HULK Attack Tool: How to Identify and Mitigate HTTP GET Floods in Web Servers
Understanding HULK
What is HULK Attack?
HULK (HTTP Unbearable Load King) is a complex denial-of-service (DoS) attack tool designed to overwhelm web servers by generating a high volume of HTTP GET requests. It uses different tricks to get around standard security measures like rate limiting and intrusion detection systems (IDS). HULK attacks are really effective because they use smart tricks like creating new URLs on the fly, faking headers, and flooding sessions. This makes the attack sneaky and hard to notice.
HULK Attack Workflow
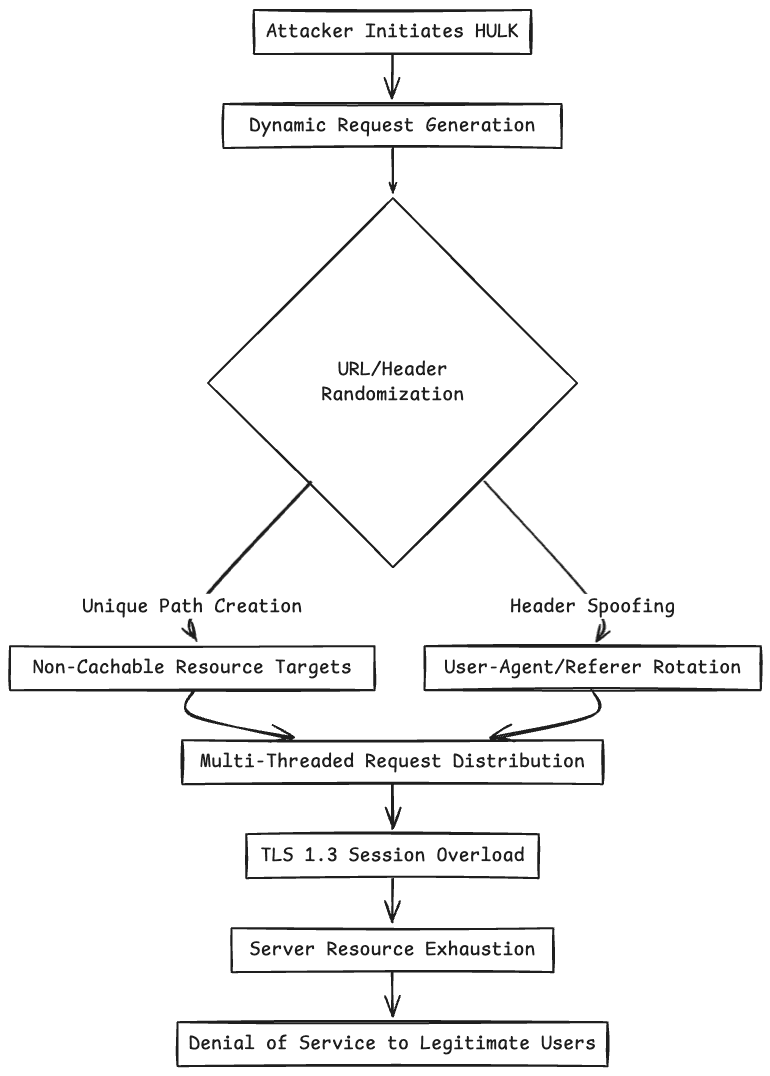
HULK uses a step-by-step approach to launch its attacks, specifically crafted to slip past regular rate limits and intrusion detection systems (IDS). Here’s a simple breakdown of how its attack process works:
Key Evasion Techniques
- Creating URLs on the fly
- Creates URLs that can't be cached (like
/product?random=123abc) to get around caching systems set by CDNs. Attackers often add random bits to these URLs (for example,token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.XtZbQZvNjJlZmVlZw) to make each link unique. This helps them slip past caching limits and control measures.
- Header Spoofing
- Rotates through 1,200+ User-Agent strings, like this one:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36. It also changes theX-Forwarded-ForIPs. Plus, it can spoof headers likeAccept-Language,Cookie, andCache-Controlto make it look like real users are browsing. For example:
GET /api/v1/resource HTTP/1.1
Host: example.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
X-Forwarded-For: 192.168.1.1, 203.0.113.1
Cache-Control: no-cache - Session Flooding
- Creates thousands of simultaneous TLS 1.3 sessions by using improved security protocols. This takes advantage of weaknesses in the server's session management, leading to memory issues and connection shortages. Hackers usually go after TLS 1.3 because its quicker handshake process allows them to spin up sessions at a much higher rate.
