10 Best Website Security Scanners: Comprehensive Protection for Your Online Presence in 2025

In today's digital landscape, ensuring website security is crucial. Websites are often targeted by cybercriminals who exploit vulnerabilities to steal data, inject malware, or disrupt services. To protect your online presence, it is essential to use a reliable website security scanner. These tools help detect vulnerabilities, malware, and misconfigurations, keeping your website safe and secure. In this article, we will explore the 10 best website security scanners for 2025, highlighting their key features and benefits.
What are Website Security Scanners?
Website security scanners are specialized tools designed to automatically detect security vulnerabilities in web applications and websites. They work by simulating attacks against a target website, analyzing the responses, and generating reports on discovered vulnerabilities. Modern scanners can detect a wide range of issues, from common vulnerabilities like SQL injection and cross-site scripting (XSS) to more complex problems like misconfigurations and authentication weaknesses.
Types of Security Scanners
- Automated vs. Manual Scanning: Automated scanners perform predefined tests without human intervention, making them efficient for regular scanning of large websites. Manual scanning involves security professionals using tools to conduct more targeted and in-depth tests, often necessary for complex applications.
- Cloud-based vs. On-premise Solutions: Cloud-based scanners offer convenience, regular updates, and scalability without infrastructure investment. On-premise solutions provide greater control over sensitive data and scanning processes but require more maintenance and technical expertise.
Key Features to Look For
When evaluating website security scanners, consider these essential features:
- Comprehensive vulnerability detection
- Low false positive rates
- Regular database updates
- Intuitive reporting capabilities
- Compliance with industry standards (OWASP, PCI-DSS, etc.)
- Remediation guidance
- Integration capabilities with development workflows
Top 10 Website Security Scanners
1. EdgeOne
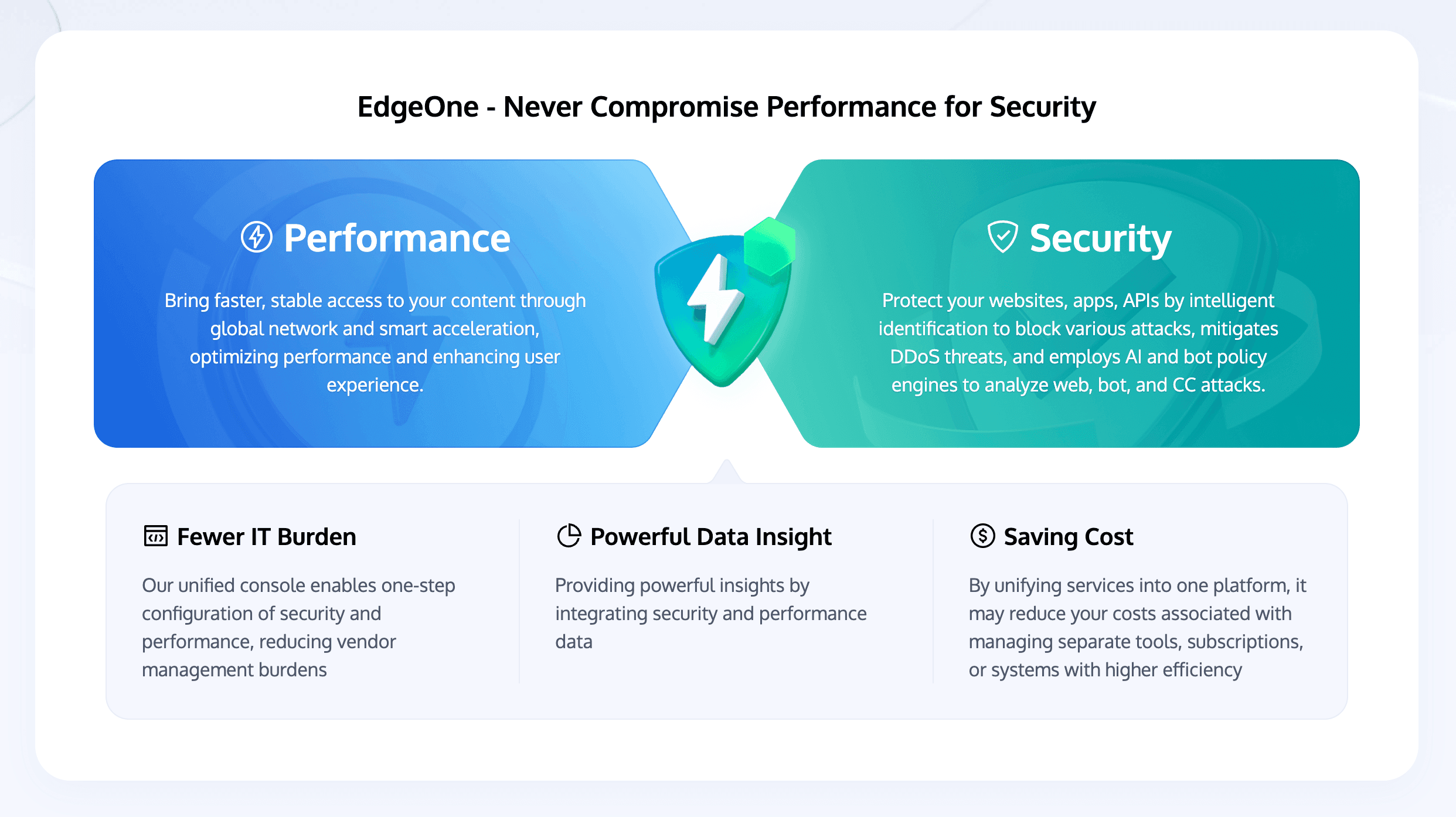
Tencent EdgeOne is a comprehensive edge security and acceleration platform designed to protect websites against various cyber threats while enhancing performance. It offers robust DDoS protection, CC attack defense, and advanced Web Application Firewall (WAF) capabilities to safeguard against SQL injection, XSS, and other common web vulnerabilities.
Key Features
- DDoS and CC Protection: EdgeOne provides intelligent CC and platform-level DDoS protection, detecting and mitigating abnormal traffic patterns to ensure website availability.
