How to Protect Web Applications: A Practical Security Guide

Ten years ago, web application security was an afterthought for most development teams. Today, it's a business-critical necessity. The headlines tell the story: major brands suffering embarrassing breaches, customer data exposed, and millions spent on recovery—often because of basic security oversights that could have been easily addressed.
Development teams frequently rush applications to production only to discover vulnerabilities the hard way. The reality is stark: web applications are under constant attack. Every public-facing app—whether a simple contact form or a complex e-commerce platform—faces dozens or even hundreds of attack attempts daily. The question isn't if attackers will target your application, but when and how persistent they'll be.
Web applications are particularly vulnerable because they're accessible to anyone with an internet connection and often handle sensitive data like payment details or personal information. Unlike internal systems hidden behind corporate firewalls, web apps stand exposed on the frontlines. As attacks grow more sophisticated, simply following last year's security practices isn't enough. For a deeper understanding of exactly what security measures your application needs, check out our detailed guide on web application security requirements.
Understanding Web Application Vulnerabilities
Before implementing protections, understanding what you're defending against is crucial. Web applications typically face several common attack vectors:
- Injection attacks (SQL, NoSQL, OS command injections)
- Cross-site scripting (XSS)
- Broken authentication and session management
- Security misconfigurations
- Cross-site request forgery (CSRF)
- Using components with known vulnerabilities
These aren't theoretical threats—they're actively exploited daily against organizations of all sizes. For a detailed breakdown of these vulnerabilities and how they can impact your application, see our in-depth guide to web application vulnerabilities.
Essential Measures to Protect Web Applications
1. Implement Strong Authentication
Authentication verifies that users are who they claim to be—the first line of defense for any application. Simple password systems no longer provide adequate protection in today's threat landscape. Strong authentication incorporates multiple verification factors and secure session handling. Best practices now include enforcing complex password policies, implementing account lockouts after failed attempts, and requiring periodic password changes.
Multi-factor authentication has moved from a luxury to a necessity, especially for applications handling sensitive data. By requiring something the user knows (password) plus something they have (like a mobile device) or something they are (biometric verification), the security barrier rises significantly.
Example: A financial services application implemented multi-factor authentication requiring both a password and a time-based verification code. During a credential stuffing attack where attackers used passwords leaked from another site, the second authentication factor prevented account takeovers. Even with valid passwords, attackers couldn't generate the required verification codes, protecting customer accounts.
2. Validate All Input
User input is the primary gateway for attacks against web applications. Every piece of data entering an application—whether from forms, URLs, cookies, or API calls—should be considered potentially malicious. Proper validation means checking that input matches expected formats, falls within acceptable ranges, and contains only permitted characters.
Client-side validation offers convenience, but attackers can easily bypass it. Server-side validation remains essential as the ultimate gatekeeper. The most secure approach uses whitelist validation (specifying exactly what's allowed) rather than blacklist validation (trying to block known bad inputs), as new attack patterns emerge constantly.
Example: An e-commerce platform experienced SQL injection attacks through its product search feature. After implementing strict server-side input validation that only accepted alphanumeric characters and specific symbols, the attacks stopped. The system now sanitizes all user input and logs suspicious patterns, reducing vulnerabilities while maintaining a streamlined user experience.
3. Use Parameterized Queries
SQL injection attacks remain surprisingly common despite being well-understood. These attacks succeed when applications build database queries by concatenating user input directly into SQL command strings. Parameterized queries solve this problem by separating SQL code from user-supplied data.
This separation means the database always treats user input as data, never as executable code. Most modern programming frameworks and libraries support parameterized queries, making implementation straightforward. The performance impact is negligible, but the security benefit is enormous.
Example: A university portal storing student records was vulnerable to SQL injection through its search functionality. By switching to parameterized queries, the application began treating student ID inputs as data parameters rather than parts of the SQL command. When an attempted attack included malicious SQL fragments, these were treated as literal search text rather than commands, protecting the database integrity while maintaining full functionality.
4. Implement Proper Session Management
Web applications use sessions to maintain state between requests, but poor session management creates serious security risks. Secure session handling requires attention to several key elements: generating cryptographically strong random session identifiers, setting appropriate cookie security attributes, implementing both idle and absolute timeouts, and properly invalidating sessions after logouts or password changes.
