API Discovery(Beta)
Function Overview
API Discovery helps enterprises automatically discover, count, and manage API call situations on the platform. This function is based on request flow data that has been integrated into the EdgeOne platform. By parsing HTTP request paths, request methods (such as GET, POST, etc.), and associated response features, it automatically extracts the actual accessed API paths and usage. The system classifies the received request data, removes noise, and performs trend analysis, helping enterprises accurately identify active APIs, deprecated APIs, and potential shadow APIs.
The main features of API asset identification include:
Automatic Comprehensive Identification: Based on real-time incoming traffic, it dynamically sorts all API call assets proxied by EdgeOne without manual input.
Precise Risk Positioning: Identifies high-frequency abnormal calls, unusually exposed interfaces, and deprecated interfaces as potential risk points, assisting in formulating security policies.
Optimized Resource Allocation: Guides the optimization of backend resource configuration and interface governance through evaluation of call activity and trends.
Typical Business Scenarios
Quickly discover and address shadow APIs: Security operations personnel discover unknown API calls during routine inspections, which may expose sensitive data or service risks.
Investigate and handle abnormal traffic for interfaces: Operations engineers notice a sudden increase in traffic for a specific API and need to quickly analyze the cause and formulate throttling strategies.
Operation Steps
The following example illustrates the specific usage process of "Shadow API Discovery and Handling":
1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. In the site detail page, click Security Protection > API Protection to enter the API asset identification page.
3. Set the time zone and time range to view at the top of the page (for example, "Last 7 days"), with data retrievable for up to 30 days.
4. Filter by domain or directly input API path keywords to search for specific interfaces, quickly locating suspected shadow APIs.
5. View the call counts and trends for specific APIs to identify abnormal or unknown API paths.
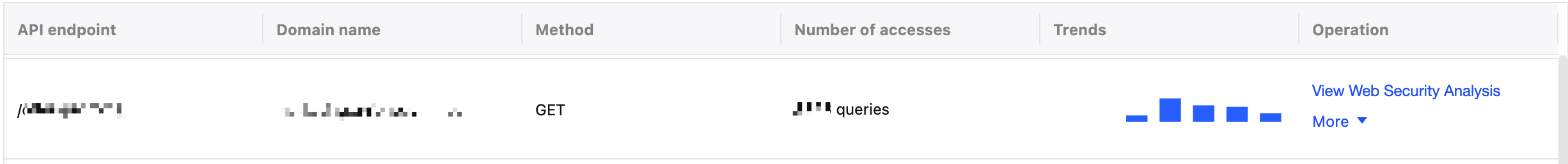
6. For risky APIs, click the corresponding action button, such as quickly creating Precise Matching Rules for interception or setting call frequency limits through Rate Limiting Rules.
Analysis Process and Handling Recommendations
1. If confirmed as abnormal traffic, immediately set rate limits for the corresponding interface to prevent backend resources from being abused or causing service unavailability.
2. For more detailed investigations, use EdgeOne's real-time logging feature to obtain real-time data, confirming the source and pattern of calls.
3. Based on the investigation results, further measures may be taken if necessary:
Adjust API Interface Permission Control: For sensitive or high-risk API interfaces, it is recommended to implement access control through custom rules in the EdgeOne console, such as:
Allowing access only from specific IPs or IP segments (via IP blocklist/allowlist rules).
Requiring specific headers (such as custom authentication tokens) to be present and pass format validation.
Working with application-side authentication mechanisms (such as JWT Token validation, OAuth authorization processes) and limiting illegal requests through rules in EdgeOne.
Combining access frequency statistics to implement throttling or interception for requests without valid identity credentials.
Strengthen API Security Protection Policies: Configure stricter WAF rules for high-risk interfaces, such as enabling strict parameter validation, access frequency limits, or challenge verification based on client behavior characteristics.
Usage Restrictions and Handling Recommendations
Data Update Delay: Data is updated daily, with a maximum delay of 24 hours. For more timely analysis results, combine with the real-time logging function for a comprehensive analysis.
Historical Data Retention Period: The platform retains API call data for the past 30 days.
Related Capability Linkage
API asset identification can be linked with the following EdgeOne security features to further enhance security operations efficiency:
Web Protection: Based on API identification results, directly create precise Web Application Firewall (WAF) rules to guard against API attack risks.
Analysis:Combine with traffic analysis functionality for in-depth investigation of abnormal API calls and locate the sources of abnormal traffic.
Rate Limiting:Quickly formulate rate limiting strategies for high-frequency abnormal APIs to protect business stability.