Step 1: Configure Authentication Method
Overview
This document introduces how to configure attestation methods on EdgeOne. These configurations determine which attestation process the client needs to complete to obtain corresponding credentials. In addition to preset attestation methods, EdgeOne also offers multiple attestation method options, such as using Tencent Cloud Captcha and Tencent Cloud Risk Control Engine (RCE). Businesses can select the suitable type based on risk control requirements.
Note:
Before configuring client attestation rules, please first refer to the process in this document to create a custom verification method, configure associated information, valid period (TTL), and related parameters.
Using Attestation Methods
EdgeOne provides two types of attestation method options: preset and custom. Before configuring a custom verification method, ensure that the corresponding attestation configuration instance is already in the related product creation.
Presetting an Attestation Method
EdgeOne provides the following preset attestation methods, which can be used directly without integrating the SDK:
JavaScript challenge: used to check whether the client accessing the Web page has a JavaScript runtime environment.
Hosted challenge: used to check whether the client accessing the Web page is a browser and operated by a human. The hosted challenge process includes verification code mechanisms such as slider challenges.
Note:
JavaScript challenge and managed challenge use interstitial challenge method, not suitable for API service or AJAX architecture webpage.
Custom Verification Method
You can use custom verification methods to control client access to EdgeOne sites with more diverse risk control capabilities. After completing the custom verification method configuration, you can specify the custom verification method in client attestation rules. EdgeOne will automatically require clients to provide designated attestation credentials within the validity period according to your configuration, achieving risk control impact. When using custom verification methods, you need to configure the following options:
Provider: The provider of risk control capability. Your client will perform independent client attestation with the provider and obtain credentials. (Currently supported options: Tencent Cloud Captcha and Tencent Cloud Risk Control Engine)
