CC attack defense
Overview
Collapse Challenge (CC) attack, also known as HTTP/HTTPS DDoS attack. Attackers occupy the connection and session resources of Web services, causing the service to be unable to respond to user requests normally, resulting in denial of service. To avoid CC attacks, EdgeOne provides a pre-set CC attack protection strategy and enables it by default to ensure the stability of your site online.
Note:
The primary objective of CC attack protection is to ensure the availability of services. For security scenarios that do not lead to errors at the origin server or a decrease in site availability, such as resource scraping, bulk logins, and automated shopping cart orders, please fortify your security policies further by using Rate Limiting and Bot Management.
EdgeOne adopts a "clean traffic" billing model, meaning that requests intercepted by the security protection features are not charged. Charges are only applied to the traffic and request volume processed after the security protection features. For the definition of the "clean traffic" billing model, see Tencent Cloud EdgeOne.
Using Platform-Managed Rate Limiting
Platform-managed rate limiting identifies CC attacks through rate baseline learning, header feature statistical analysis, and client IP intelligence, then takes action. EdgeOne provides three pre-set CC attack protection strategies:
Adaptive frequency control: Used to deal with CC attack behavior that occupies server resources through high-frequency and large amount of concurrent connection requests, and can limit access frequency based on a single IP source.
Slow attack protection: Used to deal with CC attack behavior that occupies server resources through a large amount of slow connection requests, and can limit access connection minimum rate based on a single session, eliminating slow connection clients.
Intelligent client filtering: Integrates rate baseline learning, header feature statistical analysis, and client IP intelligence to generate real-time dynamic attack defense rules. Perform human-machine verification for requests from high-risk clients or carrying high-risk header features. Intelligent client filtering is enabled by default and executes JavaScript challenges for clients that meet the rules.
Adaptive Frequency Control
Adaptive frequency control establishes and updates the rate baseline by continuously monitoring and analyzing your website's traffic pattern. The system counts the current domain name's request rate based on the configuration, establishes the rate baseline based on the last 7 days of requests (updated every 24 hours), and limits the request rate of a single client accessing the domain name according to the configured limitation level.
Note:
Adaptive frequency control is suitable for web-based business. For sites providing high-frequency API services, to avoid normal high-frequency requests being mistakenly blocked, it is recommended to avoid using moderate and emergency limitation levels. Configure protection exception rules for APIs requiring support for high-frequency access to bypass the CC attack protection module, and configure custom rate limiting rules to precisely limit the exposure of APIs.
Directions
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. Click Security > Web Protection. By default, it is a site-level security policy. To configure differentiated security policies for a specific domain name under the current site, you can enter the Domain-level security policy tab and click the corresponding domain name to enter the configuration page for the domain-level security policy. The subsequent steps are the same.
3. Locate the Rate Limiting tab and click Edit on the right side of Adaptive frequency control.
4. Configure the limiting level and action for high-frequency Access request limiting. A description of each limitation level and rate threshold is as follows:
Limitation Type | Limitation Level | Applicable Scenarios | Initial Access Rate Limit |
Adaptive | Loose (Default Configuration, Suggested) | Applicable to most web business scenarios that do not require real-time data interaction or queries. | 2,000 times / 5 seconds |
| Moderate | Applicable to business scenarios with simpler page content and less dynamic data or dynamic loading content. | 200 times / 10 seconds |
| Emergency | Applicable to web scenarios that mainly provide static contents. When an attack occurs or other restriction levels cause business impact, this restriction level can be selected for emergency protection. Due to the strict rate limit of this level, there may be a risk of accidental killing, its long-term use is not recommended. | 40 times / 10 seconds |
Note:
The action of Adaptive Frequency Control supports observation and JavaScript challenge methods. For more information on different action methods, see action.
