Top 10 Cyber Security and Hacking Movies you must watch in 2024
Cyber security and hacking have become prominent themes in the world of cinema, captivating audiences with thrilling narratives and thought-provoking storylines. This article highlights the top 10 cybersecurity and hacking movies that you should watch in 2024, offering a brief overview of each film's title and plot.
What is Cyber Security?
Cyber security refers to the practice of protecting computer systems, networks, and data from digital threats, including unauthorized access, data breaches, and cyber attacks. It involves implementing measures to prevent, detect, and respond to potential security risks in order to maintain the confidentiality, integrity, and availability of information.

Top 10 Cyber Security and Hacking Movies
1. "Digital Shadows"
A brilliant cyber security analyst discovers a hidden network of hackers planning a large-scale cyber attack. As she races against time to stop the impending disaster, she uncovers a web of deception and betrayal.
2. "Dark Code"
A former hacker turned cybersecurity expert is forced to confront his past when a notorious cybercriminal resurfaces. With lives at stake, he must outsmart his old nemesis and protect the world from a devastating cyber threat.
3. "Zero Day"
Two teenage prodigies stumble upon a zero-day vulnerability that could bring down the entire internet. As they navigate the dangerous world of hacking, they must decide whether to use their skills for good or fall into the wrong hands.
4. "Cipher"
A cryptographer is recruited by a government agency to decipher an encrypted message that holds the key to preventing a global cyber catastrophe. As she delves deeper into the code, she realizes the stakes are higher than she ever imagined.
5. "The Firewall"
A cybersecurity expert is hired to protect a high-profile corporation from a relentless hacker. As she battles against an elusive adversary, she uncovers a conspiracy that threatens not only her client but also her own life.
6. "Code Breaker"
Inspired by true events, this film follows the journey of a brilliant mathematician who joins a top-secret government project to crack an unbreakable encryption code. As he delves deeper into the code, he realizes the implications it holds for national security.
7. "The Cyber Heist"
A group of skilled hackers orchestrates a daring cyber heist, targeting a powerful financial institution. As they navigate through layers of security, they must outsmart both the authorities and rival hackers to pull off the ultimate score.
8. "Virtual Intrusion"
In a near-future world where virtual reality dominates, a skilled hacker discovers a hidden agenda within the virtual realm. As she fights against powerful forces, she must expose the truth and protect the freedom of the virtual world.
9. "The Network"
A cybersecurity analyst uncovers a vast network of hackers operating within the government. As she races against time to expose the truth, she becomes entangled in a web of conspiracy and must fight to protect her own life.
10. "The Dark Web"
A journalist delves into the dark web to investigate a series of cybercrimes. As she goes deeper into the hidden corners of the internet, she becomes a target herself, facing off against dangerous hackers and uncovering shocking secrets.
What Does Cyber Security Focus On?
Cybersecurity focuses on protecting computer systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. It encompasses various aspects, including:
1. Confidentiality: Ensuring that sensitive information is accessible only to authorized individuals or entities and remains protected from unauthorized disclosure.
2. Integrity: Maintaining the accuracy, consistency, and trustworthiness of data and systems by preventing unauthorized modifications or tampering.
3. Availability: Ensuring that systems, networks, and data are accessible and usable when needed, minimizing downtime and disruptions caused by cyber attacks or technical failures.
4. Authentication: Verifying the identity of users, devices, or systems to ensure that only authorized entities can access resources or perform specific actions.
5. Authorization: Granting appropriate access privileges to authorized individuals or entities based on their roles, responsibilities, and the principle of least privilege.
6. Risk Management: Identifying, assessing, and mitigating potential risks and vulnerabilities to minimize the likelihood and impact of cyber threats.
7. Incident Response: Developing and implementing plans and procedures to effectively respond to and recover from cybersecurity incidents, including detecting, analyzing, and mitigating the effects of attacks.
8. Security Awareness and Training: Educating users about potential risks, best practices, and safe behaviors to enhance their understanding of cybersecurity and reduce the likelihood of human error.
9. Network Security: Implementing measures to protect networks from unauthorized access, including firewalls, intrusion detection systems, and virtual private networks (VPNs).
10. Application Security: Ensuring the security of software applications by implementing secure coding practices, conducting regular vulnerability assessments, and applying patches and updates.
