Comprehensive Guide to Multi-Scenario EdgeOne CDN Anti-Fraud Practices
What is CDN Fraud?
CDN fraud refers to unauthorized users illegally obtaining website resources in large quantities, consuming bandwidth and server resources. Unlike DDoS attacks that directly impact website availability, CDN fraud primarily drains bandwidth and computing resources, causing sudden spikes in bandwidth usage or traffic, leading to bills that exceed normal consumption and significantly increasing operational costs.
Common methods of CDN fraud include:
- Sending a large number of fake requests using automation tools, proxy servers, or botnets.
- Continuously downloading large files or transferring massive amounts of data with automation tools.
- Using stress testing tools to send a high volume of concurrent requests, overloading the server.
How to Prevent CDN Fraud?
Set Usage Cap Policies
Implement usage cap policies for key website metrics (such as bandwidth, traffic, request counts, etc.) to control and set reasonable usage limits and alert thresholds. This is an effective strategy to prevent high bills due to fraudulent attacks. Once an alert is triggered, immediately check the real-time requests for any anomalies and take appropriate action.
Configuration Example: Configure a usage cap policy. In the add cap policy window, select the effective site and configure the cap policy based on the following recommendations.
| Configuration of the dimension | Configuration options | Recommended accordingly | Applicable to the scene |
| Statistical cycle | 5 minutes (recommended option) | Set a lower threshold to quickly detect and respond to anomalous flows quantity or request. | Can detect abnormal traffic or request peaks in a short time in time, Quickly take protective measures, applicable for real-time monitoring and immediate response needs. |
| hours | Set the average odor value, combined with the daily normal peak period number of operations According to, to ensure that the cap is not mistakenly touched when the flow surges in a short time. | Captures the trend of fluctuations in the flow over a short period of time, providing certain response time is adjusted for protection. | |
| days (24 hours) | Set higher thresholds based on normal business day traffic 2-3 times, ensuring that abnormal flow is identified over time. | Can provide a global view to identify abnormal flow throughout the day or request mode, which is used to develop long-term protection strategies and Resource planning and | |
| Cap configuration | Seven-tiered traffic (recommended option) | Set the traffic smell value to Increased flow mistakenly touching the cap. | Effectively preventing attackers from consuming by downloading large files in bulk and other ways Bandwidth resources are also available. |
| Number of HTTP/HTTPS requests | Set the smell value to 2-3 times the normal request number to ensure normal The top of the lid is not to be mistaken for the top during peak business hours. | Effectively prevents brush request type attacks, consumed by a large number of false requests Resources ⋅ | |
| Seven layers of bandwidth | Set the bandwidth odor value to 2-3 times the normal bandwit usage, To respond to the surge in bandwidth usage. | Effectively preventing excessive bandwidth consumption and avoiding attacks due to high traffic downloads This leads to waste of resources. | |
| Beyond the smell value | stopped service, need to go to the domain name list to re-enable it. | ||
| Alert value | 50% (recommended option), which sends an alert when the access volume reaches 50% of the alert threshold for the configuration. | ||
Enable Real-Time Log Push
EdgeOne analyzes L7 (application layer) access log data to provide multidimensional, visual traffic analysis. This includes time trend curves for metrics like traffic and request counts, country/region distribution, and top rankings. These features help you quickly detect potential abuse attacks.
To implement refined protection measures, it is recommended to enable the Real-Time Log Push feature. This function delivers request access logs to your specified destination with low latency, and can be configured via console or API. The delay from request initiation to log reception is under 5 minutes, making it suitable for scenarios requiring real-time monitoring and quick troubleshooting, such as preventing CDN abuse. Real-time analysis of access behavior allows for timely identification and analysis of abuse attack characteristics, enabling the configuration of corresponding strategies for precise interception.
Below are the request ranges recorded for each log type:
- Site Acceleration Logs: Records domain access logs, defaulting to only log requests after protection, excluding intercepted requests. These logs provide comprehensive access information to help identify unusually high-frequency requests, abnormal traffic, and potential abuse behaviors.
- Rate Limiting and CC Attack Protection Logs: Records requests that hit L7 protection—rate limiting and CC attack protection rules, regardless of interception. This helps identify behaviors attempting to flood traffic with high-frequency requests.
- Managed Rules Logs: Records requests that hit L7 protection—managed rules, regardless of interception. This aids in detecting protection based on managed rules and identifying potential attacks and abuse behaviors.