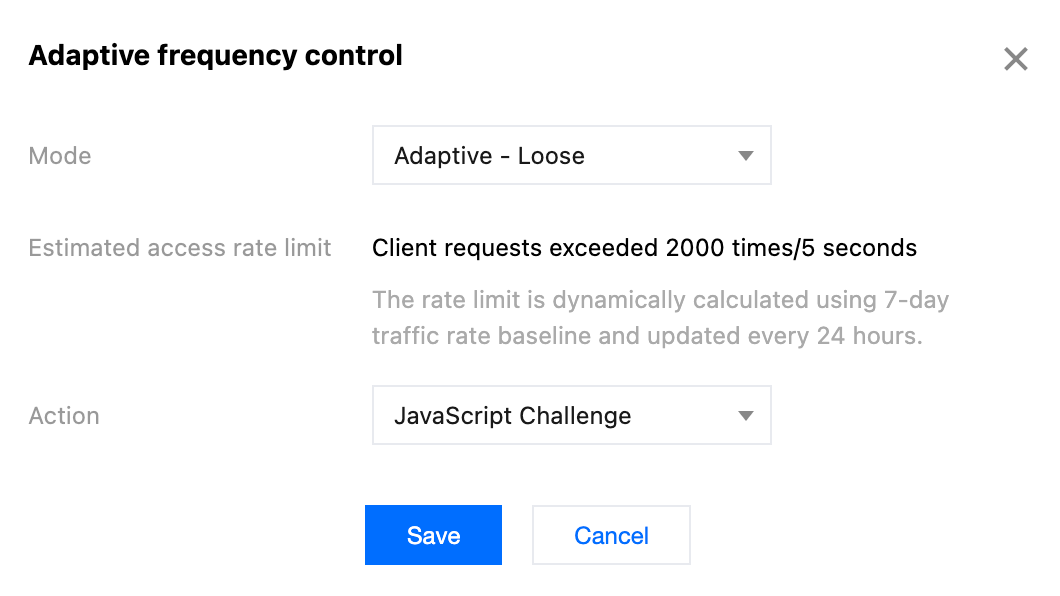
5. Click Save to complete the rule configuration.
Viewing access rate limit of the Domain
Operation Steps
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. Click Security > Web Protection. By default, it is a site-level security policy. To configure differentiated security policies for a specific domain name under the current site, you can enter the Domain-level security policy tab and click the corresponding domain name to enter the configuration page for the domain-level security policy. The subsequent steps are the same.
3. Locate the Adaptive Frequency Control card, and click View on the left of Adaptive rate limit.
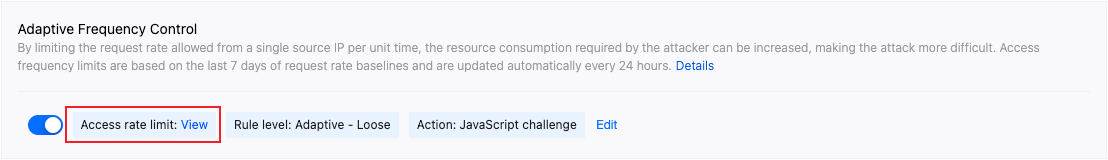
4. View the access rate limit corresponding to the associated domain name of the current protection policy in the pop-up window.
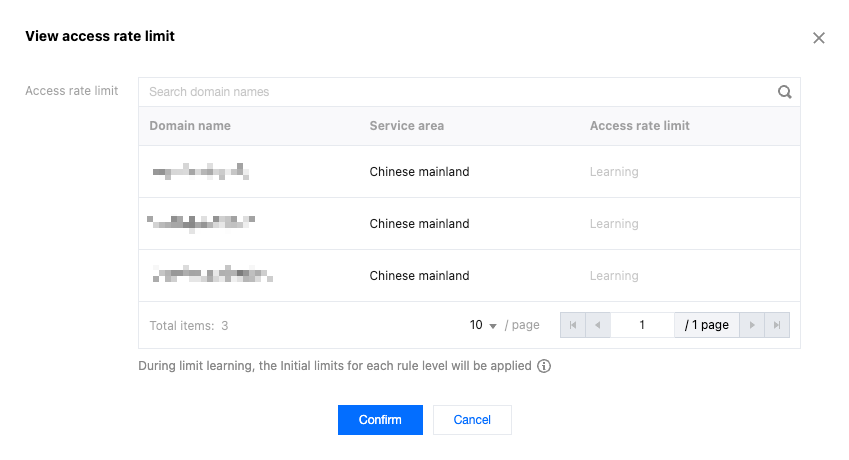
Note:
During the learning period, the initial threshold of each restriction level will continue to be used.
