Custom Bot Rule
Overview
When you need to customize fine-grained policies for specific bot behaviors or features based on existing Bot management policies, custom bot rules can provide you with flexible matching conditions (such as client IP, header information, request method, static feature recognition, and client reputation analysis results), and can be combined with disposal strategies that randomly select actions by weight, helping you create accurate management strategies to effectively manage the risks brought by bot access to the site.
Note:
Custom bot rules support randomly configuring multiple actions by weight. For example, you can configure 25% of requests as observation, 25% of requests as interception, 25% of requests as release, and 25% of requests as Managed Challenge. This approach can confuse bot tools' perception of bot effectiveness while also helping to reduce risk during the Canary testing phase.
Scenario 1: Silent Processing to Avoid Risks when Bot Requests for Sensitive API Interfaces Surge
Scenario Example
In Web security analysis, a large number of sudden request accesses to the login interface are found. After reviewing the abnormal clients, the requests mainly come from multiple proxy clients in the
222.22.22.0/24 IP segment, trying to log in to accounts using various types of clients. To urgently mitigate business risks and consume malicious tool resources, silent processing can be used to handle requests from related sources (maintaining client TCP connections but no longer responding to HTTP requests).Directions
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. Click Security > Web Security . By default, it is a site-level security policy. Click the Domain-level security policy tab and then click the target domain name such as
www.example.com, to enter the configuration page for the security policy of the target domain name.3. Locate the Bot Management tab and click Add rule under Custom rules to enter the configuration page.
4. Enter the rule name and configure the judgment conditions and actions. In this example scenario, you can configure the matching fields as Client IP equal to the
222.22.22.0/24 IP range and User-Agent including cURL , and select the action as Silent drop . Note:
Priority: The lower the value, the higher the priority. When a request matches multiple rules, the action of the rule with the higher priority (lower numerical value) applies.
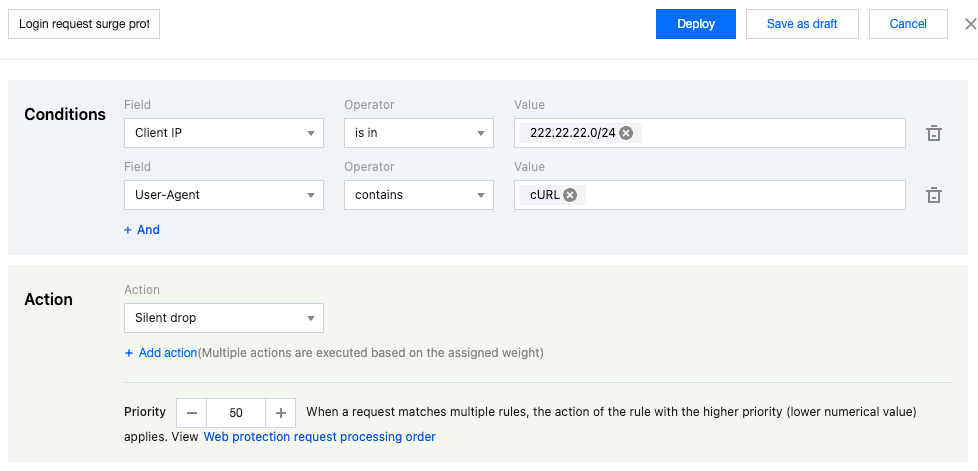
5. Click Save and publish . The rule will be deployed and take effect.
Scenario 2: Implement a Combination of Multiple Disposal Methods for Bot Management Policies on the Login Page to Reduce the Risk of Account Theft (ATO: Account-Take-Over)
Example Scenario
In order to control the risk of account theft and prevent batch login methods from stealing accounts, the business needs to conduct human-machine verification for access to the login page while ensuring the best possible user experience. Clients with a higher credibility level of account takeover risk (including brute force and other account theft methods) can be controlled: a certain proportion of login page accesses will be subject to human-machine verification, while other requests will be subject to a short time wait, ensuring that when tools attempt batch logins, they will trigger a human-machine challenge after a certain number of attempts and avoid high-frequency attempts through short time waits.
