Securing Your API Gateway: Comprehensive Protection Strategies for Modern Applications

In today's interconnected digital landscape, API gateways have emerged as pivotal components within modern software architectures. They serve as the central entry points for all API traffic, managing, routing, and mediating requests between clients and backend services. As businesses increasingly rely on APIs to facilitate data exchange, enable microservices communication, and power mobile and web applications, the security of API gateways has become paramount. A compromised API gateway can expose sensitive data, disrupt services, and compromise the entire application ecosystem. This article explores the critical aspects of API gateway security, offering actionable strategies and best practices to fortify your defenses and protect your valuable API infrastructure.
What is an API Gateway?
An API Gateway is a management tool that serves as an intermediary between API clients and backend services. It acts as a reverse proxy, accepting all API calls from clients and routing them to the appropriate backend services, while also handling various cross-cutting concerns such as authentication, rate limiting, traffic management, and security.
Key Functions of an API Gateway
- Request Routing: Directs incoming API requests to the correct backend services based on defined rules.
- Authentication and Authorization: Implements access control policies to secure APIs, using various mechanisms like OAuth 2.0, JSON web tokens, and API keys.
- Traffic Management: Manages traffic through rate limiting, request throttling, and load balancing to protect backend services from overload.
- Caching: Stores frequently accessed data to reduce latency and improve performance.
- Protocol Mediation and Transformation: Translates between different API protocols (e.g., SOAP, REST, GraphQL) to provide a consistent interface for clients.
- Analytics and Monitoring: Collects and analyzes API usage and performance data to support informed decision-making.
Benefits of Using an API Gateway
- Simplified Client Experience: Provides a single entry point for all API requests, abstracting the complexity of backend services.
- Enhanced Security: Centralizes security policies and protects backend services from unauthorized access and cyber threats.
- Improved Performance: Optimizes traffic routing and reduces latency through caching and efficient load balancing.
- Centralized Management: Allows for consistent application of policies across all APIs, making management and updates more efficient.
API Gateways are particularly valuable in microservices architectures, where they help manage communication between clients and multiple backend services, reducing complexity and improving overall system reliability. They are also commonly used in cloud environments to provide secure access to services and leverage cloud-native features like auto-scaling and monitoring.
Understanding API Gateway Security
API Gateway Security refers to the comprehensive set of measures, protocols, and practices implemented to protect API (Application Programming Interface) gateways from unauthorized access, misuse, and various cyber threats.
Core Components of API Gateway Security
API Gateway Security encompasses multiple layers of protection:
1. Authentication and Authorization
- Verifying the identity of API consumers (authentication)
- Determining what actions authenticated users can perform (authorization)
- Implementing standards like OAuth 2.0, JWT, API keys, or OpenID Connect
2. Traffic Management
- Rate limiting to prevent abuse and DDoS attacks
- Request throttling based on consumer identity
- Quota enforcement for API usage
3. Threat Protection
- Input validation to prevent injection attacks
- Protection against common API vulnerabilities (OWASP API Security Top 10)
- Bot detection and mitigation
- DDoS protection mechanisms
- Transport Layer Security (TLS/SSL) encryption
- Payload encryption for sensitive data
- Data masking and filtering capabilities
- Privacy controls for regulatory compliance
5. Monitoring and Analytics
- Real-time threat detection
- Anomaly detection for unusual traffic patterns
- Comprehensive logging and auditing
- Security incident alerting
Importance of API Gateway Security
API gateway security is critical because:
- APIs expose valuable business data and functionality
- They are increasingly targeted by attackers due to their growing prevalence
- A single compromise can affect multiple applications and services
- APIs often handle sensitive data subject to regulatory requirements
- Modern architectures (microservices, serverless) rely heavily on API communication
Properly secured API gateways not only protect organizations from data breaches and service disruptions but also enable them to confidently expose their digital services to partners, customers, and developers in a controlled, monitored manner.
