AI-driven DDoS tools: emerging threats and AI-driven defense solutions

The rapid development of AI has brought significant changes to cybersecurity, which is of vital importance to every Internet user. It is necessary for us to understand AI-driven security products to help us defend against complex attacks. In this article, we mainly introduce common AI attack tools and methods, as well as some AI-driven defense tools, and discuss the compliance issues of AI tools in penetration testing.
AI-driven DDoS tools vs traditional DDoS attacks
AI-driven DDoS tools differ from traditional DDoS attacks in terms of scale, complexity, and adaptive capabilities. Typically, AI-powered attacks are larger in scale, more intricate, and possess a higher degree of adaptability, making them more challenging to defend against.
| Feature | AI-Driven DDoS Attacks | Traditional DDoS Attacks |
|---|---|---|
| Adaptability | Adjust attack vectors, packet size, and frequency in real-time based on target defenses. | Use fixed attack patterns (e.g., SYN floods, HTTP floods) without dynamic adjustments. |
| Traffic Patterns | Mimic legitimate traffic to evade detection (e.g., human-like browsing behavior). | Generate uniform, high-volume traffic (e.g., brute-force floods). |
| Defense Evasion | Bypass CAPTCHAs and rate-limiting thresholds using AI algorithms. | Rely on overwhelming volume to overwhelm defenses. |
| Automation | Fully autonomous botnets with self-healing capabilities. | Require manual intervention to adjust attack parameters. |
| Attack Precision | Target vulnerabilities identified via AI-driven reconnaissance. | Broad, indiscriminate targeting (e.g., IP ranges). |
| Learning Capabilities | Reinforce learning to predict defensive strategies and improve evasion. | No adaptive learning; static attack methods. |
| Scale | Can scale dynamically by recruiting vulnerable devices in real-time. | Limited by pre-compromised botnet size. |
| Detection Difficulty | Higher due to traffic pattern mimicry and adaptive evasion. | Easier to detect via traffic spikes and known signatures. |
AI-Driven DDoS Tools and Techniques
AI-powered DDoS tools leverage machine learning and automation to enhance attack sophistication, evasion, and scalability.
Mirai Variants
It is enhanced with AI to evade detection and select optimal targets. This advanced Mirai botnet version uses artificial intelligence to find and attack the weakest IoT devices and computers which broadens its range of attacks. AI can continuously modify its attack pattern to bypass detection efforts and revolutionize DDoS attack strategies. The algorithm can automatically control infected devices to coordinate attacks.
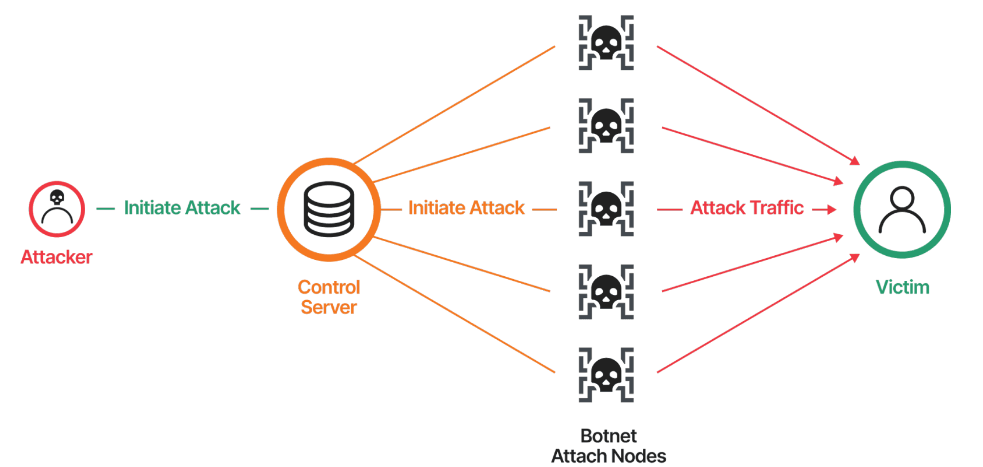
Example: Forest Blizzard, A botnet linked to Russia that uses AI for phishing and custom backdoor deployment.
CAPTCHA Bypass
CAPTCHA represents a security tool established to separate genuine human users from automated software programs. This security system confirms user identity through tasks that involve identifying distorted characters and choosing particular images.
AI-driven tools can solve CAPTCHAs to automate bot traffic, enabling sustained attacks. Common bypass methods include:
- Machine Learning and Image Recognition: AI models identify characters, graphics, and images in CAPTCHAs.
- OCR (Optical Character Recognition): OCR software extracts text from CAPTCHAs, especially those without complex distortions or interference.
- Human-Machine Collaboration: CAPTCHAs are sent to human operators for manual solving.
- Scripts and Automation Tools: Scripts or tools like Selenium simulate human behavior to bypass CAPTCHAs.
- Using Known Cracked Databases: Leveraging databases of previously solved CAPTCHAs, especially for common types.
- Exploiting CAPTCHA Design Flaws: Attackers exploit weaknesses in CAPTCHA setups including missing validations for particular scenarios.
AI significantly improves the efficiency of these bypass methods. With sufficient CAPTCHA examples, large models can autonomously learn to recognize complex content.
Behavioral Mimicry
Automated tools that mimic human behavior enable attackers to execute large-scale DDoS attacks. The attack method uses high request volumes combined with human-like behavior patterns which complicates detection and blocking of malicious traffic. Simulated human behaviors include sending requests, clicking pages, scrolling, filling out forms, and even varying access intervals.
