25+ Essential IPv6 Network Security Questions and Answers for Enterprises

IPv6 is the sixth-generation Internet Protocol. The fourth-generation Internet Protocol, IPv4, has gone through the rapid development stage of the mobile Internet, providing services for video, gaming, and payment. However, with the development of the industrial Internet, IPv4 can no longer meet the skyrocketing network demands of the world, and IPv6 was born as a result. In simple terms, the number of IPv6 addresses can assign an IP address to every grain of sand worldwide. And an IP address is our "house number" on the Internet.
25 IPv6 Security Questions and Answers
Q1: Is the IPv6 protocol more secure than the IPv4 protocol?
Answer: In addition to its rich address resources, precise correspondence, and traceable information, data transmission between IPv6 addresses will be encrypted, making it more difficult for information to be eavesdropped or hijacked. Therefore, overall, security is an important feature of IPv6. However, the increased complexity of IPv6 may lead to a higher number of attack vectors, allowing malicious hackers to execute various types of attacks. So, from a protocol perspective, IPv6 will face more security risks.
Q2: In terms of deployment security, which is safer, IPv6 or IPv4?
Answer: From the perspective of deployment security, IPv6 and IPv4 need to be compared in the following four dimensions:
- Protocol Specification Maturity: Security researchers discovered and patched Network security protocol-related vulnerabilities through long-term observation. The IPv4 protocol has undergone long-term maintenance and patching by security personnel, making it more mature and stable at this stage compared to IPv6.
- Implementation Maturity: Currently, IPv6 lacks appropriate recommendations to prevent vulnerability implementation, and its protocol design still needs improvement.
- Confidence/Experience in the Protocol: Compared to the mature IPv4 network environment, network security engineers will need some time to accumulate experience in combating network security threats in the new IPv6 environment.
- Support from Security Devices and Tools: Although security devices and tools can effectively support both IPv4 and IPv6 after improvements, the network security risks in the process of IPv6 deployment and application have not yet been fully revealed. There are still shortcomings in the features and performance of security devices and tools.
Q3: Do users of IPv4 networks need to deploy security measures for IPv6?
Answer: Yes.
Since the end of November 2017, when the national "Action Plan for Promoting the Large-scale Deployment of the Sixth Edition of the Internet Protocol (IPv6)" was launched, various operators have been able to install native IPv6 broadband networks for users. Therefore, the network used by users is likely to have dual-stack access, capable of communicating with both IPv4 and IPv6 networks.
If an attacker enables global IPv6 connectivity on the user's network, nodes in the user's network may inadvertently use IPv6 nodes intended for local traffic for non-local traffic, providing opportunities for attackers.
Q4: Do users need to increase the use of IPv6 Internet Security Protocol (IPSec)?
Answer: Currently, IPv6 IPSec is disabled by default, and users do not need to increase the use of IPSec themselves. Previous IPv6 specifications required all nodes to support IPSec, and the expected ability of IPv6 networks to use local IPSec could lead to widespread use of IPSec and affect network transmission rates.
Q5: What tools can users use to assess their networks and devices?
Answer: Users can use SI6 Networks' IPv6 Toolkit, The Hacker's Choice IPv6 Attack Toolkit, and Chiron, which are three free and open-source IPv6 toolkits.
Q6: Can IPv6 network addresses be scanned?
Answer: Usually not, as standard IPv6 subnets are /64s and user-end device network addresses are randomly distributed within a vast address space, making global scanning impossible.
However, when infrastructure nodes (such as routers, servers, etc.) typically use predictable addresses and client nodes (laptops, workstations, etc.) use random addresses, "targeted" address scanning can easily discover infrastructure nodes and then use scanning tools to obtain user-end device network addresses based on specific address patterns.
Q7: Can network reconnaissance be performed in an IPv6 network?
Answer:
- If the target is a local area network, network reconnaissance can be performed using multicast probing and multicast DNS queries.
- If the target is a remote network, techniques such as Pattern-based address scans, DNS zone transfers, DNS reverse mappings, Certificate Transparency framework, and search engines can be used to achieve network reconnaissance.
Q8: Is it possible to execute host-tracking attacks in IPv6?
Answer: It depends.
Host tracking refers to the correlation of network activity when a host moves across networks. Traditional SLAAC addresses require nodes to embed their MAC addresses into the IPv6 interface identifier, making IPv6 host tracking very weak. Temporary addresses mitigate some issues by providing random addresses for (client-like) outbound communication, while stable privacy addresses replace traditional SLAAC addresses, eliminating the problem.
