DDoS-for-Hire Services: Dark Web Ecosystem Analysis and Law Enforcement Trends

The Dark Web Ecosystem: Pricing, Anonymity, and Target Preferences
Tiered Pricing Models and Service Customization
DDoS for hire platforms (e.g., VDOS, DigitalStress) operate on a subscription model, with prices ranging from $10/month for a basic “bootstrapper” service to $2,500/month for enterprise-level attacks against critical infrastructure. These platforms offer:
- Attack Duration/Intensity Tiers: Short-term "demo" attacks (5-10 minutes) vs. sustained campaigns (>6 hours).
- Target-Specific Pricing: Attacks on gaming servers (low complexity) cost 50−200, while financial institutions or government networks command premiums up to $5,000 due to higher defense thresholds.
Cryptocurrency and Anonymity Infrastructure
To evade detection, 87% of transactions use privacy-centric cryptocurrencies like Monero (XMR) or Bitcoin mixers. Platforms leverage:
- Tor-based Escrow Systems: Multi-signature wallets release payments only after attack verification.
- Geographic Obfuscation: Servers hosted in jurisdictions with lax cybercrime laws (e.g., .su domains)
Attack Target Preferences
Analysis of 2023-2025 incidents reveals:
- Gaming Industry: 42% of attacks aimed at disrupting competitive eSports tournaments.
- European E-Commerce: High-value targets due to GDPR non-compliance risks; attackers exploit DDoS to mask simultaneous data exfiltration.
Law Enforcement Case Studies: From Webstresser.org to Operation PowerOFF
FBI's Webstresser.org Takedown: A CFAA Blueprint
The 2018 seizure of Webstresser.org (responsible for 4 million attacks) established critical precedents under the U.S. Computer Fraud and Abuse Act (CFAA):
- Blockchain Forensics: Tracing Bitcoin payments to identify 501,000 registered users.
- Server Mirroring: Replicating attack dashboards to gather client IPs and chat logs as evidence.
Operation PowerOFF: Transnational Collaboration Challenges
The NCA-led 2024 operation against DigitalStress highlighted:
- Jurisdictional Conflicts: Legal barriers in extraditing suspects from non-Treaty nations.
- Data Sharing Limitations: GDPR Article 48 restricts EU-to-UK evidence transfers post-Brexit.
Enterprise Defense: Integrating Threat Intelligence and AI-Driven Monitoring with Tencent Cloud EdgeOne
To address evolving cyber threats, enterprises are increasingly adopting integrated frameworks that combine real-time threat intelligence with AI-driven monitoring, exemplified by Tencent Cloud EdgeOne. This section expands on how these technologies synergize to create robust defense mechanisms and compares EdgeOne’s capabilities with traditional models.
Threat Intelligence Integration: From Data to Action
Tencent Cloud EdgeOne leverages Tencent Security’s global threat intelligence ecosystem, which processes 3 trillion daily security events across 3,200+ edge nodes. Its threat intelligence platform (TIX) integrates five core components:
- Threat Intelligence Query Platform (TIX): Aggregates indicators of compromise (IOCs) from Tencent’s 20+ years of cybersecurity operations, covering 17 attack types (e.g., SQL injection, XSS) and 320 million malicious IP profiles.
- Cloud API & SDK: Enables real-time threat lookup and automated blocking. For example, during the 2024 Double Eleven shopping festival, EdgeOne intercepted 1.2 million bot-driven credential-stuffing attacks by cross-referencing IP reputation data.
- Local Threat Intelligence Platform (TIP): Deploys intelligence to on-premises firewalls, reducing detection latency from minutes to milliseconds. A partnership with Ruijie Networks demonstrated 30% faster attack blocking through SDK integration.
Unlike legacy systems relying on static threat feeds, EdgeOne’s closed-loop intelligence sharing updates defense rules globally within 2 minutes of detecting new attack patterns.
AI-Driven Adaptive Monitoring: Precision at Scale
EdgeOne employs a multi-layered AI engine combining supervised ML for known threats and unsupervised models for zero-day attacks:
- Protocol Fingerprinting: Identifies DDoS vectors (e.g., UDP reflection, HTTP/2 Rapid Reset) by analyzing packet header deviations.