Attestation configuration information: Used to associate detailed attestation configurations, which include the unique identifier and attestation parameters provided by the provider for your risk control settings. (For example, Tencent Cloud Captcha provides a unique APPID and SecretKey for each configuration item.) EdgeOne will use the configuration information you provide to obtain attestation credentials and verification results.
Valid period TTL: The valid duration of the attestation result. After TTL expires, it will no longer be accessible through client attestation, and the client must re-execute the attestation process. Reasonably setting TTL can balance user experience and security.
Scenario Example
Perform security attestation for clients accessing the login API of site
www.example.com. H5 clients, iOS, and Android mobile devices must utilize existing Tencent Cloud verification code instances for validation in advance when accessing the login API. High-risk client access is blocked. If repeated visits to the login API exceed 2 hours, re-validate the client.Operation Steps
Note:
1. Before performing the operation steps here, please ensure you have created a
CAPTCHA instance in the Tencent Cloud Captcha.2. To perform client attestation by using Tencent Cloud risk identification RCE, create a
risk control policy instance in the Tencent Cloud Risk Control Engine console in advance.3. After completing the configuration steps in this document, proceed to configure client attestation rules.
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the configured site under Secure Content Delivery Network.
2. Click Security Protection > Client Attestation. Click the Attestation Options tab , and under Custom Verification, click Add Attester to enter the attestation integration access configuration interface.
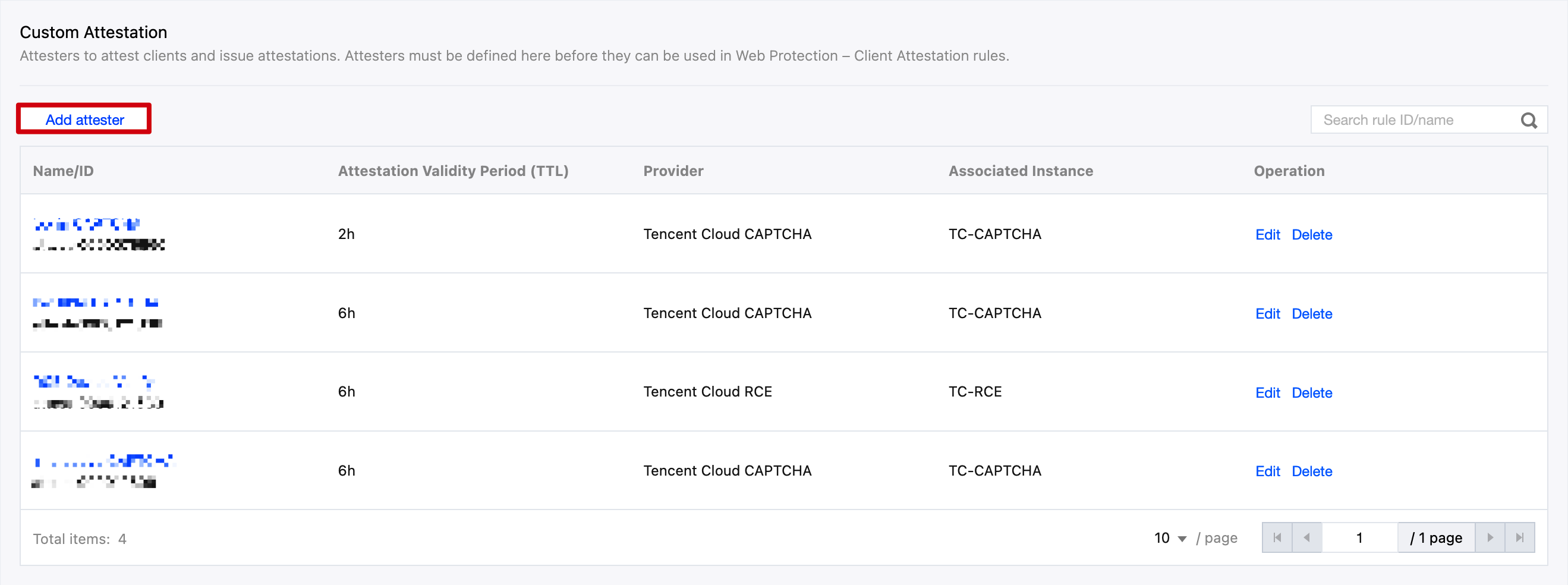
3. Fill in the attestation name, select the attestation provider and enter related instance configuration information. For example, for Tencent Cloud verification code, select Provider and choose
Tencent Cloud verification code as the attestation provider, then fill in the AppID and SecretKey provided by the Tencent Cloud Captcha console. In attestation options, select a 300-second valid duration.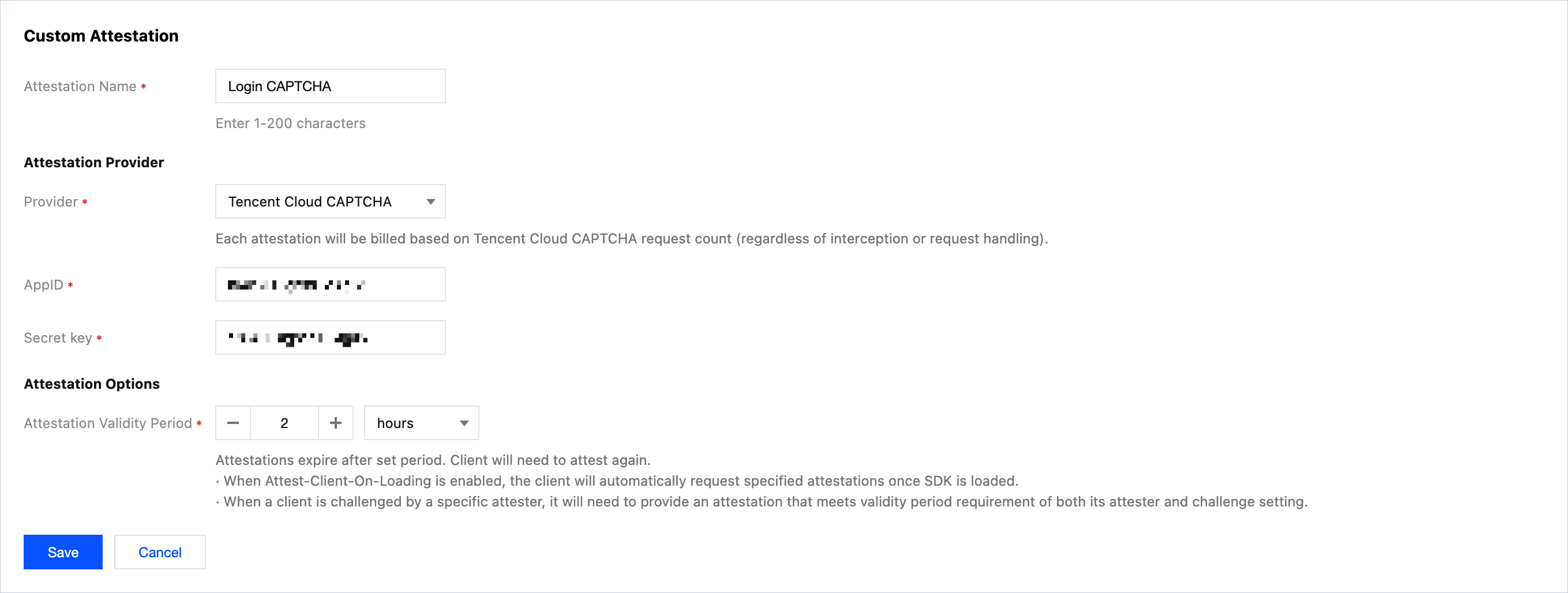
4. Click save and publish to deploy the rule, then proceed to configure client attestation rules.