Over time, implementations have evolved towards temporary addresses and stable privacy addresses. However, you should check if your operating system supports these standards.
Q9: Should unpredictable addresses be set for servers?
Answer: After analyzing the relevant trade-offs and conveniences of each network scenario, administrators can set unpredictable addresses for some important servers. By setting unpredictable addresses, attackers will have a hard time "targeting all servers within a given prefix."
Q10: How to deal with network reconnaissance behavior based on DNS reverse mapping?
Answer: You can configure DNS reverse mapping only for systems that require it, such as mail transfer agents, or configure wildcard reverse mapping so that every possible domain name in the reverse mapping contains a valid PTR record.
Q11: Are there address resolution and auto-configuration attacks in the IPv6 network environment?
Answer: IPv6's Neighbor Discovery Protocol (NDP) combines protocols such as ARP, ICMP router discovery, and ICMP redirects from IPv4, and makes improvements to them. As a foundational protocol of IPv6, NDP also provides prefix discovery, neighbor unreachability detection, address resolution, duplicate address detection, and address auto-configuration functions.
Therefore, NDP and auto-configuration attacks in the IPv6 network environment are equivalent to ARP and DHCP-based attacks from IPv4. If users' IPv4 networks are threatened by ARP/DHCP attacks, they must also pay attention to the security threats brought by NDP and auto-configuration attacks in IPv6 networks.
Users can address the security risks caused by NDP and auto-configuration attacks in IPv6 networks by using RA-Guard and DHCPv6-Shield/DHCPv6-Guard methods.
Q12: What are the differences between SLAAC and DHCPv6 in terms of address records?
Answer: When using SLAAC for address configuration, there is no centralized log of IPv6 addresses since the addresses are "auto-configured."
When DHCPv6 is applied for address configuration, the server typically maintains an IPv6 address lease log. Once a host is compromised and the maintenance of the IPv6 address lease log is detected, malicious actors can easily launch attacks through infected nodes.
At the same time, DHCPv6 does not prevent hosts from configuring addresses on their own (i.e., not requesting addresses through DHCPv6), so DHCPv6 logs should only be used when nodes cooperate with the network.
Q13: Can RA-Guard and DHCPv6-Guard/Shield be used to defend against auto-configuration attacks?
Answer: It depends.
Many implementations of these mechanisms can be easily bypassed through IPv6 extension headers. In some cases, bypassing can be reduced by discarding packets containing "hop-by-hop options."
Q14: Should users deploy Secure Neighbor Discovery (SeND) on their networks?
Answer: Deployment is not recommended.
Currently, there are hardly any host operating systems that support SeND.
Q15: What is a Neighbor Cache Exhaustion (NCE) attack, and how can it be mitigated?
Answer: NCE can cause target devices to become unresponsive, crash, or restart. The goal of an NCE attack is to create an arbitrary number of entries in the neighbor cache, making it impossible to create new legitimate entries, leading to a denial of service. NCE can also be a side effect of address scanning in remote networks, where the last-hop router creates an entry for each target address, eventually exhausting the neighbor cache.
Mitigating NCE can limit the number of neighbor cache entries in an incomplete state. Or, when facing an NCE attack from point-to-point connected nodes, using long prefixes (e.g., /127s) for point-to-point links to artificially limit the maximum number of entries in the neighbor cache.
Q16: Will the gradual popularization of IPv6 networks promote the transformation from a network-centric security paradigm to a host-centric security paradigm?
Answer: No.
The security model of IPv4 networks is not entirely "network-centric" either, but rather based on both host-based firewalls and network-based firewalls. Future IPv6 networks are likely to follow the previous hybrid model.
Q17: After deploying IPv6 networks, will all systems be exposed to the public IPv6 Internet?
Answer: Not necessarily.
Although almost all IPv6 networks may use global address space, this does not mean any-to-any global reachability. For example, IPv6 firewalls may be deployed at the same points in the network topology as NAT devices currently used in IPv4 networks. Such IPv6 firewalls may implement "outbound communication only" filtering policies, resulting in host exposure similar to that in IPv4 networks.
Q18: Can IPv6 addresses be blacklisted in the IPv6 environment as they are in the IPv4 environment? What granularity should be used to set blacklists for IPv6 addresses?
Answer: Yes.
Since IPv6 hosts can typically configure any number of IPv6 addresses within their /64 local subnet, users should blacklist at least the /64 address detected with malicious activity when a malicious event occurs.