- Web Application Security: The built-in WAF can identify and block malicious requests, including SQL injection and XSS attacks.
- Performance Optimization: It accelerates web content delivery through optimized routing and caching, improving user experience.
- Customizable Security Rules: Users can define their own security policies to adapt to specific needs.
Link: 🔥 Start free trial
2. QualysGuard
QualysGuard is a cloud-based security and compliance scanning tool that offers comprehensive vulnerability management and configuration assessment. It is designed to help organizations maintain high levels of security and compliance.
Key Features
- Cloud-Based Security and Compliance Scanning: QualysGuard performs comprehensive scans from the cloud, ensuring that your website and infrastructure remain secure.
- Extensive Vulnerability Management: The tool offers extensive vulnerability management capabilities, helping organizations identify and mitigate security risks.
- Configuration Assessment: QualysGuard assesses your configuration settings to ensure that they are secure and compliant with industry standards.
Pros and Cons
- Pros: Comprehensive scanning, extensive feature set, strong compliance capabilities.
- Cons: Can be complex to set up, may be expensive for small businesses.
3. ZeroThreat
ZeroThreat is an AI-powered, fully automated web application and API security platform that helps you analyze, detect, prioritize, and remediate vulnerabilities. It combines Dynamic Application Security Testing (DAST) with automated penetration testing to simulate real attacks on every endpoint.
Key Features
- Seamless CI/CD Integration: Integrates with CI/CD pipelines for streamlined security testing.
- Continuous Scanning: Continuously scans for vulnerabilities with regularly updated detection rules.
- Rapid Prioritization: Enables rapid prioritization of vulnerabilities based on criticality.
- Customizable Reports: Generates customizable reports tailored for executives and developers.
- Real-World Attack Simulation: Simulates real-world attacks like an ethical hacker to uncover security gaps.
Pros and Cons
- Pros: Highly accurate with near-zero false positives, easy to use with no configuration needed, strong integration with development workflows.
- Cons: May not be as comprehensive for very large enterprises, limited manual customization options.
4. Burp Suite
Burp Suite is a popular tool among security professionals for its advanced web vulnerability scanning and penetration testing capabilities. It is highly customizable and offers a wide range of features for both automated and manual security assessments.
Key Features
- Advanced Web Vulnerability Scanning: Burp Suite provides comprehensive scanning for a wide range of vulnerabilities.
