A Denial of Service (DoS) attack and a Distributed Denial of Service (DDoS) attack are cyberattacks that attempt to disrupt or shut down a targeted server, network, or website by inundating it with a large amount of traffic or requests, making it inaccessible to legitimate users.
Both Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks can inflict considerable harm on businesses and organizations. They can result in revenue loss, reputation damage, and even legal repercussions. To prevent these attacks, organizations typically utilize security measures like firewalls, intrusion detection systems, and traffic filtering.
What is a Dos Attack?
A Denial of Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic. This attack aims to render the website or service unavailable to its intended users by exhausting the target's resources. Unlike other cyber threats that seek unauthorized access to data, the primary objective of a DoS attack is to impede the accessibility of online services, causing inconvenience and potential financial losses to businesses and users alike.
In a DoS attack, a single attacker or system sends a large number of requests or data packets to the target server, network, or website, overwhelming its resources and causing it to crash or become unresponsive. This can be done using various methods, such as flooding the target with traffic, exploiting vulnerabilities, or sending malformed packets.
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack is a more advanced and coordinated form of a DoS attack. Instead of using a single system, the attacker uses multiple compromised systems (often referred to as a botnet) to launch simultaneous attacks on the target. This distributed nature of the attack makes it more challenging to trace the source and defend against it, as the traffic comes from many different sources.
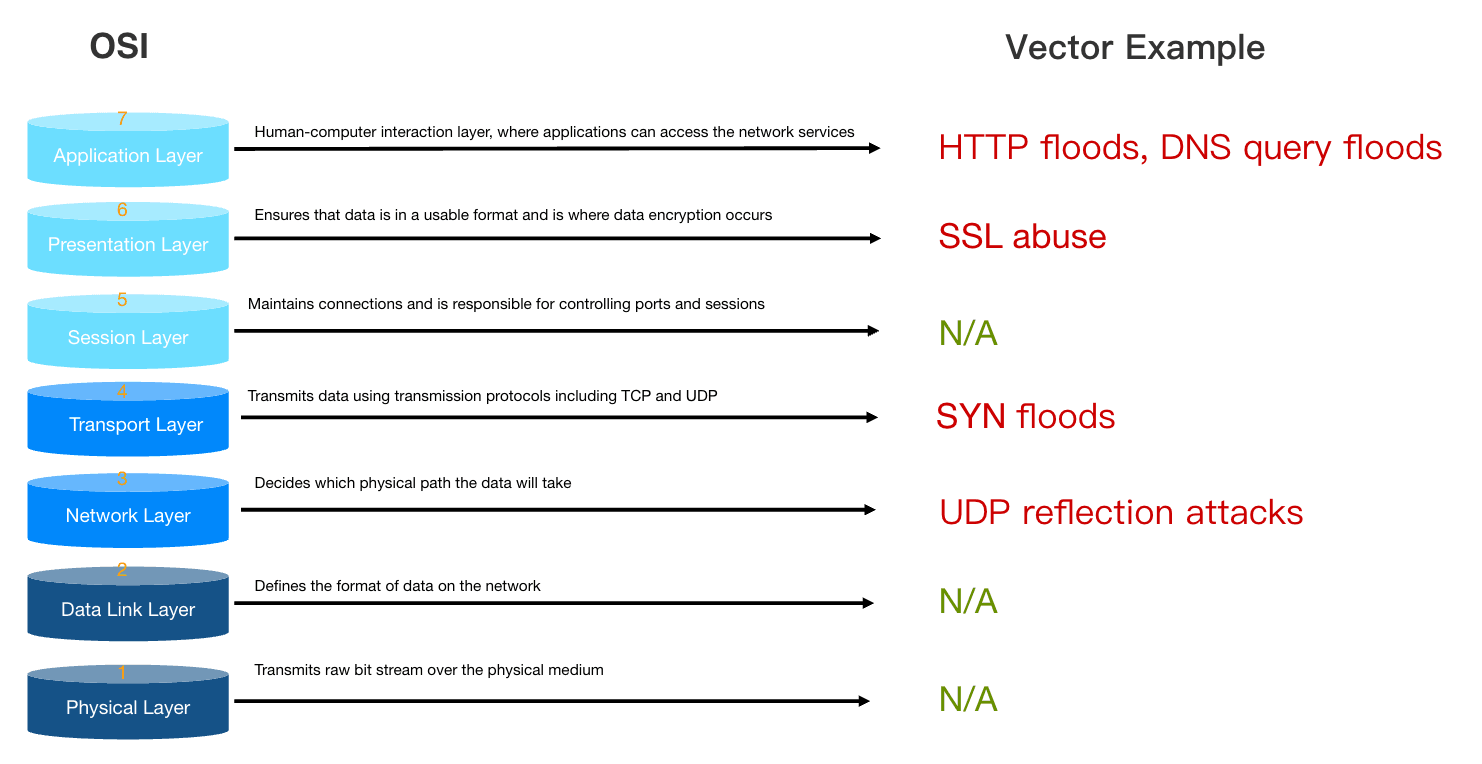
DDoS attacks can be segregated by which layer of the Open Systems Interconnection (OSI) model they attack. They are most common in the Network (layer 3), Transport (Layer 4), Presentation (Layer 6) and Application (Layer 7) Layers.
