Configuring EdgeOne Security Event Alarms via TCOP
Background
EdgeOne, in collaboration with Tencent Cloud Observability Platform (TCOP), offers flexible alarm solutions for security events such as denial-of-service (DDoS) attacks, challenge collapsar (CC) attacks, and DDoS attack blocking. Users can leverage TCOP's alarm capabilities to set detailed alarm trigger rules and receive alarms through various notification channels, including telephone, SMS, email, WeChat, and VIP customer support groups. This significantly improves response speed and handling efficiency for security threats.
Note:
Applicable Scenario
This document is applicable to all users who have integrated EdgeOne and need to configure security event alarms.
Default Alarm Policy
Once you have connected a domain name/L4 proxy instance to EdgeOne, TCOP will, by default, push alarm messages to the email and SMS configured for your Tencent Cloud root account when a security event occurs. You can view the rules for default alarms of cloud service events in TCOP - Event Bus - Event Rules.
Operation Step
Step 1: Configure an Alarm
1. Log in to the TCOP console, in the left navigation bar, choose Alarm Management > Alarm Configuration, and click Create Policy.
2. The detailed configuration of the alarm policy is as follows:
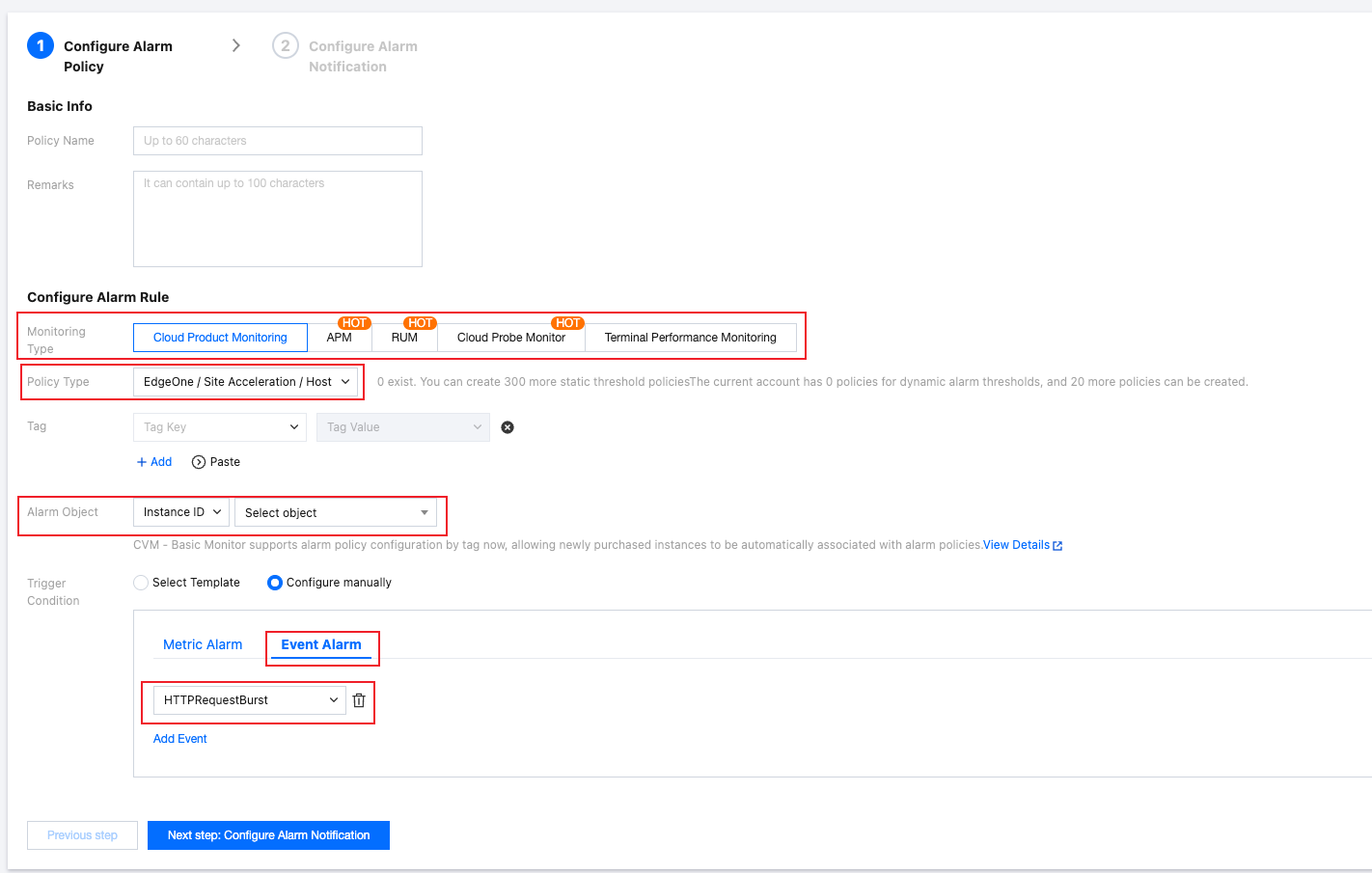
2.1 Select Cloud Product Monitoring for the monitoring type.
2.2 Select EdgeOne / Site Acceleration / Host for the policy type. Different security event alarms require different policy types. See the table below for details:
EdgeOne Security Event Type | TCOP Alarm Policy Type | Configuration Meaning |
HTTPRequestBurst | EdgeOne / Site Acceleration / Host | Alarm for CC attacks on the specified domain name |
DDoS Attack / DDoS Attack Blocked | EdgeOne / L4 Proxy / Instance | Alarm for DDoS attacks/blocking events on the specified L4 proxy instance |
| EdgeOne / Plan | |
2.3 Select the domain name list you want to monitor as the alarm object.
2.4 Select Event Alarm for the trigger condition.
2.5 Select HTTPRequestBurst from the drop-down list.
2.6 For other related configurations, refer to Creating Alarm Policy.
3. Click Next step: Configure Alarm Notification.
Step 2: Configure Alarm Notifications
