DoS vs DDoS Attacks: Understanding the Key Differences

When websites suddenly become unavailable or painfully slow, organizations often face either a Denial of Service (DoS) or its more powerful cousin, a Distributed Denial of Service (DDoS) attack. While both share the same goal—making online services inaccessible to legitimate users—they differ significantly in execution, scale, and the challenges they present to defenders.
Understanding these differences isn't just technical trivia; it directly impacts how organizations detect, respond to, and protect against these increasingly common threats. As businesses continue shifting critical operations online, the distinction between these attack types becomes increasingly relevant to organizations of all sizes.
What is a DoS Attack?
A Denial of Service (DoS) attack occurs when a malicious actor attempts to make a website or online service unavailable by flooding it with malformed or disruptive network traffic from a single source. Think of it as a single person repeatedly calling a business phone line—legitimate customers can't get through because the line is constantly busy with the attacker's calls. The business cannot serve customers because all resources are tied up handling these malicious calls.
Traditional DoS attacks exploit specific vulnerabilities in web servers, network equipment, or applications. For example, an attacker might send specially crafted packets designed to crash a web server, or repeatedly request resource-intensive pages to overwhelm server capacity. Common examples include:
- SYN floods: Sending connection requests without completing the connection process
- Ping floods: Overwhelming a target with ICMP echo request packets
- Application-layer attacks: Targeting specific resource-intensive website functions
While damaging, classic DoS attacks have significant limitations. They originate from a single IP address, making them relatively easy to block. Additionally, the attack's power is limited by the bandwidth and processing capability of the attacker's own connection.
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack shares the same fundamental goal as a DoS attack but employs a fundamentally different approach. Rather than attacking from a single source, DDoS attacks leverage networks of compromised computers and devices (known as botnets) to direct traffic from hundreds, thousands, or even millions of different sources simultaneously.
Extending our phone analogy: instead of one person calling repeatedly, DDoS resembles thousands of people from different phone numbers all calling at once. The business phone system becomes completely overwhelmed, unable to distinguish legitimate customer calls from the coordinated attack calls. The outcome is far more devastating and much harder to mitigate.
Modern DDoS attacks typically fall into three categories:
- Volumetric attacks: Overwhelming bandwidth with massive traffic volumes
- Protocol attacks: Exploiting weaknesses in network protocols to consume server resources