- Custom Rules Logs: Records requests that hit L7 protection—custom rules, regardless of interception. This helps identify abnormal requests that meet custom rules, preventing specific types of abuse.
- Bot Management Logs: Records requests that hit L7 protection—Bot management rules, regardless of interception. This assists in identifying abuse behaviors caused by automated scripts or malicious bots.
If you need to push certain field values from HTTP request headers, HTTP response headers, or cookies, you can accurately log this information using the custom log field feature.
How to Analyze CDN Fraud?
After implementing the preventive measures mentioned earlier, if an alert is received indicating a significant increase in usage, the next step is to conduct a thorough investigation. This section focuses on how to utilize EdgeOne's traffic and log analysis features for multi-dimensional analysis of suspected fraudulent traffic.
Traffic Analysis
EdgeOne analyzes L7 (Application Layer) access log data to provide multi-dimensional, visual traffic analysis, including time trend curves for metrics like traffic and request counts, as well as country/region distribution and top rankings. In the context of investigating fraudulent attacks, it's recommended to filter data and focus on the following aspects:
- Referer Distribution: A concentration of empty or invalid Referers often indicates malicious requests such as credential stuffing or scraping.
- Changes in Access Volume by URL/Resource Type: A sudden spike in requests for a few URLs or resource types, significantly exceeding others, may suggest targeted fraud.
- Top Client IPs: Check if a small number of IPs contribute to most requests, assessing the feasibility of IP-based request frequency controls.
You can refer to the following console operation steps:
- Log in to the EdgeOne Console. Click on the Analytics.
- On the L7 client traffic page, select the date range during which fraudulent activity is suspected.
- View the top rankings for the following dimensions:
- Hosts: Subdomains of client requests.
- URLs: Specific resource paths of client requests.
- Resource Types: Types of resources requested, e.g., “.png”, “.json”.
- Client IP Addresses: Specific source IP addresses of client requests.
- Referers: Referer information for client requests.
- Client Device Types:
- Device Types: Types of hardware used, including: TV, Tablet, Mobile, Desktop, and Other.
- Browsers: Types of browsers used for client requests.
- Operating Systems: Types of operating systems used for client requests.
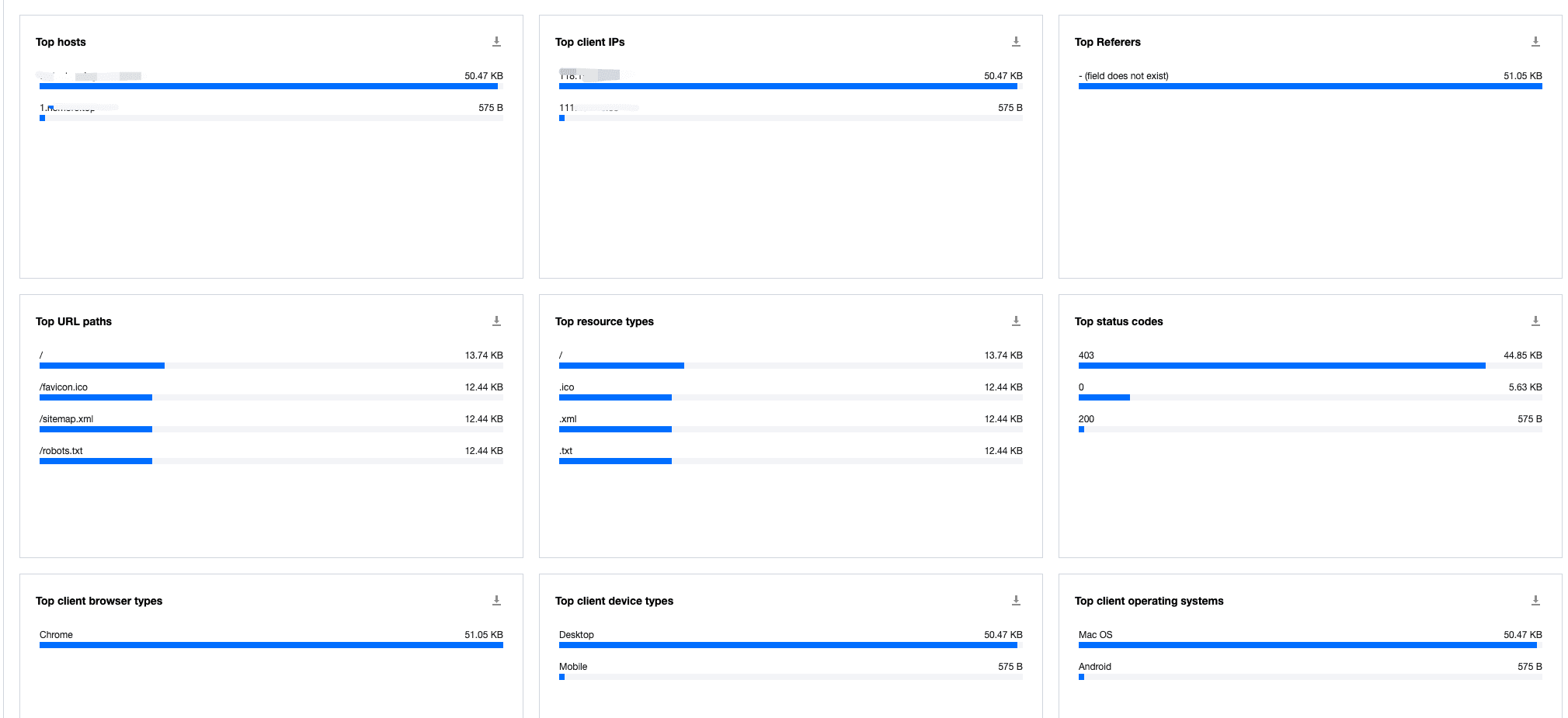
- Click "Add Filter" on the analysis page and apply the following suggested filters to focus on abnormal traffic, then click "OK":
- Referer: Identify empty Referer requests.
- URL: Include the top 5 URLs to locate suspicious hot resources.
- Resource Types: Include the top 5 resource types to identify the distribution of hot resource types.
- Client Device/Browsers/Operating Systems: Set to equal "Other" or "Empty" to identify suspicious, unconventional clients.