Directions
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. Click Security > Web Security . By default, it is a site-level security policy. Click the Domain-level security policy tab and then click the target domain name such as
www.example.com, to enter the configuration page for the security policy of the target domain name.3. Locate the Bot Management tab and click Add rule under Custom rules to enter the configuration page.++
4. Enter the rule name and configure the judgment conditions and actions. In this example scenario, you can configure the matching field as Client reputation equal to Account Take Over Attackers-High confidence . For the action, first select Managed Challenge and then click Add action to add the Add short latency action. Set the weight to 20% for Managed Challenge and 80% for Delayed response(short).
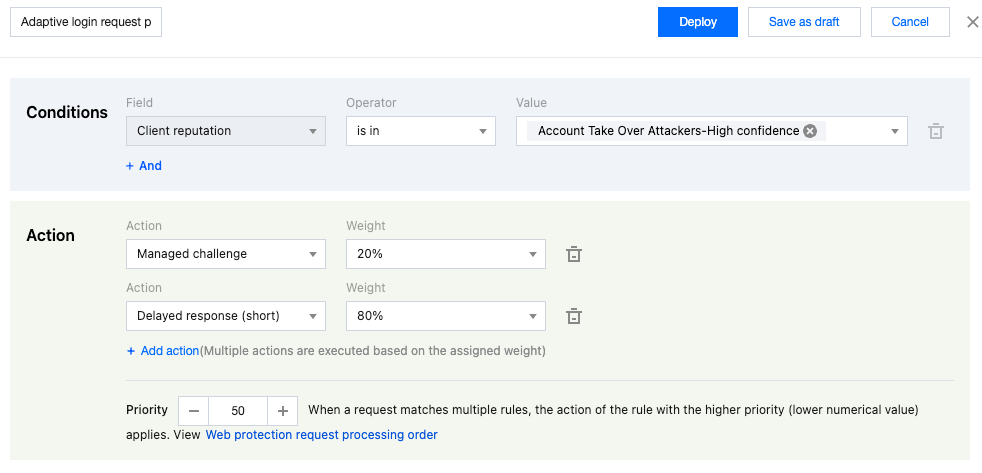
5. Click Save and publish . The rule will be deployed and take effect.
Scenario 3: Optimize the Bot Intelligent Analysis Policy and Allow Requests with Specified Bot Intelligent Analysis Features
Example Scenario
After the site enables Bot intelligent analysis, it identifies Bot tags for site requests based on the general policy model. By default, it identifies scenarios where the request User-Agent does not match the request TLS fingerprint and marks them with Bot risk tags. When a client accesses the site through a local proxy (e.g., local SOCKS proxy), the request User-Agent and TLS fingerprint mismatch will occur. If the site service allows the client to access through this method, you should optimize the Bot intelligent analysis policy and allow requests with specific Bot intelligent analysis features to avoid false blocking.
Directions
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. Click Security > Web Security . By default, it is a site-level security policy. Click the Domain-level security policy tab and then click the target domain name such as
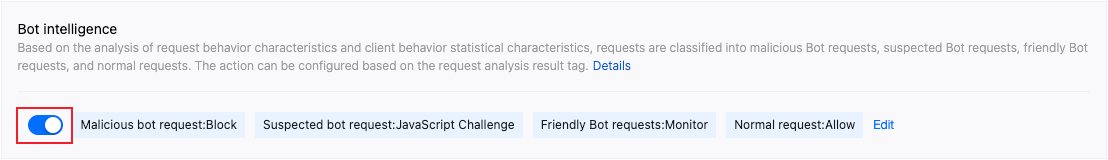
www.example.com, to enter the configuration page for the security policy of the target domain name.3. Locate the Bot Management tab and click the switch under Bot Intelligent Analysis to enable this feature.
4. Locate the Bot Management tab and click Add rule under Custom rules to enter the configuration page.
5. Enter the rule name and configure the judgment conditions and actions. In this example scenario, you can configure the matching field as Bot intelligent analysis feature equal to TLS Fingerprint Inconsistency and select the action as Allow.
