Top Tools to Perform DDoS Attacks: Know Your Enemy's Arsenal for Stronger Defense
In today's hyperconnected digital ecosystem, Distributed Denial of Service (DDoS) attacks have evolved from occasional disruptions to persistent, sophisticated threats against organizations of all sizes. The frequency, scale, and complexity of these attacks continue to grow at an alarming rate. These digital tsunamis can devastate unprepared targets within minutes, resulting in service outages, financial losses, reputational damage, and erosion of customer trust.
As critical infrastructure, financial services, e-commerce, and even government services migrate to online platforms, the potential impact of successful DDoS attacks extends far beyond mere inconvenience. For security professionals responsible for protecting digital assets, developing effective defense strategies requires a thorough understanding of the adversary's capabilities and techniques.
What is DDoS?
Distributed Denial of Service (DDoS) attacks represent a significant threat in the cybersecurity landscape. These attacks aim to overwhelm a target system, network, or service with a flood of internet traffic, rendering it inaccessible to legitimate users.
Common types of DDoS attacks include:
- Volume-based attacks: Flooding the target with massive amounts of traffic to consume bandwidth
- Protocol attacks: Exploiting vulnerabilities in network protocols to drain server resources
- Application layer attacks: Targeting specific applications or services with seemingly legitimate requests
Is DDoS Illegal?
DDoS attacks are explicitly illegal in most jurisdictions worldwide under computer crime statutes. In the United States, conducting DDoS attacks violates the Computer Fraud and Abuse Act (CFAA), potentially resulting in federal felony charges with penalties including up to 10 years in prison and substantial fines. Similarly, the UK's Computer Misuse Act and the EU's Directive on Attacks Against Information Systems criminalize such activities.
Even "minor" DDoS attacks or those conducted against personal targets can trigger serious legal consequences. Several individuals have received significant prison sentences for launching DDoS attacks against gaming services, financial institutions, and government websites. Furthermore, many countries have enhanced their cooperation in prosecuting cybercrime across borders, making international enforcement increasingly effective.
The only legitimate contexts for DDoS testing are:
- Authorized penetration testing with explicit written permission
- Controlled testing environments isolated from production systems
- Academic research conducted under appropriate ethical guidelines
Understanding DDoS Tools for Better Defense
While discussing attack tools may seem controversial, understanding how attackers operate is essential for building effective defenses. As the military strategist Sun Tzu famously wrote, "Know your enemy and know yourself; in a hundred battles, you will never be defeated." This principle applies directly to cybersecurity—security professionals who comprehend attack methodologies can design more resilient systems.
By analyzing the capabilities, limitations, and signatures of common DDoS tools, defenders can:
- Identify attack patterns more quickly during security incidents
- Configure detection systems to recognize tool-specific signatures
- Implement targeted countermeasures against specific attack techniques
- Test defensive systems against realistic attack scenarios
With this defensive mindset, let's examine the most prevalent DDoS attack tools, their mechanisms, and the specific threats they pose to modern networks.
Top Tools to Perform DDoS Attacks
Cyber attackers typically employ DDoS attack tools to disrupt the normal operations of targeted websites, servers, or networks by overwhelming them with a flood of internet traffic. These tools exploit multiple compromised computer systems as sources of attack traffic. Devices can include computers and other networked resources such as IoT devices. The sophistication and availability of these tools have increased over the years, making it easier for attackers to launch large-scale attacks.
Using DDoS tools to conduct cyber attacks for malicious purposes is illegal and unethical, but similar incidents occur frequently and the number is increasing significantly. Understanding these tools is crucial to developing effective defenses that can identify and mitigate attacks before they cause significant damage.