- Examine the distribution of the filtered metrics, identify data that significantly deviates from normal levels, and analyze its correlation with fraud.
Offline Log Analysis
To further identify more characteristics of fraudulent requests, an in-depth analysis of offline logs during the alert period is necessary. By conducting a comprehensive analysis through various fields, we can outline the profile of fraudulent requests from multiple dimensions, including source IP, URL path, request parameters, User-Agent, and Referer source. This analysis will provide a data foundation for formulating precise countermeasures.
Key log fields to focus on in the fraud investigation and their corresponding explanations are as follows:
| Field Name | Data Type | Description | Supported by Offline Logs or Not | Supported by Real-Time Logs or Not |
| RequestUrl | String | URL path of the client request, excluding query parameters. | ✓ | ✓ |
| RequestUrlQueryString | RequestUrlQueryString | Query parameter carried in the client request URL. | ✓ | ✓ |
| RequestUA | String | User-Agent information of the client request. | ✓ | ✓ |
| RequestReferer | String | Referer information of the client request. | ✓ | ✓ |
| ClientIP | String | Client IP address connected to EdgeOne nodes. | ✓ | ✓ |
| EdgeResponseBodyBytes | Integer | Size of the response body returned by the node to the client, in bytes. | ✓ | ✓ |
For more fields and their corresponding explanations, please refer to the Seven-Layer Access Log Field Description.
EdgeOne CDN Anti-Fraud Best Practices
In response to the complex and ever-changing attack scenarios of website fraud, there is no one-size-fits-all solution. EdgeOne offers a variety of protective features, such as access control and rate limiting, which can be flexibly combined. Therefore, it is essential to choose the optimal protection configuration based on attack characteristics and actual business conditions.
Below, we provide specific EdgeOne anti-fraud practice tutorials from the perspectives of individual site operators and online business platforms.
Scenario 1: Rapid Interception of Abnormal Source IPs Based on Traffic Analysis
By analyzing traffic and identifying the top 5 resource types, it was found that access to a 5.244MB file was abnormally high. Further investigation revealed that the file URI was /test/app5m.apk, and the request client IPs were concentrated in the 1.11.32.0/24 subnet. Based on this information, an IP blacklist policy can be quickly created to block this malicious subnet and curb potential fraud.
Configuration Recommendation
It is recommended to use the custom rules of EdgeOne Web Protection to configure protective strategies. For specific operations, please refer to the Custom Rules.
For individual users, you can set up a client IP control rule under basic access management, with the matching method set to "Client IP equals" and the matching content set to 1.11.32.0/24, with the action to "Block".
For users of the Basic version and above, in the precise matching strategy, you can configure the matching field to be the client IP equal to 1.11.32.0/24 and the request path (Path) equal to /test/app5m.apk. The action to be executed is a JavaScript challenge.
