Memcached Amplification Attacks: Exploiting Vulnerabilities in UDP Protocols
This Distributed Denial of Service (DDoS) attack against Memcached servers forces a victim's server network to become overloaded with traffic until the service ceases operation. Attackers exploit vulnerable UDP Memcached servers by sending deceptive requests which cause those servers to flood the target victim with request traffic. The victim's resources experience a dramatic surge resulting in the target server becoming overloaded and thus preventing it from issuing new requests. Normal traffic cannot reach the service because it leads to a denial of service situation.
What is Memcached?
Memcached functions as a high-performance open-source system that distributes memory and database caching capabilities. Dynamic websites and web applications utilize key-value pairs to enhance performance through in-memory caching of commonly accessed data. Major corporations including Facebook, Twitter, and YouTube heavily utilize Memcached. The default support for UDP in Memcached makes it a popular choice for attackers to conduct their assaults.
How Memcached Attacks Work
This tool that supercharges website speeds - Memcached - conceals a terrifying dark side. When targeted by hackers, this in-memory caching wonder transforms into a "digital mortar" - using specially crafted HTTP requests, they commandeer vulnerable Memcached servers to redirect what's supposed to be speed-enhancing data channels into torrential "data tsunamis" crashing onto their targets.
The attack unfolds like a precision-engineered trap:
Identity Spoofing: Hackers falsify the request's source address, tricking Memcached into believing data should be sent to the victim
Chain Reaction Trigger: Exploiting server vulnerabilities, they amplify simple "GET" requests by a staggering 51,000 times
Data Tsunami Creation: A few kilobytes of commands suddenly mushroom into gigabytes of UDP packets
Imagine someone attaching a firehose to your garden hose - a 50,000x surge in normal traffic that no network defense could withstand. This attack not only cripples servers but cunningly obfuscates the real attack path, leaving defenders drowning in a sea of fake requests.
The Memcached Amplification Attack is akin to someone calling a cafe's waiter saying, 'I want one of everything on your menu, please call me back and tell me the whole order.' When the waiter asks for a callback number, the person gives the target victim's phone number instead. Then, the target victim receives a call from the restaurant, leading to a massive influx of information they did not request.
Specific Attack Process
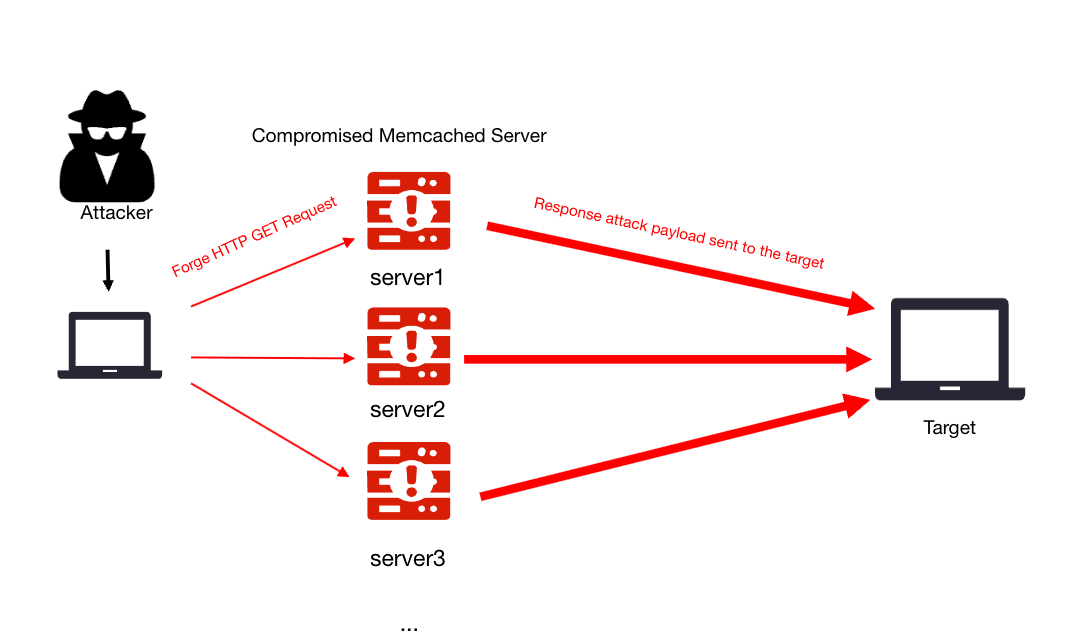
- Attackers scan the internet to find vulnerable Memcached servers, often deploying their malicious programs to run on the same physical machine as the target program, typically involving deployment in a multi-tenant environment;
- Next, attackers use the target victim's IP address to forge HTTP GET requests, demanding the server return a large amount of UDP Memcached attack payload data. This request aims to spoof the source IP address, making it appear as though it is coming from the victim's IP address.