The following provides a comprehensive overview of the tools commonly used to perform DDoS attacks and their principles and mechanisms:
LOIC (Low Orbit Ion Cannon)
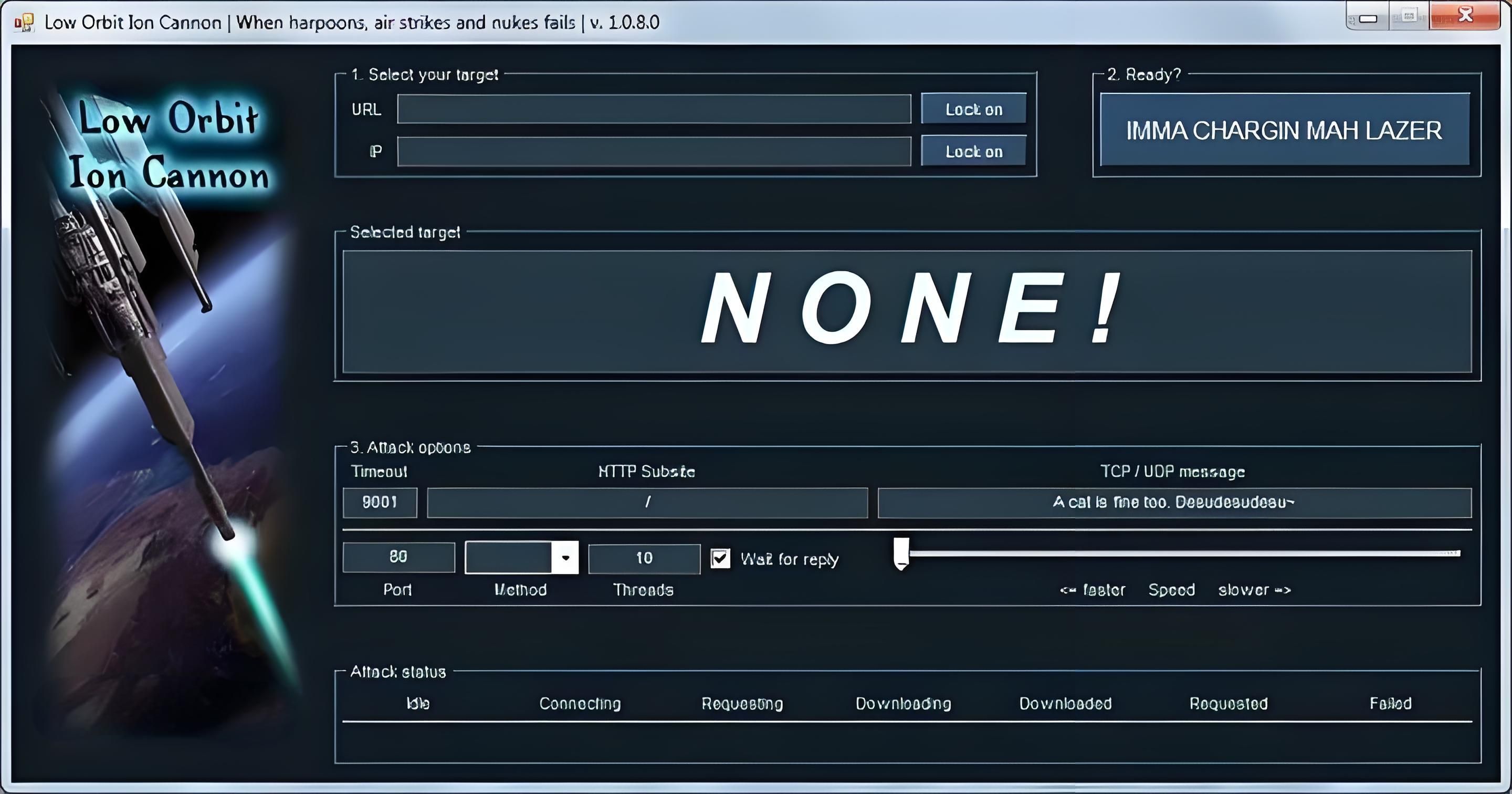
Description: Originally developed for network stress testing, LOIC has been repurposed for DDoS attacks. It is an open source tool that allows users to attack the target server by sending a large number of requests. LOIC can use a single user or multiple users to work together to form a distributed attack, thereby increasing the power of the attack. This tool also has a HIVEMIND mode. It lets attacker control remote LOIC systems to perform a DDOS attack. This feature is used to control all other computers in your zombie network. This tool can be used for both DOS attacks and DDOS attacks against any website or server. The most important thing you should know is that LOIC does nothing to hide your IP address.
Mechanism: It can flood a target with TCP, UDP, or HTTP requests.
Usage: Often used in coordinated attacks by hacktivist groups like Anonymous.
