Client Reputation
Overview
Malicious bots often initiate requests through proxy pools, botnets, or specific devices. EdgeOne's client profile analysis leverages Tencent's twenty years of cybersecurity experience and big data intelligence accumulation to determine the threat status of source IPs in real time. It employs a scoring mechanism, quantifies risk values, precisely identifies access from malicious dynamic IPs, and accurately detects high-risk clients. The system updates the latest threat intelligence every 24 hours and provides threat confidence reports for different IPs. Based on client types involved in attacks, it offers five risk classifications and confidence degrees, allowing custom configuration of protection policies according to threat confidence levels. This effectively controls access from multiple high-risk client categories (network attack sources, exploited network proxy devices, vulnerability scanning tools, cracked login clients, etc.), reducing business risks and blocking malicious activities.
Note:
EdgeOne's Bot intelligence database is continuously updated to include IP addresses that have exhibited multiple, sustained attack behaviors on Tencent's self-operated services in recent days.
Example Scenario
In the Web security analysis module, you observe that under the site
api.example.com, the login interface /api/login has high-frequency access, and there are a large number of failed access requests in a short period of time. However, due to the large number of access IPs, mainly from broadband operator networks, a single IP request is only 1-2 times. Judging from the access features, it is suspected that dial-up IPs are used for brute force cracking login attempts. To strengthen the security policy, we suggest intercepting higher confidence network proxy clients and setting medium confidence clients to observe.Directions
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. Click Security > Web Security . By default, it is a site-level security policy. Click the Domain-level security policy tab and then click the target domain name such as
shop.example.com , to enter the configuration page for the security policy of the target domain name.3. Locate the Bot Management tab and click Edit under Client reputation to enter the configuration page.
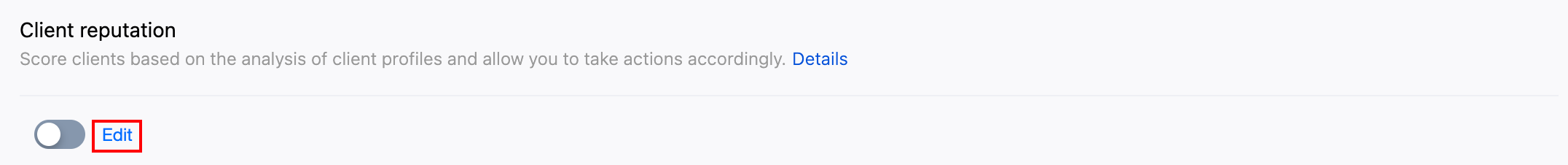
4. Client reputation is classified into network attack, network proxy, scanner, account takeover attack, and malicious bot. For different client types, you can select the corresponding action based on the client credibility level. In this example scenario, dial-up IPs belong to a typical network proxy client. When high-frequency access from dispersed IPs is monitored at the site, you can block high-credibility network proxy clients, and set the action to Monitor for moderate-credibility clients.
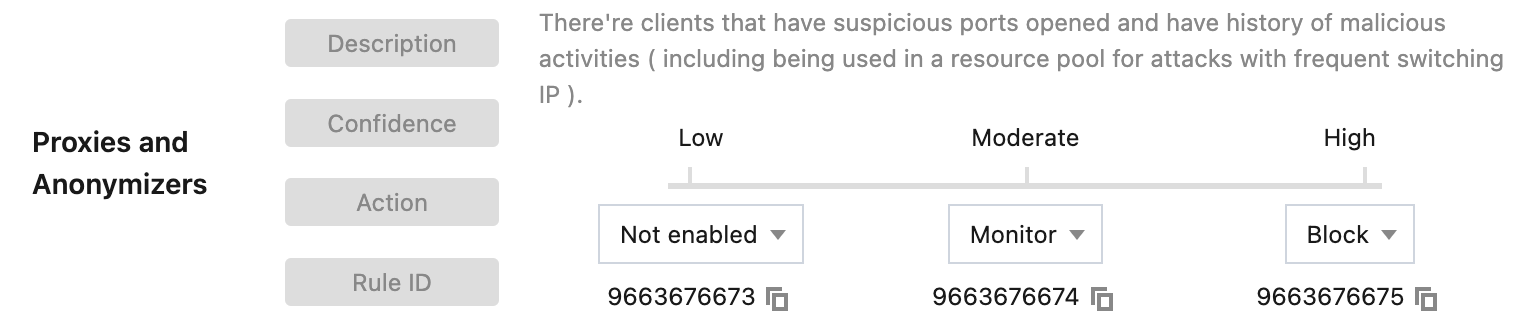
5. Click OK to complete the configuration.
Viewing Traffic That Hits Client Profile Analysis
To view traffic that hits the intelligent client filtering rule:
1. Log in to the TencentCloud EdgeOne console, then click Web security analysis in the left menu bar.
2. Click Add Filter, select Bot Management - Client Profile Analysis, and filter by rule ID, threat classification, and confidence level.
3. Click OK to apply the filter conditions and observe the protection effectiveness in Statistical Trend and Statistical Detail.
Feature Limitation and Handling Solution
Bot client profile analysis may cause a small amount of normal requests to be misjudged in special business scenarios.
IP sharing scenario: In real network environments, multiple users may share the same public network IP address (such as company networks, campus networks). Some large organizations (such as ISPs, large enterprises) may also route multiple users' requests through one or a few egress IPs. When specific users' requests are identified as malicious bots, it may impact other legitimate users. For this scenario, Web-type businesses can consider adjusting the client profile analysis handling method to JavaScript challenge. If the business is super sensitive to false positives, it is advisable to temporarily set the handling method to observation.
Different types of businesses have different tolerance for false positives. When configuring the handling method for Bot client profile analysis, it is advisable to fully consider the characteristics and requirements of the business. Through analysis of traffic that hits client profile analysis, combined with protection exception rules and custom bot rules, you can reduce the error rate and enhance protection capability.
Related References
Risk Classification
Client reputation analysis is based on real-time threat intelligence libraries and can effectively identify clients with the following 5 types of malicious behavior history:
Network attack: Clients with recent attack behavior (such as DDoS, high-frequency malicious requests, site attacks, etc.). For example, attacks initiated by the Mirai botnet can be classified into this category.
Network proxy: Clients that have recently opened suspicious proxy ports and have been used as network proxies, including dial-up IP proxy pools and IoT proxy networks used to initiate malicious requests.
Scanner: Clients with recent scanner behavior targeting known vulnerabilities. For example, vulnerability scanning tools for Web applications.
Account takeover attack: Clients with recent malicious login cracking and account takeover attack behavior. For example, attackers who use brute force to crack user login credentials.
Malicious bot: Clients with recent malicious bot, hotlinking, and brute force cracking behaviors. For example, illegal bots that collect website content.
Credibility Level
For each category of client reputation rules, each credibility level corresponds to a client address list. The credibility level reflects the frequency and consistency of the client address's recent malicious behavior in that category:
Higher credibility: The client address has recently engaged in stable, high-frequency malicious behavior in that category. It is recommended to intercept such clients.
Moderate credibility: The client address has recently engaged in significant frequency malicious behavior in that category. It is recommended to configure such clients for JavaScript challenge or observation.
General credibility: The client address has recently engaged in stable malicious behavior in that category. It is recommended to configure this type of client as an observation, and then adjust it to a JavaScript challenge or a hosting challenge based on the analysis results.