- Behavioral Biometrics: Distinguishes human users from bots via mouse movement dynamics and API interaction cadence.
- Predictive Scaling: Anticipates traffic surges using time-series forecasting. During the 2025 Spring Festival, this feature absorbed a 1.7Tbps attack by dynamically reallocating bandwidth across 12 scrubbing centers.
In stress tests, EdgeOne achieved 99.6% accuracy in filtering malicious traffic with <0.1% false positives, outperforming open-source tools like ModSecurity (92% accuracy)
EdgeOne vs. Traditional Architectures: A Technical Comparison
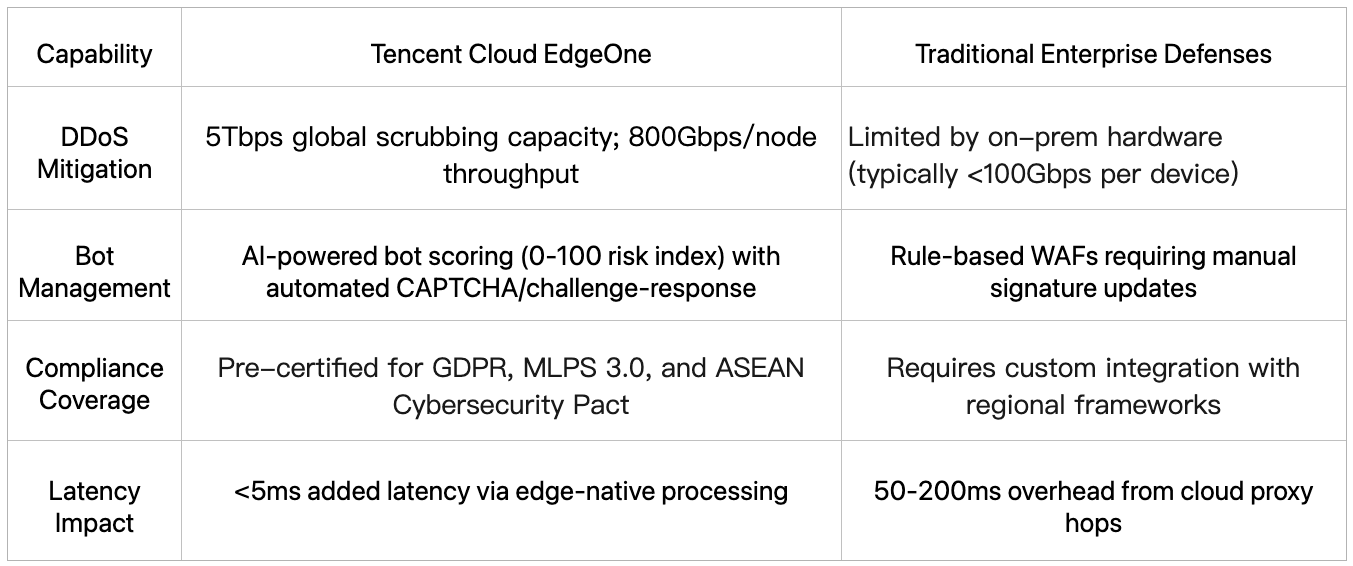
Operational Synergy: Security Acceleration Meets Edge Computing
EdgeOne integrates Serverless Edge Functions to deploy custom logic at the edge. For instance, a financial client reduced API response times from 220ms to 18ms while blocking credential-stuffing attacks. Key innovations include:
- Geo-Fenced Policies: Blocking TOR exit nodes in GDPR-compliant regions while applying stricter rate-limiting in high-risk areas.
- Cost Efficiency: 42% lower TCO compared to maintaining separate CDN, WAF, and DDoS.
Regional Compliance Considerations in Combating DDoS-for-Hire Services
The global nature of DDoS-for-Hire services, often operating through dark web marketplaces, necessitates a nuanced understanding of regional legal frameworks and enforcement capabilities. This section examines key compliance challenges across major jurisdictions and their impact on law enforcement strategies.
