Bandwidth Abuse Protection
Overview
Bandwidth abuse refers to the malicious behavior of repeatedly accessing site resources through PCDN platforms or automation tools, resulting in a waste of bandwidth resources. Static resources are the main target of bandwidth abuse attacks. Images or data packages to be downloaded may be subjected to numerous crawler requests, leading to repeated downloads of resources, generating hefty download traffic bills, and even resulting in arrears and service suspension. Bandwidth abuse protection provides preset security policy options to mitigate or reduce the impact of bandwidth abuse.
Use of Bandwidth Abuse Protection
EdgeOne provides bandwidth abuse protection policies, which enable recognition and extraction of bandwidth abuse request features based on platform-wide traffic analysis to form a bandwidth abuse database. This database is used for automatic matching and interception of high-risk bandwidth abuse requests. The bandwidth abuse database is updated every 24 hours to cover the latest bandwidth abuse features.
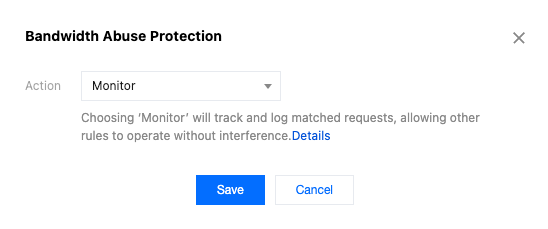
Bandwidth abuse protection supports Monitor, Block, and JavaScript Challenge actions. Choose an appropriate option based on business compatibility. For details, see Action.
Note:
The intelligence database only covers traffic theft behavior targeting sites in the Chinese mainland
When the bandwidth abuse protection feature is enabled for the first time, it is recommended to use the Monitor action for evaluation. After evaluating the matching situation through metric analysis and web security analysis, you can choose Block.
If your domain name service has enabled bot management, bandwidth abuse protection will use TLS fingerprint technology to further improve the recognition accuracy of distributed bandwidth abuse crawlers.
If you find that normal traffic is mistakenly blocked by the bandwidth abuse protection feature, configure protection exception rules to restore access by blocked normal clients.
Note:
Since the bandwidth abuse protection feature recognizes high-risk requests based on historical information, there may be an information lag when bandwidth abuse behavior changes. If you believe that bandwidth abuse attacks are still bypassing the protection after the bandwidth abuse protection policy is enabled, consider the following mitigation methods:
Contact technical support. We will analyze the request traffic as soon as possible and update the policy.
In web protection, configure custom rate limiting rules to recognize and block clients that repeatedly access static resources by using statistical dimensions such as client IP addresses and request URLs.
In bot management, configure bot intelligent analysis to dynamically recognize crawlers' access behavior and mitigate the impact of bandwidth abuse. (A plan for the standard edition or above is required. For details, see Comparison of EdgeOne Plans.)
Directions
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. Click Security Protection > Web Protection. The default is site-level security policy. If you need to configure a differentiated protection policy for a specific domain name under the current site, go to the Domain-level security policy tab, click the corresponding domain name to go to the domain-level security policy configuration page, and follow the same subsequent steps.
3. Locate the Rate Limiting card and click Edit on the right side of Bandwidth Abuse Protection.
4. Choose the action for bandwidth abuse protection. It is recommended to choose Monitor initially. After evaluating the matching situation through metric analysis and web security analysis, you can choose Block.