- Penetration Testing Tools: The tool includes a suite of tools for manual penetration testing, allowing security professionals to identify and exploit vulnerabilities.
- Customizable Attack Tools: Burp Suite allows users to customize their scanning and attack tools, making it highly adaptable to different security needs.
Pros and Cons
- Pros: Highly customizable, powerful penetration testing capabilities, extensive feature set.
- Cons: Can be complex to use and requires significant technical expertise.
5. Detectify
Detectify is an automated website security scanner that provides detailed reports and continuous monitoring. It is designed to be user-friendly and accessible to both technical and non-technical users.
Key Features
- Automated Website Security Scanning: Detectify performs regular automated scans to identify vulnerabilities and other security issues.
- Detailed Reports: The tool provides detailed and easy-to-understand reports, helping users address security concerns effectively.
- Continuous Monitoring: Detectify offers continuous monitoring and alerts, ensuring that your website remains secure at all times.
Pros and Cons
- Pros: User-friendly interface, detailed reports, continuous monitoring.
- Cons: Limited customization options, may not be as comprehensive as some other tools.
6. Intruder
Intruder is a cloud-based vulnerability scanner that offers automated scanning and easy-to-understand reports. It is designed to be easy to use and integrate into existing workflows.
Key Features
- Cloud-Based Vulnerability Scanning: Intruder performs automated scans from the cloud, making it accessible and easy to use.
- Automated Scan Scheduling: The tool allows users to schedule regular scans, ensuring that security issues are identified promptly.
- Easy-to-Understand Reports: Intruder provides clear and concise reports, making it easy for users to understand and address security concerns.
Pros and Cons
- Pros: Easy to use, cloud-based scanning, regular updates.
- Cons: Limited customization options, may not be as comprehensive as some other tools.
7. APIsec
APIsec is a specialized tool designed to provide comprehensive security scanning for APIs. It is particularly useful for organizations that rely heavily on API-based integrations.
Key Features
- Specialized in API Security: APIsec is specifically designed to identify vulnerabilities in APIs, ensuring that your API-based integrations are secure.
- Automated Vulnerability Detection: The tool performs automated scans to identify potential security issues.
- Customizable Scan Configurations: APIsec allows users to customize their scanning configurations, making it adaptable to different security needs.
Pros and Cons
- Pros: Specialized API security, customizable scanning, detailed reports.
- Cons: Limited to API security, may not cover other aspects of web security.
8. Nessus
Nessus is a comprehensive vulnerability assessment tool that offers extensive network and web application scanning capabilities. It is widely used by both small and large organizations to identify and mitigate security risks.
Key Features
- Comprehensive Vulnerability Assessment: Nessus performs detailed scans to identify a wide range of vulnerabilities, including those in web applications and networks.
- Extensive Network Scanning: The tool offers comprehensive network scanning capabilities, ensuring that all aspects of your infrastructure are secure.
- Regular Plugin Updates: Nessus regularly updates its plugins to ensure that it can detect the latest vulnerabilities and threats.
Pros and Cons
- Pros: Comprehensive scanning, extensive feature set, regular updates.
- Cons: Can be complex to set up and use, requires significant technical knowledge.
9. Invicti
Invicti is a powerful web application security scanner that offers automated scanning and real-time alerts. It is designed to be highly accurate and user-friendly, making it suitable for both technical and non-technical users.
Key Features
- Automated Scanning: Invicti performs automated scans to identify vulnerabilities and other security issues.
- Real-Time Alerts: The tool provides real-time alerts, ensuring that security issues are addressed promptly.
- Accurate and Actionable Security Insights: Invicti provides detailed and accurate reports, helping users understand and mitigate security risks.
Pros and Cons
- Pros: Highly accurate scanning, user-friendly interface, real-time alerts.
- Cons: Can be expensive, limited customization options.
10. Acunetix
Acunetix is a widely recognized website security scanner known for its comprehensive vulnerability detection capabilities. It is designed to identify a wide range of security issues, including SQL injection, cross-site scripting (XSS), and other common web vulnerabilities.
Key Features
- Automated Vulnerability Scanning: Acunetix can automatically scan your website for vulnerabilities, providing detailed reports on identified issues.