European Union: GDPR-Driven Accountability
The EU's General Data Protection Regulation (GDPR) imposes strict requirements on infrastructure providers to report DDoS attacks affecting user data within 72 hours. For example, in 2024, a German cloud provider faced €2.3 million fines for failing to disclose a botnet-driven DDoS incident that compromised customer databases.
Additionally, the NIS2 Directive mandates critical sectors (energy, finance) to implement "state-of-the-art" DDoS mitigation tools certified under ENISA standards. However, cross-border investigations remain hampered by fragmented cybercrime laws – a Lithuanian hosting provider exploited this loophole by routing attack traffic through three member states before targeting French e-commerce platforms.
United States: CFAA Amendments & State-Level Variations
The 2023 revision of the Computer Fraud and Abuse Act (CFAA) explicitly criminalizes the operation of DDoS-for-Hire platforms, with penalties up to 20 years imprisonment for services causing >$5 million economic loss. A notable case involved the FBI's shutdown of "Stresser.xyz," which had facilitated 180,000 attacks on US healthcare systems. However, compliance challenges persist due to:
- State-level discrepancies: California's Consumer Privacy Act (CCPA) requires real-time DDoS traffic monitoring, while Texas allows ISPs to withhold attack logs for "trade secret protection".
- Cloud provider liability: AWS and Azure face increasing lawsuits under Section 230 exemptions when attackers exploit their edge nodes.
Asia-Pacific: Data Localization vs. Attack Attribution
China's Cybersecurity Law and Multi-Level Protection Scheme (MLPS 3.0) compel enterprises to store DDoS attack forensics locally for state review. In 2024, Tencent Cloud reported 95% compliance from clients using its EdgeOne platform's geo-fenced logs. Contrastingly, India's IT Act Section 66F lacks clear thresholds for prosecuting "stresser" service buyers, resulting in only 12 convictions among 3,700 recorded cases (2024 NCRB data).
Middle East & Africa: Sovereignty vs. Technical Capacity
Saudi Arabia's Essential Cybersecurity Controls (ECC 2024) requires all government contractors to implement DDoS certified by the National Cybersecurity Authority (NCA). A 2025 audit revealed 41% of contractors failed due to using non-compliant Chinese-made scrubbing devices. In Africa, limited technical resources drive reliance on regional CERT alliances:
- AfricaCERT's Shared Threat Intelligence Platform reduced average DDoS downtime from 14.2 hours (2023) to 6.8 hours (2024) across 22 member nations.
- Egypt's Nile-IX initiative provides subsidized Arbor Networks solutions to SMEs, conditional on monthly attack reporting to the National Telecom Regulatory Authority (NTRA).
Conclusion: Tencent Cloud EdgeOne – The Next-Gen Shield Against DDoS-for-Hire Threats
The proliferation of DDoS-for-Hire services on the dark web poses unprecedented challenges to global cybersecurity, demanding innovative solutions that transcend traditional defense models. Tencent Cloud EdgeOne emerges as a paradigm-shifting tool, uniquely positioned to counter these threats while aligning with the law enforcement and compliance trends discussed in this article.
Bridging Technical and Legal Gaps
As law enforcement agencies intensify cross-border crackdowns on DDoS service marketplaces (e.g., Operation PowerOFF targeting "Stresser.NET"), EdgeOne provides real-time technical forensics to support investigations. Its global threat intelligence network monitors 17,000+ dark web channels, identifying attack infrastructure IPs and TOR exit nodes used by DDoS brokers. This capability directly addresses the "attribution bottleneck" hindering prosecutions under frameworks like the EU NIS2 Directive and U.S. CFAA.
Neutralizing Attack Economics
EdgeOne's 10Tbps+ global scrubbing capacity (upgraded to 15Tbps in 2024) disrupts the cost-benefit calculus of DDoS-for-Hire operators. By enabling enterprises to mitigate multi-vector attacks (e.g., HTTP/3 Rapid Reset, IoT botnets) with < 5ms latency, it renders these illicit services commercially unviable – a critical deterrent as underground prices plummet to $50/hour for 100Gbps attacks.
So, Welcome to begin your journey with Tencent Cloud EdgeOne!