HOIC (High Orbit Ion Cannon)
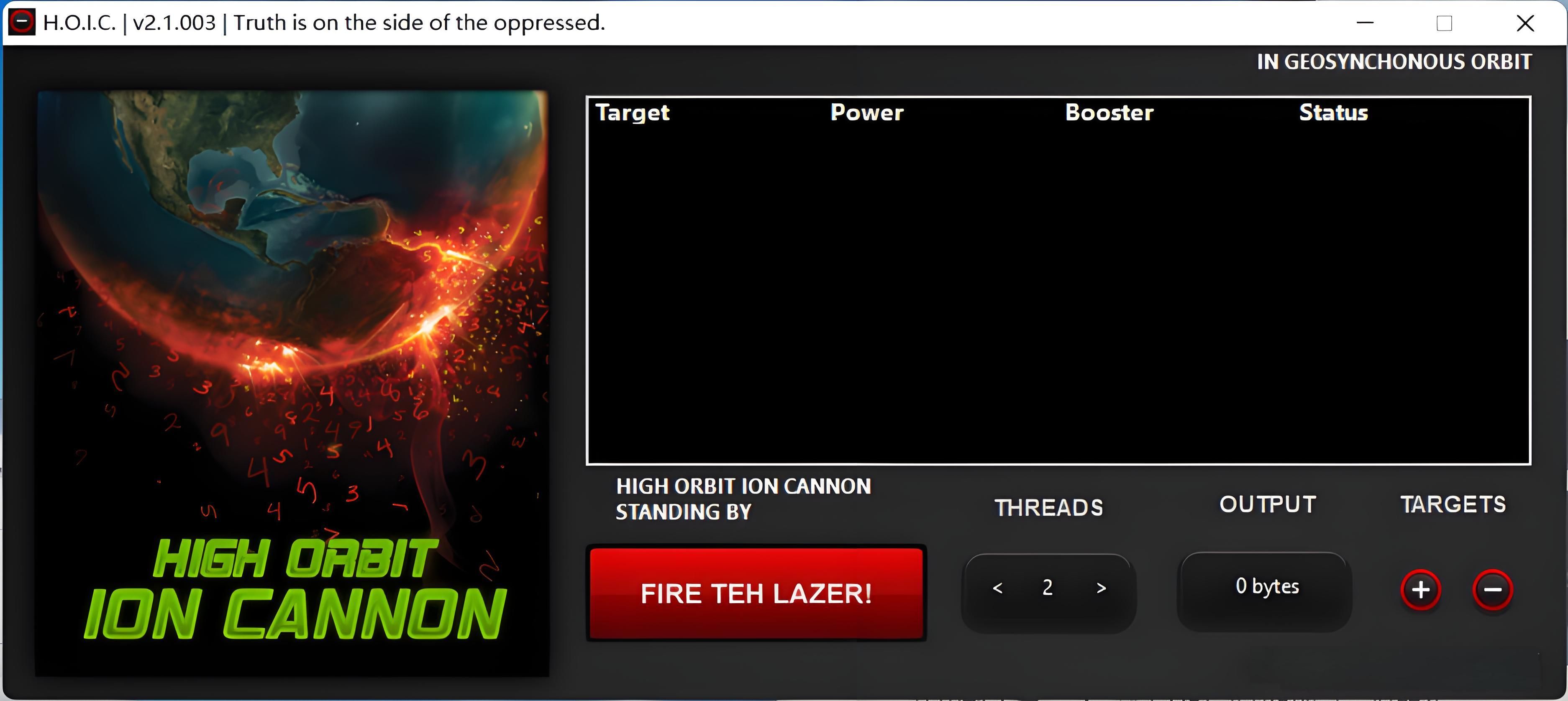
Description: An advanced version of LOIC, HOIC is more powerful and versatile. Unlike LOIC, HOIC can use multiple proxy servers, thereby hiding the attacker's real IP address. This makes it more difficult to track and block the attack.
Mechanism: It can launch HTTP floods with customizable attack patterns and supports "booster scripts" to increase the attack's effectiveness.
Usage: Suitable for more sophisticated DDoS attacks.
XOIC (eXtreme Orbit Ion Cannon)
Description: XOIC is a tool used for conducting Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks. It is designed to be user-friendly, making it accessible even to those with limited technical knowledge. Developers of XOIC claim that XOIC is more powerful than LOIC in many ways. The tool comes with three attacking modes. The first one, known as test mode, is very basic. The second is normal DOS attack mode. The last one is a DOS attack mode that comes with a TCP/HTTP/UDP/ICMP Message. The tool supports multiple attack methods, including:
- TCP Flood: Sends a large number of TCP packets to the target, overwhelming its ability to process legitimate requests.
