Certificate Format Requirements
If your certificate is issued by a root certificate authority (CA), you will get a unique certificate. The configured site will be considered trustworthy by access devices such as browsers without the need for additional certificates.
If your certificate is issued by an intermediate CA, you will receive a file containing multiple certificates. You need to manually concatenate the intermediate certificate and the root certificate in order before uploading. The concatenation rule is: first put the intermediate certificate and then put the root certificate, with no blank lines between them.
Note:
In general, CA will provide corresponding instructions when issuing certificates. Pay attention to such instructions.
Examples of CA Certificate Format and Certificate Chain Format
Below are examples of certificate format and certificate chain format. Confirm that the formats are correct before uploading:
1. The example of the PEM format of the certificate issued by a root CA is as follows:
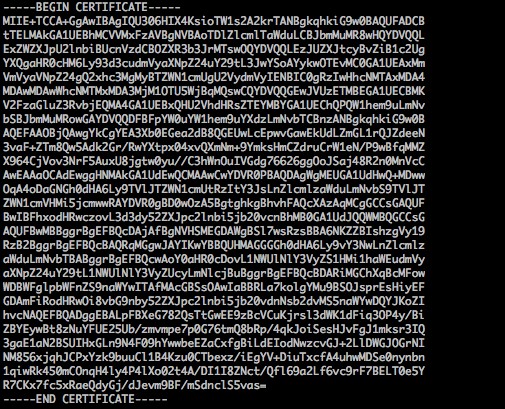
The certificate format is as follows:
Your certificate should start with "-----BEGIN CERTIFICATE-----" and end with "-----END CERTIFICATE-----".
Each line should contain 64 characters, with the last line containing no more than 64 characters.
2. If the certificate is issued by an intermediate CA, the CA certificate needs to include a multi-level certificate chain. The certificate chain structure is as follows:
-----BEGIN CERTIFICATE-----Intermediate CA-----END CERTIFICATE----------BEGIN CERTIFICATE-----Root CA-----END CERTIFICATE-----
The certificate chain rules are as follows:
There should be no blank lines between certificates.
All certificates should meet the certificate format requirements mentioned above.
Instructions for Converting Certificates to PEM Format
Generally, HTTPS certificates are in PEM format. For certificates in other formats that need to be converted to PEM format, it is recommended to use the OpenSSL tool for conversion. Below are methods to convert several popular certificate formats to PEM format.
The DER format is generally used on Java platforms.
Certificate conversion:
openssl x509 -inform der -in certificate.cer -out certificate.pem
Private key conversion:
openssl rsa -inform DER -outform PEM -in privatekey.der -out privatekey.pem
The P7B format is generally used on Windows Server and Tomcat.
Certificate conversion:
openssl pkcs7 -print_certs -in incertificat.p7b -out outcertificate.cer
You need to get the content between "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----" in outcertificate.cer to upload as certificate.
Private key conversion: Private keys can generally be exported on IIS servers.
The PFX format is generally used on Windows Server.
Certificate conversion:
openssl pkcs12 -in certname.pfx -nokeys -out cert.pem
Private key conversion:
openssl pkcs12 -in certname.pfx -nocerts -out key.pem -nodes```
You can convert certificates in CER/CRT format by directly modifying their file extensions. For example, you can directly rename the "servertest.crt" certificate file as the "servertest.pem" certificate file.