Detecting HULK-Driven HTTP GET Floods
Detection Indicators
| Category | Red Flags | Tools/Methods |
|---|---|---|
| Traffic Volume | Sudden 10x+ spike in GET requests (e.g., 50k/min → 500k/min) | NetFlow analyzers (Wireshark), Cloud monitoring (Tencent Cloud Monitor, AWS CloudWatch, Google Stackdriver). |
| Request Patterns | High URL entropy (>4.0 Shannon value) Repeating patterns with slight variations | Log analysis (ELK Stack), URI frequency mapping (GoAccess). |
| IP Behavior | Traffic originating from IP stresser pools (e.g., 192.168.1.0/24 ranges). | IP reputation databases (AbuseIPDB, Spamhaus DROP List), GeoIP tracking. |
| Server Health | CPU utilization >90%, connection timeouts, and memory exhaustion | System monitoring (Prometheus, Datadog), application performance metrics. |
Step-by-Step Detection Process
- Baseline Establishment
- Use tools like Grafana to establish traffic baselines for:
- Average requests per minute (RPM)
- Unique URI patterns
- Session duration distribution
- Anomaly Alerting
- Configure SIEM systems (Splunk, Elastic Stack) with custom rules:
index=web_logs
| stats count as request_count
| where http.method == "GET"
| group by ip
| threshold request_count > 5000, count where _time > now() - 5m - Set alerts for:
- RPM exceeding 5,000
- URLs with entropy scores >4.2
- Sudden spikes in TLS session establishments
- Forensic Analysis
- Search logs for HULK signatures:
grep -E "^GET|User-Agent:HULK|X-Forwarded-For:127\.0\.0\.1" /var/log/nginx/access.log - Analyze packet captures for repeated attack patterns using Wireshark.
Mitigation Framework
Defense Layers
Mitigation Tactics Comparison
| Tactic | Pros | Cons |
|---|---|---|
| Rate Limiting | Blocks malicious IPs quickly | May impact legitimate users during flash sales |
| WAF Rules | Stops known attack patterns (e.g., HULK/1.0 User-Agent) | Requires continuous rule updates |
| IP Blocklisting | Immediate effectiveness against stresser IPs | Vulnerable to IP rotation and botnet usage |
Advanced Mitigation Strategies
- Energetic Rate Limiting
- Implement Nginx
limit_req_zonewith energetic thresholds:
limit_req_zone $binary_remote_addr zone=dl:10m rate=1r/s;
location / {
limit_req zone=dl;
} - Take advantage of the global rate limiting features in today's modern ADCs for better distributed protection.
- Challenge-Response Mechanisms
- Deploy CAPTCHA for high-risk endpoints (e.g., login pages).
- Integrate client-side entropy validation to distinguish human users from bots. For example:
// note: The calculateEntropy function is a simplified example, but in practice more complex implementations may be required to accurately calculate entropy.
function calculateEntropy(str) {
const charSet = new Set(str);
const len = str.length;
const entropy = [...charSet].reduce((sum, char) => {
const p = str.split(char).length - 1;
return sum - (p / len) * Math.log2(p / len);
}, 0);
return entropy;
}
// client-side validation
function validateRequest() {
const entropyScore = calculateEntropy(document.userAgent + window.location.href);
if (entropyScore < 4.5) {
// This is a hypothetical method for sending challenge tokens to clients. In practice, this may involve integrating a third-party CAPTCHA service or using client-side authentication capabilities provided by a specific Web Application Firewall (WAF).
edgeone.sendChallengeToken();
}
} - TLS Session Management
- Optimize Apache session caching:
SSLSessionCache shmcb:/run/shm/sssession_cache(102400)
SSLSessionCacheSize 102400
SSLSessionTimeout 10m - For advanced protection, enable session hijacking mitigation features in next-gen firewalls.
IP Stressers
Legitimate vs. Malicious Use
| Aspect | Legitimate Use | Malicious Use |
|---|---|---|
| Traffic Patterns | Controlled bursts with clear test plans | Randomized high-volume floods |
| Protocol Diversity | HTTP/HTTPS only | Mixed UDP/ICMP/HTTP payloads |
| Legal Compliance | Adherence to service provider ToS | Violates CFAA, GDPR, and other cybersecurity laws |
Identifying Stresser Traffic
- Behavioral Analytics:
- Look for geographically dispersed traffic spikes (e.g., 10,000 IPs from Eastern Europe in 5 minutes).
- Packet Analysis:
- Use tcpdump to inspect packet payloads for stresser signatures:
tcpdump -i eth0 -n 'tcp port 80 and http.request.method == "GET"' - Reputation Feeds:
- Cross-reference IPs against MaxMind GeoLite2 and industry-leading threat feeds.
Case Study
Attack Scenario
A mid-sized e-commerce platform suffered an 800k requests/minute attack during Black Friday, resulting in 45-minute downtime and $200K in lost sales.
Response Workflow
- Traffic Analysis
- Darktrace detected 60% of traffic originating from IPs associated with Luminati stresser services.
- ELK Stack revealed 98% of requests targeting
/api/cartwith randomized query parameters.
- Mitigation Steps
- Emergency Rate Limiting:
limit_req_zone $binary_remote_addr zone=emergency:10m rate=100r/m;
location /api/cart {
limit_req zone=emergency;
} - IP Blocking:
- Synced Spamhaus DROP List IPs into the firewall:
// Example rule template for enterprise-grade firewalls
{
"action": "block",
"priority": 1,
"source_ip": "192.0.10.0/24",
"geolocation": ["CN", "US"]
} - CAPTCHA Integration:
- Enabled risk-based verification for API endpoints to balance security and usability.