Depending on the specific upstream ISP, an attacker can control prefixes of any length between /48 and /64 (e.g., if the attacker obtains a delegated prefix through DHCPv6-PD). Therefore, within the possible range, if malicious activity persists after the customer blacklists the offending /64, you may want to block shorter prefixes (larger address blocks) - for example, start by blocking a /64, then block a /56 or /48 if necessary.
Q19: Is it safe to block IPv6 fragments for security reasons in systems/networks?
Answer: It depends on the situation because discarding IPv6 fragments is only safe when two conditions are met:
- Use protocols that can avoid fragments - such as TCP with Path-MTU discovery
- Block ICMPv6 "Packet Too Big" (PTB) error messages that notify MTUs should be less than 1280 bytes
UDP-based protocols may rely on data fragmentation, so traffic-blocking data fragments are generally not recommended when using such protocols. Other protocols (such as TCP) can completely avoid using data fragments through mechanisms like Path-MTU discovery.
When ICMPv6 "PTB" error messages declare an MTU smaller than 1280 bytes, fragmentation may be triggered. Therefore, if IPv6 fragments are discarded but ICMPv6 "PTB" error messages resulting in an MTU smaller than 1280 bytes are not discarded, attackers may exploit such ICMPv6 error messages to trigger data fragmentation, causing resulting fragments to be discarded and leading to a denial of service (DoS) condition.
In the revised IPv6 specification [RFC8200], IPv6 fragments that generate responsive ICMPv6 PTB messages are no longer supported, so eventually, all implementations will eliminate this feature and related vulnerabilities. However, you might be using legacy facilities that still exhibit vulnerable behavior.
Q20: Should users remove packets containing IPv6 extension headers?
Answer: Users are advised to flexibly set filtering policies for packets containing IPv6 extension headers based on the enforcement location within the network.
If the filtering policy is enforced on transit routers, use a blacklist approach for filtering within the possible range, avoiding packet removal as much as possible; if the filtering policy is enforced on enterprise networks, users would want to allow only the desired traffic, so a whitelist approach should be used.
[IPv6-EHS-f] contains recommendations for filtering IPv6 packets, including extension headers on transit routers. Additionally, it includes security assessments of all standardized IPv6 extension headers and options, as well as an analysis of any potential interoperability issues arising from filtering such packets.
Q21: How should users evaluate the use of extension headers to bypass security controls on networks and devices?
Answer: Most IPv6 security toolkits provide support for arbitrary IPv6 extension header attack packets. For example, [SI6-RA6] explains the use of extension headers and router advertisement packets.
Q22: What packet filtering policies should be set for dual-stack networks?
Answer: IPv6 protocol security policies should match IPv4 protocol security policies, but due to the current lack of experience in setting IPv6 protocol policies, there are many vulnerabilities when enterprises set IPv6 protocol security policies.
Q23: How should IPv6 firewalls be configured for networks using temporary and stable addresses?
Answer: Configuration should allow connections to be initiated from any address but only allow incoming connections from stable addresses. Thus, addresses exposed due to client-like activities (such as web browsing) will not be usable for external systems to connect back to internal nodes or for address scanning to internal nodes.
Q24: How will temporary addresses affect users' ACLs?
Answer: Temporary addresses change over time, so specifying nodes using temporary addresses as a single IPv6 address or a set of addresses will usually fail.
To implement these ACLs, you can choose the following:
- Specify ACLs based on each prefix (e.g., /64)
- Disable temporary addresses on affected nodes
- Execute ACLs on stable addresses and configure nodes so that stable addresses are more suitable for accessing services/applications described in the ACL
Q25: What new challenges does the IPv6 network environment bring to enterprise security measures?
Answer: In the IPv6 network environment, the IP address space is almost infinite, and the pool of IP resources available to attackers will also expand indefinitely, with a surge in network data. At the same time, with attackers' widespread use of large-scale proxy IP pools, especially per-second dialing IPs, IP addresses are no longer trustworthy, leading to a rapid increase in false positives and missed detections for many traditional security solutions. Traditional security policies based on the IP address dimension can no longer meet the protection needs under the new trend.
How to Configure IPv6 in the EdgeOne Console?
In Tencent EdgeOne you can configure IPv6 settings for individual domains through Domain Management. Here, you'll find three configuration options, with the default being the Follow site configuration.
