What is the Definition of ETag?
ETag: Entity Tag in HTTP Strong Caching Mechanism
As a unique identifier for versions of a resource, ETag is paramount in optimizing the loading speed of web applications and alleviating server load.
ETag (Entity Tag) is a response header field defined in the HTTP protocol, utilized to uniquely identify a specific version of a resource. The value of ETag is typically generated based on the resource's hash value or content digest, ensuring its uniqueness. This uniqueness allows the server to accurately identify and track different resource versions. This is crucial in maintaining the integrity of the resource and ensuring that the client always receives the most up-to-date version.
An example of an ETag header:
Working Principle of ETag
1. Resource Identification and Response
When a client initially requests a resource, the server converts the resource content into an ETag and returns this value in the HTTP response header. This process involves the computation of a hash or digest of the resource content to generate a unique ETag. This ETag serves as a fingerprint of the resource at a specific point in time, allowing the server to track changes and updates to the resource.
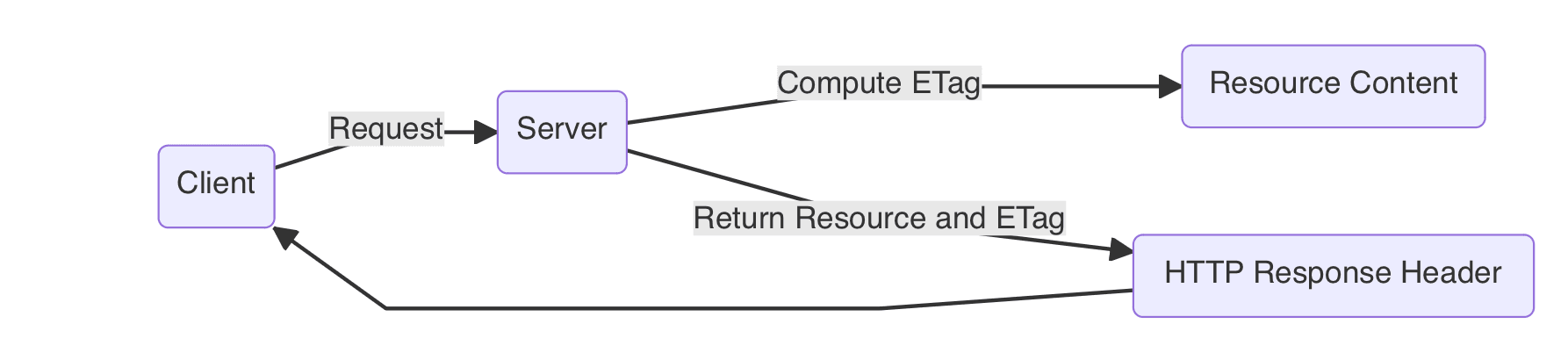
2. Client Caching
Upon receiving the resource and its corresponding ETag, the client stores them in the local cache for future use. This allows the client to use this cache in future requests, instead of fetching the resource from the server each time. This not only saves bandwidth but also improves the speed and efficiency of the client's requests.

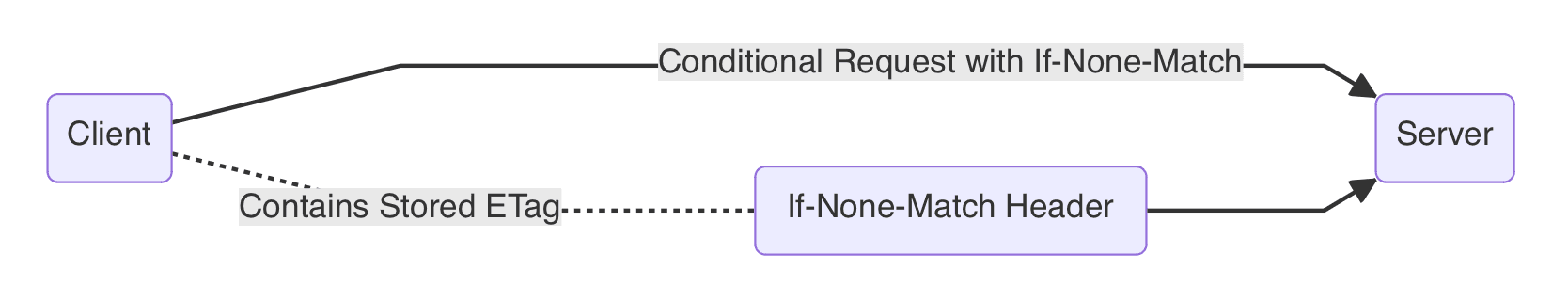
3. Conditional Requests and Validation
When the client needs to request the same resource again, it includes an If-None-Match field in the HTTP request header, the value of which is the previously stored ETag. This is a conditional request, implying that the client only needs a new response if the resource has changed. This mechanism allows the client to avoid unnecessary data transfers and optimizes the use of network resources.