Baseline Calculation and Update Method
Adaptive frequency control calculates the current domain request rate based on the configured restriction level and dynamically generates a rate baseline using the daily peak traffic from the past 7 days. The baseline updates every 24 hours, always calculating based on the most recent 7 days of traffic data.
Adaptive rate control uses a distributed statistical approach. Each EdgeOne node tracks request rates per client IP and enforces rate limiting based on the threshold range for the current limit level. Due to the distributed nature of the statistics, the total request rate aggregated to the origin server may exceed the configured limit.
Enabling Suggestions
To fully leverage the advantages of adaptive frequency control, we recommend following the progressive enabling method below:
1. Initial configuration: Enable adaptive frequency control and select the " Adaptive - Loose " level, with the action being Monitor . The loose level is suitable for most web business scenarios. Its higher initial access rate limit can effectively reduce the risk of false interception, while providing ample space for the system to learn your traffic pattern.
2. Learning period (7 days is recommended): During this phase, the system will deeply analyze your traffic pattern, count the source IP access rate based on historical access traffic with a 24-hour update cycle, and gradually establish an accurate rate baseline.
3. Policy optimization: After the learning period, the system will have established a relatively accurate traffic baseline. You can view the traffic hitting adaptive frequency control in Web Security Analysis, and decide whether to adjust or tighten the policy according to the protection effect and business needs.
Viewing the Traffic Hitting Adaptive Frequency Control
To view the traffic hitting adaptive frequency control rules:
1. Log in to the EdgeOne console and click Web Security Analysis in the left sidebar.
2. Select the time period from the initial access to adaptive frequency control to the current time as the learning period .
3. Click Add Filter and select Web Protection - CC Attack Protection Rule equal to Adaptive Frequency Control .
4. Click OK to apply the filter conditions and observe the protection effect in Statistical Trends and Statistical Details .
Functional Limitations and Solutions
Adaptive frequency control may require additional adjustments in certain special cases:
1. Low-frequency attacks: When the attack frequency is below the lower limit of the set limitation level, adaptive frequency control may not achieve effective interception. In this case, it is recommended to use web security analysis for identifying and locating low-frequency attack behaviors, such as accessing specific sensitive pages/APIs multiple times in a row, and intercept requests that meet the characteristics according to custom rules or custom rate limiting rules.
2. Legitimate high-frequency access: Legitimate high-frequency access (such as API calls) may exceed the upper limit of adaptive frequency control and be mistakenly intercepted. For business types that require real-time client data queries such as retail, e-commerce, and game platforms, and scenarios like travel, ticketing, and open third-party API services, it is recommended to disable the adaptive frequency control feature to avoid false interception.
3. Special business scenarios: During major events such as game updates, promotional activities, and ticket sales, adaptive rate control may affect the normal access peak in a short period. When short-term access behavior significantly differs from the norm, it is recommended to disable the adaptive rate control feature to avoid false interception. You can use custom rules and custom rate limiting rules for precise protection according to multi-dimensional characteristics.
Configure Slow Attack Protection
By limiting the minimum data rate and setting timeout, mitigate the consumption of site resources in slow transmission attack scenarios, and avoid the decline of service availability. EdgeOne slow attack protection supports content transmission timeout and minimum content transmission rate options. When the content transmission rate is slow or there is no data transmission for a long time, apply the corresponding action to the client.
Directions
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. Click Security > Web Protection. By default, it is a site-level security policy. To configure differentiated security policies for a specific domain name under the current site, you can enter the Domain-level security policy tab and click the corresponding domain name to enter the configuration page for the domain-level security policy. The subsequent steps are the same.