How does a DDoS Attack Work?
The working principle of a DDoS attack involves using a large number of legitimate or forged requests to occupy the resources of the target server, making it unavailable to legitimate users.
Here's a breakdown of how DDoS attacks work:
- Building a Botnet: Attackers first use malware or other means to infect multiple internet devices, creating a botnet. These compromised devices are then under the control of the attacker.
- Launching the Attack: When the attacker decides to initiate the attack, they send instructions to the botnet, directing the infected devices to send a large number of requests to the target. These requests can be TCP connections, UDP packets, or application-layer requests, such as HTTP requests.
- Consuming Resources: As these numerous requests flood the target, even though they may seem trivial to legitimate users, they can overwhelm the target server's bandwidth, processor, memory, and other resources. This causes the server's performance to degrade, latency to increase, and may even result in complete service unavailability.
- Hiding Identity: Attackers often use proxy servers, virtual private networks (VPNs), or Tor networks to disguise their true IP addresses, in an attempt to evade tracking and investigation.
- Persistent Attacks: DDoS attacks can be persistent or intermittent. During the attack, attackers may continuously adjust their tactics and traffic volume to maintain the effectiveness of the attack.
What are the Types of DDoS Attacks?
When analyzing and classifying attack methods, we categorize the attacks into the infrastructure layer (Layer 3 and Layer 4) and the application layer (Layer 6 and Layer 7). Attacks on Layer 3 and Layer 4 are typically classified as infrastructure layer attacks, which are also the most common types of DDoS attacks. Attacks on Layer 6 and Layer 7 are usually classified as application layer attacks. While these are less common, they tend to be more complex. Compared to infrastructure layer attacks, these attacks are usually smaller in volume.
Based on common attack scenarios, the attack types are categorized as follows:
Protocol Attacks
These attacks target network layer or transport layer protocols, primarily focusing on the 3rd and 4th layers. These are the most common types of DDoS attacks, including Synchronous (SYN) flood attacks and other reflection attacks such as User Datagram Protocol (UDP) flood vectors. These attacks are usually large in number, aiming to overload the capacity of the network or application server. However, these attacks are also the types with clear identifiers and are easier to detect.
This type of attack is like the staff in the supply room receiving requests from the store counter. The staff receives the request, goes to fetch the package, waits for confirmation, and then delivers the package to the counter. The staff receives too many package requests but gets no confirmation, until they can't handle more packages, and are overwhelmed, resulting in no one being able to respond to the requests.
These attacks involve exploiting the TCP handshake, which is a series of communications that two computers go through when initiating a network connection. The attacker sends a large number of TCP initial connection request - SYN packets with spoofed source IP addresses to the target. The target computer responds to each connection request and then waits for the last step in the handshake, but this step never happens, thus exhausting the target's resources. As a result, the attacks consume the resources of servers or network devices such as load balancers and firewalls.
Application Layer Attacks
These attacks focus on specific applications or services, mainly targeting the 6th and 7th layers. They are complex attacks that often resemble normal user traffic. Examples include HTTP floods, slow attacks like Slowloris, and DNS query floods. Although less common, these attacks are often more intricate. In comparison to infrastructure layer attacks, they usually involve fewer instances but pinpoint specific critical areas of the application, rendering it inaccessible to genuine users.
Examples of such attacks involve a high volume of HTTP requests on the login page, resource-intensive search APIs, or Wordpress XML-RPC flooding (also known as Wordpress pingback attacks). It's akin to repeatedly hitting refresh in numerous web browsers, causing a flood of HTTP requests overwhelming the server and resulting in a denial of service. These attacks can be simple or complex. Simple implementations might involve using the same set of attacking IP addresses, referrers, and user agents to access a URL. In contrast, more complex versions may use numerous aggressive IP addresses and employ random referrers and user agents to target random URLs.