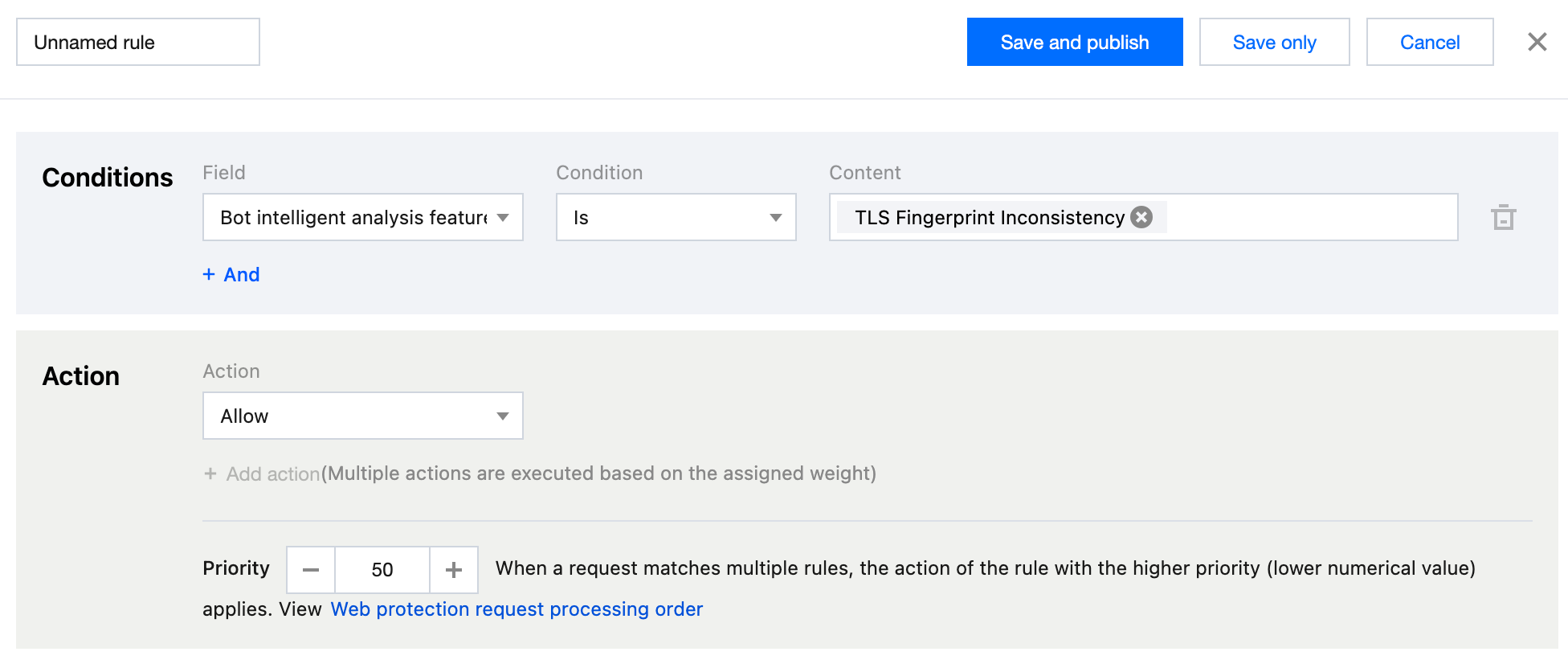
6. Click Save and publish. The rule will be deployed and take effect.
- Overview
- Scenario 1: Silent Processing to Avoid Risks when Bot Requests for Sensitive API Interfaces Surge
- Scenario 2: Implement a Combination of Multiple Disposal Methods for Bot Management Policies on the Login Page to Reduce the Risk of Account Theft (ATO: Account-Take-Over)
- Scenario 3: Optimize the Bot Intelligent Analysis Policy and Allow Requests with Specified Bot Intelligent Analysis Features