Session fixation and session hijacking attacks succeed when these elements are overlooked. Modern frameworks offer secure session management tools, but configuration details matter significantly.
Example: An online banking application implemented secure session handling with 15-minute idle timeouts and forced re-authentication for sensitive transactions. When a customer logged in at a public computer but forgot to log out, the session automatically expired shortly after they walked away. Later that day, someone else using the same computer couldn't access the account, preventing unauthorized access to financial information.
5. Implement Content Security Policy
Content Security Policy (CSP) acts like a security guard for web browsers, controlling which resources they can load when displaying your site. By specifying approved sources for scripts, styles, images, and other content, CSP prevents browsers from running malicious code even if attackers find a way to inject it into your pages.
While implementing a strong CSP requires careful planning—especially for complex applications—the protection it provides against XSS attacks justifies the effort. Start with a reporting-only policy to identify issues before enforcement, then gradually tighten restrictions.
Example: A news website implemented a strict CSP that only allowed scripts to load from specific trusted domains. When a malicious actor attempted to inject a script tag through a comment form, the browser refused to execute it because the script violated the policy. This prevented the attack despite the initial XSS vulnerability, giving developers time to fix the underlying input validation issue.
6. Enable HTTPS Everywhere
HTTPS encrypts data traveling between users' browsers and web servers, preventing eavesdropping, data tampering, and credential theft. With free certificate authorities like Let's Encrypt and minimal performance overhead, there's no excuse for transmitting sensitive data unencrypted.
Beyond basic encryption, proper HTTPS implementation includes secure configuration, HTTP Strict Transport Security (HSTS), and automatic HTTP-to-HTTPS redirection. These measures protect against downgrade attacks and ensure users always connect securely.
Example: A healthcare patient portal switched from HTTP to HTTPS for all pages—not just the login and payment screens. Later, when a patient accessed their records from a hotel network, someone attempting to intercept the connection could only see encrypted data. The HTTPS implementation protected sensitive medical information despite the compromised network environment.
7. Practice Least Privilege
The principle of least privilege means giving users and systems only the minimum access rights needed to perform their functions. This fundamental security concept limits what attackers can do even if they compromise credentials or exploit vulnerabilities.
Implementing least privilege requires careful role definition, regular permission audits, and designing systems where components operate with minimal required access. Though initially requiring more planning, this approach dramatically reduces breach impacts.
Example: An enterprise management system redesigned its access control using role-based permissions instead of universal admin rights. When an account was later compromised through a phishing attack, the attacker gained access only to specific reports rather than system-wide administrative functions. This limited the breach impact and provided time for the security team to detect unusual activity before critical systems were affected.
8. Keep Dependencies Updated
Modern web applications typically rely on dozens of third-party libraries and frameworks, each potentially introducing vulnerabilities. The severe vulnerability discovered in Next.js middleware implementation (CVE-2025-29927) in 2025 demonstrated this risk perfectly. This vulnerability allowed attackers to bypass authentication and route protection mechanisms by simply forging the x-middleware-subrequest header. Affecting all versions from 11.1.4 to 15.2.3—representing over 82% of production deployments—this single framework flaw exposed countless applications to potential compromise.
Regularly updating dependencies is essential but challenging. Establish a systematic process to track the versions used, monitor security advisories for those components, and quickly apply updates when vulnerabilities are discovered. Automated tools can help, but human oversight remains necessary for evaluating update risks.
Example: A retail website using an outdated e-commerce framework was compromised when attackers exploited a known vulnerability. After recovery, the company implemented automated dependency scanning that flagged vulnerable components during development. This system alerted developers to a critical vulnerability in a payment library shortly after disclosure, allowing them to update before attackers could exploit it.
9. Implement Security Headers
HTTP security headers tell browsers how to handle website content, adding defense layers against common attacks. They're easy to implement yet provide significant protection. Key security headers include Content-Security-Policy, X-Content-Type-Options, X-Frame-Options, and Strict-Transport-Security.
These headers prevent clickjacking, reduce XSS risks, block MIME-type sniffing, and enforce secure connections. Each addresses specific attack vectors, creating a more robust security posture when used together.