3. Locate the Rate Limiting tab and click Edit on the right side of Slow attack defense.
4. Configure the matching method for slow attack protection rules, and choose from the following limitations:
Content transmission duration: Mitigate slow attacks that occupy connections without transmitting content data. Specify the content transmission timeout duration, and clients that fail to complete the transmission of the first 8KB of content data within the configured time will apply the corresponding action; the supported configuration is 5-120 seconds.
Minimum content transmission rate: Mitigate attacks that occupy connections and session resources by transmitting content at an extremely slow rate. Specify the minimum transmission rate, and when the content transmitted within the statistical time window is less than the configured rate, apply the corresponding action. The minimum supported transmission rate is 1 bps, and the maximum is 100 Kbps.
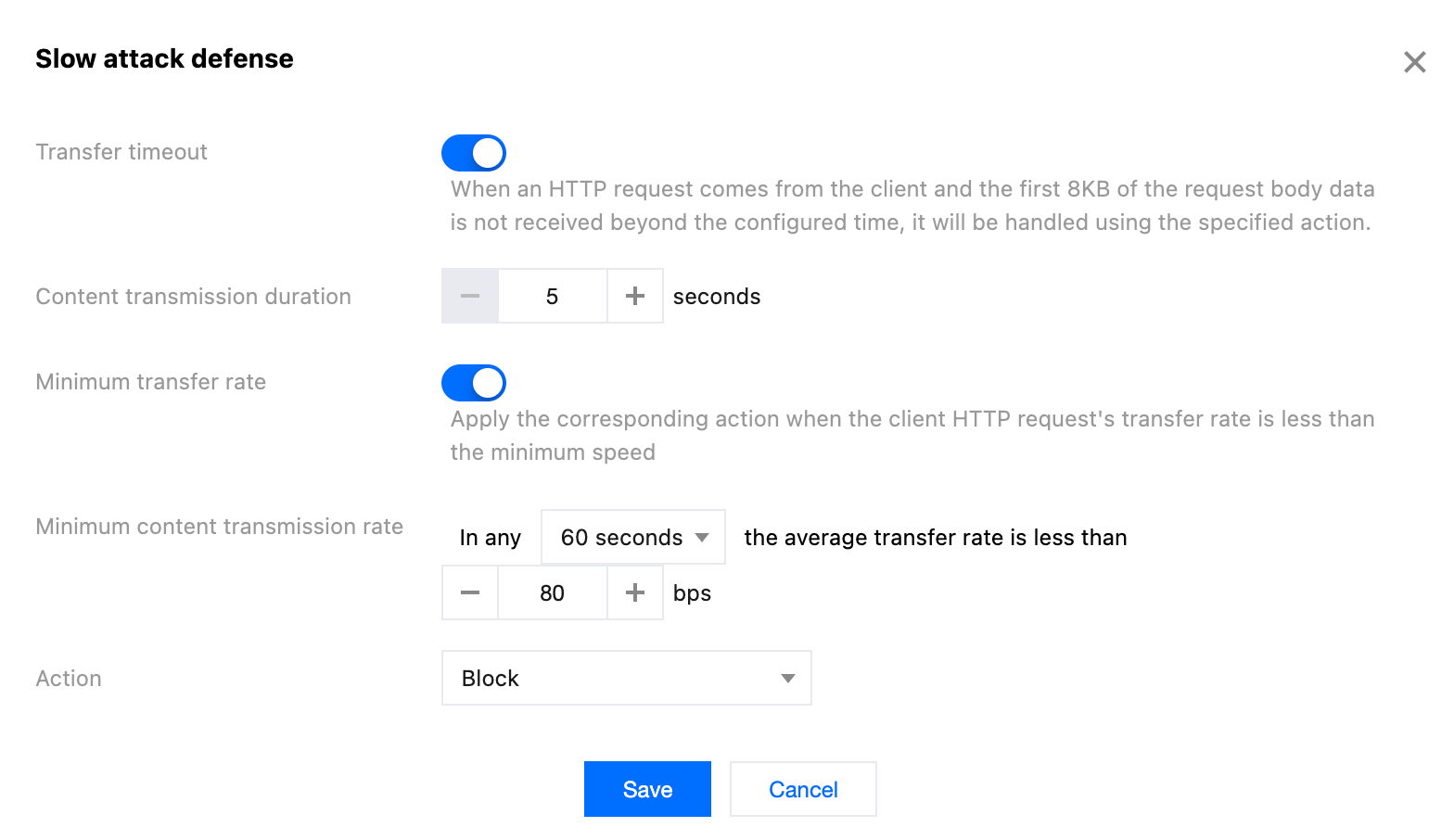
Note:
The action of Slow Attack Protection supports observation and JavaScript challenge methods. For more information on different action methods, see action.