- The vulnerable Memcached server receives the request and sends a large amount of data to the victim's IP address in response.
- The victim's data center servers become overwhelmed by responding to the massive requests, leading to service overload and inability to respond to normal requests.
Why Are Memcached DDoS Attacks So Effective?
Memcache DRDoS was first discovered by the 360 Information Security Department's 0kee Team in June 2017 and was publicly reported at the PoC 2017 conference in November 2017. The conference report detailed the principles and potential harms of the attack. In this document, the authors noted the characteristics of this attack:
- Memcache has an extremely high amplification factor, at least over 50k;
- There are many Memcached servers (reflection points in the case), estimated to be about 60k globally in November 2017, which can be exploited and these servers often have high bandwidth resources.
US-CERT Security Advisory, This article also introduces some principles and potential harms of UDP-based amplification attacks.
Based on the research report, the following conclusions can be drawn:
This attack method can be exploited to launch large-scale DDoS attacks, and some small attack teams may also gain large traffic attack capabilities they did not previously have. Based on the content of the document, we know that Memcached DDoS attacks are effective because they can amplify attack payload traffic by up to 50,000 times. This means that a small request could lead to a massive amount of traffic being sent to the victim's server or data center. Additionally, Memcached servers are often connected to high-speed networks, meaning traffic can be sent very quickly, making it harder to defend. Another common reason is that attackers do not need to maintain their own infrastructure to conduct DDoS attacks. Attackers can use open internet resources for IP spoofing, UDP port attacks, and other endpoint attacks.
Major International Attack Incidents
DDoS attackers and defenders are always in real-time confrontation. Attackers often create shocking incidents that cause immeasurable damage to nations, governments, businesses, and the internet ecosystem. Below, we list some real cases:
GitHub Suffers a 1.35 Tbps Attack
GitHub faced the biggest Distributed Denial of Service attack in history on February 28, 2018 when traffic reached 1.35 Tbps at its peak. The interruption caused service disruptions on GitHub which resulted in high latency for users before the site became completely inaccessible. The attackers executed a Memcached reflection amplification attack which resulted in an amplification factor surge of nearly 50,000 times. Using a spoofed GitHub IP address the attackers targeted exposed Memcached servers with stats requests which caused the servers to send response data back to GitHub. The servers became overloaded as the response data reached massive proportions which caused network congestion. GitHub engaged Akamai's CDN services at this time and utilized its traffic scrubbing centers to clear malicious packets. The attack was stopped eight minutes after Akamai integration.
A U.S. Service Provider Suffers a 1.7 Tbps Attack
Just days after the GitHub attack, a U.S. service provider reported a peak traffic Memcached reflection attack reaching 1.7 Tbps. The attackers used about 20,000 exposed Memcached servers to initiate a flood of traffic by forging IP addresses. The main platforms targeted included well-known platforms such as Google, Amazon, Pornhub, as well as gaming websites (like Rockstar Games, Minecraft), and financial institutions. The service provider immediately initiated a repair task for over 60,000 exposed Memcached servers and restricted Memcached UDP traffic through blacklist filtering.
Continuous Attacks on the New Zealand Stock Exchange
During the final week of August 2020, New Zealand's stock exchange fell victim to a meticulously orchestrated cyberattack. Hackers unleashed a relentless five-day barrage using Memcached reflection attacks - a "heavy artillery" in the cybercriminal arsenal - flooding the exchange with traffic tsunamis. Daily service disruptions lasting up to six hours paralyzed stock and bond trading, leaving investors glued to screens displaying nothing but "connection failed" notices.
This assault inflicted more than financial losses; it detonated a vulnerability bomb within the financial infrastructure. As investors watched their account data stagnate and market prices remain frozen in a six-hour time capsule, individual concerns snowballed into collective panic. The exchange's technical teams engaged in a high-stakes race against time, collaborating with New Zealand's Government Communications Security Bureau (GCSB) and ISPs to deploy layered defenses: Erecting digital firewalls through dedicated high-defense IPs while activating traffic-scrubbing systems to neutralize malicious data torrents. Through unrelenting efforts, they finally resuscitated the trading systems.
Though the identity of the ransomware group remains partially obscured, the attack's unprecedented duration suggests a cyber tempest of historical proportions. This incident sounds a clarion call: In an era dominated by cryptocurrencies and electronic trading, every cyberattack carries the potential to spark a financial tsunami. Safeguarding investors' digital assets demands the entire industry build smarter, more adaptive defense architectures.
