DNS was born in the early days of the Internet, when security threats were relatively few and DNS traffic could pass through network firewalls without hindrance. However, as the number of Internet users and networks has grown, so has the appeal of DNS among malicious actors. It has become an attack method that can be exploited to threaten network security and induce users to disclose personal information. DNS security involves all protective measures related to the DNS protocol. An effective DNS security strategy includes many overlapping defenses, including establishing redundant DNS servers, DNS filtering, and strict DNS logging.
What are the common DNS attacks?
1. DDoS attack
Distributed Denial of Service (DDoS) attack refers to an attacker remotely controlling a large number of zombie hosts through the network to send a large number of attack requests to one or more targets, blocking the network bandwidth of the target server or exhausting the system resources of the target server. Overload or crash the DNS server, causing it to be unable to respond to normal service requests, and even cause data leakage.
2. DNS cache poisoning
In this type of attack, attackers exploit vulnerabilities in the DNS server to take over the server. During the 'cache poisoning' process, attackers inject malicious data into the cache system of the DNS resolver, thereby redirecting users to a website specified by the attacker, where personal information or other data is often stolen.
If cybercriminals successfully gain control of a DNS server, they can manipulate the information in the cache (DNS poisoning). This poisoning code is commonly found in URLs sent via spam or phishing emails. Since DNS servers can access the caches of other DNS servers, this attack method has significant propagation properties. The main risk of DNS cache poisoning is data theft.
3. DNS tunnel
DNS tunneling attacks begin when a user downloads malware to a computer, or when a hacker successfully exploits a vulnerability in a computer system and installs a malicious attack payload. Typically, attackers want to retain control of the device to be able to run commands or transfer data outside of that environment. To do this, an attacker would need to establish a tunnel, a method of sending commands and receiving data from a compromised system while evading detection by network perimeter security measures.
DNS traffic can often pass freely through perimeter security measures such as firewalls, making it ideal for this type of exploit. In order to create a tunnel, an attacker would need to create and register a domain name, as well as configure an authoritative name server controlled by the attacker. When malware on a victim's device issues a DNS query to the attacker's server, the server responds with a DNS packet containing data and commands specific to the infected device. This allows the attacker to continuously communicate with the infected device without triggering any alerts. Additionally, an attacker could send the data encoded in the query to a malicious authoritative name server.
4. DNS hijacking
DNS hijacking is an attack technique that can be implemented in a variety of ways, including DNS cache hijacking, DNS server hijacking, router hijacking, and malware hijacking. Attackers redirect users' domain name resolution requests to malicious IP addresses or websites by tampering with data in the DNS resolution process. This kind of attack can cause users to be redirected to malicious websites to conduct malicious activities such as phishing, malware spreading, and information theft.
Measures and techniques to prevent DNS attacks
- DNS resolution service provider: Choose a trustworthy DNS resolution service provider and ensure that it has good security and protection measures. These service providers usually adopt various techniques to protect the security of the DNS resolution process.
- Configuring DNSSEC: DNSSEC is a security extension protocol that ensures the integrity and authenticity of DNS responses through digital signatures and verification mechanisms, preventing DNS hijacking and cache poisoning attacks.
- Detection and Logging: Implement DNS traffic monitoring and logging to promptly detect abnormal activities and attack behaviors. By monitoring and analyzing DNS traffic, potential signs of attack can be discovered, and corresponding defensive measures can be taken.
- Regularly Check and Update Router and Device Firmware: Regularly check and update the firmware of routers and devices to ensure their security and the latest protective features.
- Use Firewalls and Security Software: Configure firewalls and security software to detect and block malicious DNS requests and responses, preventing malware hijacking and DNS hijacking.
- Pay Attention to Security Awareness and Education: Enhance users' security awareness to avoid clicking on suspicious links and downloading files from unknown sources. Regularly update and scan computers to detect malware.
How EdgeOne Can Help?
1. DDoS Protection
EdgeOne provides and enables L3/L4 traffic-based DDoS attack protection for all connected services. It monitors network traffic in real time and immediately performs traffic cleaning and filtering when a DDoS attack is identified. The DDoS protection feature offers preset protection strategies based on attack profiling, behavior pattern analysis, AI intelligent recognition, and other protection algorithms. It can identify and filter the following types of DDoS attacks:
| Protection Category | Description |
|---|---|
| Malformed Packet Filtering | Filters frag flood, smurf, stream flood, land flood attacks, and filters malformed IP, TCP, UDP packets. |
| Network Layer DDoS Attack Protection | Filters UDP Flood, SYN Flood, TCP Flood, ICMP Flood, ACK Flood, FIN Flood, RST Flood, DNS/NTP/SSDP and other reflection attacks, null connections. |
| DNS DDoS Attacks | DNS DDoS attacks mainly include DNS Request Flood, DNS Response Flood, Fake Source + Real Source DNS Query Flood, authoritative server attacks, and Local server attacks. |
| Connection-based DDoS Attacks | Connection-based DDoS attacks mainly refer to TCP slow connection attacks, connection exhaustion attacks, Loic, Hoic, Slowloris, Pyloris, Xoic and other slow attacks. |
2. Configure DNSSEC
Domain Name System Security Extensions (DNSSEC) can effectively prevent DNS spoofing and cache poisoning attacks. By adopting digital signatures, it can ensure the authenticity and integrity of DNS response messages, thereby preventing users from being redirected to unexpected addresses. This in turn enhances user trust in the internet while protecting your core business. If you want to improve the security of site resolution to prevent hijacking and tampering, it is recommended to activate this configuration.
