SYN Flood is one of the most primitive and classic Distributed Denial of Service (DDoS) attacks on the internet. It's called a "flood" because it overwhelms a system with a flood of network requests. The "SYN" part refers to the synchronize (SYN) packets used in the attack.
A SYN Flood Attack exploits the three-way handshake mechanism of the TCP protocol, where attackers typically use tools or control zombie hosts to send a massive amount of TCP SYN packets with varying source IP addresses or source ports to the server. The server, upon responding to these packets, generates a large number of half-open connections, aiming to exhaust available server resources. Once the system resources are depleted, the server will become sluggish or even unresponsive when handling legitimate traffic.
How Does a SYN Flood Attack Work?
To understand how a SYN Flood attack works, we first need to know about the normal way computers talk to each other over the internet. This process is called the TCP three-way handshake.
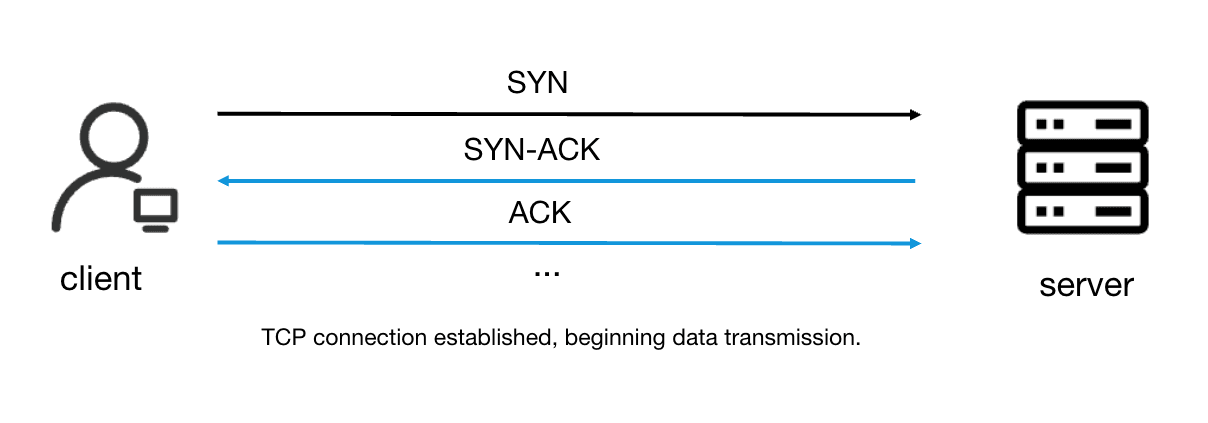
Let's use an example to describe the process of the TCP three-way handshake. Client wants to talk to server and it sends a "hello" message called a SYN packet. The Server says, "I hear you!" by sending back a SYN-ACK packet. Client then says, "Great, let's talk!" with an ACK packet. After these three steps, client an server can start sharing information. Here is a more detailed process:
- At the start of establishing a connection, the client sends a SYN packet to the server and waits for the server to acknowledge. The SYN packet's source IP address and port are those of the client.
- Upon receiving the SYN packet, the server responds with a SYN-ACK (Synchronize-Acknowledgement) packet. The destination IP address and port of the SYN-ACK packet are those of the client.
- The client receives the SYN-ACK packet from the server and sends an ACK packet back to the server. Once the server receives this ACK packet, the three-way handshake is completed, and the TCP connection is successfully established.
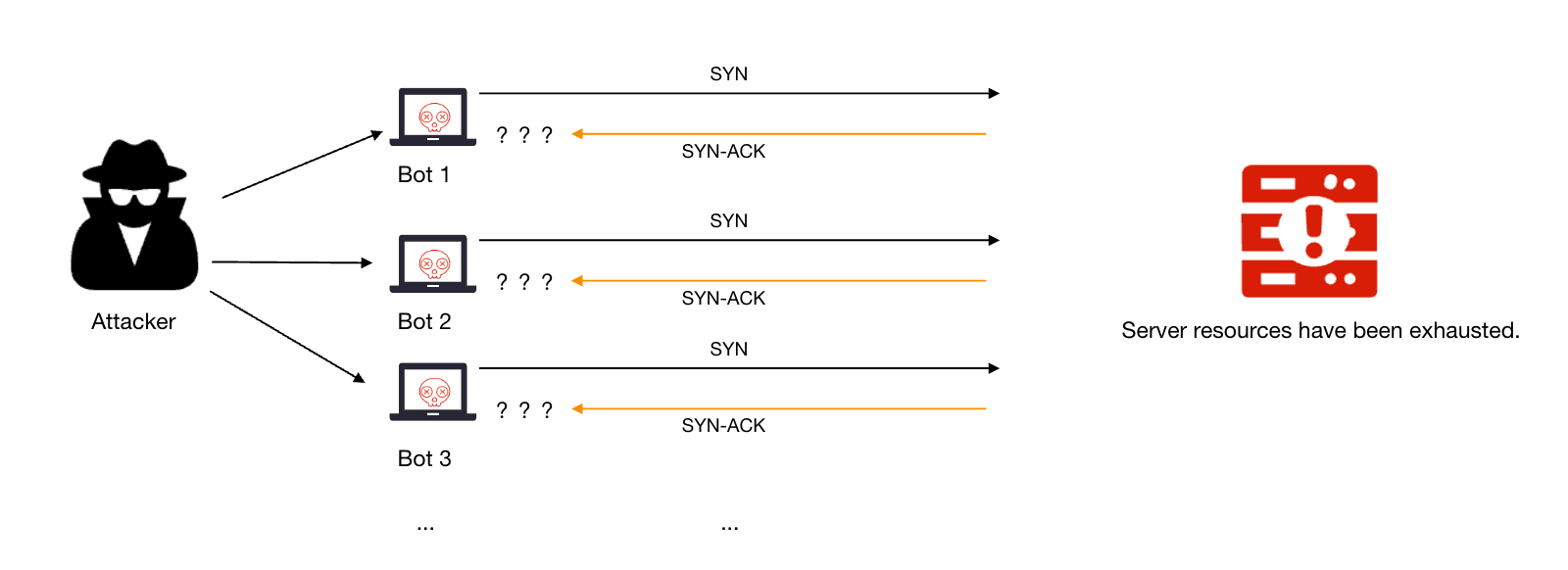
Now, here's how an attacker exploits this process in a SYN Flood attack:
- The attacker sends many SYN packets to the target server, pretending to be from different addresses.