Volumetric Attacks
These are the most common types of DDoS attacks, aiming to saturate network bandwidth. The attacker needs to control a large number of 'botnets' to generate enough traffic, trying to create and send a large amount of traffic to make network services unavailable. Examples include UDP floods, ICMP floods, and other indiscriminate amplified traffic attacks. Specific types include:
- SYN Flood: SYN flood is a type of DoS attack that exploits the TCP handshake process by sending numerous SYN requests to a target server, overwhelming its resources and causing it to become unresponsive. This attack prevents legitimate users from establishing connections, leading to service disruptions.
- UDP Flood: The attacker sends a large number of UDP packets to random ports on the target server. The server tries to respond to each packet, eventually exhausting its ability to handle legitimate requests.
- ICMP (Ping) Flood: Using the ICMP protocol, the attacker sends a large number of 'echo requests' (ping requests) to the target system. If the target system responds to all requests, it may be overloaded, preventing legitimate traffic from reaching.
- Other Spoofed Packet Floods: The attacker spoofs IP addresses to send a large number of packets. These packets can be any type of protocol, aiming to consume as much bandwidth as possible.
- Amplification Attacks: The attacker uses protocols with large responses, such as DNS or NTP, to send small query requests and spoof the victim's IP address. Since responses are usually much larger than requests, this results in the victim receiving a large amount of unrequested data.
- DNS Amplification: A specific type of amplification attack, where the attacker uses DNS servers to amplify the attack. The attacker sends small query requests but requests the DNS server to return larger responses to the victim's address.
- NTP Amplification: Similar to DNS amplification attacks, but uses Network Time Protocol (NTP) servers. The attacker requests the NTP server to send time synchronization responses to the victim's IP address.
- Smurf Attack: The attacker sends ICMP requests to the network broadcast address, and all responses are sent to the victim's IP address. This not only exhausts the victim's bandwidth but also affects intermediate network devices.
- Fraggle Attack: Similar to Smurf attacks, but uses UDP instead of ICMP. The attacker sends UDP echo requests to the broadcast address, and all responses are directed to the victim.
Reflection and Amplification Attacks
Attackers exploit third-party servers to amplify attack traffic. For example, NTP amplification, DNS amplification, and SNMP reflection attacks. These attacks forge the victim's IP address, directing the response of the reflection server towards the victim, thereby amplifying the attack traffic. It's like someone calling a restaurant and saying, 'Order one of each dish and call me back to repeat the entire order,' but the callback number belongs to the victim. With little effort, a lengthy response can be generated and sent to the victim. After sending a request to an open DNS server using a forged IP address (the victim's IP address), the target IP address will receive the server's response.
Multi-Vector Attacks
These attacks combine several of the above methods, attacking the target in multiple ways simultaneously. They are harder to defend against because they require dealing with multiple attack surfaces at once.
What Harm can a DDoS Attack Cause?
If a DDoS attack causes business interruption or damage, it will bring huge commercial losses.
- Significant economic loss: After suffering a DDoS attack, the origin server may not be able to provide services, causing users to be unable to access your business, resulting in huge economic losses and brand losses.
- Data leakage: Hackers may take the opportunity to steal your core business data while launching a DDoS attack on your server.
- Malicious competition: Some industries have vicious competition, and competitors may use DDoS attacks to maliciously attack your services, thereby gaining an advantage in industry competition.
Conclusion
Tencent EdgeOne offers robust DDoS protection, leveraging Tencent's extensive global network and advanced security technologies. Key features include:
- Basic DDoS Protection: EdgeOne provides platform-level basic DDoS protection enabled by default. This protection monitors network traffic in real-time and immediately cleans up traffic-based DDoS attacks when detected, offering second-level protection.
- Advanced Security Policies: The default DDoS protection includes security policies based on attack profiles, behavior pattern analysis, AI intelligent recognition, and other protection algorithms, effectively dealing with common DDoS attack behaviors.
- Enhanced HTTP Security Features: To protect web services, EdgeOne offers various HTTP security features. These include defenses against high-frequency DDoS attacks that cause a decline in origin availability, custom rules to block specified IP lists or subnet lists, and restrictions on the allowed access service area.
- Exclusive DDoS Protection: For scenarios where the default protection is not sufficient, EdgeOne provides a paid feature for exclusive DDoS protection. This includes exclusive access to the cleaning center and a high-defense IP for traffic cleaning, with protection bandwidth based on the purchased capacity.
By using Tencent EdgeOne DDos Protection, businesses can ensure the availability and performance of their online services, even in the face of large-scale DDoS attacks. We have now launched a free trial, welcome to contact us for more information.