- Application layer attacks: Targeting specific website features with seemingly legitimate requests
These distributed attacks generate traffic volumes that dwarf what's possible from single sources, with major attacks easily overwhelming standard network defenses.
Key Differences Between DoS and DDoS
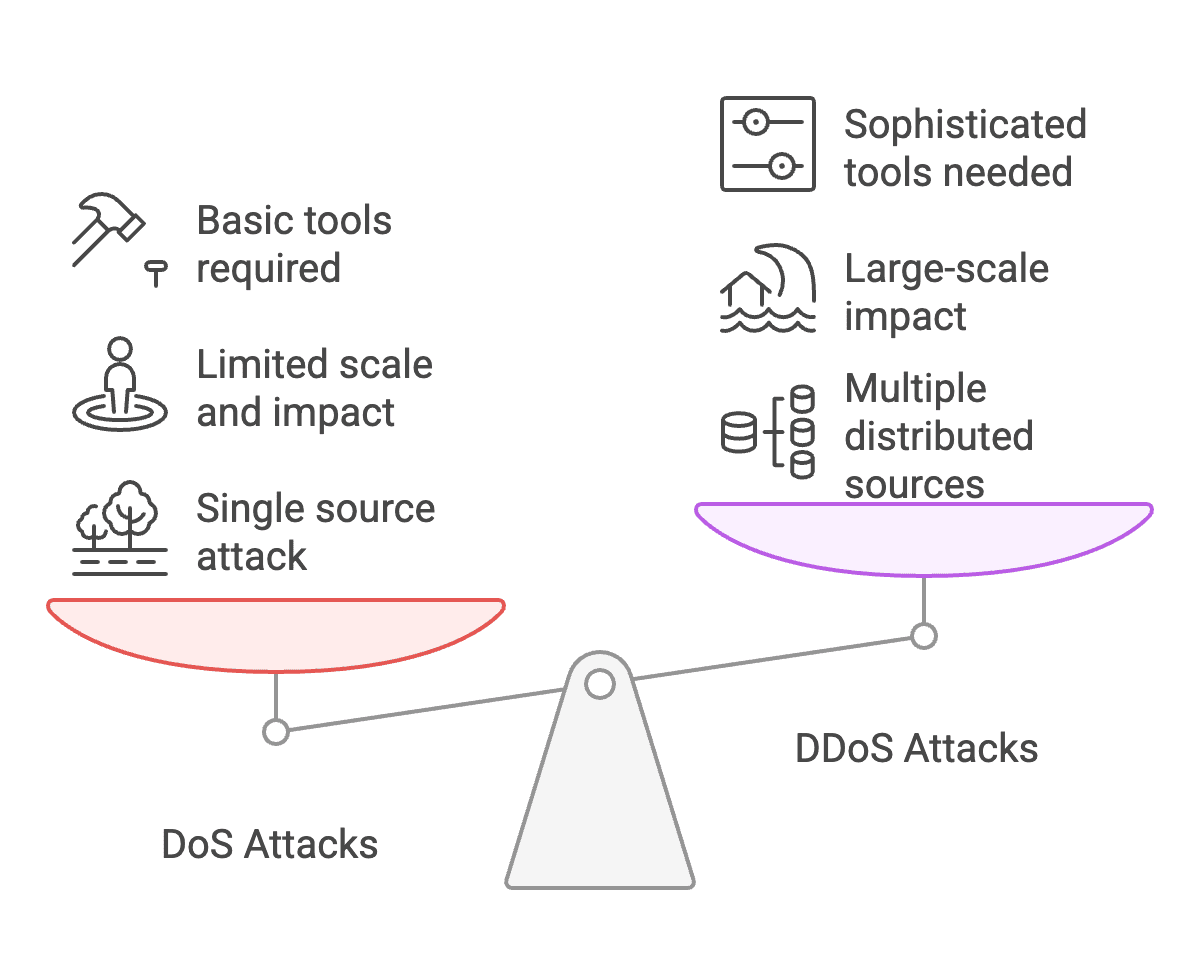
1. Attack Source
The most fundamental difference between these attack types lies in their source:
- DoS attacks: Traffic comes from a single origin (one computer/IP address)
- DDoS attacks: Traffic originates from multiple distributed sources (potentially thousands or millions of unique IP addresses)
This distinction dramatically affects how the attacks are executed, detected, and mitigated. While a DoS attack from a single source can be blocked with a simple firewall rule, DDoS traffic coming from thousands of different legitimate-looking sources requires far more sophisticated filtering.
2. Scale and Impact
The distributed nature of DDoS attacks creates significant differences in scale and effectiveness:
- DoS attacks: Limited by the attacker's own bandwidth and processing power
- DDoS attacks: Can aggregate the bandwidth and processing capability of thousands of compromised devices
This difference in scale means DoS attacks rarely impact organizations with proper hosting infrastructure, while DDoS attacks can potentially overwhelm even well-resourced networks. A single server might easily handle one connection attempting to flood it with requests, but when thousands of connections do the same simultaneously, even robust systems can fail.
3. Complexity and Sophistication
The technical complexity required to execute each attack type varies significantly:
- DoS attacks: Can be executed with relatively basic tools and limited technical knowledge
- DDoS attacks: Require controlling a botnet or purchasing attack services, representing a higher level of criminal sophistication
This complexity gap has narrowed somewhat as "DDoS-as-a-service" offerings have democratized access to attack capabilities, but operating a botnet still requires more technical sophistication than executing basic DoS attacks. Criminal marketplaces have unfortunately made it possible for even technically unsophisticated attackers to rent botnet capacity for DDoS attacks.
4. Detection and Mitigation Challenges
Perhaps the most important difference involves how organizations identify and respond to these attacks:
- DoS attacks: Relatively simple to block by filtering traffic from the attacking IP address
- DDoS attacks: Much harder to mitigate due to traffic coming from numerous legitimate-looking sources
This distinction explains why DDoS attacks remain effective against even well-prepared targets. When attack traffic is mixed with legitimate traffic from thousands of sources, distinguishing between them becomes extremely challenging. Network defenders must analyze traffic patterns and behaviors rather than simply blocking individual sources.