1. Determine whether the system preset notification template meets expectations. If you need a custom notification template, refer to Creating Notification Template.
2. After selecting the required notification template, click Complete to save the configuration.
References
EdgeOne Security Events and Corresponding Handling Suggestions
The following is a list of security events that could be triggered by EdgeOne, including event types, event descriptions, suggestions, and more.
Event Type | Event Description | Suggestion |
HTTPRequestBurst | EdgeOne has detected a sudden increase in HTTP requests to the domain name, possibly due to a CC attack. Note: The trigger condition is that the rate of HTTP requests exceeds 1,000 queries per second (QPS), and this increase is beyond the baseline of normal traffic predicted by the platform's intelligent learning algorithm. | 1. Monitor your business availability. You can also check recent traffic and request details on the EdgeOne console - Metrics Analysis page to determine whether the spike in traffic is part of normal business activity. 2. If you determine that the sudden increase in traffic is not part of normal business activity and the current security policy does not cover the characteristics of the attack, it is recommended to modify and tighten the Web protection policy. 3. If you determine that the sudden increase in traffic is part of normal business activity, you can ignore this alarm. Additionally, it is recommended to loosen the Web Protection - Adaptive Frequency Control Limit Level or switch to observation mode. |
DDoSAttack | EdgeOne has detected that the IP address serving you is under a DDoS attack. Note: The trigger condition is that the detected DDoS attack bandwidth exceeds the DDoS attack traffic alarm threshold configured by a customer in the EdgeOne console (default value is 100 Mbps). | Monitor your business availability. You can also click the L3/4 DDoS Attack Protection Bandwidth tab on the EdgeOne console - Metrics Analysis page, and then click the Number of DDoS Attack Events tab at the top to view details of the corresponding attack events. |
DDoSAttackBan | The IP address serving you has been blocked by the ISP due to a DDoS attack. |