Fundamental Security Requirements for API Gateways
Security by Design Principles
Securing API gateways must begin with fundamental security-by-design principles. This approach integrates security considerations throughout the API lifecycle rather than applying security as an afterthought. Key aspects include:
- Threat modeling during the design phase
- Least privilege access control by default
- Defense-in-depth strategies
- Continuous security testing and validation
API Gateway Security vs. Traditional Web Security
API security differs significantly from traditional web application security in several important ways:
| Traditional Web Security | API Gateway Security |
| Focus on user interfaces | Focus on machine-to-machine communication |
| Session-based authentication | Token-based authentication |
| CSRF protection | API key management |
| Browser security controls | Protocol-level security |
Regulatory Compliance Considerations
API implementations must adhere to various regulatory frameworks depending on industry and geography:
- GDPR: Requires strict data protection measures for European users
- PCI-DSS: Mandates secure handling of payment card information
- HIPAA: Enforces privacy standards for healthcare data
- CCPA/CPRA: California's privacy regulations affecting data handling
Authentication & Authorization Strategies
OAuth 2.0 and OpenID Connect Implementation
OAuth 2.0 remains the industry standard for API authorization, with OpenID Connect extending its capabilities for authentication:
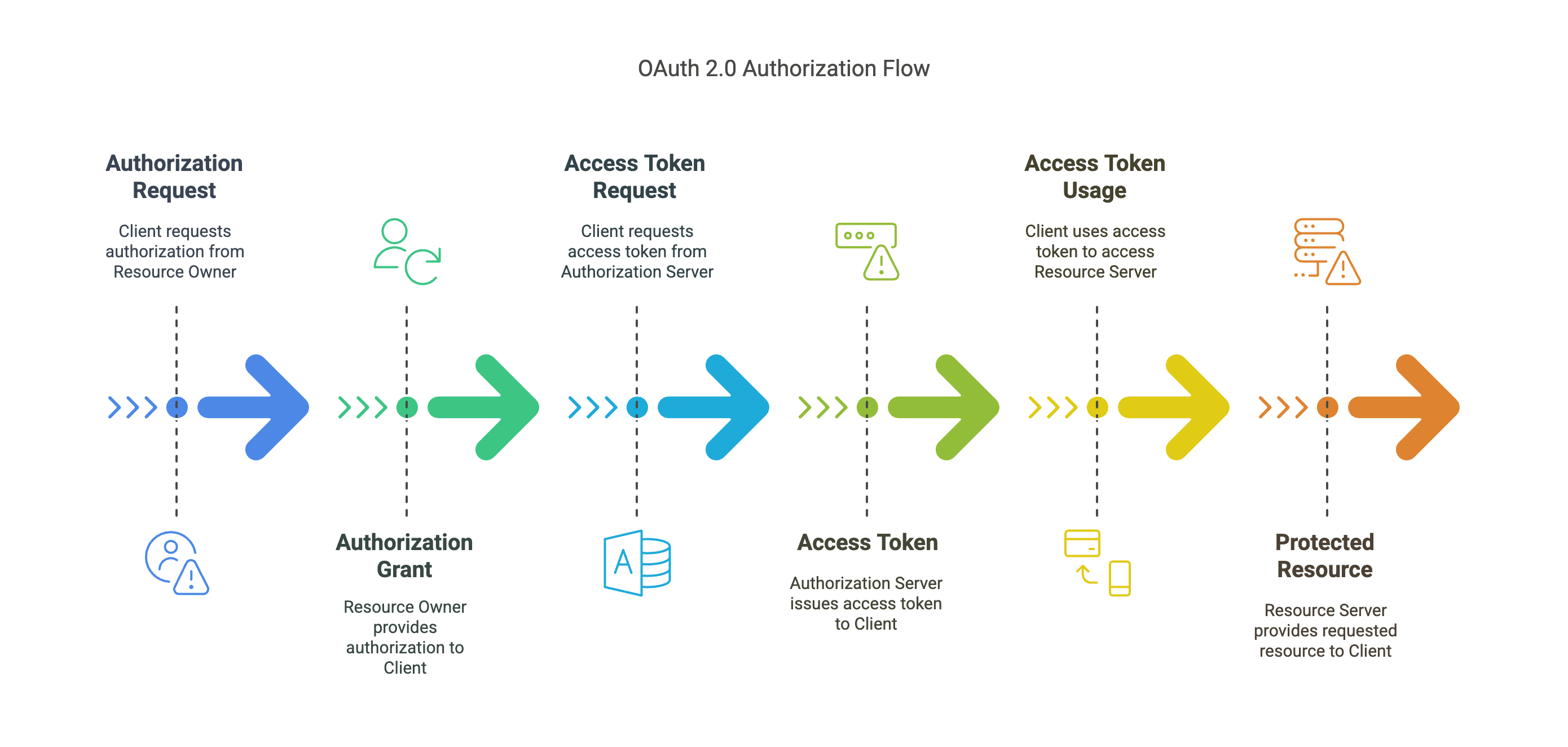
Best practices for implementation include:
- Implementing proper scope limitations
- Using short-lived access tokens with refresh capabilities
- Securing token storage and transmission
- Validating all token parameters
API Key Management Best Practices
While simpler than OAuth, API keys require careful management:
- Regular key rotation policies
- Granular access control per key
- Monitoring for unusual usage patterns
- Secure distribution and storage mechanisms
JWT (JSON Web Tokens) Security Considerations
JWT implementation requires specific security attention:
- Properly validating signature algorithms (avoid "none" algorithm)
- Setting appropriate expiration times
- Implementing proper key management for signing
- Being cautious with sensitive data in payload
Multi-factor Authentication for APIs
Even for machine-to-machine communication, additional factors can enhance security:
- Certificate-based authentication alongside tokens
- IP-based restrictions as a second factor
- Hardware security module (HSM) integration
- Time-based one-time passwords for critical operations
Traffic Management & Threat Protection
Rate Limiting and Quota Management
Effective rate limiting protects APIs from abuse and denial of service:
- Request rate limits per consumer
- Concurrent connection limitations
- Resource-specific quotas (e.g., database operations)
- Graduated response mechanisms (warning, throttling, blocking)
DDoS Protection Strategies
API gateways should incorporate multi-layered DDoS protection:
- Layer 3/4 traffic filtering
- Layer 7 application-aware protection
- Traffic anomaly detection
- Integration with cloud-based DDoS protection services
Bot Detection and Mitigation
Sophisticated bot detection helps identify malicious automated traffic:
- Behavioral analytics to identify bot patterns
- CAPTCHA challenges for suspicious behavior
- Device fingerprinting
- Machine learning-based detection systems
Input Validation and Sanitization
Preventing injection attacks requires robust validation:
- Schema validation for all requests
- Content type enforcement
- Parameter type checking and sanitization
- JSON/XML structural validation
Data Protection & Encryption
Transport Layer Security (TLS) Best Practices
API communications must be secured with proper TLS implementation:
- Enforce TLS 1.2 or 1.3 minimum
- Implement perfect forward secrecy