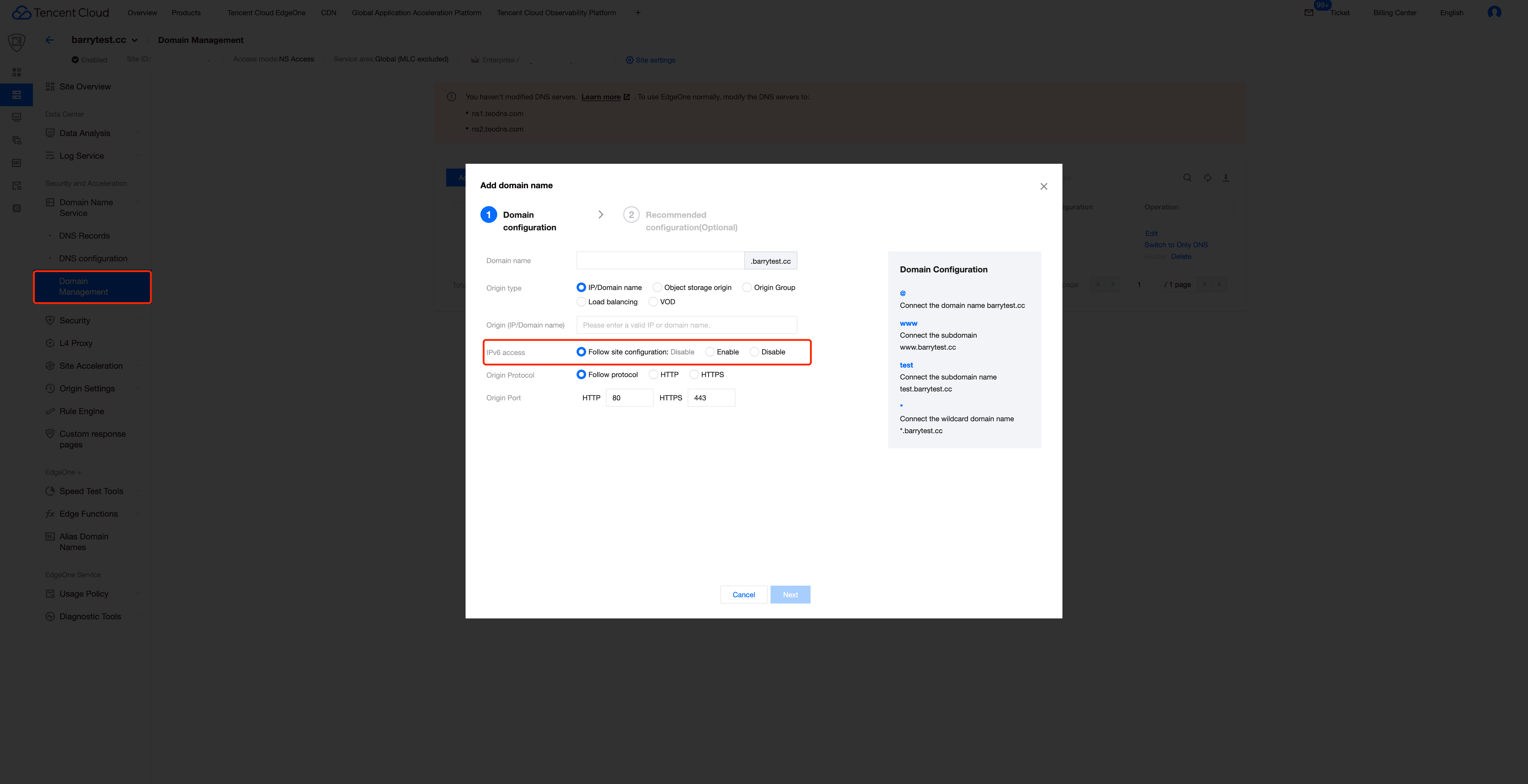
Let's explore how to implement global domain acceleration configurations in Tencent EdgeOne. Navigate to the Site Acceleration's Network Optimization module, where you'll discover a wide range of powerful acceleration features. By using the IPv6 Access Switch, you can enable acceleration for all domains under the site with the Follow site configuration. IPv6 configuration with just one click. Additionally, you're encouraged to utilize the Rule Engines and Security Protection to configure more robust and feature-rich functionalities and security protections for your domains.
You can also learn more about the usage and features of the Tencent EdgeOne Rule Engine by reading this article. If you are interested in experiencing these benefits firsthand, feel free to contact us to learn more about Tencent EdgeOne and its features. You can also click here to get started free and experience its benefits firsthand.