Scenario 2: Rapid Interception of Anomalous User-Agent Based on Log Analysis
Real-time logs show an abnormal concentration in the RequestUA distribution during a specific time period. Further analysis reveals that the highest number of requests is from python-requests/2.22.0, with many requests using Python script-specific User-Agent identifiers like python-requests/. Since these requests significantly deviate from typical browser User-Agent characteristics, they can be classified as automated requests or even malicious crawlers. Consequently, a User-Agent blacklist rule can be configured to accurately intercept suspicious requests with specific User-Agent identifiers.
Configuration Recommendations
It is recommended to use the custom rules feature of EdgeOne Web Protection to configure protective strategies. For specific operations, please refer to the Custom Rules.
For personal users, you can configure the rule type as User-Agent control in the basic access management, matching requests where the User-Agent equals python-requests/2.22.0, with the action set to intercept.
For basic users and above, you can configure the matching field in the precise matching strategy to include requests with User-Agent containing python-requests/, with the action set to JavaScript challenge.
Scenario 3: Preventing Interception Based on Known Malicious User-Agents
For known common scraping tools, you can pre-configure their characteristic User-Agent strings into custom rules. Enabling this rule globally or on key paths can significantly reduce the risk of scraping attacks. Common scraping User-Agents include: empty User-Agent; curl/xx.xx; Wget/xx.xx; ApacheBench/xx.xx; python-requests/xx.xx.
Configuration Example
We recommend using the custom rules feature of EdgeOne Web Protection to configure protective strategies. For specific operations, please refer to the Custom Rules.
For personal edition users, you can configure two rules in the basic access control settings:
- Rule 1: Configure a User-Agent control rule with a matching condition of an empty request User-Agent, and an action of blocking.
- Rule 2: In basic access control, configure a User-Agent control rule with a wildcard matching condition for request User-Agent, matching the contents of `curl/`, `Wget/`, `ApacheBench/`, and `python-requests/`, with an action of blocking.
For basic and above users, two rules can be configured in the precise matching strategy:
- Rule 1: In the precise matching strategy, configure the matching field for requests where the User-Agent contains `curl/`, `Wget/`, `ApacheBench/`, or `python-requests/`, with an action of JavaScript challenge.
- Rule 2: In the precise matching strategy, configure the matching field for requests with an empty User-Agent, with an action of JavaScript challenge.
Scenario 4: Allow Only Common User-Agents (Temporary High Defense)
When facing large-scale distributed scraping using various User-Agents, if it's difficult to identify malicious User-Agent characteristics individually, you can use reverse logic by allowing only legitimate User-Agents from common browsers and apps. This approach can filter out a significant number of suspicious requests at once, but due to the strictness of the rules, there's a risk of false positives, so it should be used cautiously in conjunction with other dimensional features.
Configuration Recommendation
We recommend using the custom rules feature to configure defense policies. For detailed operations, please refer to the custom rules documentation.
For personal edition users, you can configure the rule type in basic access control to User-Agent control, with the matching method set to "request User-Agent wildcard not matching," and the matching content as *Linux*; *Macintosh*; *Android*; *iPhone*; *iPad*; *Windows*, with the action set to intercept.
For users with the basic plan and above, you can configure the matching field in the precise matching rules to requests where User-Agent does not contain Android, iPhone, iPad, Mac, Windows, or Linux, and set the action to JavaScript challenge.
Scenario 5: Setting High-Frequency Access Restrictions for a Single IP during CC Attack (Temporary High Defense)
CC attack protection identifies CC attacks through rate baseline learning, header feature statistical analysis, and client IP intelligence, then takes action. EdgeOne provides three pre-set CC attack protection strategies:
- High-frequency access request restriction: Used to deal with CC attack behavior that occupies server resources through high-frequency and large amount of concurrent connection requests, and can limit access frequency based on a single IP source.
- Slow attack protection: Used to deal with CC attack behavior that occupies server resources through a large amount of slow connection requests, and can limit access connection minimum rate based on a single session, eliminating slow connection clients.
- Intelligent client filtering: Integrates rate baseline learning, header feature statistical analysis, and client IP intelligence to generate real-time dynamic attack defense rules. Perform human-machine verification for requests from high-risk clients or carrying high-risk header features. Intelligent client filtering is enabled by default and executes JavaScript challenges for clients that meet the rules.