- Regularly audit cipher suites
- Deploy proper certificate management
End-to-End Encryption Strategies
Beyond transport encryption, consider end-to-end protection:
- Field-level encryption for sensitive data
- Client-side encryption for high-security requirements
- Homomorphic encryption techniques for specialized use cases
- Key management separation
Sensitive Data Handling
Proper handling of sensitive data reduces exposure risk:
- Data classification and tagging mechanisms
- Automatic PII detection
- Response filtering for sensitive fields
- Secure logging practices that mask sensitive data
Implementing Zero Trust Architecture for APIs
Principle of Least Privilege
Zero Trust begins with minimizing access rights:
- Granular permission models
- Role-based access control (RBAC)
- Just-in-time access provisioning
- Regular access reviews and revocation
Continuous Verification Methods
Trust must be continuously validated:
- Real-time token validation
- Continuous context assessment
- Step-up authentication for sensitive operations
- Behavior-based anomaly detection
Micro-segmentation Strategies
API infrastructure should be segmented to limit lateral movement:
- Service mesh security controls
- Network policy enforcement
- API gateway zoning
- Internal vs. external gateway separation
API Gateway Security Monitoring
Logging and Auditing Best Practices
Comprehensive logging enables security monitoring and forensics:
- Request/response metadata logging
- Authentication and authorization events
- Rate limiting and security policy violations
- Infrastructure and configuration changes
Real-time Threat Detection
Proactive security requires real-time monitoring:
- Pattern-based attack recognition
- Baseline deviation alerts
- Correlation of security events across systems
- Integration with threat intelligence feeds
Security Information and Event Management (SIEM) Integration
API security data should feed into broader security monitoring:
- Standardized log formats
- Real-time log streaming
- Correlation with enterprise security events
- Automated incident response workflows
Secure API Development Lifecycle
Security Testing for APIs
API security testing should occur throughout the development lifecycle:
- Static Analysis Security Testing (SAST) for code vulnerabilities
- Dynamic Analysis Security Testing (DAST) for runtime issues
- Interactive Application Security Testing (IAST) for comprehensive coverage
- Fuzzing techniques to identify unexpected behavior
CI/CD Pipeline Security Integration
Security should be automated within deployment pipelines:
- Pre-commit hooks for basic security checks
- Automated security scanning in build processes
- Policy-as-code implementation
- Security gates before production deployment
API Versioning and Deprecation Security
Secure versioning practices help manage the API lifecycle:
- Clear deprecation timelines and notifications
- Security patch backporting policies
- Graceful security-driven retirement
- Maintaining security support for legacy versions
Case Studies: API Gateway Security in Action
Financial Services Implementation Examples
A major international bank implemented a multi-layered API security approach:
- Mutual TLS for all partner connections
- Real-time fraud detection via machine learning
- Hardware-based encryption for transaction data
- Regulatory-compliant audit trails
- Result: 99.9% reduction in unauthorized access attempts
Healthcare API Security Solutions
A healthcare provider network secured patient data exchanges:
- FHIR-compliant API security controls
- Consent management via OAuth
- De-identification services at the gateway
- Specialized healthcare DDoS protection
- Result: Full HIPAA compliance with zero data breaches
E-commerce API Protection Strategies
A global e-commerce platform secured its marketplace APIs:
- Behavioral analysis for transaction risk
- Rate limiting based on business context
