Exclusive DDoS Protection Usage
Background Introduction
If your business has the following requirements for accessing services:
1. DDoS protection services with committed protection capacity, such as financial business, gaming platform services, etc.
2. When subjected to large-scale DDoS attacks, the business under the default platform protection may change the resolution IP due to business scheduling, which may affect the smooth operation of the business. You need to continuously maintain the session state business, including maintaining the DNS resolution IP unchanged, maintaining the TCP long connection and HTTP long session state. Such as: multiplayer online gaming services, voice services, etc.
3. Need to customize network layer DDoS protection strategy or network layer control strategy. For example, discard client traffic from specified regions.
It is recommended that you purchase exclusive DDoS protection services. Exclusive DDoS protection services provide further on the basis of the default platform protection:
1. Regular access to the cleaning center for continuous detection, cleaning, and filtering of malicious traffic.
2. Committed protection capacity with stable sessions maintained during protection. You can flexibly select protection specifications of global availability zones (excluding the Chinese mainland), Chinese mainland availability zones, or global availability zones based on your business deployment.
3. Customizable DDoS protection strategies, including IP-based and client region-based control options.
Help you mitigate DDoS attack risks and ensure business stability.
Policy Configuration
Exclusive DDoS protection can provide flexible custom DDoS protection and traffic control policies to meet your business protection requirements. You can respond to ever-changing attacks by flexible settings based on special business characteristics. For L4 proxy instances, the following custom rule features are supported:
Protection Module | Feature Description |
Restricts access to EdgeOne sites in DDoS attacks by matching the IP allowlist/blocklist. | |
Restricts access to EdgeOne sites from a specified port range in DDoS attacks by using custom port rules. | |
Allows access to EdgeOne sites only through specified protocols. | |
Supports protection against connection-type attacks by automatically blocking clients with abnormal connection behaviors. | |
Supports custom blocking policies for IP, TCP, and UDP message headers or payload characteristics in DDoS attacks. | |
Restricts access to EdgeOne sites in DDoS attacks by matching regions. |
Note:
1. Only L4 proxy instances with exclusive DDoS protection enabled support custom DDoS protection policies.
2. When the access traffic matches policies of multiple protection modules simultaneously, it is handled according to the module order shown in the table.
Usage Guide
Exclusive DDoS protection can be applied to both L7 and L4 services. You can refer to the following different scenarios to understand how to enable exclusive DDoS protection for your site.
Note:
1. Exclusive DDoS protection is only available for EdgeOne Enterprise plans, and supports only Enterprise plans connected after July 1, 2023. If you connected EdgeOne Enterprise before this date and wish to use Exclusive DDoS protection, please contact us.
2. After an L7 site subscribes to Exclusive DDoS protection, all L7 sites within the same plan will share this subscription. Different plans cannot share Exclusive DDoS protection subscriptions and require separate subscriptions.
3. Each L4 proxy instance requires an individual Exclusive DDoS protection subscription.
Scenario 1: Enable exclusive DDoS protection for L7 sites
Scenario Example
You provide a unified login service (SSO, Single-Sign-On) through the domain name
onelogin.example.com, mainly serving users in the Chinese mainland. Due to frequent DDoS attacks, users may not be able to log in normally. The estimated daily attack level is 30Gbps, and the peak period may reach 50Gbps. You need to access exclusive DDoS protection to ensure the provision of stable and available services.Precautions
After the exclusive DDoS protection is created within the L7 site, it is temporarily not supported to unsubscribe in the console. If you need to unsubscribe, please contact Tencent Cloud sales.
Enabling or disabling DDoS protection during the process may affect the business (connection reset, etc.), and the impact duration is estimated to be generally 2-3 minutes for enabling or disabling. If there is local or operator DNS cache, the switch may take effect later, and the specific effective time depends on the TTL configuration of the DNS record used by the client.
Operation Steps
1. Log in to the EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. On the site details page, click Security > DDoS Mitigation.