11. Data Protection: Implementing encryption, access controls, and data loss prevention measures to safeguard sensitive information from unauthorized access or disclosure.
12. Threat Intelligence: Monitoring and analyzing emerging cyber threats, vulnerabilities, and attack techniques to proactively identify and respond to potential risks.
Enhance your cybersecurity with Tencent EdgeOne
Tencent EdgeOne provides an acceleration and security solution based on Tencent edge nodes and provides security protection services such as WAF and Anti-DDoS. Nodes identify and block various layer-3/4/7 attack requests, cleanse DDoS attack traffic, and use the smart AI engine and bot policy engine to analyze the behaviors of web, bot, and CC attacks and update attack blocking policies. This helps prevent malicious requests from reaching your origin servers and guarantees smooth and stable access to your business.
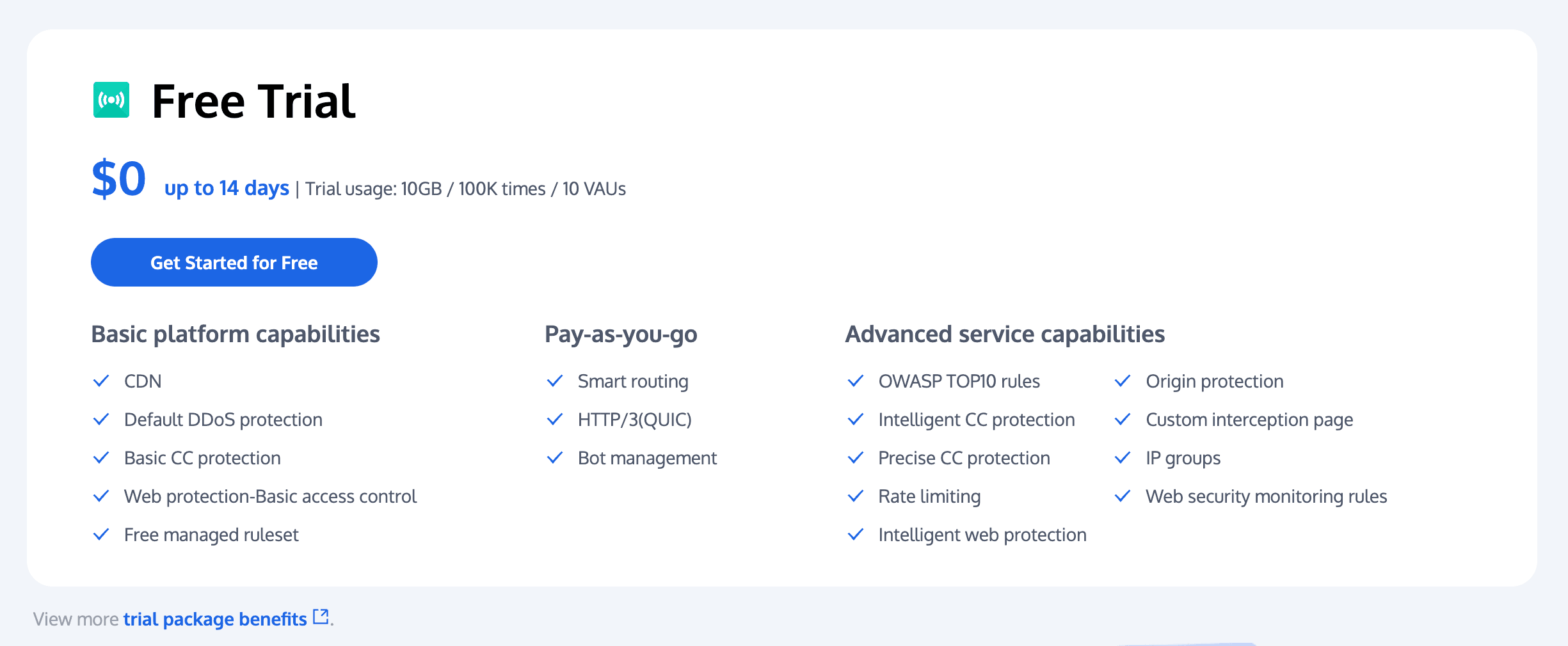 Tencent Edgeone has now launched a free trial offer. Click here to start free trial or contact us for more information.
Tencent Edgeone has now launched a free trial offer. Click here to start free trial or contact us for more information.