- UDP Flood: Sends a flood of UDP packets to the target, consuming its bandwidth and resources.
- HTTP Flood: Generates a high volume of HTTP requests to overwhelm web servers.
Mechanism: It performs a DOS attack an any server with an IP address, a user-selected port, and a user-selected protocol. The user configures the type of attack (TCP, UDP, or HTTP) and sets parameters such as packet size and the number of threads. Once configured, the user initiates the attack. XOIC then generates and sends a large volume of packets to the target, aiming to overwhelm its resources.
Botnets
Description: Networks of compromised computers (bots) controlled by an attacker. These infected devices can be PCs, servers, smartphones, or even Internet of Things (IoT) devices. Botnets are usually spread through malware to infect these devices, which attackers infect with malware and bring into a centralized control.
Mechanism: Botnets can launch large-scale DDoS attacks by coordinating the actions of thousands or even millions of infected devices. It can generally be divided into infection stage, control stage, and attack stage.
Examples: Mirai, which targets IoT devices, is a well-known botnet used for DDoS attacks.
Slowloris
Description: A tool designed to keep many connections to the target web server open and hold them open as long as possible. It sends partial HTTP requests, keeping the server's resources tied up and unable to serve legitimate users.
Mechanism: Slowloris send partial HTTP requests to the target server, but do not complete them. Only send the HTTP header information. Periodically send small amounts of data (the continuation of the HTTP header) to prevent the server from closing the connection. The server allocates resources (such as memory and processing power) for each unfinished request. A large number of unfinished requests will exhaust the server resources. When the server resources are exhausted, it cannot process new legitimate requests, resulting in service interruption.
Usage: Effective against certain types of web servers, particularly those with limited connection handling capabilities.
R-U-Dead-Yet (RUDY)
Description: Targets web applications by injecting long form field submissions. It performs a DOS attack with a long form field submission via the POST method. This tool comes with an interactive console menu. It detects forms on a given URL and lets users select which forms and fields should be used for a POST-based DOS attack.
Mechanism: Exploits the HTTP POST method to keep connections open and exhaust server resources.
Usage: Particularly effective against web applications with form submission functionalities.
Xerxes
Description: Xerxes is a tool specifically designed to attack web servers. Known for its simplicity and effectiveness, Xerxes can overwhelm a target server with a flood of requests, leading to service disruption. It is often used in Distributed Denial of Service (DDoS) attacks aimed at making the target server unable to handle legitimate user requests.
Mechanism: Xerxes can generate a large number of HTTP requests, which are simultaneously sent to the target server. Xerxes can spoof the source addresses of the requests, making it difficult for the server to distinguish between legitimate and malicious requests. Xerxes utilizes multi-threading or multi-processing techniques to create a large number of concurrent connections, maximizing the attack's impact.
Usage: Often used in targeted DDoS attacks against specific web servers.
Defending Against the DDoS Attacks with EdgeOne
This article has discussed some of the most well-known DDoS attack tools, such as LOIC and HOIC. However, the DDoS landscape is much broader than just these examples. Other tools like HULK, DDOSIM, PyLoris, DAVOSET, and Tor's Hammer utilize various attack vectors and techniques to achieve similar disruptive outcomes.
By understanding the methods and mechanisms employed by these tools, you can better anticipate potential threats and formulate strong defense strategies. This knowledge allows you to identify vulnerabilities in your network, implement appropriate security measures, and respond quickly to minimize the impact of an attack.
Tencent EdgeOne offers comprehensive DDoS protection against a wide range of DDoS threats through its multi-layered defense system, which is designed to handle attacks of any size or complexity. The platform continuously monitors network traffic and automatically triggers mitigation when attack indicators are detected. It leverages advanced traffic analysis, behavioral pattern recognition, and AI-powered detection algorithms to identify and neutralize evolving attack methods. EdgeOne's global distribution network stops attacks closer to their source, safeguarding against volumetric floods, protocol exploits, and sophisticated application layer attacks before they can disrupt your infrastructure.
In today's threat landscape, robust DDoS protection isn't optional—it's essential for business continuity and digital trust. Experience EdgeOne's enterprise-grade DDoS protection capabilities through our free trial program. Our security experts can help assess your current vulnerabilities and design a protection strategy tailored to your specific needs.
Start Your Free Trial or Contact Our Security Team to learn more about protecting your digital assets from increasingly sophisticated DDoS threats.