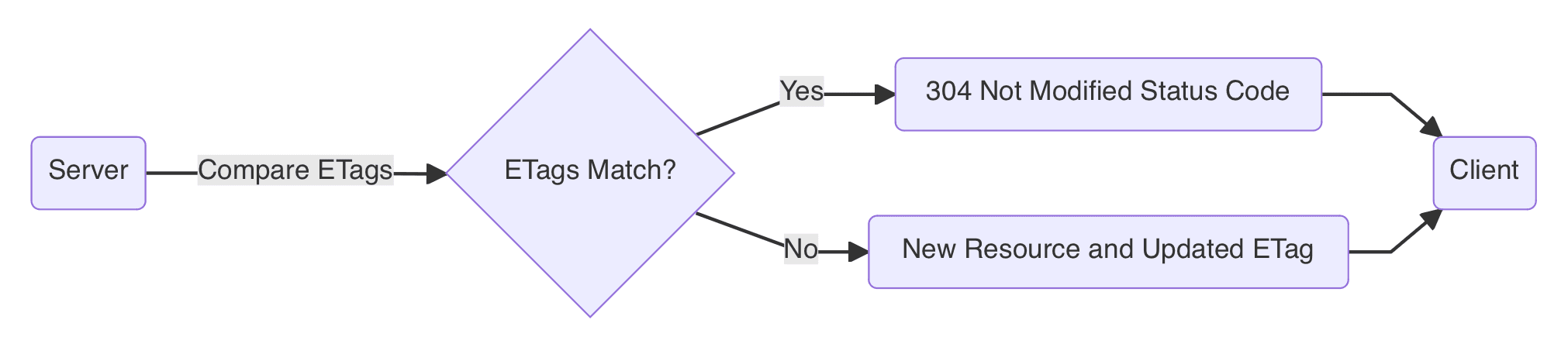
4. Server Response
Upon receiving a request with an If-None-Match, the server compares this value with the current resource's ETag. If they match, the server returns a 304 Not Modified status code, instructing the client to use the local cache; if they do not match, the server returns the new resource and an updated ETag. This mechanism ensures that the client only needs to download new content when the resource has changed, thus optimizing network traffic and server load.
ETag and Strong Caching
Strong caching is an HTTP caching strategy that allows clients to directly use local cached resources without communicating with the server. The role of ETag in this mechanism is as follows:
- Cache Validation: ETag provides a mechanism for clients to verify whether their cached resources are the latest version. This allows the client to ensure it is using the most recent resource without having to download from the server each time. This validation process is crucial in maintaining the integrity of the resource and ensuring that the client always has the most up-to-date version.
- Data Transfer Reduction: Through ETag validation, the server can avoid sending the content of unmodified resources, thus saving bandwidth. This has significant implications for network performance and server load. By reducing unnecessary data transfers, the server can optimize its resources and improve its overall performance.
- Performance Improvement: The ETag mechanism aids in enhancing the response speed and overall performance of web applications. By reducing unnecessary data transfers, ETag can significantly improve page load speeds and user experience. This is particularly important in today's digital age, where speed and efficiency are key factors in the success of a web application.
Considerations in Practice
ETag Generation Strategy
The generation of ETag should consider the frequency and manner of resource changes to ensure the effectiveness and efficiency of caching. For instance, if a resource changes frequently, a content-based ETag might be more effective. This strategy ensures that the ETag accurately reflects the current state of the resource and allows for efficient cache validation.
Weak ETag
A weak ETag, indicated by the prefix 'W/', signifies that the value is not a strong validator but a weak validator. Weak ETags are used when the resource representation has been transformed or modified in a way that makes precise comparison with the original resource impractical. For example, the resource might have been compressed or encoded differently, yet still be equivalent in content to the client. Weak validators are primarily used to detect cases where the representation is functionally equivalent, even if the byte-for-byte comparison would indicate a difference.
Example:
ETag: W/"67ab"In this example, the presence of 'W/' indicates that the ETag is a weak validator. The server may consider two resources with this ETag to be not modified if they are equivalent in a semantic sense, even if their byte representations differ.
Coordination with Last-Modified
ETags can complement the Last-Modified header field to provide a more nuanced caching strategy. The Last-Modified header indicates the date and time at which the resource was last changed, and it is often used as a basis for conditional requests. However, Last-Modified only provides a timestamp, which may not be precise enough for certain use cases.
ETags, on the other hand, offer a more precise method of validation because they are based on the actual content of the resource. When used together, a client can first check the Last-Modified time to determine if a conditional request is necessary, and if so, use the ETag for a more accurate validation.
Example:
If-Modified-Since: Fri, 14 June 2024 07:28:00 GMT
If-None-Match: "3f4d5"In this example, the client sends both an If-Modified-Since header (based on Last-Modified) and an If-None-Match header (based on ETag). The server can use the Last-Modified check as a quick first pass to possibly avoid more expensive ETag calculations, and if the timestamps do not match, it can then use the ETag for a definitive comparison.
Conclusion
Tencent EdgeOne, as a leading edge computing service provider, is committed to delivering outstanding performance and comprehensive security protection for users. In terms of intelligent acceleration, EdgeOne integrates L4 proxy acceleration and L7 intelligent acceleration technology to adapt to various complex business scenarios. Particularly noteworthy is that EdgeOne skillfully utilizes the ETag mechanism in cache management.
ETag, as an HTTP response header, is used to identify the version of resources returned by the server. When a client requests resources, it carries the If-None-Match header containing the ETag value of the previously requested resource. The server compares it with the current resource's ETag to determine whether to return new resources or use the cache.
Leveraging the ETag mechanism, EdgeOne can accurately judge whether resources have changed, thereby avoiding sending unchanged resources to the client, reducing bandwidth consumption, and improving loading speed. This intelligent cache management strategy not only enhances user experience but also helps to reduce the load on the origin server, achieving more efficient resource distribution.
In addition, EdgeOne performs well in terms of security protection. It provides strong DDoS protection capabilities to effectively defend against distributed denial-of-service attacks. At the same time, the auto-updated SSL certificate feature ensures the security of the website, providing users with a secure and reliable access environment.
In summary, Tencent EdgeOne, with its intelligent acceleration, efficient cache management, and excellent security protection capabilities, has become the ideal choice for global users when building and maintaining websites.
You are welcome to Contact Us for more information.

