Understanding CDN Theft: An In-Depth Analysis
Content Delivery Networks (CDNs) have become an essential part of the modern internet infrastructure, enabling faster content delivery, improved website performance, and enhanced user experiences. However, as with any technology, CDNs are not immune to security threats. One of the most concerning issues is CDN theft, which can lead to significant data breaches, financial losses, and reputational damage for businesses. In this article, we will explore the concept of CDN theft, its types, causes, and effective solutions to mitigate the risks associated with it.
What is CDN Theft?
CDN theft, also known as CDN abuse, refers to the unauthorized use or exploitation of a Content Delivery Network (CDN) to access, distribute, or manipulate content without proper authorization. CDNs are designed to enhance the performance and availability of web content by caching it on multiple servers distributed across various geographical locations. While CDNs provide significant benefits, such as faster load times and reduced server load, they can also be vulnerable to various forms of abuse.

Types of CDN Theft
Data Theft
Data theft involves the unauthorized access and extraction of sensitive information stored on a CDN. This can include user credentials, payment information, and proprietary business data. Attackers may exploit vulnerabilities in the CDN's security protocols to gain access to this information.
Session Hijacking
Session hijacking occurs when an attacker takes control of a user's active session, allowing them to impersonate the user and access their account without authorization. This can happen if the CDN does not properly secure session tokens or if the tokens are intercepted during transmission.
Content Manipulation
In content manipulation attacks, an attacker alters the content delivered through the CDN. This can involve injecting malicious scripts, changing images, or redirecting users to phishing sites. Such attacks can damage a brand's reputation and lead to loss of customer trust.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks can also be considered a form of CDN theft. In this scenario, attackers overwhelm the CDN with traffic, rendering it unable to deliver content to legitimate users. While this does not involve stealing data, it disrupts services and can lead to significant financial losses.
Causes of CDN Theft
Understanding the causes of CDN theft is crucial for developing effective prevention strategies. Here are some common causes:
Misconfigured Security Settings
One of the primary causes of CDN theft is misconfigured security settings. Many organizations fail to properly configure their CDN's security features, leaving vulnerabilities that attackers can exploit. This includes inadequate access controls, weak authentication mechanisms, and improper SSL/TLS configurations.
Insecure APIs
APIs are essential for enabling communication between different systems, but they can also be a weak point in security. If a CDN's API is not properly secured, attackers can exploit it to gain unauthorized access to sensitive data or manipulate content.
Lack of Encryption
Data transmitted over the internet should always be encrypted to protect it from interception. If a CDN does not enforce encryption for data in transit, attackers can easily capture sensitive information, leading to data theft.
Social Engineering Attacks
Social engineering attacks, such as phishing, can trick employees into revealing their credentials or other sensitive information. If attackers gain access to an organization's CDN account through social engineering, they can carry out various malicious activities.
Software Vulnerabilities
Like any software, CDNs can have vulnerabilities that attackers can exploit. These vulnerabilities may arise from outdated software, unpatched security flaws, or third-party integrations that introduce risks.
Solutions to Mitigate CDN Theft
To protect against CDN theft, organizations must implement a multi-layered security approach. Here are some effective solutions:
1. Configure Security Settings Properly
Organizations should ensure that their CDN's security settings are configured correctly. This includes setting up strong access controls, enabling two-factor authentication, and regularly reviewing permissions to ensure that only authorized users have access to sensitive data.
2. Secure APIs
APIs should be secured using best practices, such as implementing authentication and authorization mechanisms, validating input data, and monitoring API usage for suspicious activity. Organizations should also consider using API gateways to manage and secure API traffic.
3. Enforce Encryption
All data transmitted between users and the CDN should be encrypted using SSL/TLS. Organizations should ensure that their CDN provider enforces HTTPS and that all content is served securely. Additionally, sensitive data stored on the CDN should also be encrypted.
4. Educate Employees
Employee training is crucial for preventing social engineering attacks. Organizations should conduct regular training sessions to educate employees about the risks of phishing and other social engineering tactics. Employees should be encouraged to report suspicious emails or activities.
5. Regularly Update Software
Organizations should keep their CDN software and any associated applications up to date. Regularly applying security patches and updates can help protect against known vulnerabilities. Additionally, organizations should conduct regular security audits to identify and address potential weaknesses.