3. Traffic Monitoring
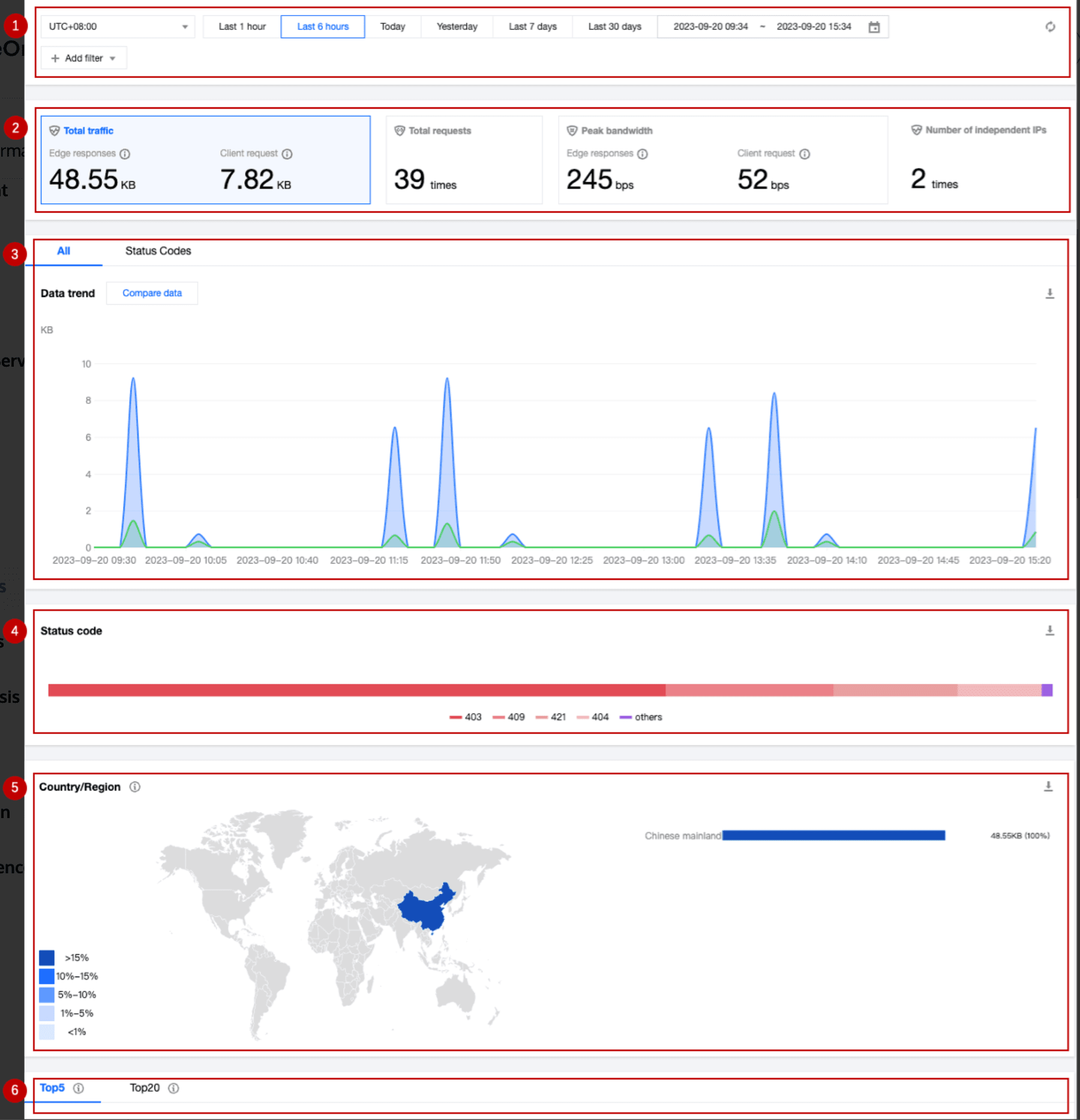
EdgeOne Service provides multi-dimensional, visualized traffic analysis by analyzing L7 (application layer) access log data, including time trend curves of traffic, requests and other indicators, as well as country/region distribution and TOP rankings.
Summary
With EdgeOne, you can identify which sites pose a threat and block all requests from these sites. You can also use EdgeOne as an auxiliary DNS server, as mentioned above. This sets up a wall between your main DNS server and potential attackers. By hiding your main DNS server behind EdgeOne, it protects your organization from attackers and various types of malware.