- Post-Attack Measures
- NGINX Optimization:
worker_processes auto;
events {
worker_connections 4096;
}
http {
keepalive_timeout 65s;
...
} - Threat Intelligence Partnership:
- Subscribed to a provider offering real-time attack pattern detection for emerging threats like HULK variants.
Results
- Downtime reduced from 45 minutes to 2 minutes in subsequent attacks.
- False positives dropped by 85% after refining WAF rules.
- Annual DDoS mitigation costs decreased by $40k through proactive measures.
Proactive Defense Checklist
Infrastructure Hardening
- Set Nginx/Apache connection limits:
worker_processes 4;
events {
worker_connections 4096;
} - Enable SYN cookies on Linux kernels:
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_max_syn_backlog = 65535 Monitoring & Alerting
- Deploy behavioral analytics platforms to detect anomalous traffic patterns.
- Configure Prometheus alerts for:
- alert: HighRequestRate
expr: rate(http_requests_total[5m]) > 1000
for: 10m
labels: severity=high Incident Response
- Maintain pre-built WAF rule templates for HULK variants.
- Establish partnerships with DDoS mitigation providers for enterprise-grade protection.
Conclusion
HULK and IP stresser attacks can really pose serious threats to organizations. However, by adopting a comprehensive defense strategy that includes traffic analysis, rate limiting, and optimizing infrastructure, you can greatly reduce their impact. For those organizations that emphasize a zero-trust architecture and need ultra-low latency, EdgeOne offers some fantastic solutions:
Near-source Cleaning : EdgeOne provides edge security using Anycast technology (Unicast in mainland China) for near-source cleaning and attack traffic dispersion to nearby ISP nodes, resulting in 15 Tbps+ global protection, exceeding the largest historical DDoS attacks.
AI Intelligent Recognition : EdgeOne employs AI analysis for accurate malicious request identification, reducing false alarms and offering efficient, adaptive, and low-maintenance DDoS protection. It blocks over 99.995% of DDoS attacks within seconds.
One-stop Solution : EdgeOne offers an all-in-one security and acceleration solution for internet businesses, tackling network performance and security challenges with increased cost-effectiveness and reduced management costs compared to standalone solutions.
By using EdgeOne DDos Protection, businesses can ensure the availability and performance of their online services, even in the face of large-scale DDoS attacks.
We have now launched a free trial, welcome to contact us for more information.
FAQs about HULK attacks
1. What is a HULK attack?
HULK (HTTP Unbearable Load King) is a complex denial-of-service (DoS) attack tool designed to overwhelm web servers by generating a high volume of HTTP GET requests.
2. How does a HULK attack bypass security measures?
HULK attacks use techniques such as dynamically generating uncachable URLs, spoofing request headers, and session flooding to slip past standard rate limiting and intrusion detection systems.
3. How can HULK attacks be detected?
Indicators for detecting HULK attacks include sudden spikes in GET request volume, high URL entropy values, and traffic originating from known attack IP pools.
4. What should be done to mitigate HULK attacks?
Mitigation strategies include implementing rate limiting, using Web Application Firewall (WAF) rules, managing IP blocklists, and deploying challenge-response mechanisms (like CAPTCHA) on high-risk endpoints.
5. How big of a deal is a HULK attack?
HULK attacks can lead to high server loads and service outages, resulting in economic losses and reputational damage for organizations.
6. How can infrastructure be optimized to defend against HULK attacks?
Optimizing infrastructure can involve setting connection limits, enabling SYN cookies, and deploying behavioral analytics platforms to monitor for anomalous traffic patterns.
7. Can HULK attacks be launched from multiple IP addresses?
Yes, HULK attacks can use botnets or IP stresser services to hit from various IP addresses, which makes it trickier to block them.
8. What are the signs of a HULK attack in server logs?
You can spot a HULK attack in your server logs when you see a ton of GET requests coming from just one or a couple of IP addresses. You might also notice some repetitive patterns in the URLs, with just a few small changes.
9. How can organizations prepare for potential HULK attacks?
To get ready, organizations should regularly check their security, set up strong systems to monitor traffic, and make sure they have a plan for responding to any incidents.
10. Are there specific tools recommended for detecting HULK attacks?
Recommended tools for detecting HULK attacks include NetFlow analyzers (like Wireshark), log analysis tools (such as ELK Stack), and application performance monitoring solutions (like Prometheus).
11. What role does AI play in defending against HULK attacks?
AI can enhance defense mechanisms by analyzing traffic patterns in real-time, identifying malicious requests, and reducing false positives, which helps in quicker threat mitigation.
12. How often should security measures be updated to combat HULK attacks?
It's a good idea to check and update your security measures regularly—ideally every three months. Of course, you should also take a close look right away if there's ever a big security issue or if you find a vulnerability.
13. What is the difference between HULK attacks and other types of DDoS attacks?
HULK attacks specifically target web servers with HTTP GET requests and employ evasion techniques, while other DDoS attacks may use different protocols (like UDP or ICMP) and methods to overwhelm resources.