- Customizable Reporting: The tool allows users to generate customizable reports, making it easier to understand and address security concerns.
- Integration with CI/CD: Acunetix integrates seamlessly with continuous integration and continuous deployment (CI/CD) pipelines, ensuring that security is maintained throughout the development process.
Pros and Cons
- Pros: Highly accurate scanning, extensive feature set, excellent support.
- Cons: Can be expensive for small businesses, requires some technical knowledge to fully utilize.
Comparison Criteria for Website Scanners
Scanning Capabilities and Detection Rates
The most effective scanners offer comprehensive coverage of both common vulnerabilities (OWASP Top 10) and more sophisticated threats. Acunetix and Burp Suite consistently demonstrate the highest detection rates for complex vulnerabilities, while Qualys and Nessus provide broader coverage across various systems.
Ease of Use and User Interface
For organizations without dedicated security personnel, tools like Intruder and Detectify offer intuitive interfaces and actionable reports. More complex tools like OWASP ZAP and Burp Suite provide greater control but require more technical expertise.
Reporting Features
Qualys and Nessus excel in detailed reporting suitable for compliance purposes. Detectify and Intruder offer more business-friendly reports that effectively communicate risk to non-technical stakeholders.
Integration Capabilities
Modern development practices require security tools that integrate with CI/CD pipelines. SonarQube, Acunetix, and OWASP ZAP provide strong integration options for DevSecOps environments.
Price-to-Value Ratio
Open-source tools like OWASP ZAP offer exceptional value for organizations with technical expertise. For businesses seeking commercial support, Intruder and Detectify provide good value for medium-sized organizations, while enterprise solutions like Acunetix and Qualys deliver comprehensive capabilities at higher price points.
Support and Documentation
Commercial tools generally offer better support options, with Acunetix and Qualys providing excellent documentation and customer service. Open-source alternatives rely on community support, which can vary in responsiveness and thoroughness.
How to Choose the Right Security Scanner
Assessment of Your Specific Security Needs
Begin by identifying your organization's specific requirements:
- Are you primarily concerned with compliance requirements?
- Do you need to scan custom-built applications or standard CMS platforms?
- Is continuous monitoring essential, or are periodic scans sufficient?
- What types of vulnerabilities are most relevant to your technology stack?
Budget Considerations
Security scanning solutions range from free open-source tools to enterprise platforms costing thousands annually. Consider:
- Total cost of ownership, including setup and maintenance
- Return on investment through risk reduction
- Scaling costs as your organization grows
Technical Expertise Required
Match the tool to your team's capabilities:
- Organizations with security professionals can leverage more complex tools like Burp Suite
- Those without dedicated security staff may prefer user-friendly solutions like Intruder or Detectify
- Consider training requirements and learning curve
Compliance Requirements
If your organization must meet specific compliance standards:
- PCI-DSS: Qualys, Nessus, and Acunetix offer specialized scanning profiles
- HIPAA: Look for tools with detailed reporting like Nexpose
- SOC 2: Solutions with continuous monitoring capabilities are advantageous
Best Practices for Website Security
Regular Scanning Schedule
Implement a consistent scanning regimen:
- Critical applications: Weekly or bi-weekly scans
- Standard websites: Monthly scans
- After significant changes: Immediate scan before deployment
Complementary Security Measures
Website scanners are just one component of a comprehensive security strategy:
- Web Application Firewalls (WAFs) for real-time protection
- Content Security Policy implementation
- Regular backups and disaster recovery planning
- SSL/TLS certificate management
Importance of Updates and Patches
Maintain current software across your technology stack:
- Apply security patches promptly
- Update scanning tools regularly for the latest vulnerability definitions
- Review deprecated technologies in your stack
Employee Training
Human factors remain crucial in security:
- Train developers in secure coding practices
- Educate content managers about security risks
- Establish clear security protocols for all website administrators
Conclusion
In conclusion, website security scanners are essential tools for protecting your online presence from cyber threats. The 10 best website security scanners for 2025 offer a range of features and capabilities to help you detect and mitigate vulnerabilities. When selecting a scanner, consider factors such as accuracy, ease of use, customization options, and pricing to find the best tool for your needs. By using a reliable website security scanner, you can ensure that your website remains secure and protected in today's digital landscape.