6. Monitor for Suspicious Activity
Implementing monitoring tools can help organizations detect suspicious activity related to their CDN. This includes monitoring for unusual access patterns, failed login attempts, and changes to content. Organizations should have an incident response plan in place to address any security breaches promptly.
7. Use a Reputable CDN Provider
Choosing a reputable CDN provider with a strong security track record is essential. Organizations should evaluate potential providers based on their security features, compliance with industry standards, and incident response capabilities. A reliable CDN provider will have robust security measures in place to protect against CDN theft.
Reliable CDN Provider: Tencent EdgeOne
Tencent EdgeOne stands out as a reliable CDN provider, offering robust security features, high performance, and extensive global coverage. With its advanced technology and commitment to delivering exceptional user experiences, Tencent EdgeOne effectively addresses the challenges of content delivery while ensuring data protection. You can trust Tencent EdgeOne to enhance their online presence, improve website performance, and safeguard sensitive information against potential threats.
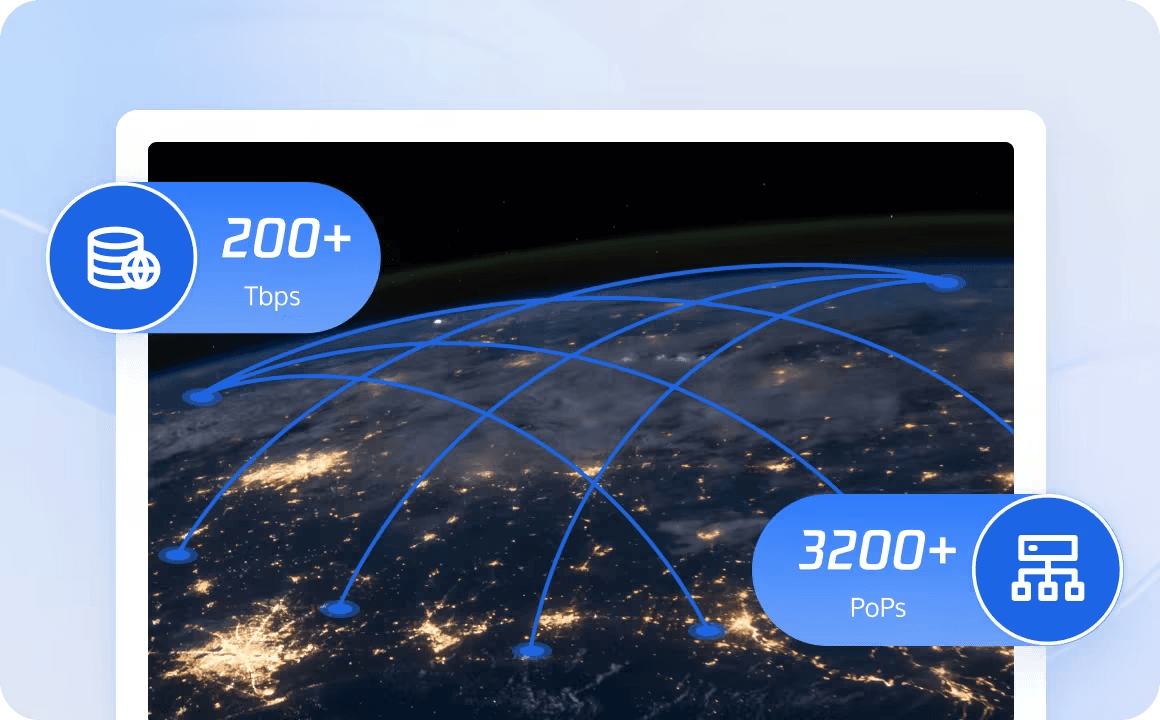
Key features of Tencent EdgeOne's CDN:
- 3200+ Global Edge Nodes: EdgeOne has more than 3,200 edge nodes in more than 70 countries and regions around the world. The global edge nodes, multi-layer architecture and direct connection lines to core nodes provide high-quality network performance guarantees.
- Global Intelligent Scheduling: By monitoring network links and utilizing its custom GSLB scheduling system and intelligent routing technology, CDN directs user access to optimal edge nodes for accelerated, stable resource access.
- One-stop Management: EdgeOne's next-generation edge architecture, with its high integration of security and acceleration capabilities, significantly reduces management and usage costs through its comprehensive one-stop service.
If you have any questions or need assistance online, our support team is always ready to help. Please feel free to Contact us or join us on Telegram.