In the event of suspected fraudulent attacks or abnormal usage alerts, it is recommended to temporarily set high-frequency access request limitations to adaptive - emergency level, with the action set to JavaScript challenge. This effectively blocks numerous requests from malicious IPs, preventing fraud and other attacks. For specific operations, please refer to CC attack defense.
Scenario 6: Personalized Frequency Control Based on Business Levels
Unlike DDoS attacks, fraudulent transactions are often more covert and require specific business context for accurate assessment. It’s crucial to establish personalized frequency limitation strategies to avoid mistakenly blocking legitimate users. Interception strategies targeting IPs or User-Agents fall under precise interception. However, attack characteristics may not be obvious; for instance, the request volume from a source IP can reach hundreds of thousands.
To implement a defense strategy based on business context, site administrators must evaluate normal access patterns and establish a traffic baseline. For example, in app download or upgrade scenarios, most IPs typically conduct only one or two downloads, with occasional retries due to failures, generally within a reasonable frequency range. An abnormal high-frequency access may indicate an attack or malicious activity.
When a website is subjected to fraudulent transactions, the domain's bandwidth will significantly increase. To address this, it is recommended to use the EdgeOne Web Protection feature for rate limiting, setting thresholds based on normal business levels, configuring speed limit strategies, or adjusting them through real-time log monitoring. For specific operations, please refer to the Rate Limiting Documentation.
Scenario 7: Frequency Limiting for Game Package Downloads Based on Business Baseline
A gaming platform provides download services for various game installation and update packages, accelerated through EdgeOne. The download URLs for game packages follow a fixed pattern, such as:
- Game A Installation Package: https://cdn.example.com/games/A/installer_v1.0.zip
- Game A Update Package: https://cdn.example.com/games/A/patch_v1.1.zip
- Game B Installation Package: https://cdn.example.com/games/B/installer_v2.0.exe
- Game B Update Package: https://cdn.example.com/games/B/patch_v2.1.exe
On the day of a game version release, a single IP typically downloads once, with retry downloads due to network issues not exceeding three times. However, some IPs frequently download installation and update packages after the release, far exceeding normal user behavior, triggering usage alerts. This may indicate scraping by piracy sites or communities, or attackers attempting to exhaust bandwidth. Rate limiting rules can be configured to promptly block such malicious requests.
Configuration Recommendation
In precise rate limiting, configure the matching object as a custom protection object, with matching fields for URLs containing "games/", "installer/", and "patch/" AND the request method (Method) equal to GET. The counting mechanism triggers when a single client IP requests to the EdgeOne node, with a threshold of exceeding three requests within a 10-minute period. Once triggered, maintain this state for one hour and execute a JavaScript challenge. For detailed steps, please refer to the Rate Limiting Documentation.
Scenario 8: Frequency Limiting Based on Log Analysis of Abnormal User-Agents
A site is under attack due to heavy access from attackers, leading to usage alerts. Real-time log analysis reveals that the access IPs are dispersed, suggesting a distributed attack, but the User-Agent is highly concentrated, e.g., Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/6.0), which is inconsistent with normal operations. Comparing periods without attacks shows a diverse range of User-Agents covering different browsers and devices. The suspicious User-Agent typically has low traffic but has surged to dominate, indicating potential CDN scraping attacks, which can be mitigated by configuring rate limiting rules to block these malicious requests.
Configuration Example
In the precise rate limiting rules, configure the matching object as a custom protection object, with the matching field for User-Agent equal to Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/6.0). The trigger condition is set for exceeding 400 requests within a 1-minute counting period, with the counting mechanism triggered when a single client IP requests to the EdgeOne node. After triggering, maintain this state for 30 minutes and execute a JavaScript challenge. For detailed steps, please refer to the Rate Limiting Documentation.
Conclusion
In addition to direct protective measures against unauthorized usage, websites should prioritize the protection of their resources through proactive defenses. Anti-leeching is a crucial method to prevent unauthorized use of website resources.
Leeching refers to the unauthorized referencing and use of a website's resources (such as images, videos, or software packages) on other sites without the owner's permission, consuming the original site's bandwidth and resources. This not only infringes upon the original site's legitimate rights but can also negatively impact its SEO. Therefore, implementing anti-leeching measures is essential.
EdgeOne offers a comprehensive anti-leeching solution that manages leeching behavior from multiple angles, including Referer-based protection, Token-based protection, and remote authentication. This helps safeguard your content from unauthorized access and enhances the security of your acceleration services.
We have now launched a Free Trial, welcome to Contact Us for more information.