5. Attribution and Tracing
Identifying the actual perpetrators also differs significantly between these attack types:
- DoS attacks: Easier to trace back to the original attacker (though still challenging)
- DDoS attacks: Multiple layers of obfuscation make attribution significantly more difficult
The distributed nature of DDoS attacks provides attackers with natural anonymity, as compromised devices rather than the attacker's own systems generate the malicious traffic. Forensic investigation might reveal the compromised devices but rarely leads back to the controlling entity behind the attack.
Real-World Impact of DoS and DDoS Attacks
Both attack types can create significant business disruptions, though their typical targets and impacts often differ:
DoS Attacks:
- More commonly target smaller organizations without enterprise-grade protection
- Often opportunistic or executed by less sophisticated attackers
- May serve as a testing ground before larger DDoS campaigns
- Can still cause significant damage to inadequately protected targets
DDoS Attacks:
- Frequently target higher-profile organizations with better security resources
- Often executed by organized threat actors with specific objectives
- Increasingly used alongside ransom demands or as distractions for other attacks
- Can create widespread service outages even for major online platforms
The business consequences extend beyond immediate availability issues. Customer trust erodes quickly when services become unreliable, and regulatory concerns may arise if attacks lead to broader security issues or affect critical services.
How to Defend Against DoS and DDoS Attacks?
Defending against these attacks requires different approaches based on the attack type:
DoS Protection:
- Configure firewalls to block suspicious traffic patterns
- Implement rate limiting for incoming requests
- Patch systems regularly to fix vulnerabilities exploited in DoS attacks
- Monitor traffic patterns for early detection
DDoS Protection:
- Use specialized DDoS protection services that can absorb attack traffic
- Implement traffic scrubbing to filter malicious requests
- Distribute resources across multiple locations to increase resilience
- Develop incident response plans specifically for DDoS scenarios
Organizations with limited security resources should consider cloud-based protection services that can detect and mitigate attacks before they reach internal networks. These services provide specialized expertise and the bandwidth capacity to absorb even large-scale attacks.
Conclusion
While DoS and DDoS attacks share the same disruptive goal, they represent distinctly different threats requiring specific defensive strategies. The distributed nature of DDoS attacks makes them significantly more dangerous to organizational operations and more challenging to mitigate effectively.
EdgeOne DDoS protection service addresses these challenges through a multi-layered defense system designed to counter both traditional DoS and sophisticated DDoS attacks. By leveraging a global network of scrubbing centers, EdgeOne can absorb the massive traffic volumes associated with DDoS attacks while its intelligent traffic analysis distinguishes between legitimate users and attack traffic. The system provides protection against all attack types discussed in this article—from simple SYN floods to complex application-layer attacks.
Ready to protect your online services against both DoS and DDoS threats? EdgeOne offers a straightforward deployment process that requires no hardware installation and minimal configuration changes. Experience enterprise-grade protection through our free trial, which allows you to evaluate the service's effectiveness against real-world attacks without commitment. Contact our security specialists today to discuss your specific protection needs or visit our website to learn more about how EdgeOne creates a shield between your critical infrastructure and the evolving landscape of denial of service attacks.
Frequently Asked Questions
Q1: Can a DoS attack come from multiple computers operated by the same attacker?
A1: Even if an attacker uses several of their own computers, it's still considered a DoS attack; DDoS specifically refers to attacks using distributed networks of compromised devices typically controlled through malware or botnets.
Q2: Which is more common today, DoS or DDoS attacks?
A2: DDoS attacks have become significantly more common as attack tools and botnets have become more accessible through criminal marketplaces, while basic DoS attacks are now primarily seen against smaller, unprotected targets.
Q3: Can home users be targeted by DDoS attacks?
A3: Yes, even home internet connections can be targeted, particularly gamers, streamers, or individuals who have attracted negative attention online; these attacks typically overwhelm the victim's internet connection, making it unusable until the attack stops.
Q4: How long do these attacks typically last?
A4: DoS attacks often last minutes to hours as they're easier to block, while DDoS attacks can persist for days or even weeks with attack patterns shifting to avoid mitigation, particularly when backed by persistent threat actors.
Q5: Is it possible to completely prevent these attacks?
A5: Complete prevention isn't realistic given the evolving nature of these threats, but organizations can implement robust detection and mitigation strategies that minimize impact and recovery time, essentially making attacks a manageable disruption rather than a catastrophe.