- Automated credential stuffing protection
- Seasonal scaling for security controls
- Result: 60% reduction in fraud attempts during peak seasons
Future Trends in API Gateway Security
AI/ML in API Security
Artificial intelligence is transforming API security:
- Anomaly detection via unsupervised learning
- Predictive threat modeling
- Automated response optimization
- Natural language processing for API abuse detection
Quantum-Safe API Authentication
Preparing for quantum computing threats:
- Post-quantum cryptography algorithms
- Hybrid classical/quantum-resistant approaches
- Key exchange hardening
- Crypto-agility implementation
Emerging Standards and Protocols
The security landscape continues to evolve:
- gRPC security best practices
- GraphQL-specific protections
- WebAuthn for API authentication
- FIDO2 integration with API access
API Security for IoT and Edge Computing
Extending API security to the network edge:
- Lightweight security protocols for constrained devices
- Edge-based threat detection
- Device attestation for API access
- Disconnected operation security
How to Protect API Security with EdgeOne?
Tencent EdgeOne combines edge computing, content delivery, and security capabilities into an integrated platform specifically designed to protect web applications and APIs. By positioning security controls at the network edge, organizations can identify and mitigate threats before they reach the origin infrastructure.
1. Advanced DDoS Protection
EdgeOne's distributed architecture provides robust protection against volumetric and application-layer DDoS attacks targeting APIs:
- Multi-terabit mitigation capacity across global points of presence
- Protocol-level protection against SYN floods and other attack vectors
- Specialized detection of API-focused DDoS attacks
- Automatic traffic scrubbing without impacting legitimate API requests
2. API-Aware Web Application Firewall
Unlike traditional WAFs, EdgeOne's security engine is designed with API-specific protections:
- Specialized rule sets aligned with the OWASP API Security Top 10
- Deep inspection of API payloads including JSON and XML content
- Context-aware protection against injection and parameter tampering
- Custom rule capabilities for business logic vulnerabilities
3. Intelligent Bot Management
Controlling automated access to APIs is critical for security:
- Machine learning-powered bot classification system
- Behavioral analysis to identify malicious automation
- Protection against credential stuffing and account takeover attempts
- Customizable responses to different bot categories
4. Granular Rate Limiting
Prevent abuse while maintaining availability:
- Configurable rate limits based on multiple client attributes
- Progressive rate limiting that escalates restrictions for suspicious behavior
- Separate thresholds for different API endpoints based on sensitivity
- Custom response codes and headers for rate-limited requests
As part of a comprehensive API security strategy, Tencent EdgeOne helps organizations implement the defense-in-depth approach recommended throughout this article, protecting the network edge to the application core.
Sign up and start a free trial with us now!
Conclusion
Securing your API gateway is not merely a technical task but a strategic imperative for protecting your digital assets and maintaining business continuity. By implementing robust authentication and authorization mechanisms, ensuring data encryption, managing traffic effectively, monitoring activities diligently, and adopting advanced security measures, organizations can significantly enhance their API gateway security. Learning from real-world examples and staying informed about future trends will further strengthen your security posture. Remember that API gateway security is an ongoing journey requiring continuous learning, adaptation, and improvement to stay ahead of evolving threats and protect your valuable API ecosystem.