Example: A government services portal implemented comprehensive security headers including Content-Security-Policy and X-Frame-Options. When attackers later attempted to embed the portal within an invisible frame on a fraudulent site, the browser refused to display the government site within the malicious page, protecting users from an elaborate credential theft scheme.
10. Regular Security Testing
Security isn't a "set and forget" feature—it requires ongoing verification. Regular testing identifies vulnerabilities before attackers can exploit them, particularly as applications evolve with new features and updates.
A comprehensive testing strategy includes automated scanning with tools like OWASP ZAP, manual testing focused on business logic flaws, and possibly penetration testing for critical applications. The key is integrating security testing into development rather than treating it as an afterthought.
Example: A software-as-a-service provider integrated automated security scans into their development pipeline. When a developer unknowingly introduced a cross-site scripting vulnerability while implementing a new feature, the automated scan caught it before the code reached production. This prevented what could have become a significant security incident affecting thousands of customers.
Implementing a Defense-in-Depth Strategy for Web Applications
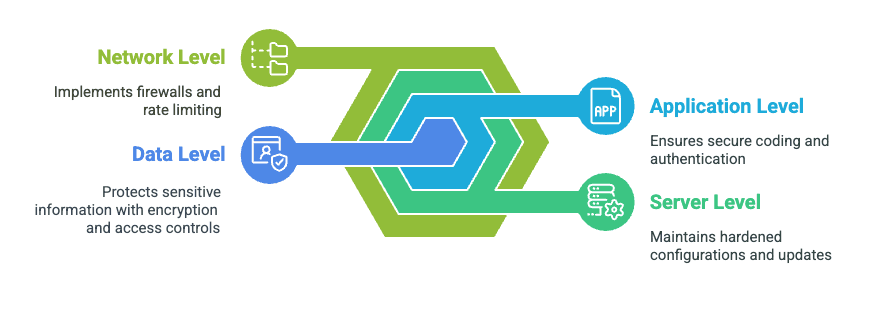
Individual security measures can fail—that's why defense-in-depth is essential. This approach implements multiple layers of protection so that if one fails, others still stand. Think of it as multiple security guards rather than just a single lock on the door.
Effective defense-in-depth for web applications requires security at several levels:
- Network level (firewalls, rate limiting)
- Server level (hardened configurations, updates)
- Application level (secure coding, authentication)
- Data level (encryption, access controls)
When these layers work together, even sophisticated attackers face significant challenges breaching your defenses.
Conclusion
Web application security isn't a one-and-done project but an ongoing process that evolves with the threat landscape. The measures outlined here provide a foundation that significantly reduces risk, but they must be adapted to your specific application's needs and continuously maintained.
The most successful approach starts by securing authentication and data handling components—the areas that typically present the highest risk. Then systematically work through implementing other protections based on your application's unique risk profile.
Remember that perfect security doesn't exist. The goal is raising the bar high enough that attacking your application becomes difficult and costly compared to easier targets. With thoughtful implementation of these security measures, that goal becomes achievable.
Try EdgeOne for Enhanced Web Application Protection
Looking for additional layers of protection for your web applications? EdgeOne provides comprehensive security including DDoS protection, web protection, and bot management without the complexity of traditional security solutions. Start your free trial today and see how EdgeOne can strengthen your web application security posture with minimal configuration effort.
FAQs
Q1: What is the most common web application vulnerability?
A1: Injection attacks (particularly SQL injection) and Cross-Site Scripting (XSS) remain among the most common vulnerabilities, allowing attackers to execute malicious code or commands through unsanitized inputs.
Q2: How often should I scan my web application for vulnerabilities?
A2: At minimum, scan after every significant code change or dependency update, but ideally implement continuous security scanning in your CI/CD pipeline for real-time protection.
Q3: Is a WAF (Web Application Firewall) enough to protect my application?
A3: No, while WAFs provide valuable protection against common attacks, they should be part of a comprehensive security strategy that includes secure coding practices and proper authentication.
Q4: How can I protect my web application APIs?
A4: Secure APIs by implementing strong authentication, rate limiting, input validation, and ensuring proper authorization checks for each API endpoint.
Q5: What's the first step I should take to improve my web application's security?
A5: Start with an inventory of your application components and a basic vulnerability scan to identify high-risk issues, then prioritize fixing authentication weaknesses and input validation problems.