Dynamic Attack Composition
AI switches between attack vectors (e.g., HTTP and SYN floods) based on defensive responses. This is a relatively complex attack method that can adjust the current attack strategy in real-time based on feedback from defenses.
Example Attack Workflow
- Reconnaissance: AI scans for vulnerabilities (e.g., unpatched servers).
- Botnet Recruitment: Compromised devices are added to the botnet via automated exploits.
- Attack Launch: AI coordinates traffic floods, adjusting parameters (e.g., packet size) to evade defenses.
- Evasion: Bots mimic legitimate traffic or solve CAPTCHAs to bypass mitigation.
AI-Driven DDoS Defense Tools
With advanced attack methods, defensive tools must rely on low-latency real-time analysis, anomaly detection, and autonomous responses to counter evolving threats. Below are some well-known AI-driven DDoS defense tools and platforms:
| Tool Name | Features | Functions |
|---|---|---|
| Tencent EdgeOne | Uses AI-powered DDoS intelligent recognition algorithms for real-time mitigation. | 15+ Tbps DDoS protection bandwidth reserve, global anycast protection nodes, independent DDoS IP protection. |
| AWS Shield | Automated DDoS protection service provided by Amazon Web Services. | Automated DDoS detection and mitigation, supports HTTP/HTTPS, TCP/UDP protocols. |
| Akamai Prolexic | Analyzes traffic patterns using AI to mitigate DDoS attacks in real time. | Global distributed defense network, advanced attack analysis. |
| Radware DefensePro | AI-driven DDoS protection device. | Real-time attack detection, automatic mitigation, behavioral analysis. |
| Cloudflare | Uses AI and machine learning to detect and mitigate DDoS attacks. | Real-time traffic analysis, automatic attack mitigation, global distributed network. |
Defense Process Example
- Traffic Monitoring and Analysis: Collect and analyze network traffic data in real-time; use machine learning models to detect abnormal traffic patterns.
- Attack Identification: Identify attack types (e.g., HTTP flood, SYN flood, UDP flood); determine source IP, target IP, and attack intensity.
- Defense Strategy Deployment: Dynamically adjust defense strategies based on attack types (e.g., rate limiting, traffic filtering, CAPTCHA verification); automatically deploy measures like Web Application Firewalls (WAF) or load balancing.
- Continuous Optimization: Optimize detection and defense strategies through machine learning models; log attack data for future analysis and defense.
AI-Driven Automated Testing Tools
Test Craft is a free, open-source browser extension for software testing that simplifies the testing process with a GPT-4-powered assistant. It is user-friendly and can provide various automated test cases tailored to different projects and programming languages, including expected, unexpected, and special test cases. Finally, it generates automated test code based on these cases.
Lambdatest is an AI-powered test execution platform that supports large-scale manual and automated testing using a scalable cloud infrastructure. It offers root cause analysis (RCA) for faster issue resolution, and advanced flaky test detection, and allows customization and in-depth insights into test fragility. It also supports test orchestration, visual testing (comparing visual drafts with UI consistency), and error classification, among other features.
Roost.ai is an AI-driven testing tool that leverages Vertex AI and GPT-4, among other LLMs, to provide automated software testing. It seamlessly accelerates the testing process by offering 100% test coverage. Additionally, it can convert source code, user stories, and other inputs into test cases.
Compliance Issues
The training of AI models relies on massive amounts of data, most of which is scraped from the Internet or uploaded by users. Different training data may produce different results, so AI-driven penetration and defense tools may have risks, value consistency challenges, lack of transparency, and algorithmic bias.
Privacy risks, AI training on content scraped from the Internet may contain personally identifiable information (PII), secrets, and tokens, which may be inadvertently leaked in the output. Local agents can provide privacy-based protection for coding assistants or add tokenization to the output content to protect user privacy.
The value consistency challenge is a key challenge faced by AI development in ensuring that AI-driven products are consistent with human value principles. The value consistency issue involves the AI system's ability to make decisions that are consistent with community norms, ethical standards, and human preferences. For example: WormGPT can automatically generate code to perform various network attacks and quickly iterate and upgrade, which does not meet the consistency with human value principles.
Lack of transparency. AI algorithms and decision-making processes lack transparency. Operations are black boxes with no clear accountability and explanation mechanisms. For example, AI hallucinations can output content that is inconsistent with actual facts or fabricated. Users need to carefully identify the content during use. In the development of AI, we can hopefully improve transparency by making training data public and increasing accountability mechanisms.
AI algorithm bias is a relatively common problem. Bias in training data, algorithm design, or decision-making can lead to unfair results and reinforce existing social inequalities. For example, if a certain group of people is analyzed as abnormal traffic in AI defense and automated testing, then this group of people may never be able to access the product normally. To mitigate the bias of AI-driven tools, active measures need to be taken, such as collecting diverse data sets, bias detection tools, fairness-focused algorithms, and continuous monitoring to identify and resolve issues related to bias.
Conclusion
The cybersecurity challenges brought by AI development are closely related to every internet user. Understanding different attack methods and defense platforms can help businesses and individual users protect their accounts and resources, avoiding bandwidth and traffic theft, among other issues.
EdgeOne is a comprehensive web service platform that provides solutions to enhance website performance and security. It supports AI-powered DDoS protection, offering businesses and individuals a robust, all-in-one solution for faster, safer, and more reliable web services.
FAQs
Q1: Does EdgeOne provide AI intelligent protection?
A1: Yes, Our products provide DDos AI intelligent identification protection.
Q2: How can Internet users prevent their IoT devices from being controlled by hackers?
A2: Update product systems promptly and do not use product default passwords.