- The target server replies with SYN-ACK packets to all these fake addresses.
- The target server waits for the final ACK packets, which never come.
- This leaves many "half-open" connections on the target server.
- Eventually, the target server runs out of resources to handle real connections.
What are the Types of SYN Flood Attacks?
There are typically several types of SYN flood attacks:
- Direct Attack: In a direct SYN Flood attack, the attacker uses one or several known IP addresses to send a large volume of SYN packets directly to the target server. This method is relatively simple, and the source of the attack is easy to identify and trace. Since the attack traffic comes from fixed or a few sources, network administrators can defend against the attack by configuring firewall rules or directly blocking these IP addresses. However, although this type of attack is relatively easy to defend against, if the attacker controls sufficient bandwidth, it can still significantly impact the target server.
- Spoofing Attack: A deceptive SYN Flood attack involves IP address forgery. Attackers randomly generate source IP addresses or use non-existent IP addresses when sending SYN requests. This method prevents the target server from correctly sending SYN-ACK responses because they are sent to non-existent or incorrect addresses. It also makes tracking the source of the attack more difficult, as the returning packets cannot find the correct source. Spoofing attacks are more covert and complex to defend against, typically requiring more advanced detection and filtering systems to identify and block these forged packets.
- Distributed Attack: A Distributed SYN Flood attack (DSYN Flood) is a more complex and powerful form of attack, usually involving multiple systems controlled by the attackers (such as a botnet). These systems are used to send SYN requests to the target from multiple locations simultaneously, significantly increasing the scale and effectiveness of the attack. Since the attack traffic comes from a wide range of geographical locations and multiple different IP addresses, simple IP blocking or basic traffic monitoring measures are often ineffective. Defending against distributed attacks usually relies on more complex network security solutions, such as Distributed Denial of Service (DDoS) protection services and behavioral analysis technologies, which can help identify and mitigate large-scale attack activities.
Why are SYN Flood Attacks Dangerous?
SYN Flood attacks are dangerous because they can make websites and online services stop working. This can lead to:
- Lost business for companies
- Frustrated users who can't access services
- Damage to a company's reputation
- Potential security breaches if the attack is used to distract from other malicious activities
How to Spot a SYN Flood Attack?
Some signs that you might be under a SYN Flood attack include:
- Your network is very slow
- Websites or services stop working
- You see a lot of half-open connections in your network logs
- There's a sudden increase in SYN packets from many different IP addresses
How to Defend Against SYN Flood Attacks?
Protecting against SYN Flood attacks can be challenging, but here are some strategies:
- Increase Your Resources: While not a long-term solution, having more powerful servers can help you withstand smaller attacks.
- Use Firewalls and Intrusion Detection Systems: These can help identify and block suspicious traffic.
- Implement SYN Cookies: This technique helps servers handle SYN packets more efficiently without running out of resources.
- Rate Limiting: Set limits on how many connections can be made from a single IP address in a given time.
- Blackholing or Sinkholing: Redirect attack traffic to a "black hole" where it's discarded.
- Use a Content Delivery Network (CDN): CDNs can absorb a lot of attack traffic before it reaches your servers.
- DDoS Protection Services: Specialized services can detect and mitigate various types of DDoS attacks, including SYN Floods.
Conclusion
SYN Flood attacks have been around for a long time, but they're still a significant threat to online services. By understanding how these attacks work and implementing proper defenses, you can protect your systems and ensure your services remain available to legitimate users. Remember, cybersecurity is an ongoing process, so stay informed about the latest threats and protection methods to keep your digital assets safe.
For more robust protection, consider using advanced solutions like EdgeOne DDoS protection. This system:
- Monitors network traffic in real-time
- Cleans and filters traffic when it detects an attack
- Uses AI and behavioral analysis to identify and block false requests
- Ensures your services keep running even during an attack
We have now launched a free trial and welcome you to register or contact us for more information.
FAQs
Q1: What is a SYN flood attack?
A1: A SYN flood attack is a type of Denial of Service (DoS) attack that overwhelms a server by sending a large number of SYN requests, creating half-open connections and exhausting server resources.
Q2: How does a SYN flood attack work?
A2: The attacker sends numerous SYN packets to the target server without completing the TCP three-way handshake, causing the server to allocate resources for each incomplete connection until it can no longer respond to legitimate requests.
Q3: What are the consequences of a successful SYN flood attack?
A3: A successful SYN flood attack can crash the target server or make it unresponsive, preventing it from providing services to legitimate users.
Q4: Are there effective ways to prevent SYN flood attacks?
A4: While there aren't many foolproof methods, one of the most well-known and effective techniques is SYN cookies, which help mitigate the impact of SYN flood attacks.
Q5: Can SYN flood attacks be launched using readily available tools?
A5: Yes, there are tools available, such as Python-based SYN flood attack tools, that can be used to launch these attacks, making it relatively easy for attackers to execute such attacks.