3. In the Site (L7) Service Protection tab, click Subscribe Exclusive DDoS Protection.
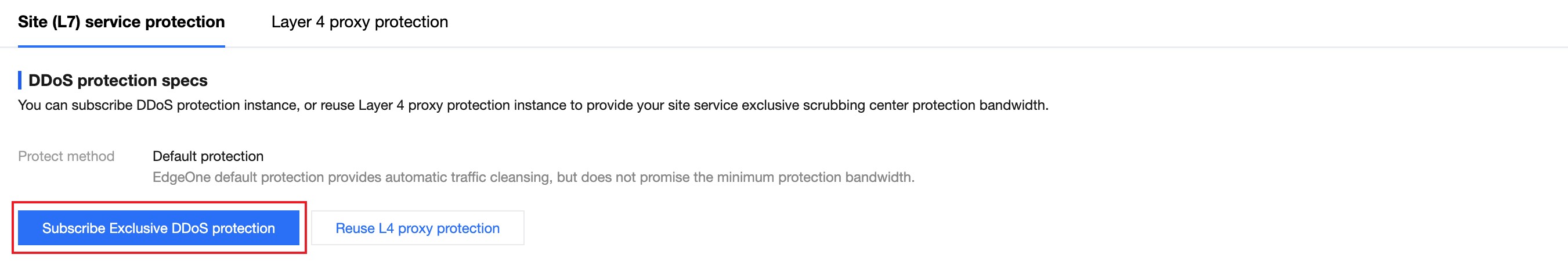
4. On the Subscribe Exclusive DDoS Protection Instance page, select the protection region and protection specs you need to subscribe to. In this scenario, based on the service area and historical attack level, you can choose to subscribe to the Chinese mainland availability zone with a guaranteed 30Gbps and an elastic capacity protection peak of 50Gbps.
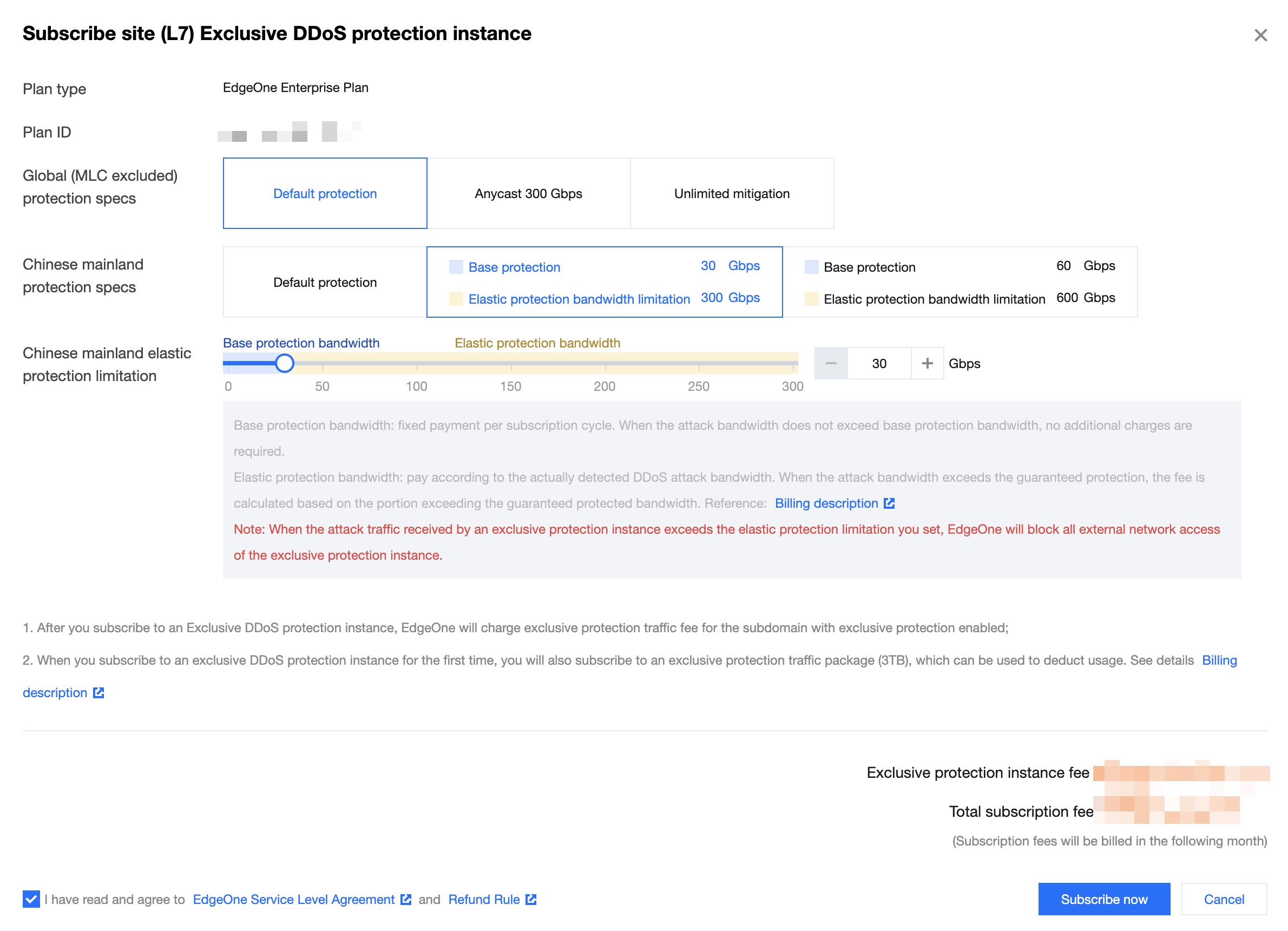
5. After confirming the relevant fee information, check the box to agree to the relevant user agreement, and click Subscribe Now to start automatically issuing exclusive DDoS protection instance configurations for you.
6. After the instance is issued, you can enable exclusive DDoS protection for all domain names in the protection configuration page, or select
onelogin.example.com in this scenario and enable exclusive DDoS protection for this domain name.7. If you enable exclusive DDoS protection for a single domain name, a deployment confirmation window will pop up. Click Confirm to start the deployment, and wait for the deployment to complete before it takes effect.
Scenario 2: Enable exclusive DDoS protection for L4 proxy instances
Scenario Example
You have an upcoming game release that requires L4 proxy acceleration to optimize player login experience, transmitting TCP traffic data through port 80. The game is mainly distributed overseas, and it is expected to encounter large-scale DDoS attacks (not exceeding 300 Gbps) during the launch period. By accessing exclusive DDoS protection, you can ensure the stability of the login API service during the release and operation period, avoiding player loss.
Precautions
Currently, only new L4 proxy instances are allowed to select exclusive DDoS protection, and it cannot be modified or changed after creation;
Exclusive DDoS protection for L4 proxy is temporarily not supported for dynamic enabling/disabling.
Operation Steps
1. Log in to the EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. On the site details page, click L4 Proxy.
3. On the L4 Proxy Management Instance page, click Create L4 Proxy.
4. When creating an L4 proxy instance, you can select the corresponding protection method in the security protection configuration, switch to exclusive DDoS protection, and select Anycast joint defense 300Gbps for the current scenario.
