Authentication Method A
Authentication URL format
http://Hostname/Filename?token=timestamp-rand-uid-md5hashhttps://Hostname/Filename?token=timestamp-rand-uid-md5hash
Description of authentication fields
Field | Description |
Hostname | Site Acceleration Domain. |
Path | Resource access path, authentication requires prefixing with /. |
token | Authentication parameters name set by Definition. |
timestamp | Decimal positive integer Unix timestamp (the total number of seconds from 00:00:00, January 1, 1970, UTC time, to now, independent of the timezone) |
rand | 0 - 100 characters, a random string consisting of uppercase and lowercase letters and numbers. |
uid | User ID, currently unused, default is 0. |
md5hash | A fixed length string of 32 bits calculated using the MD5 algorithm: Algorithm: MD5(Path-timestamp-rand-uid-key). Authentication Logic: If the request has not expired, the node compares this string value with the md5hash value carried in the request URL. If the values are the same, authentication passes, and the request is responded to; if the values are different, authentication fails, returning 403. |
Configuration Samples
Assume the request
https://www.example.com/foo.jpg uses Authentication Method A, configured as follows: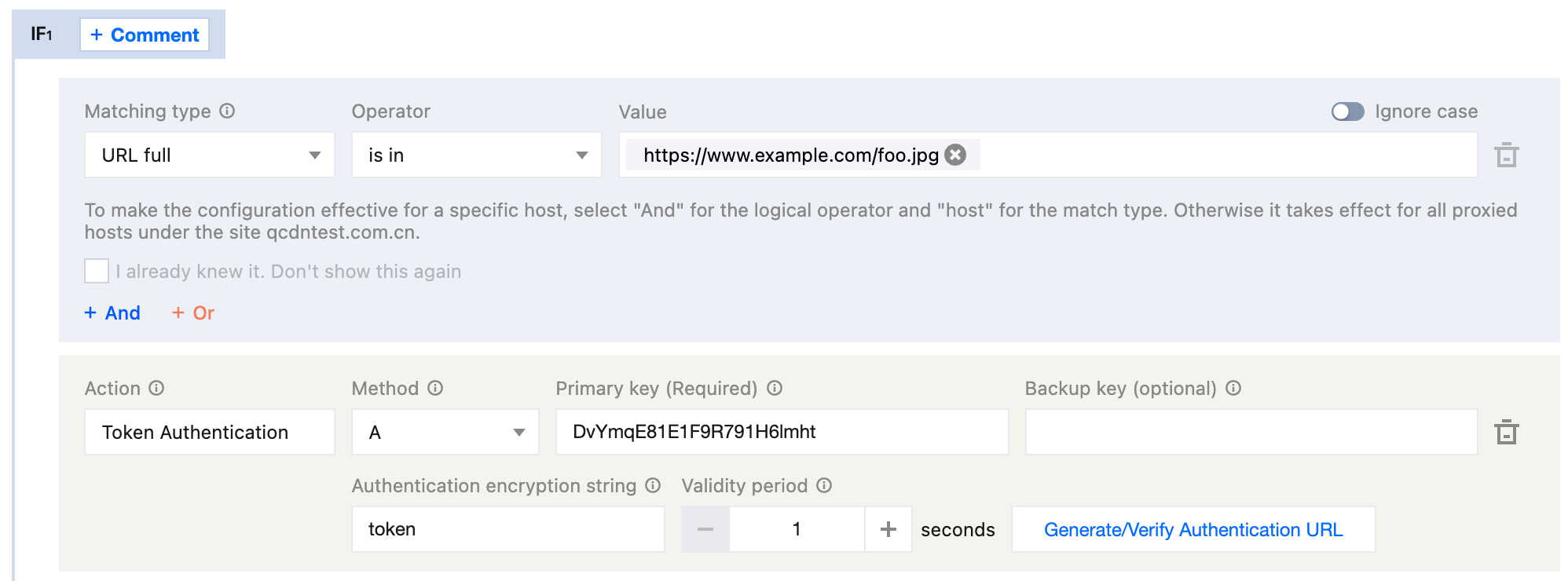
Get authentication parameters:
Path:
/foo.jpg.timestamp: The server generates the authentication URL timestamp as July 15, 2024, 15:27:17 (UTC+8), converted to a decimal (Unix timestamp) format value:
1721028437.rand: The generated random number is
Kv4cPTAAP5YTi.uid:
0.Key:
DvYmqE81E1F9R791H6lmht.md5hash:MD5(Path-timestamp-rand-uid-key)= MD5(
/foo.jpg-1721028437-Kv4cPTAAP5YTi-0-DvYmqE81E1F9R791H6lmht)= 0fbdca749d7ab784750685347e42075c.Authentication URL generated by the client request
https://www.example.com/foo.jpg?token=1721028437-Kv4cPTAAP5YTi-0-0fbdca749d7ab784750685347e42075cNode Authentication
When the Node Server receives a request from the client via the encrypted URL, it extracts the timestamp parameter from the URL, adds the configured Effective duration of "1 second", and compares it to the current time:
1. exceed the "timestamp + effective duration" time, the request is not expired, continue to step 2.
2. The Node Server calculates the md5hash value using the obtained authentication parameters and compares it with the md5hash value carried in the request URL. If the values are the same, authentication passes and the request is responded to; if the values are different, authentication fails, returning 403.