5. Click Save to complete the rule configuration.
Intelligent Client Filtering
Intelligent client filtering integrates rate baseline learning, request header feature statistical analysis, and client IP intelligence to dynamically generate protection rules in real-time. It performs real-time human-machine recognition for traffic from high-risk clients or carrying high-risk request header features. Intelligent client filtering is enabled by default and performs JavaScript challenges for clients that meet the rules.
Intelligent client filtering is an advanced protection mechanism that integrates rate baseline learning, request header feature analysis, and client IP reputation evaluation technology. This feature can dynamically generate protection rules in real-time and perform real-time human-machine identification for traffic from high-risk clients or carrying high-risk request header features. Intelligent client filtering is enabled by default and automatically implements JavaScript challenges for suspicious clients that meet the rules.
Note:
Intelligent client filtering uses the business rate baseline as one of the references. When significant changes (new business access, traffic switching, new feature launch, or marketing activities) occur in the business, changes in the baseline may lead to false interception. It is recommended to temporarily adjust the action to "Monitor" in such cases, and enable it once the business traffic stabilizes.
Intelligent client filtering is only supported by the Standard plan and Enterprise plan.
Policy Mechanism
Intelligent client filtering uses real-time learning algorithms to continuously analyze the request traffic of the past 1 - 12 hours, and establishes and stores the baseline model of normal user traffic. When abnormal traffic is detected, the system analyzes the aggregation of current request features and compares it with historical traffic to identify potential abnormal traffic and take corresponding action.
Modify the Action Method for Intelligent CC Attack Protection
If you need to modify the action method triggered by intelligent client filtering, you can follow these directions:
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. Click Security > Web Protection. By default, it is a site-level security policy. To configure differentiated security policies for a specific domain name under the current site, you can enter the Domain-level security policy tab and click the corresponding domain name to enter the configuration page for the domain-level security policy. The subsequent steps are the same.
3. Locate the Rate Limiting tab and click Edit on the right side of Client filtering.
4. Configure the actions.
Note:
Intelligent client filtering supports four actions, including Disable (Not Enable), Monitor and JavaScript Challenge. For more information on different actions, see Action.
5. Click Save to complete the rule configuration.
Note:
View the requests that match the intelligent client filtering rules. For details, see Web Security Analysis.
Viewing the Traffic Hitting Intelligent Client Filtering Rules
To view the traffic hitting intelligent client filtering rules:
1. Log in to the EdgeOne console and click Web Security Analysis in the left sidebar.
2. Click Add Filter and select Web Protection - CC Attack Protection Rule equal to Intelligent Client Filtering .
3. Click OK to apply the filter conditions and observe the protection effect in Statistical Trends and Statistical Details .
Functional Limitations and Solutions
Intelligent client filtering may require additional adjustments in certain special cases:
Business traffic fluctuates drastically: In scenarios such as large-scale attacks, major business activities, or other situations causing significant traffic pattern changes, intelligent client filtering may require a learning period of 4 to 24 hours to achieve optimal protection. During this period, it is recommended to use custom rules or custom rate limiting rules to enhance protection.