How to Protect Against Memcached Attacks
- Pulling the Plug: Disabling the UDP Protocol: The UDP protocol, which is the default for this memory caching tool, is like an airport security checkpoint with no checks — anyone can forge an identity and get through. Hackers exploit this by using the UDP protocol to masquerade as victims when sending requests. It is recommended to completely disable UDP when it is not needed, akin to installing a security door on the server that only allows the verified TCP protocol to pass.
- Setting Up an Electronic Gatekeeper: Deploying Smart Firewalls: A firewall acts like a 24-hour security guard, precisely identifying and blocking malicious traffic from blacklisted IPs. It is advisable to deploy high-defense firewalls at server entry points to monitor and block connection requests from known attack sources in real-time, making it impossible for hackers to even touch the server's door.
- Vaccinating the System: Keeping Software Updated: Vulnerabilities are like the flu virus, spreading through outdated software. The Memcached team regularly releases security patches to fix known vulnerabilities, and it is recommended to update to the latest version promptly. This is akin to vaccinating the server, giving the system immunity against new types of attacks.
- Cutting Off Ammunition Supply: Limiting Response Data Volume: Hackers' amplification attacks essentially involve getting something for nothing — using minimal requests to trigger massive responses. It is recommended to control the response data of each UDP request to be within the size of the original request through code optimization. This is like replacing a cannon with a water gun, rendering the attacker's 'data ammunition depot' completely ineffective.
Edgeone filters UDP traffic at our network edge, eliminating risks from amplification attacks like these. Edgeone's protection scenarios cover various sectors including gaming, internet, finance, government, and enterprises, providing and activating L3/L4 traffic-based DDoS attack protection for all connected services. It monitors network traffic in real time, and immediately undertakes traffic scrubbing and filtering upon detecting a DDoS attack. The DDoS protection feature offers preset protection strategies, utilizing defense algorithms based on attack profiles, behavioral pattern analysis, and AI-based intelligent recognition, capable of identifying and filtering the following types of DDoS attacks. Additionally, EdgeOne provides basic DDoS protection capabilities and resources to all services connected to EdgeOne, offering basic protection sufficient for everyday use for most site services and TCP/UDP applications. On this basis, for businesses that anticipate a higher risk of significant DDoS attacks, need to maintain persistent connections, or require customized traffic control strategies, EdgeOne offers dedicated DDoS protection. If you are interested, you are welcome to explore Edgeone's advanced DDoS protection.
Memcached DDoS Attack FAQ
Q1: How can one detect a Memcached reflection attack?
A1:
By using traffic monitoring tools (such as NetFlow, SIEM) to detect abnormal UDP 11211 port traffic, especially when there is a significant difference in the size of request and response packets (response packets are much larger than request packets).
Q2: Why is it difficult to trace the source of the attack?
A2:
Attackers forge the target IP, and Memcached servers are distributed globally, leading to dispersed traffic sources. Additionally, the attack often combines with other reflection techniques (such as NTP), increasing the difficulty of tracking.
Q3: How can enterprises respond to large-scale attacks (e.g., Tbps level)?
A3:
- Layered defense: Deploy CDN and DDoS high-defense services to clean traffic at the backbone network and IDC entrances.
- Protocol restrictions: Disable the Memcached UDP protocol, retain only TCP, and enable SASL authentication.
- Redundant architecture: Use multi-line BGP access to avoid single points of failure.
Q4: Are there open-source tools to mitigate attacks?
A4:
- Mem-Fixed: A tool developed by Corero that sends specific commands to shut down the Memcached service on attacking servers.
- Shodan scans: Used to discover exposed Memcached servers, to strengthen or block them in a timely manner.
Q5: Do the attacks involve ransom demands?
A5:
Some attacks are accompanied by ransom emails demanding payment in cryptocurrencies such as Monero. For example, in the GitHub attack, attackers attempted to profit by implanting ransomware.
Q6: What are the future trends of Memcached attacks?
A6:
As the number of exposed servers decreases, attacks may shift towards more covert protocols (such as QUIC) or combine with AI technology to optimize attack paths. It is recommended that enterprises regularly update their protection strategies and strengthen monitoring of 0day vulnerabilities.
Q7: Do individual users need to guard against Memcached attacks?
A7:
Individual users are usually not direct targets, but should be cautious of routers and smart home devices exposing Memcached services. It is advisable to disable public internet access on devices and regularly update firmware.

