protocol.
What is an SSL Certificate?
SSL certificates, also known as digital certificates, are provided by Tencent Cloud in collaboration with well-known industry digital certificate authorities (CA, Certificate Authority). Tencent Cloud platform offers a one-stop management service for applying, managing, and cloud deploying both free and paid SSL certificates. SSL certificates provide a complete HTTPS solution for your website, mobile apps, web APIs, and other applications, including identity verification and encrypted data transmission.
What is the Role of SSL?
SSL certificates primarily serve HTTPS. After deploying the certificate, the website link changes from starting with HTTP to HTTPS.
They are mainly used for sending secure emails, accessing secure sites, online bidding and tendering, online contracting, online ordering, online office work, online payments, online tax payments, and other secure online electronic transactions.
The content of SSL certificates implements two basic functions:
1. Data Transmission Encryption
Our usual internet access and browsing are based on the standard TCP/IP protocol, with content transmitted in the form of data packets across the network.
Since the content of the data packets is not encrypted, anyone who intercepts them can obtain the contents. Therefore, if the data packets transmit usernames, passwords, or other personal privacy information, it is easy for others to steal them.
SSL can establish an encrypted channel between the client (e.g., browser) and the server used by the user. First, all data transmitted over the network will be encrypted and then decrypted after reaching the destination. This way, even if the data packet is intercepted during transmission, it is difficult to crack its content.
2. Server Information Verification
Currently, phishing websites have become a serious threat to internet usage. Attackers can create an interface identical to a real website and use similar domain names to direct users to visit.
If users are not careful, they can easily be deceived. Once users enter their account numbers, passwords, and other information on a phishing website, this information will be recorded and stolen, threatening the security of their accounts.
SSL server certificates can effectively prove the true information of the website and the legality of the domain name used, allowing users to easily identify real and fake websites.
SSL certificates go through strict review procedures to confirm the identity of the applicant during the application process. Users can see the content of the certificate when visiting the website, which includes the real domain name of the website, the owner of the website, the certificate issuing organization, and other information. Browsers also display corresponding security indicators, allowing visitors to use the site with confidence.
How to Deploy SSL Certificate to EdgeOne Domain?
- Log in to the EdgeOne Console and click the target site in the site list to display second-level menus for site management.
- In the left sidebar, click Domain Name Service > Domain Management.
- In the domain name list that appears, find the domain name for which the managed SSL certificate is to be configured and click Edit in the HTTPS column of the domain name.
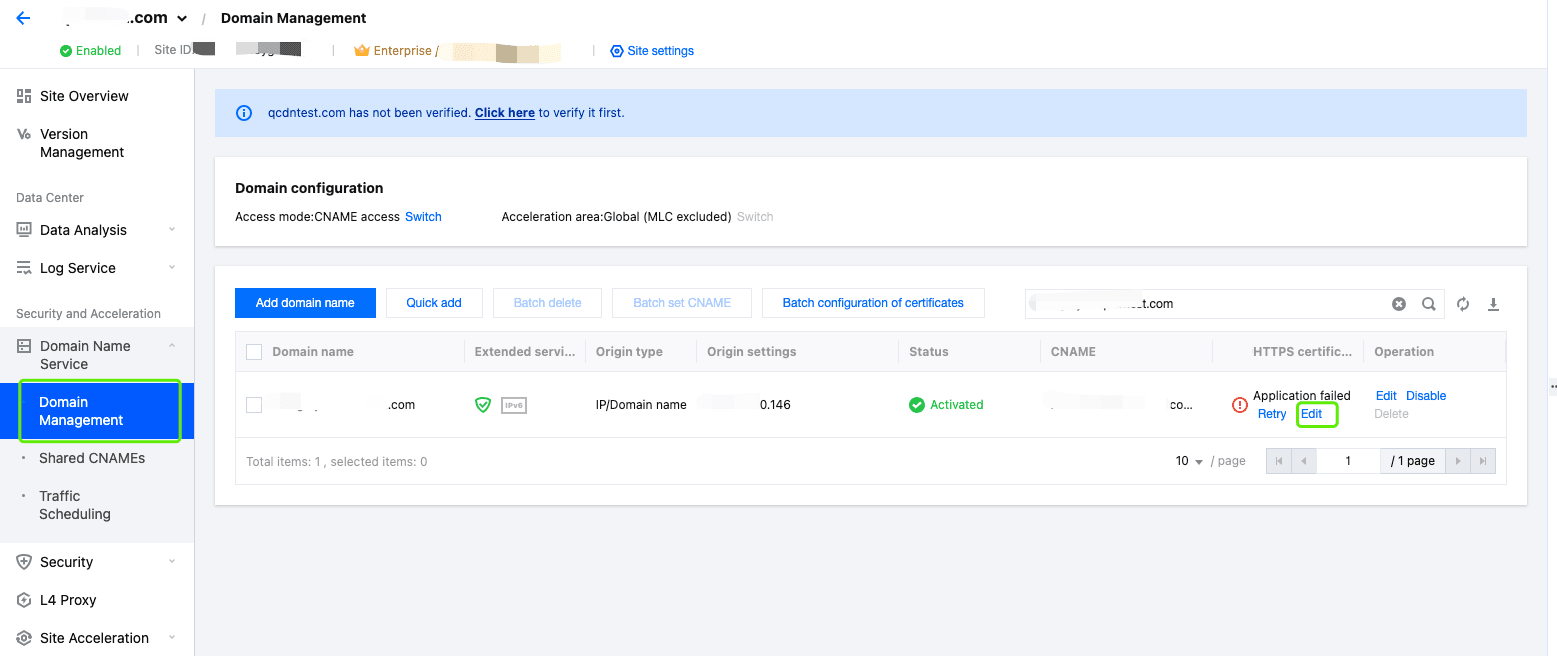
- In the pop-up window, set the Certificate type to Managed SSL certificate. In the certificate list that appears, select the ID of the certificate to be associated and click OK. Then the certificate configuration is delivered.
- In the domain name list, hover over the icon before Configured in the record of the target domain name, and you can see the information of the deployed certificate.
Note: Up to one ECC, one RSA, and one national secret SM2 encryption algorithm certificate can be deployed to the same domain.
What Types of Certificates are Supported by EdgeOne?
Tencent EdgeOne supports the following types of certificates:
- International Standard Certificates with RSA, ECC encryption algorithms.
- Chinese SM Standard Certificates with SM2 encryption.
- Free and paid certificates are available. If a domain for a Small-Medium Enterprise site or a personal blog needs to have HTTPS access, a free certificate can be configured for the domain.
- To switch sites from HTTP to HTTPS, a free certificate can be deployed to the EdgeOne domain (only single-domain certificates are supported).