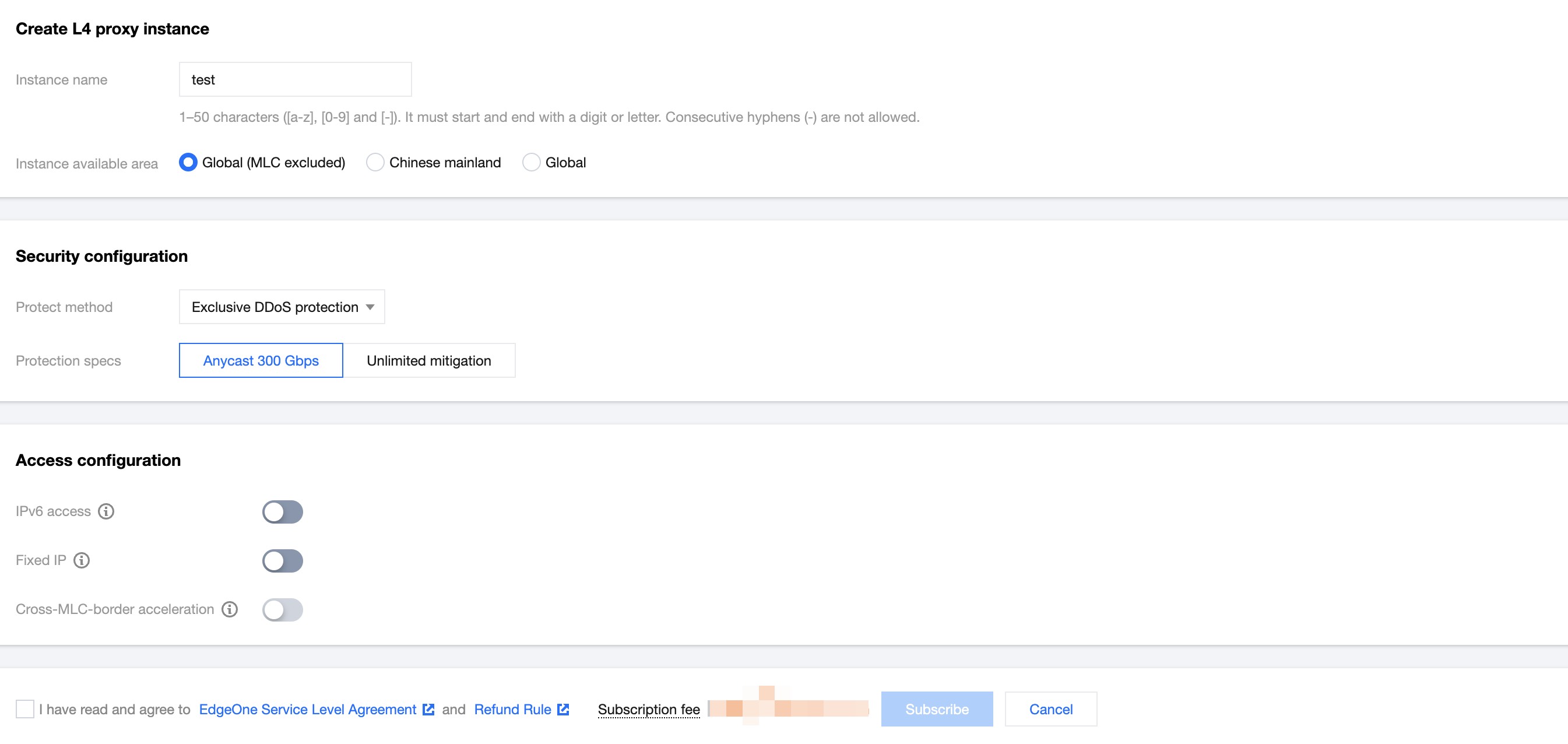
5. After confirming the relevant user agreement and price information, click Subscribe to complete the creation of the L4 proxy instance. After creation, the platform will automatically issue exclusive DDoS protection configurations for the instance;
6. After the configuration is issued, you can click Configure to enter the instance configuration interface, add the required acceleration port information and origin address, and click Save to enable L4 proxy acceleration.
Related References
Working Principle
After enabling Exclusive DDoS protection, the traffic will be processed according to the following process:
1. When the client resolves the service DNS record, it will obtain the cleaning center address.
2. When the client accesses the service, the cleaning center first cleans the traffic, automatically identifies and filters the network layer DDoS attack traffic. If the current business has access to the L4 proxy service, the filtered traffic is accelerated by the L4 proxy service.
If your site includes L7 site acceleration, the traffic will continue to be forwarded according to the following steps:
3. After SSL authentication, HTTPS protocol requests continue to be protected by Web Protection and bot management security policies;
4. Requests that pass the security module verification will continue to go through site caching, site acceleration, and origin-pull service functions.